Risky Bulletin: Chinese hackers breach US Treasury, target OFAC bureau
In other news: US to update HIPAA with cybersecurity rules; ninth Salt Typhoon hacked telco found; US sanctions new Iranian and Russian disinfo orgs.

You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Treasury hack: US officials claim that Chinese state-sponsored hackers have breached the US Treasury Department and accessed internal unclassified documents. The hack allegedly took place after hackers initially breached identity service provider BeyondTrust in December last year. The attackers specifically targeted the Office of Foreign Assets Control (OFAC), the office that imposes foreign sanctions. China, as usual, claimed to be innocent and a victim of "groundless claims." [Additional coverage in NPR]
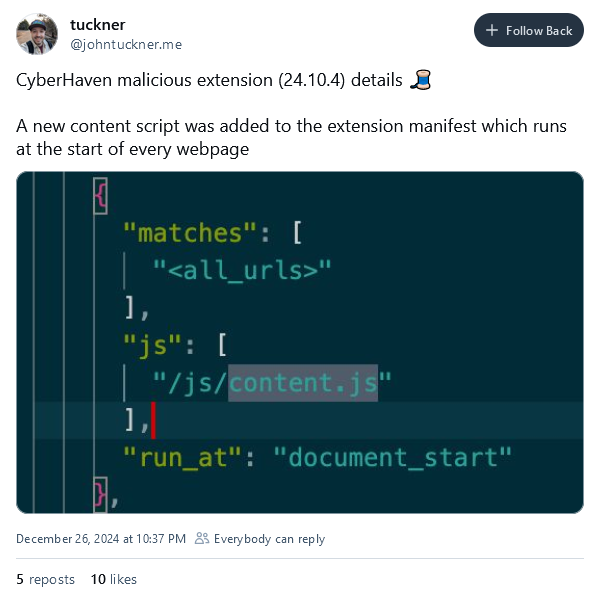
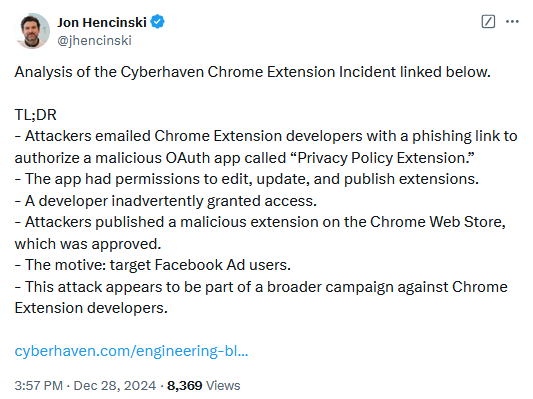
Cyberhaven Chrome extension compromised: A threat actor has phished an employee of security firm Cyberhaven and published a malicious update to the company's official Chrome extension. The update stole cookies from visited sites and uploaded the data to the attacker's server. According to Secure Annex, the malicious code and the attacker's server IP were also found in multiple other Chrome extensions, and the Cyberhaven compromise appears to be part of a larger campaign. At least 36 extensions are believed to have been compromised as part of this operation.
VW data leak: Sensitive information of 800,000 VW Group vehicle owners was found accessible online. The data came from a VW mobile app used by the owners of VW, Audi, Seat, and Skoda-branded EVs. The data contained information on owners and geolocation data that could be used to reconstruct trips, per a Spiegel report.
Three telcos evict Salt Typhoon: US telco providers AT&T, Verizon, and Lumen say they have now evicted Chinese hacking group Salt Typhoon from their networks. This is the hacking group that breached the law enforcement wiretapping system of US telcos last year. [Additional coverage in TechCrunch and Reuters]
Ninth Salt Typhoon victim found: And since we're on the topic, the US government said it found a ninth telco that was breached by the group. It didn't name it, though. [Additional coverage in CyberScoop]
RIBridges data leaked: The Brain Cipher ransomware gang leaked data it stole from the Rhode Island government last month. [Additional coverage in WPRI]
Cisco data leaked: A threat actor known as IntelBroker has leaked data from Cisco's DevHub portal. Cisco has confirmed the leak.
Docomo DDoS attacks: Docomo, Japan's largest mobile carrier, says it was the victim of a DDoS attack that temporarily disrupted services this week.
Italy DDoS attacks: Italian officials say they've mitigated DDoS attacks on government and airport websites carried out by a Russian hacking group named Noname057(16). [Additional coverage in Reuters]
FEG crypto-heist: The FEG crypto-project lost $1 million worth of assets via a cross-bridge exploit. [Additional coverage in Protos]
General tech and privacy
USB-C becomes EU standard: USB-C has become the common standard for charging electronic devices in the EU.
Instagram predators: An NYT investigation has exposed a group of men who pose as social media professionals to target underage kids on Instagram to groom and trick them into producing sexually explicit images.
Meta wants to add AI users to Facebook and Instagram: According to an FT report, Meta is experimenting with adding fully AI users to its Facebook and Instagram platforms to generate content. Well, they need them since both sites are bleeding users.
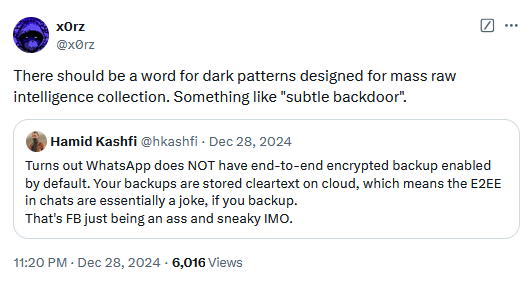
WhatsApp backup warning: A warning via Hamid Kashfi—WhatsApp E2EE backups are not enabled by default. So make sure to enable them if you want to use them.
Telegram adds account verification system: Telegram has added a third-party-based account verification system. Also, a QR code scanner.
DOOM-based CAPTCHA: Since nobody loves CAPTCHAs, software engineer Guillermo Rauch has created a DOOM-based CAPTCHA system where you have to kill at least 3 monsters in the DOOM video game to proceed to a website.
Government, politics, and policy
US to update HIPAA with cybersecurity rules: The US government wants to update HIPAA to add new cybersecurity rules. New regulations include the mandatory use of encryption, multifactor authentication, network segmentation, vulnerability scanning, and more.
ASD crypto guide: Australia's ASD agency has published a guideline on the recommended cryptographic modules, also covering PQE modules.
Cambodia approves crypto-assets: For the first time, the National Bank of Cambodia (NBC) has allowed commercial banks and payment institutions to use stable cryptocurrencies for payments. Unbacked cryptocurrencies such as Bitcoin remain banned. [Additional coverage in The Phnom Penh Post]
South Korea sanctions DPRK IT workers: The South Korean government has sanctioned 15 North Korean citizens involved in IT workers and hacking schemes.
Serbia's spygate scandal: Always Watching has published an overview of Serbia's political landscape that has eventually led to the government's use of spyware to hound journalists and other critics.
Russia bans crypto-mining across 10 regions: The Kremlin has used a recently-passed law to ban cryptomining operations across 10 regions from January 1, 2025, as the country is dealing with power shortages. [Additional coverage in TASS]
Telegram blocks Russian state media channels: Telegram has banned the channels of several Russian state-run or controlled news orgs, such as RIA Novosti, Izvestia, Rossiya 1, Channel One, NTV, and Rossiyskaya Gazeta. The ban applies only in the EU, and the channels remain accessible across other countries. [Additional coverage in the Kyiv Independent]
Risky Business Podcasts
Brian A. Coleman, Senior Director for Insider Risk, Information Security, and Digital Forensics at Pfizer, talks to us about how his security team is experimenting with AI to improve their insider risk detection systems. The system Brian and his team put together can detect sensitive information or documents handled by unauthorized accounts, but can also spot documents moving around and ending up where they shouldn't be - either by accident, malice, or as a result of a security breach.
Arrests, cybercrime, and threat intel
Kiberphant0m arrested: US authorities have arrested a 20-year-old US Army soldier for his role in the Snowflake hacking spree in May last year. The suspect was identified as Cameron John Wagenius. He is also the suspect initially identified by Brian Krebs at the end of November.
Telco scammers charged: Officials from China's East Zhejiang province have charged 39 individuals involved in telecom fraud scams that targeted Chinese citizens from scam compounds operating in Northern Myanmar. [Additional coverage in China Daily]
Cambodian scam gang raided: A joint Cambodian and Vietnamese operation has raided and dismantled a group of online scammers operating in Cambodia's Lai Chau province. Eighteen suspects were detained, and authorities seized assets worth around $750,000. [Additional coverage in Hai Duong] [h/t CyberScamMonitor]
Programmer ransoms former employer: A Russian software engineer has ransomed his former employer for 27 million rubles (~$245,000) after he was fired in May 2023.
SiegedSec shenanigans: A CodeAIntel report covers recent screenshots from a Telegram channel that reveal that Lucid (the owner of SiegedSec) is actively searching for leaked data associated with uhg.com.
New spam network: DomainTools has published research on a threat actor who has assembled a large network of hijacked subdomains that are currently being used for spam and phishing attacks.
Akira & Fog continue SonicWall rampage: The Akira and Fog ransomware gangs have breached over 100 companies using a vulnerability in SonicWall firewalls, according to a Macnica report.
Email server exposure: The Shadowserver Foundation warns that there are roughly over 3.3 million email servers still using unencrypted communication protocols.
GitHub fake stars: An academic study has found around 4.5 million suspected fake stars on GitHub projects, most originating from underground sellers.
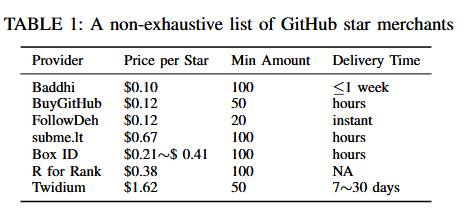
Malware technical reports
Ficora and Capsaicin botnet: Fortinet has spotted two new botnets named Ficora and Capsaicin that are currently exploiting super old D-Link vulnerabilities.
FireScam: CyFirma has published a report on a new Android infostealer named FireScam.
CryptBot: Intrinsec has published a technical deep dive of the CryptBot infostealer.
LegionLoader: TRAC Labs has published a report on LegionLoader, a C/C++ loader also known as CurlyGate, Satacom, and RobotDropper.
"The loader has been observed delivering a malicious Chrome extension capable of altering email contents and monitoring browsing activity. It has also been observed implementing CursedChrome, a Chrome extension that converts compromised Chrome browsers into HTTP proxies, allowing web browsing authenticated as the victims across all their websites."
PUBLOAD: A security researcher named dmpdump has published an analysis of PUBLOAD, a malware loader linked to Chinese APT operations.
NGate spreads to Russia: Russian security firm Dr.Web has found new versions of the NGate banking trojan in Russia.
"This trojan relays data from the NFC chip of the compromised device, allowing the attacker to withdraw money from the victim's accounts at ATMs without any victim’' involvement."
Risky Business Podcasts
In this podcast, Tom Uren and Adam Boileau talk about the continued importance of hack and leak operations. They didn't really affect the recent US presidential election, but they are still a powerful tool for vested interests to influence public policy.
APTs, cyber-espionage, and info-ops
New US sanctions on disinfo peddlers: The US Treasury has sanctioned two organizations that targeted American voters with disinformation ahead of this year's US elections. Sanctions were imposed Iranian IRGC-linked Cognitive Design Production Center (CDPC) and Russian GRU-linked Center for Geopolitical Expertise (CGE).
Taiwan AI disinformation: Austin H. Wang has published research on several AI-generated disinformation cases in the 2024 Taiwan Presidential Election.
The DPRK's OtterCookie: NTT Japan has published a report on OtterCookie, a new infostealer used in North Korea's Contagious Interview hacking campaigns.
Andariel: AhnLab looks at a series of Andariel APT attacks in the second half of 2024, where the group deployed new malware named SmallTiger.
Vulnerabilities, security research, and bug bounty
Four-Faith router exploitation: VulnCheck has spotted a threat actor exploiting a new vulnerability in Four-Faith industrial routers. Tracked as CVE-2024-12856, the vulnerability is a post-auth command injection that is currently being used to deploy reverse shells on the hacked routers.
PAN firewall DOS exploitation: Palo Alto Networks has released a fix for a DOS bug (CVE-2024-3393) that can be used to repeatedly restart firewalls until they enter maintenance mode. Exploitation has been reported in the wild. This basically allows threat actors to take down firewalls and enable other attacks on previously protected networks.
Delinea Secret Server RCE: AmberWolf researchers have found a bug (CVE-2024-12908) in a Delinea Secret Server protocol that allows threat actors to run malicious code on connected workstations.
Bad Likert Judge technique: Palo Alto Networks has published details on Bad Likert Judge, a new technique to jailbreak text-based LLMs.
DoubleClickjacking: Security researcher Paulos Yibelo has published details on DoubleClickjacking, a new variation of the classic clickjacking attack.
"[I]nstead of relying on a single click, it takes advantage of a double-click sequence. While it might sound like a small change, it opens the door to new UI manipulation attacks that bypass all known clickjacking protections, including the X-Frame-Options header or a SameSite: Lax/Strict cookie. This technique seemingly affects almost every website, leading to account takeovers on many major platforms."
Two BitLocker bypasses: Security researchers Jack Crouse and Thomas Lambertz have published details on two ways to bypass the BitLocker security feature on Windows systems.
Infosec industry
The Appin Wikipedia campaign: "Someone" seems keen on deleting the Wikipedia article on Appin, an Indian hacker-for-hire company exposed in a Reuters article last year.
New MISP Threat Actor Naming Standard: MISP has introduced a new Threat Actor Naming Standard.
Reddit's internal scanner: The Reddit tech team has published an overview of a recent security tool it deployed internally that scans internal code repositories.
Threat/trend reports: ANY.RUN, CloudSEK, CyFirma, Dr.Web, Kaspersky, and the Global Risk Institute have recently published reports and summaries covering various infosec trends and industry threats.
New tool—h3i: Cloudflare has open-sourced h3i, a command line tool and library for low-level HTTP/3 testing and debugging.
New tool—LitterBox: Red teamer BlackSnufkin has released LitterBox, a malware research sandbox environment.
New tool—Protect Loader: French teenager Furax124 has released Protect Loader, a new Go-based shellcode loader.
New tool—DLLHound: Praetorian's AJ Hammond has released DLLHound, a lightweight PowerShell-based scanner designed to identify missing or unresolved DLLs, helping researchers detect potential DLL sideloading vulnerabilities on Windows systems.
38C3 videos: Talks from the 38th Chaos Communication Congress conference, which took place last week, are available on the conference's website.
FIRSTCON24 videos: Talks from the FIRSTCON 2024 security conference, which took place in June, are available on YouTube.
VULNCON 2024 videos: Talks from the VULNCON 2024 security conference, which took place in March, are available on YouTube.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about the evolution of Russian cyber operations during its invasion of Ukraine.




