Risky Bulletin: CISA tells federal agencies to mitigate on-prem-to-cloud Exchange attack
In other news: New HTTP desync attacks; new Trend Micro zero-day; and loads and loads of data breaches.

This newsletter is brought to you by no-code automation platform Tines. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
CISA has released a rare emergency directive ordering federal agencies to patch a new attack vector in Microsoft Exchange email servers.
Federal agencies have four days, until August 11, to address the issue and apply mitigations shared by Microsoft on Wednesday.
The guidance addresses a vulnerability (actually more of a design flaw) in hybrid environments, where Exchange on-premise servers sync data to an Exchange Online instance.
Microsoft says that in old default setups, on-prem servers share the authentication service (Service Principal) with the synced online instance.
When deployed for the first time, default hybrid installations will upload the on-prem authentication certificates to this service to allow local instances to authenticate on the Exchange Online server and sync data.
Attackers who compromised an on-prem Exchange server can abuse their control over the system to hijack, create, or alter authentication tokens that grant intruders access further up the cloud environment.
Microsoft says this attack scenario does not leave an "easily detectable and auditable trace" and may be invisible to compromised companies.
The company has urged owners of on-prem servers to install an April hotfix that converts the connection between on-prem and online environments into a standalone Entra app.
Exchange owners must then follow setup instructions that include steps to clean older hybrid auth certs and upload new ones to the separate Entra hybrid app exclusively, where an attacker's access is severely limited.
The hybrid on-prem-to-online attack works on Exchange 2016 and Exchange 2019, but also Exchange Server Subscription Edition. This latter version is a yearly subscription model for Exchange servers that replaces the old "OS release" style versions. Customers of all three versions will have to follow the steps if using a hybrid configuration.
Microsoft assigned CVE-2025-53786 to this issue.
The company credited Dirk-jan Mollema from Outsider Security with reporting the attack vector. So far, Microsoft says it saw no active exploitation, but that's a rushed and somewhat silly thing to say for an attack that doesn't leave traces in logs.
Is it even a real Black Hat talk without last minute fixes? 😅 And even a surprise CVE it seems, with slight spoilers for my talk: https://t.co/mubGjbYfNG
— Dirk-jan (@_dirkjan) August 6, 2025
See you in an hour at Black Hat!
@_dirkjan dropping a ton of interesting info at BlackHat. Including a day-fresh CVE pic.twitter.com/1G16dxoHt4
— Olaf Hartong (@olafhartong) August 6, 2025
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
DOJ hacked again: A suspected state-sponsored hacking group has hacked the case management system of the US Department of Justice. The hack took place around the July 4th holiday. It impacted two systems for managing case files, known as PACER and CM/ECF. According to Politico, the hack exposed sensitive court data, including ongoing investigations and some informant and witness data.
Google discloses breach: Hackers have breached and stolen customer data from Google's Salesforce account. Google confirmed the breach and attributed the hack to a group named UNC6040. The company said most of the stolen data was publicly available business information, such as business names and contact details.
Pandora breach: Danish jewelry company Pandora is notifying customers of a security breach. The company says hackers took the data from a third-party platform. Per reports, Pandora is the latest to have its Salesforce account hacked. It joins the aforementioned Google, along with Cisco and fashion house Chanel, which also disclosed similar breaches this week.
Air France and KLM breach: A hacker stole customer data from Dutch airline KLM and French airline Air France. The breach occurred at a third-party platform that the two use for customer service. The airlines said no sensitive or financial data was stolen in the incident.
Bouygues Telecom breach: Hackers have stolen the personal data of 6.4 million customers of French telecommunications company Bouygues Telecom. The breach took place on Monday, August 4. The hackers stole personal and contractual details, along with bank account numbers. Account passwords were not compromised. Bouygues Telecom said it's notifying affected customers.
TeaOnHer breach: The TeaOnHer app is leaking user data due to a security flaw. According to TechCrunch, the app is leaking usernames, emails, driver's licenses, and selfies. The app launched this week and allows men to share details of abusive women and discuss their dates. It is a response to the controversial Tea app, which suffered a similar and more public leak.
PBS breach: A trove of PBS employee data was apparently being shared around in a Discord channel for PBS Kids fans. [Additional coverage in BleepingComputer]
WestJet inquiry: Canada's privacy commissioner has opened an investigation into the WestJet hack from June. The hack was the work of Scattered Spider, and the investigation may end up with a big fine for the airline. [Additional coverage in CBC]
DaVita breach numbers: Kidney dialysis service DaVita said that this year's April ransomware attack exposed the data of more than 915,000 patients. [Additional coverage in The Record]
SK Telekom reports huge losses: South Korea's largest telco reports that second-quarter profits fell by 37% due to a recent security breach. SK Telekom said compensation expenses weighed heavily on its Q2 results. The company suffered a catastrophic breach in April, when hackers stole the SIM data of all its customers. The telco incurred huge costs in replacing everyone's SIM cards, and also lost a large number of customers who moved to rival networks. [Additional coverage in The Korea Herald]
General tech and privacy
Microsoft hosted Israel's surveillance program: Israeli intelligence built a massive phone surveillance operation that tracked all phone calls and messages sent across Palestine. The system became operational in 2022 and was hosted in a segregated part of Microsoft's Azure cloud. According to a joint investigation by The Guardian, the +972 Magazine, and Local Call, Israel's Unit 8200 Commander Yossi Sariel personally met Microsoft CEO Satya Nadella to secure the project's technical backbone. This included almost infinite storage and a highly secure environment. The project caused internal strife at Microsoft among staff. One employee interrupted a Nadella keynote this year, yelling: "How about you show how Israeli war crimes are powered by Azure?"
Home Depot and Lowe's ALRs: US retail chains Home Depot and Lowe's are sharing the data from their automatic license plate readers with US law enforcement. [Additional coverage in 404 Media]
Musk wins deepfake lawsuit: Elon Musk and Twitter have won a lawsuit filed against the state of California over its law that required online platforms to remove deep fakes of politicians during election cycles. [Additional coverage in Bloomberg Law]
NVIDIA argues against backdooring its chips: In a blog post this week, NVIDIA has appealed against chip backdoors. The post comes as US officials are exploring the idea of mandating the company to include killswitches, backdoors, and location-tracking tech in its chips to prevent products from reaching adversaries like China.
Windows UI to go "truly" open-source: Microsoft has promised to open-source the Windows user interface. They did this six months ago, but the OS maker is promising to actually release the full source this time around.
Dashlane ends free tier: Password manager Dashlane is discontinuing and ending its free plan on September 16.
Rare Breed TV shutdown: Anti-piracy group ACE announced the shutdown of illegal streaming service Rare Breed TV after the service agreed to shut down servers and pay a financial settlement.
Government, politics, and policy
Russian GDPR: The Russian government is working on a data privacy law that will allow citizens to see who uses their data and withdraw consent for the use of their data from within their own government portal accounts. [Additional coverage in Forbes Russia]
US formally declares war on the EU DSA: The US State Department has ordered US diplomats to lobby against the EU's Digital Service Act, a EU law that requires tech platforms to crack down on illegal online content. The marching orders included in a leaked memo obtained by Reuters were to argue that the DSA stifles fReE sPeEcH. It doesn't. It's just the US government is a slave to tech broligarchs these days.
NIST cancels AI security report: NIST has canceled the publication of a report on an AI red team exercise that found 139 new ways to hack AI models. [Additional coverage in Wired]
Small defense firms are a tempting target: Speaking at Black Hat, NSA official Bailey Bickley has warned that small defense industrial base companies are an attractive target for foreign APTs due to their weaker cyber defenses but oversized role in military supply chains. [Additional coverage in NextGov]
Germany rules on spyware use rules: Germany's highest court ruled that police can only use spyware against suspects of serious crimes. Spyware cannot be used to monitor individuals suspected of crimes that carry a maximum sentence of less than three years. The court ruled in a 2017 lawsuit brought by German digital freedom organization Digitalcourage. [Additional coverage in The Record]
Sponsor section
In this Risky Business sponsor interview, Tines Field CISO Matt Muller chats with Casey Ellis about the interesting and out-of-the-box ways they've seen people using the platform. Tines is a platform designed to automate repetitive tasks for IT and security teams. And, as it turns out, it can be used to … gamify shift handover?
Arrests, cybercrime, and threat intel
Samourai founders plead guilty: The two founders of the Samourai Wallet cryptocurrency mixing service have pleaded guilty to money laundering-related charges. Samourai CEO Keonne Rodriguez and CTO William Lonergan Hill were arrested last year after the FBI took down their service. Officials say the two specifically designed and promoted their tool to hide and move illicit funds. Samourai Wallet allegedly helped launder more than $200 million worth of crypto assets from hacks, online fraud, and drug trafficking.
Tornado Cash co-founder convicted at trial: The co-founder of the Tornado Cash cryptocurrency mixing service was found guilty following a four-week jury trial. Roman Storm was found guilty of running an unlicensed money transmitting business. The FBI took down the Tornado Cash service in 2022 for helping launder more than $1 billion in illicit crypto operations. The jury didn't find Storm guilty of money laundering. He's set to be sentenced later this year and faces a maximum prison sentence of five years.
Toha profile: Brian Krebs has published a profile on Toha, the admin of the XSS forum, who was detained last month by Ukrainian authorities.
GreedyBear floods Firefox AMO: A threat actor has uploaded more than 150 malicious Firefox extensions on the browser's official add-ons store. The extensions were initially clean but were later updated with malicious code that collected crypto-wallet credentials. According to Koi Security, the group also runs fake crypto investment scam sites, phishing sites, and malware delivery portals. So far, the group appears to have earned more than $1 million from its operations.
VexTrio: Infoblox has published a report on VexTrio, a TDS platform that launched in 2017 and currently redirects traffic from hijacked sites and devices to a wide spectrum of cybercrime operations. Per Infoblox, the operation is managed by individuals from Belarus and Russia, through a network of front companies across Eastern Europe.
New UNC6240 group: The hacking campaign targeting Salesforce accounts includes two threat actors. Google says the hacking is done by a group tracked as UNC6040, while a second group named UNC6240 is extorting companies with the stolen data. The group contacts victims via email and phone to request payment in Bitcoin within 72 hours. The messages are signed using ShinyHunters, the name of an old hacking group that had many members arrested. It's unclear if the new group is connected to the older group.
Chinese smishing ecosystem: The Security Alliance has published an analysis of the Chinese smishing ecosystem, believed to have compromised between 12.7 million and 115 million payment cards in the US alone over the past three years.
npm libraries wipe systems: Socket Security has discovered two npm libraries with a unique killswitch that can wipe developer systems. The libraries will check a developer's phone number against a remote database and wipe systems if not found. The libraries pose as dev tools for the WhatsApp Business API, and the remote database contains mostly Indonesian numbers.
Malicious Go packages: Socket also found 11 malicious Go libraries that download and run malware on infected systems.
Malicious PyPI packages: GitLab's security team has found five malicious PyPI packages targeting the dev ecosystem of the Bittensor cryptowallet.
BADBOX 2.0: Despite several attempts to take down the BADBOX botnet, the malware is still alive. Recently, both Estonian and Finnish authorities have published alerts that the malware is still active within their borders.
Akira's SonicWall attacks: GuidePoint Security and Logpoint have published their own findings from investigating attacks on SonicWall firewalls that resulted in the deployment of the Akira ransomware. The new findings include Akira's abuse of two new drivers to bypass and evade AV/EDR solutions.
ThrottleStop driver abuse: Kaspersky says threat actors are abusing the ThrottleStop driver to disable antivirus and security software during malware deployments. This is one of the two drivers that GuidePoint also saw abused (see item above).
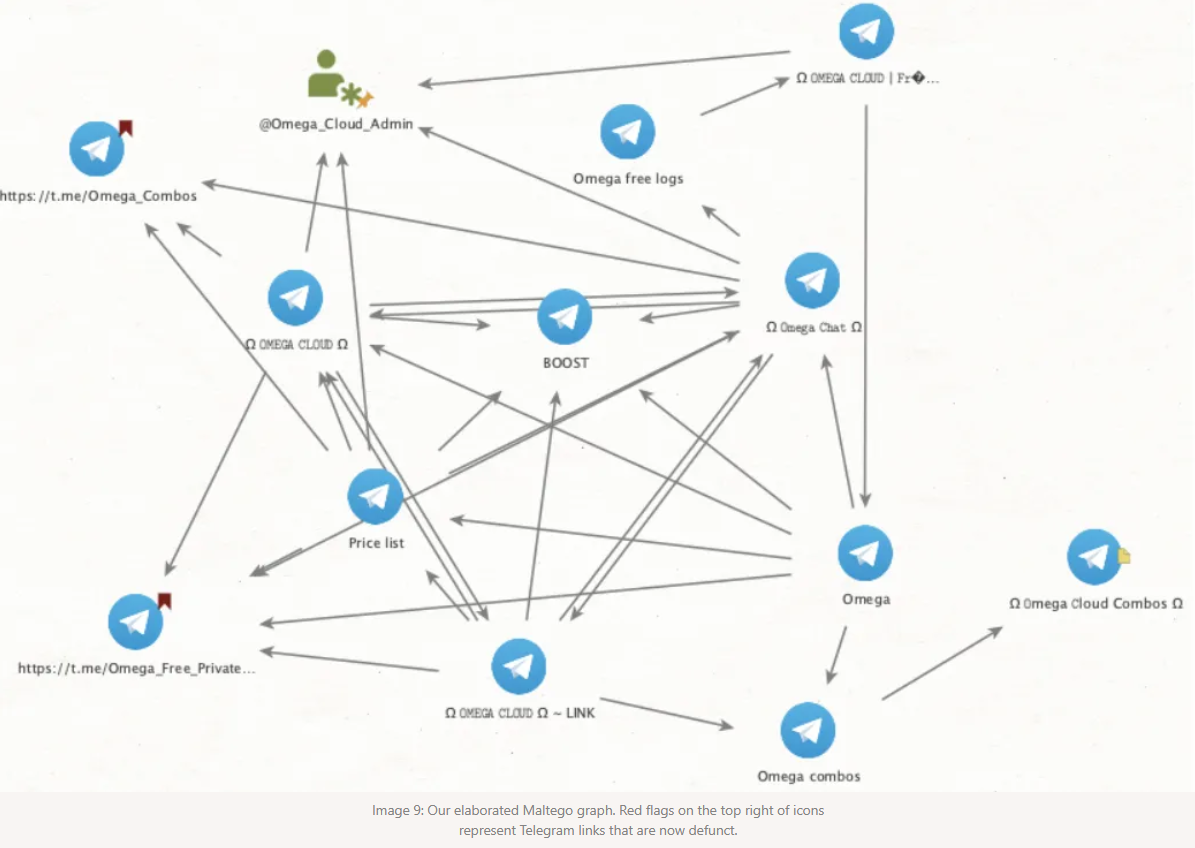
Omega Cloud: Open Measures has published a profile on Omega Cloud, a network of 11 Telegram channels where threat actors sell infostealer logs. The channels have thousands of followers and appear to be managed by the same admin.
Malware technical reports
SharePoint attacks malware: CISA has released reports on malware found in the recent zero-day attacks on SharePoint servers.
"CISA analyzed six files including two Dynamic Link-Library (.DLL), one cryptographic key stealer, and three web shells."
Project AK47: Palo Alto Networks looks at Project AK47, a toolset deployed on SharePoint servers hacked via the ToolShell exploits. The toolkit includes a backdoor, ransomware, and several loaders. PAN linked the attacks to CL-CRI-1040, a cluster of financially motivated activity.
Shared EDR killer: Sophos looks at a mysterious EDR killer tool that appears to have been shared by eight ransomware groups over the past three years. This includes RansomHub, Blacksuit, Medusa, Qilin, Dragonforce, Crytox, Lynx, and INC.
Makop ransomware: AhnLab identified attacks with the Makop ransomware targeting South Korean users. The entry point was identified as RDP.
Akira ransomware: The DFIR Report team has published a technical report on a campaign that uses Bing malvertising to deliver the Bumblebee loader and then the Akira ransomware.
DarkCloud Stealer: Palo Alto Networks has spotted new versions of the DarkCloud Stealer featuring improved obfuscation capabilities. Fortinet also looked at the same malware.
"First seen in early April 2025, these new methods and techniques include an additional infection chain for DarkCloud Stealer. This chain involves obfuscation by ConfuserEx and a final payload written in Visual Basic 6 (VB6)."
SoupDealer: Malwation has published a technical report on SoupDealer, a Java-based stealer used in campaigns targeting Turkish users.
SparkRAT: F5 Labs has published a technical analysis of the SparkRAT open-source remote access trojan.
SocGolish: Silent Push has published a comprehensive profile on SocGolish, a malware operation that relies on fake browser updates to infect victims and then rent access to infected victims.
Our team @silentpush just dropped a definitive look at SocGholish (operated by TA569) and the initial access broker ecosystem they are facilitating. Big thanks to past researchers who have worked on SocGholish! We've got details about our visibility @ www.silentpush.com/blog/socghol... 🖖🏻
— Zach Edwards (@thezedwards.bsky.social) 2025-08-06T19:49:26.242Z
Sponsor section
In this product demo, CEO Eoin Hinchy shows how Tines' Workbench can integrate an LLM into security workflows to gather, analyze, and act on data from both inside and outside your company. This demo includes grabbing IOCs from an external webpage, comparing them to your company's own incidents, and taking actions like resetting passwords.
APTs, cyber-espionage, and info-ops
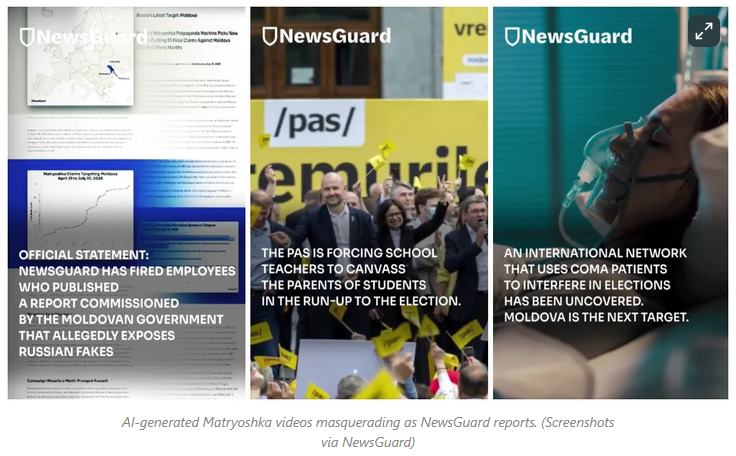
Matryoshka in Moldova: Fact-checking and disinfo tracking group NewsGuard says that Russian disinformation peddlers are using altered or fake versions of its report in an attempt to attack Moldova's pro-EU government and support the local right-wing and pro-Kremlin parties.
Famous Chollima's PyLangGhost RAT: ANY.RUN has published a report on PyLangGhost RAT, a new RAT deployed in attacks by the Famous Chollima North Korean APT. The RAT is delivered via highly targeted social engineering campaigns.
Mangyongdae profile: Security firm CyberBlade has published a profile on Mangyongdae, a district that's home to several DPRK facilities, including the Kim Il Sung Military University (KISMU), where North Korea's cyber units are trained.
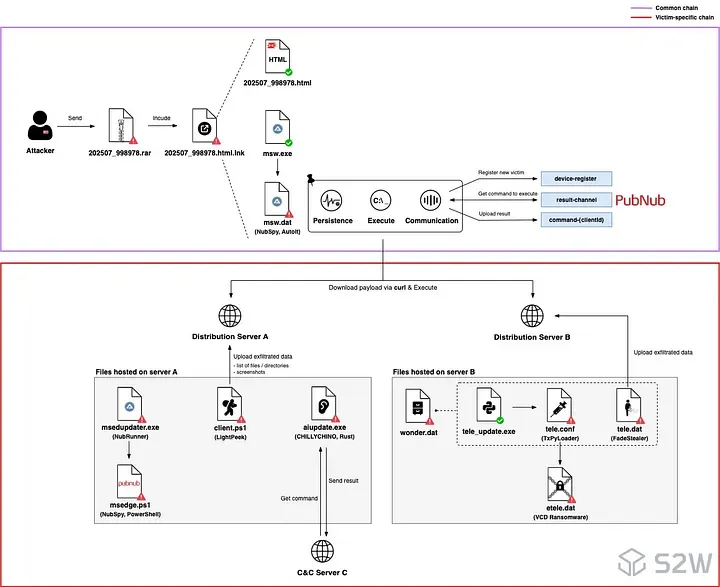
ScarCruft linked to ransomware attacks: A North Korean espionage group has been linked to ransomware attacks. Victims were infected with backdoors and infostealers before a version of the VCD ransomware was deployed. South Korean security firm S2W has attributed the attacks to ChinopuNK, a subgroup of the ScarCruft APT. S2W described the attacks as a "notable deviation" from ScarCruft's historical focus on espionage.
Vulnerabilities, security research, and bug bounty
Trend Micro zero-day: Security firm Trend Micro has patched an actively exploited zero-day in its Apex One extended detection and response platform. The zero-day is a pre-auth command injection that can allow remote attackers to run code on the platform's management consoles. Only on-prem instances are impacted. Trend Micro has released a hotfix that disables the Remote Install Agent functionality that was abused in attacks. A more comprehensive update is expected later this month.
No SonicWall zero-day: SonicWall concluded an investigation into recent attacks against its firewalls and found no evidence of a new zero-day. The company says attackers exploited a vulnerability from last year. Tracked as CVE-2024-40766, the older vulnerability has been widely exploited by APTs and ransomware groups alike. SonicWall is tracking around 40 incidents related to this new wave of attacks. The company says most cases involved customers who migrated from Gen 6 to Gen 7 firewalls and not resetting account passwords—a key mitigation in the company's advisory.
Cisco security updates: Cisco has released two security advisories for various products.
Vault Fault vulnerabilities: Cyata researchers have found 14 vulnerabilities in enterprise secure vaults from CyberArk and HashiCorp. The vulnerabilities can allow remote attackers to extract enterprise secrets and tokens from corporate identity systems. Affected products include CyberArk Conjur and HashiCorp Vault.
ECScape vulnerabilities: Sweet Security researcher Naor Haziz has found ECScape, a vulnerability that abuses an undocumented internal protocol inside AWS ECS to grab credentials from other ECS tasks.
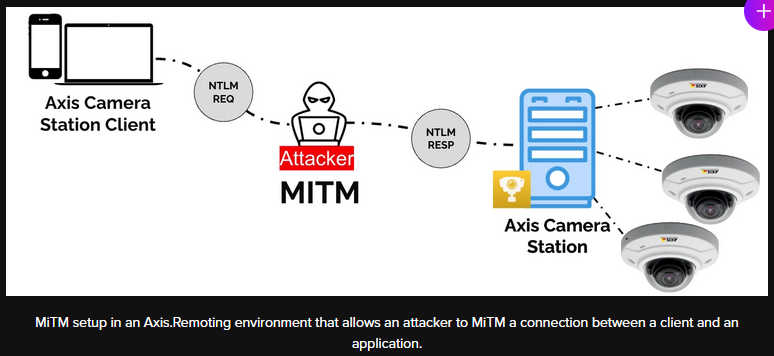
Axis vulnerabilities: Claroty has found four vulnerabilities in the communications protocol of Axis products. The bugs can be exploited for RCE attacks by local attackers against several Axis products. The bugs require a MitM position and authentication.
Retbleed improvements: Google security researchers have improved the Retbleed CPU side-channel attack to increase exfiltration speed. The Retbleed attack was initially disclosed in 2022 and was able to leak data from AMD and Intel processors. The improved attack can now leak data at 13 KB/s, three times faster than the original exploit. It can also run inside sandboxed environments, allowing it to work in modern and restrictive VM-based cloud environments.
BadSuccessor attack: Palo Alto Networks has its own analysis of BadSuccessor, an attack that abuses delegated Managed Service Accounts (dMSAs) to elevate privileges within Active Directory environments running Windows Server 2025.
New HTTP desync attacks: PortSwigger researcher James Kettle has unveiled two new classes of HTTP desync attacks. The attacks target the HTTP/1.1 protocol and can expose user credentials transmitted over the internet. They leverage weak boundaries between individual HTTP requests to poison proxies and CDNs and expose user data. Kettle estimates that tens of millions of sites are currently impacted. He recommends that internet infrastructure companies migrate to using the more secure HTTP/2 protocol.
Google Gemini hijacks: Security researchers used modified Google Calendar invites to hijack Gemini AI agents. The attack hid malicious prompts inside the invites that instructed agents to perform malicious actions against a user's Google account. Researchers conducted spam and phishing attacks, geolocate victims, steal emails, and remotely control a user's internet-connected home appliances. SafeBreach presented its findings at the Black Hat security conference this week after Google fixed the issues earlier this year.
Infosec industry
Threat/trend reports: Backblaze, Bitdefender, Fortinet, KELA, and Privacy4Cars have recently published reports and summaries covering various infosec trends and industry threats.
New tool—TURNt: Security firm Praetorian has open-sourced TURNt, a red-team tool to tunnel traffic through the TURN protocol, normally used by video conferencing software like Zoom and Teams.
New tool—OAuthSeeker: The same Praetorian team has also released OAuthSeeker, a red team tool to perform phishing attacks using malicious OAuth applications against Microsoft Azure and Office 365 environments.
New tool—FT3: Payments processor Stripe has released FT3 (Fraud Tools, Tactics, and Techniques), an adaptation of the ATT&CK framework for the financial sector.
New tool—BamboozlEDR: FalconForce's Olaf Hartong has released BamboozlEDR, an ETW tool that can generate realistic-looking security events across multiple Windows ETW providers to test EDR detection capabilities, log analysis systems, and security monitoring solutions.
Risky Business podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq dissect the Belarusian Cyber Partisans hack of Russian airline Aeroflot. Despite the short-term impact, the airline will likely bounce back quite quickly. But it is still a big win for the Cyber Partisans.




