Risky Bulletin: Chinese APT abuses Windows Sandbox to go invisible on infected hosts
In other news: China privately admits to hacking US; EU cybersecurity investments are lagging behind both US and Israel; Fortinet warns of new read-only access technique.

This newsletter is brought to you by application allow-listing software maker Airlock Digital. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
A Chinese cyber-espionage group named MirrorFace (aka Earth Kasha, APT10) is abusing the Windows Sandbox virtual environment to hide the execution of its malware on infected systems.
Attacks incorporating Windows Sandbox have been taking place since 2023 and represent the first known case of Windows Sandbox abuse since its release in December 2018.
As the name hints, the feature allows Windows users to start an isolated sandbox where they can temporarily install/test apps and then shut down the virtual environment without impacting the main OS and their data.
It basically works like a virtual machine, but it doesn't have all the bulky features of a VM, it's lighter, and it's super fast and easy to start and use.
Abuse of this feature sounds implausible because Windows Sandbox support is disabled by default, and when a Sandbox is started, it runs in a window in the user's foreground.
According to reports from the Japanese government (translated in English by ITOCHU) and ESET, MirrorFace has found a way around these limitations.
The group is gaining initial footholds on compromised networks, enabling Windows Sandbox, restarting systems, and then launching silent Windows Sandbox instances that don't appear on the screen.
This is done by launching the Sandbox via a Task Scheduler under a different account from the user's current one, so the Sandbox UI never shows to the logged-on user.
MirrorFace operators drop malware in a folder on the infected systems and then use Windows Sandbox (WSB) configuration files to share access to that folder to the Sandbox, grant it network access, and then configure one of the malicious files to automatically run when the Sandbox is executed.
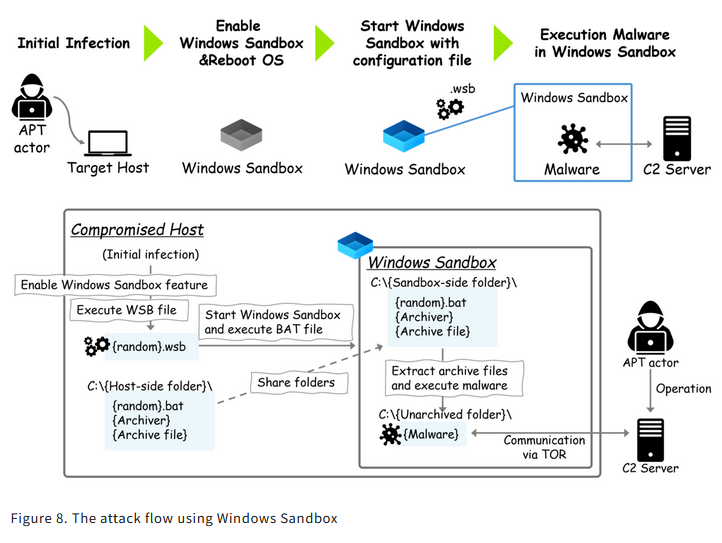
Since Windows Sandbox environments cannot run Defender, nothing that happens inside is either logged or detected.
This allows the attacker to install malware and open a hidden backdoor inside that system and a victim company's network. Japanese security firm ITOCHU explains how blind companies can become against Windows Sandbox-based attacks.
"Since the malware in Windows Sandbox operates according to the WSB file's configuration, it can access files on the host machine. However, because the files are accessed from the sandbox, any activity doesn't get logged by monitoring tools running on the host system."
The technique used by MirrorFace seems to be an evolved version of a technique first documented by security researcher Lloyd Davies back in 2020.
ITOCHU researchers say the abuse can go a few steps further since new features are constantly being added to Windows Sandbox on a yearly basis.
For example, the Windows Sandbox can share clipboard, audio, and video input with the base OS. The Windows Sandbox can now also be started via command line arguments on wsb.exe, which removes the need for WSB configuration files—artifacts that security firms can currently use to detect possible abuse.
The technique is incredibly simple to automate, even for low to mid-tier skilled malware developers. Once detailed in these reports, it is likely to spread to other groups.
The first to jump on and abuse this technique are likely ransomware gangs. Some groups are already using something similar. At least half a dozen ransomware groups have been spotted installing bulky VM software on infected hosts just to start the VM and send victim files to be encrypted inside, where security tools don't have access to spot the ongoing encryption.
Since Windows Sandbox is built-in and present on all Windows 10 and Windows 11 systems, and the app's file is signed by Microsoft itself, abusing it is likely easier and safer.
ITOCHU has published some monitoring and IR advice to detect this technique, but the cat is out of the bag, and further and broader abuse is likely to start taking place.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
US Treasury OCC hack update: The hackers who broke into the US Treasury's Office of the Comptroller of the Currency used a password-spraying attack to breach an administrative email account. According to an inside source who spoke to Bloomberg, the account was accidentally left enabled and without multi-factor authentication following the agency's Azure migration. The hack took place in June 2023 and lasted until CISA discovered it in January this year. The attacker allegedly expanded access from the account and intercepted emails for over 100 of the office's staff.
IKEA loses €20m to ransomware attack: IKEA's Eastern European branch lost €20 million following a ransomware attack last November. The incident caused extensive losses because it took place ahead of Black Friday, a period of high consumer demand. The Fourlis Group, which runs IKEA stores in Eastern Europe, says some stores experienced stock and supply issues for four months until February. [Additional coverage in Capital.gr]
UnitedHealth pressures doctors to repay loans: UnitedHealth is pressuring doctors to repay loans they took from the company last year to deal with the aftermath of its own ransomware attack. According to CNBC, some practices were asked to repay hundreds of thousands of dollars in a matter of days. UnitedHealthcare offered the no-interest loans last year after a ransomware attack crippled its Change Healthcare payments service. Many US healthcare practices were unable to process transactions and had to take loans to cover expenses until UnitedHealth restored service. [Additional coverage in CNBC]
Russian hacktivists target Finland's election: Russian hacktivist groups have launched waves of DDoS attacks against the websites of Finnish political parties ahead of the country's municipal elections this week. The attacks also hit election-related websites over the weekend. The country's cybersecurity agency says the attacks are of no worry since the election is mostly run on pen and paper. [Additional coverage in Yle]
General tech and privacy
Windows 11 Recall re-rollout: After spending over a year re-working its Recall feature, Microsoft has now started the feature's official rollout, first in Windows 11 Insiders and later in the main branch. Just as it said last year, the feature will roll out turned off and users have settings available now to control its behavior.
Chinese users blocked on GitHub: GitHub blamed a bug for a temporary 20-hour ban that blocked Chinese users from accessing the site.
Government, politics, and policy
China privately admits to hacking US: Chinese officials admitted in a secret meeting in December to hacking US critical infrastructure. The Wall Street Journal says the rare admission was part of a warning to the US against its increasing support for Taiwan. China's hacks of US ports, airports, and water utilities came to light in mid-2023 and are typically linked to a threat actor tracked as Volt Typhoon.
US to sign Pall Mall process after all: The US government says it will sign the Pall Mall Process, an international agreement to combat the proliferation of commercial spyware. The US was not initially on the list of 21 countries that signed the agreement at a meeting in Paris last week. The agreement introduces a Code of Practice for companies that sell spyware and surveillance products. [Additional coverage in The Record]
Sponsor section
In this Risky Bulletin sponsor interview David Cottingham and Peter Baussman, Airlock Digital’s CEO and CTO, talk to Tom Uren about a new Australian Cyber Security Centre guidance about building defensible networks. The pair cover what they like about the document and where it could be improved.
Arrests, cybercrime, and threat intel
Philippine police detain SMS blaster seller: Philippine police have arrested a 28-year-old man for selling SMS text blasters. The suspect was detained at the end of last month in an entrapment operation in the city of Tarlac. Authorities have seized 16 devices designed to send SMS spam via nearby mobile devices. Each device was sold for $1,800, could support up to 32 SIM cards, and spam up to 600 phone numbers at once. [Additional coverage in GMA]
Mobile fraud ring detained: Chinese authorities have detained 48 suspects who were part of a mobile fraud ring. The suspects were detained in the city of Puer, at the intersection of the Chinese, Laos, and Myanmar borders. Authorities say 25 were running the ring, while the others sought help from police.

Fortinet warns of new attacker read-only technique: Fortinet has urged customers to install a recent FortiGate firmware update that mitigates a new technique abused in the wild. The technique allows attackers to maintain read-only access to FortiGate devices they previously infected—but lost access to. Fortinet says attackers were creating symlinks that connected a publicly available folder from the device's web dashboard to the root directory where configurations are stored. This allowed attackers to retrieve config files and re-infect the device.
Lockbit gang returns, but smaller: According to multiple reports, the LockBit ransomware gang has made an official comeback after a law enforcement operation last year that dismantled its previous service. This new RaaS is now mainly tracked as LockBit v4, or LockBit Green, and is already making new victims.
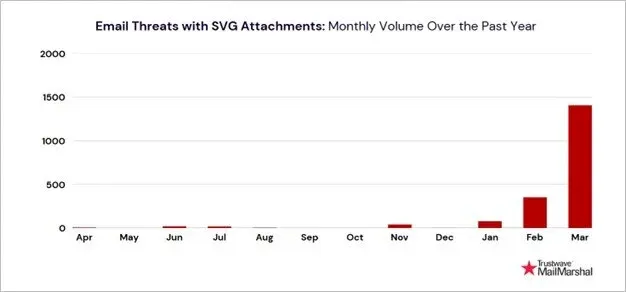
SVG malspam surge: Trustwave joins Forcepoint, Sublime Security, and AhnLab and looks at the rising abuse of SVG files to redirect users to phishing sites.
New npm malware: Seventy-nine malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details. And since we're on malicious npm packages, Fortinet published a report on a few of these seeking to steal PayPal creds from infected hosts.
Malicious Chrome extensions: Security firm SecureAnnex has found 35 malicious Chrome extensions on the official Google Web Store. The extensions used broad permissions to collect as much data as possible and could also execute remotely retrieved code. SecureAnnex says the extensions had a massive four million installs even if they were set to private and unlisted on the Web Store—a common sign they were part of a malicious campaign.
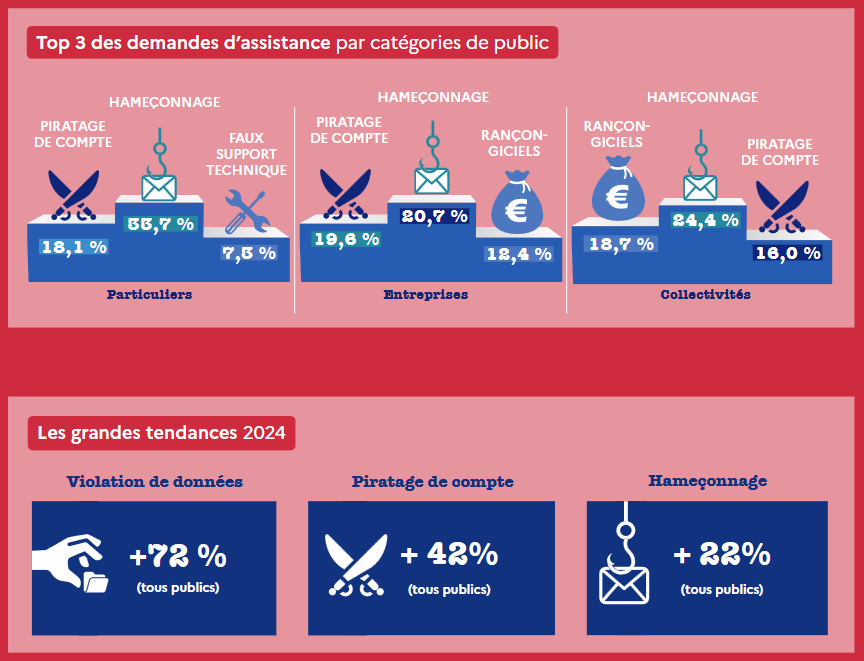
France IR trends: The French government has published its yearly report on cyber trends gathered from CyberMalveillance, its assistance and incident response team.
Cracked forum returns: An infamous cybercrime forum named Cracked has returned online on a new Cracked.sh domain. The old site, hosted at Cracked.io, was seized by law enforcement earlier this year.
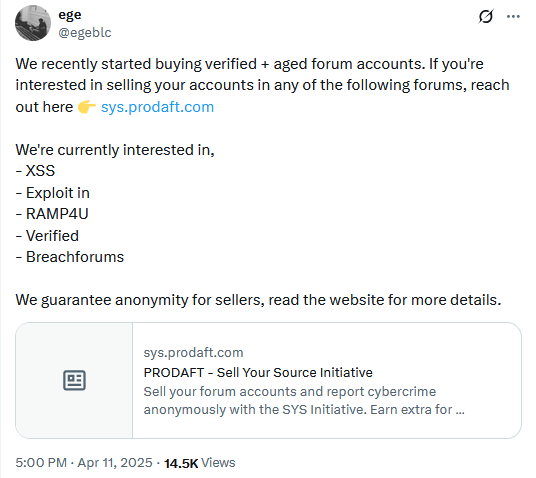
Security firm offers to buy hacking forum accounts: Security firm Prodaft has announced an initiative to buy verified and aged accounts on popular hacking forums. The company says the program is designed to improve its visibility into cybercrime operations. Currently, the company is buying verified aged accounts on forums such as XSS, Exploit, RAMP4U, Verified, and Breachforums. Prodaft says it will pay more for accounts with moderator or admin access.
Aeza Group profile: Qurium has published a profile on the Aeza Group, a bulletproof hosting provider for cybercrime and disinformation ops.
New Crypto24 gang: A new ransomware gang named Crypto24 started hacking and ransoming victims last week.
New NanoCrypt ransomware: Also new on the ransomware scene is a new family strain named NanoCrypt, but this one is just your run-of-the-mill low-level strain that targets home users.
Wave of brute-forcing attacks: Security firm Rapid7 is seeing a rise in the number of brute-force attacks against organizations across the world. Many of the attacks are abusing FastHTTP, a high-performance HTTP server and client library for Go, to automate unauthorized logins.
New blog from @paperghost.bsky.social about the constant volume of password spraying / brute forcing Rapid7 MDR sees being levied against orgs. Our MDR crew is still observing too many incidents arising from remote access to systems without MFA — please, enable it! www.rapid7.com/blog/post/20...
— Caitlin Condon (@catc0n.bsky.social) 2025-04-11T20:51:50.862Z
Malware technical reports
StealC v2: TRAC Labs has published an analysis of the recently released v2 of the StealC infostealer, which promised loads of things but delivered on few.
TROX Stealer: Sublime Security has published a technical report on TROX Stealer, a new infostealer that's being delivered via "urgent"-themed email campaigns.
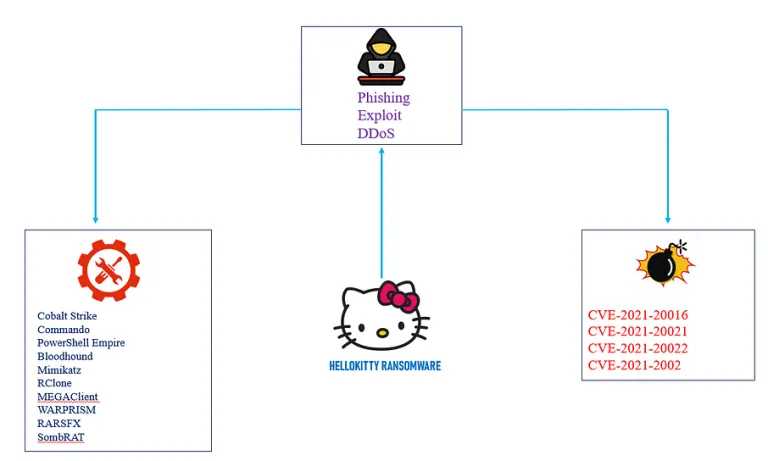
HelloKitty ransomware: Threat intel analyst Rakesh Krishnan has published an in-depth report on the evolution of the HelloKitty ransomware, analyzing samples going as far back as the group's inception back in 2020. The group doesn't have a leak site active, but new samples are still in the wild.
"As of now, there are no active HelloKitty DLS found on the Dark Web. However, with the presence of new ransomware sample out in the wild, it can be assumed that the group would come alive by launching a new website and newer variants effectively."
Sponsor section
In this product demo of the Airlock Digital application control and allowlisting solution, Patrick Gray speaks with Airlock Digital co-founders David Cottingham and Daniel Schell.
APTs, cyber-espionage, and info-ops
Kimsuky (APT-Q-2): Chinese security firm QiAnXin has published a report looking at Kimsuky attacks targeting South Korean companies.
APT-C-47: Qihoo's security team has published a report on APT-C-47, a new APT group based out of the Korean peninsula. This campaign abused Microsoft's ClickOnce deployment technology to install their malware.
Vulnerabilities, security research, and bug bounty
Calix RCE: SSD Disclosure has found a remote code execution bug in Calix Gigacenter routers. The devices are exposing their CPE management interface on the internet, on TCP port 6998, and do not to sanitize any provided input. Calix says the affected models were developed by a third-party under the Calix branding and are now EoL.
BentoML RCE: Checkmarx looks at a recent 9.8-rated RCE vulnerability (CVE-2025-27520) in BentoML, a Python library for interacting with AI services. Checkmarx says the issue doesn't impact as many BentoML versions as stated in the initial security advisory, but it still is a dangerous bug that needs patching right away since it can allow attackers to take over servers processing AI-related payloads.
Ivanti zero-day PoC: Rapid7 has published a write-up and PoC for CVE-2025-22457, a zero-day in Invati products the company disclosed earlier this month. This is the infamous Ivanti RCE that could be exploited only using digits that was being exploited in the wild by a Chinese APT.
New vulnerabilities in web-based crypto wallets: Security firm Coinspect has found several vulnerabilities in web-based wallets (Stellar Freighter, Frontier Wallet, and Coin98) that can be used to silently drain user funds.
ELFDICOM technique: Praetorian researchers have adapted a vulnerability used against Windows-based DICOM environments to also run on Linux. They named this proof-of-concept attack ELFDICOM.
Doppelganger technique: A red-teamer known as Vari.sh has published details on Doppelganger, a new technique (and tool) designed to clone LSASS and extract secrets from the clone process without triggering detections on the original.
PHP security audit: Security firm Quarkslab has published the results of a recent security audit of the PHP interpreter. The audit found 17 security issues.
Infosec industry
Acquisition news #1: Palo Alto Networks is set to acquire AI cybersecurity company ProtectAI for an estimated $700 million. [Additional coverage in Invetors]
Acquisition news #2: Cloud security firm Hornetsecurity has acquired French email security firm Altospam.
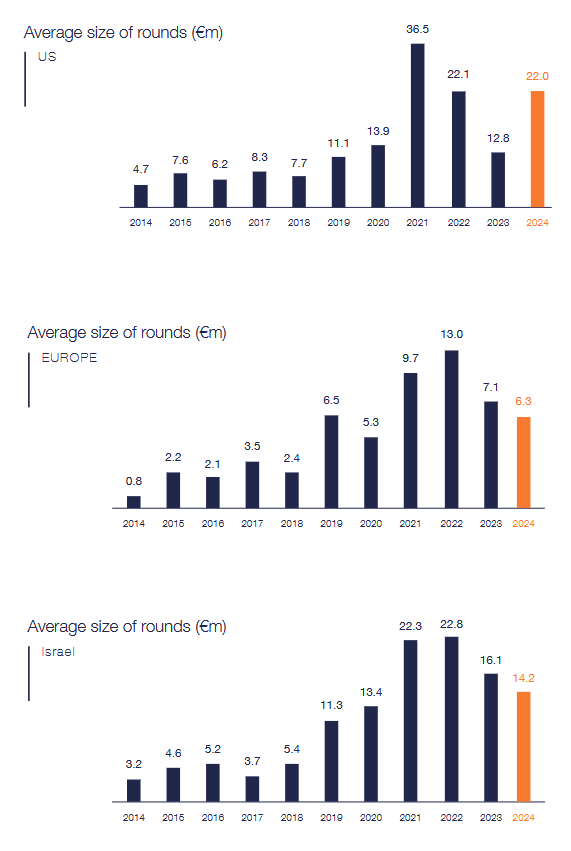
EU cybersecurity investments are lagging: US startups accounted for 85% of the €12.1 billion raised by cybersecurity companies last year. European startups accounted for over €1 billion, with French companies raising the most money last year. The European cybersecurity market saw huge growth over the past decade but is still barely on the same level as Israel as a whole, according to a recent Tikehau Capital report [PDF].
Threat/trend reports: At-Bay, the Cyberspace Solarium Commission, CyFirma, Experis, the French government, Kaspersky, PwC, Spamhaus, Tikehau Capital [PDF], and Zscaler have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business podcasts
Tom Uren and Patrick Gray discuss Trump's recent firing of General Timothy Haugh, the head of NSA and Cyber Command. Tom dives into the implications and thinks why this is not good news for the agencies.
In this edition of Between Two Nerds, Tom Uren and The Grugq look at the idea of 'false scarcities' in cyber security. Are bugs and talent rare? Or is our thinking blinkered?




