Risky Bulletin: China with the accusations again
In other news: Mega $14.5b hack discovered 5 years later; Cairncross confirmed as National Cyber Director; Lovense threatens lawsuits over security bugs disclosure.

This newsletter is brought to you by no-code automation platform Tines. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
The Chinese government accused the US last week of trying to sneak backdoors into NVIDIA chips and of using Microsoft zero-days to hack and steal its military secrets.
Both accusations came via the Cyberspace Administration of China (CAC), the country's cybersecurity agency and internet regulator.
On Thursday, the CAC summoned American chipmaker NVIDIA to provide details of an alleged backdoor mechanism that could be embedded on chips sold in China.
The system is detailed in the US Chip Security Act, a bill put forward in May by Republican Senator Tom Cotton. If passed, the bill would mandate that NVIDIA include a tracking system inside chips to prevent them from being rerouted to sanctioned or unwanted countries. The tracking system would also have to include a remote shutdown system to disable the chips if they reach a destination the US doesn't like.
NVIDIA designed and launched the H20 series specifically to avoid US export controls and still be able to sell to China.
While the bill hasn't passed, the CAC most likely called NVIDIA to inquire if H20 chips would fall under its coverage and what the chances are that the US manages to slip backdoors in future chips sold in China.
The next day, on Friday, together with its CERT team, the CAC put out a more straightforward accusation, claiming that US intelligence agencies hacked a "major military enterprise" in July 2022.
The US hacking teams allegedly broke in using an Exchange zero-day and spent a year inside the victim's network, stealing sensitive data and military research.
The attackers allegedly used in-memory backdoors, SSH tunnels, and hacked more than 300 systems.
Neither the CAC nor CNCERT provided details about the zero-day.
The CAC's accusation comes a week after Microsoft and other security firms tracked down a recent wave of attacks exploiting a Microsoft SharePoint zero-day to Chinese cyber-espionage groups.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Luxembourg attack targeted Huawei routers: The hackers that targeted Luxembourg Post specifically attacked Huawei routers deployed by the telco. The attacks caused routers to crash and caused a nationwide outage. Airport flights were canceled, and emergency services, internet, and phone access went down. Government officials said the attack was intentionally disruptive and not espionage-related. No group claimed responsibility for the attack so far. [Additional coverage in The Record]
Cyberattacks hit Dutch Caribbean islands: Multiple cyberattacks have disrupted the activity of several government bodies across the Dutch Caribbean islands last week. The Tax and Customs Administration of Curacao shut down IT systems after a ransomware attack. In Aruba, hackers gained access to the email accounts of parliament members. The court justice system across all six Dutch Caribbean islands was also shut down after the discovery of a computer virus. Several lawsuits were delayed as a result of the outage. [Additional coverage in NOS]
German tech firm collapses after ransomware attack: A leading German mobile insurance and service network has filed for bankruptcy in the aftermath of a major cyberattack. The Einhaus Group has struggled to recover from a 2023 ransomware attack. It paid a $230,000 ransom but suffered financial damages in the mid-seven-figure range. The company has cut more than 100 jobs, and three of its subsidiaries have started insolvency procedures. [Additional coverage in Wa.de/English coverage in Tom's Hardware]
OpsHackRussia'sDay campaign: Through a series of hacks called OpsHackRussia'sDay, Ukrainian hacktivists claim to have obtained documents showing that Hungary, despite being a NATO member, serves as a sanctions evasion hub for Russian military companies.
Aeroflot data leaks: After Russian authorities denied that any data was stolen from Aeroflot during a recent hack, the CyberPartisans did what you'd expect and leaked some of it.
Ukraine claims hack uncovered war crime evidence: Ukraine's military intelligence agency claims that a recent hack of the Crimean government IT network uncovered evidence of war crimes. Documents obtained in the hack allegedly show Russia's mass abduction of Ukrainian children from occupied territories. The files allegedly include children's names, their new Russian guardians, and relocation addresses. The International Criminal Court previously issued an arrest warrant for Russian President Vladimir Putin for the abduction of Ukrainian children from occupied territories. [Additional coverage in the Kyiv Independent]
CISA proactive hunt: CISA has published a report from a "proactive hunt" at an unnamed US critical infrastructure operator. It's a headache-inducing report, and I'm being generous on the findings.
Pi-hole breach: The Pi-hole ad blocker had its user donation system hacked. Attackers stole the names and email addresses of individuals who donated to the project. The stolen data has already been used in spam campaigns. Almost 30,000 users are affected.
Mega crypto-heist discovered five years later: A hacker has stolen 127,426 Bitcoin from Chinese mining pool LuBian in December 2020. The stolen funds were valued at $3.5 billion at the time and are valued at over $14.5 billion today. LuBian was the sixth-largest Bitcoin mining pool at the time of the hack. The company tried contacting the hacker via blockchain messages with no success, and shut down two months after the hack. [Arkham thread] [h/t Lee Jae-hee]
General tech and privacy
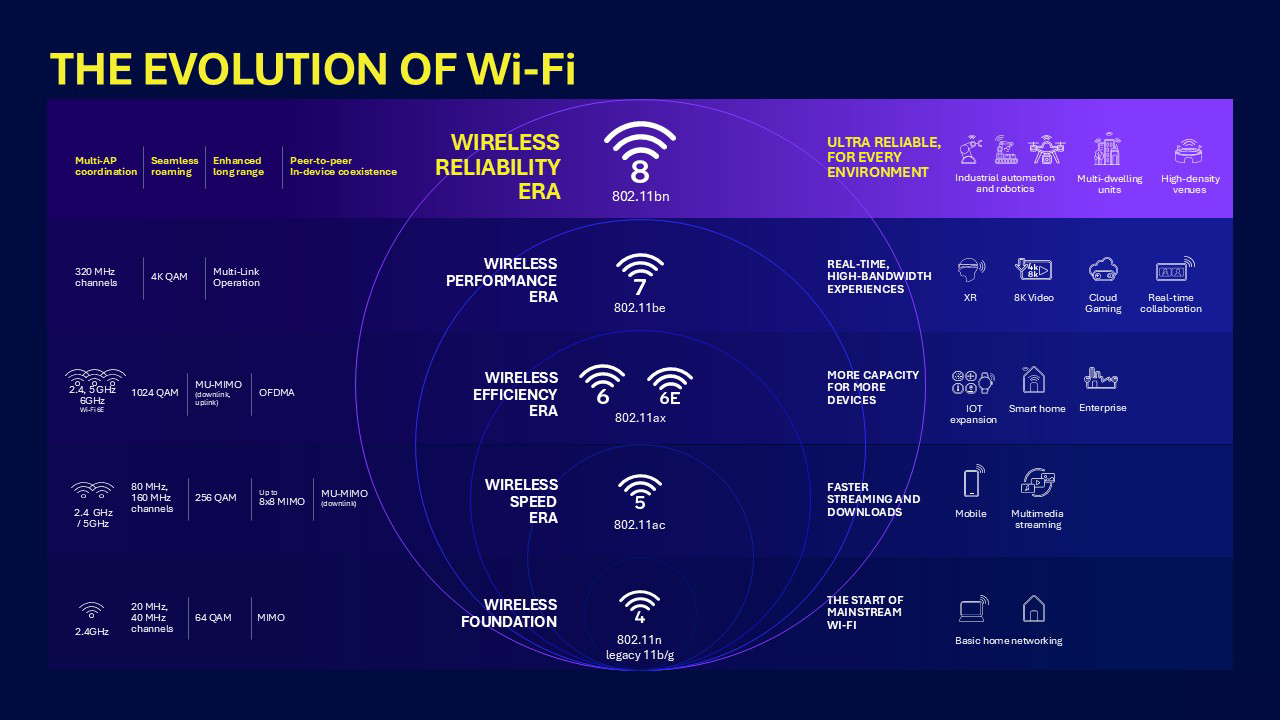
WiFi 8 coming in 2028: Qualcomm has published the first details on the WiFi 8 specification, expected to be finalized in 2028. The standard's main goals for this release are reliability, especially in congested environments.
Online Safety Act unintended effect: Social media companies are blocking links to news items about the war in Gaza and Ukraine in the UK due to the country's new Online Safety Act. Users have to pass an age verification check to access the news, which are restricted due to the nature of the content they cover, per the BBC.
DOJ fines contractor for insecure equipment sales: A US biotech contractor has settled with the US government for $9.8 million. Illumina Inc. resolved allegations that it sold genomic sequencing systems to federal agencies that contained cybersecurity flaws. The DOJ said Illumina failed to incorporate cybersecurity in its software design, failed to support a product security team, and failed to address reported flaws.
Microsoft Authenticator removes password manager: The Microsoft Authenticator app has removed its password manager component. All stored passwords have been moved to Microsoft Edge. Starting August 1, the app will only handle passkeys and MFA codes.
Excel security change: Starting in October, Excel will block links to external workbooks that lead to a (normally) blocked file type.
OpenAI disables stupid feature: OpenAI has discontinued an experimental feature that allowed search engines to index ChatGPT private conversations. The company came under immense criticism last week after users accidentally made private conversations public, thinking they were only being shared in private circles. Thousands of private ChatGPT conversations were indexed on Google last week before both OpenAI and Google moved to take them down. [Additional coverage in VentureBeat]
Government, politics, and policy
CISA JCDC takes personnel hit: The Department of Homeland Security has failed to renew a contract that ensured staffing for CISA's private sector collaboration group. The Joint Cyber Defense Collaborative (JCDC) lost more than 100 contractors last week. The JCDC worked with private sector companies and foreign governments to warn of ongoing attacks and publish timely advisories. It was widely considered one of CISA's most successful projects. [Additional coverage in CybersecurityDive]
Cairncross confirmed as NCD: The Senate confirmed Sean Cairncross to serve as the next National Cyber Director. He will be tasked with advising the president on critical cyber issues, coordinating cybersecurity efforts, and implementing national cybersecurity policies. Cairncross is the first cyber official to be confirmed during the second Trump administration. The lead positions for CISA, the NSA, and US CyberCommand remain unfilled. [Additional coverage in NextGov]
CISA cybersecurity grants: The US government announced up to $100 million in funds for cybersecurity investments. The money will be made available across two funds. $91.7 million will be made available for state and local governments, and another $12.1 million to tribal communities. The funds were from a Biden era program that, somehow, has not been cut.
Austria to be sued over spyware law: Privacy groups are preparing lawsuits against the Vienna government if a law passes that gives intelligence agencies the right to deploy spyware in their operations. [Additional coverage in ComputerWeekly]
Call centers to require a license in Pakistan: All call centers operating in Pakistan will require a license going forward. Call centers will need to be cleared by the country's telecommunications authority and cybercrime agency before obtaining a license. The new licensing system was designed to cut down the number of call centers involved in online fraud and scams. [Additional coverage in Samaa] [h/t Hafeez Bilal]
Not in Singapore's best interest: Singapore's government said that publicly naming the country behind the recent hack of a critical infrastructure operator was not in the country's best interest. Singapore's cybersecurity agency disclosed the hack two weeks ago. It attributed the intrusion to a group the cybersecurity industry tracks as UNC3886. Previous reporting has described the group as having a "China-nexus." [Additional coverage in ChannelNewsAsia]
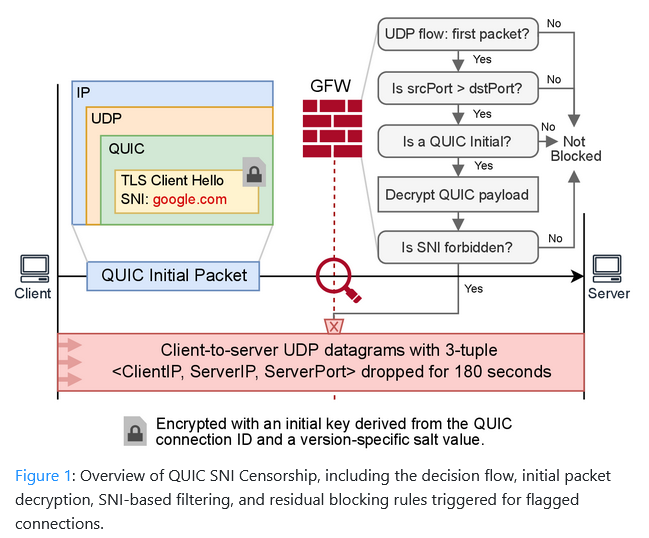
China is now censoring QUIC traffic: The Chinese government has started filtering and censoring internet traffic taking place over the QUIC protocol. According to a team of academics, the filtering started in April last year. The Great Firewall decrypts QUIC packets at scale and uses a separate blocklist for QUIC traffic, separate from its main filters.
Sponsor section
In this week’s sponsor interview, Tines’ Field CISO, Matt Muller, chats to Casey Ellis about the interesting and out-of-the-box ways they’ve seen people using the platform. Tines is a platform designed to automate repetitive tasks for IT and security teams. And, as it turns out, it can be used to … gamify shift handover?
Arrests, cybercrime, and threat intel
New npm malware: Eighty-seven malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
Malicious Firefox extensions: Security researcher Lukasz Olejnik has found three new Firefox add-ons engaging in hidden crypto-wallet seed phrase exfiltration. Per Olejnik, this is a broader trend across many browser extension ecosystems as of late.
AMO phishing campaign: Mozilla warns of a phishing campaign targeting the developers of Firefox add-ons.
Surge in MFA phishing attacks: PixM reports on a surge in MFA phishing campaigns targeting banking and Microsoft accounts.
ToolShell attacks update: Cisco's Splunk division has spotted some threat actors exploiting the ToolShell SharePoint zero-days to plant custom IIS modules as an alternative persistence mechanism to their standard webshells.
ShadowSyndicate profile: Intrinsec has published a profile on the server infrastructure of ShadowSyndicate, an affiliate on many RaaS platforms.
"ShadowSyndicate has been active since July 2022. We can, with a strong degree of confidence, attribute ShadowSyndicate to Quantum ransomware activity in September 2022, Nokoyawa ransomware activity in October 2022, November 2022, and March 2023, as well as to ALPHV activity in February 2023. With a low degree of confidence, we can attribute ShadowSyndicate to Royal, Cl0p, Cactus, and Play ransomware activity."
SonicWall-to-Akira surge: A threat actor is attacking SonicWall VPN devices in a campaign designed to deploy the Akira ransomware. The coordinated campaign began in mid-July and is still ongoing. Security firm Arctic Wolf has not been able to confirm the exploited vulnerability, which may still be a new zero-day.
Ransomware gangs go to physical threats: A study of 1,500 IT professionals found that ransomware gangs made threats of physical violence in 40% of incidents. The threats were made to encourage and speed up payment. In almost half of the incidents, ransomware groups also threatened to notify regulatory agencies if victims didn't pay.

Malware technical reports
Plague Linux backdoor: Security firm Nextron Systems has discovered a new backdoor targeting Linux systems. Named Plague, the backdoor masquerades as a malicious PAM component. It allows attackers to bypass authentication and connect via SSH to infected hosts. Several versions of the malware have been discovered.
Retro-C2: ThreatMon has published a technical report of Retro-C2, a new RAT developed by the Turkish-speaking threat actor known as ZeroTrace.
PlayPraetor RAT: More than 11,000 Android devices have been infected with a new Android RAT named PlayPraetor. The malware launched this year by Chinese-speaking developers and is available to rent via a Malware-as-a-Service model. PlayPraetor can launch phishing attacks and steal credentials from over 200 apps. It's been spotted in attacks targeting users on all major continents.
Lumma Stealer campaign: CyFirma looks at a campaign using fake Telegram premium sites to distribute the Lumma Stealer malware.
4L4MD4r ransomware: Palo Alto Networks has spotted threat actors hacking Microsoft SharePoint servers with the ToolShell exploit and deploying the new 4L4MD4r ransomware.
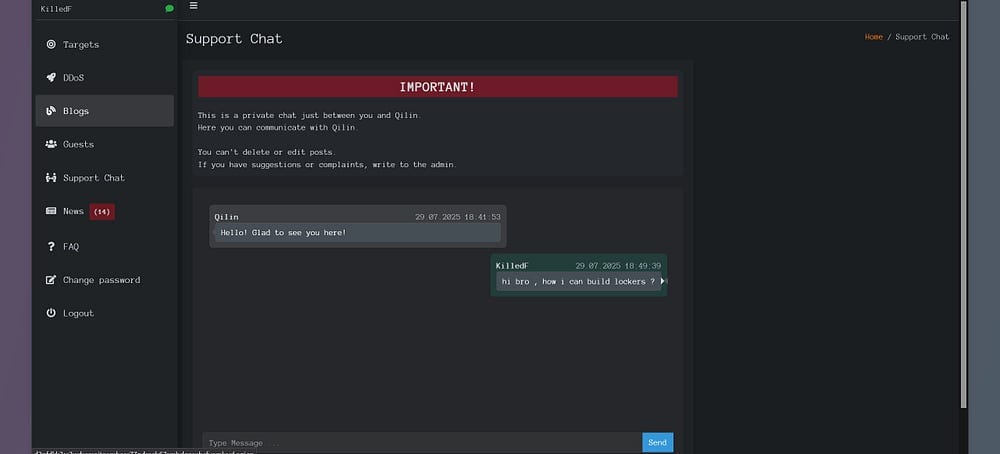
Qilin ransomware: Threat intel analyst Rakesh Krishnan has published an analysis of a leak of the Qilin ransomware backend panel. The leaker shared their credentials, claiming the Qilin group had exit-scammed and that the backend was full of "full of FBI agents and security researchers."
Sponsor section
In this product demo, CEO Eoin Hinchy shows how Tines' Workbench can integrate an LLM into security workflows to gather, analyze, and act on data from both inside and outside your company. This demo includes grabbing IOCs from an external webpage, comparing them to your company's own incidents, and taking actions like resetting passwords.
APTs, cyber-espionage, and info-ops
TikTok info-ops summary: TikTok has published its monthly report on covert influence operations the company has spotted on its platform in June this year. The company took down influence networks targeting political discourse in the Philippines, Saudi Arabia, Ecuador, Moldova, and Europe.
PAN APT list: After publishing an explainer of how it does attribution and its APT naming scheme on Thursday, Palo Alto Networks has also published a list of all the APTs it tracks and their equivalent names elsewhere.
DPRK on npm: Veracode has linked 20 malicious npm packages to North Korean campaigns targeting the cryptocurrency community.
Kimsuky: Aryaka has published a report on North Korean cyber-espionage Kimsuky (APT43, Thallium, and Velvet Chollima). The report covers a cyber-espionage campaign targeting South Korean entities with malicious LNK files for initial access.
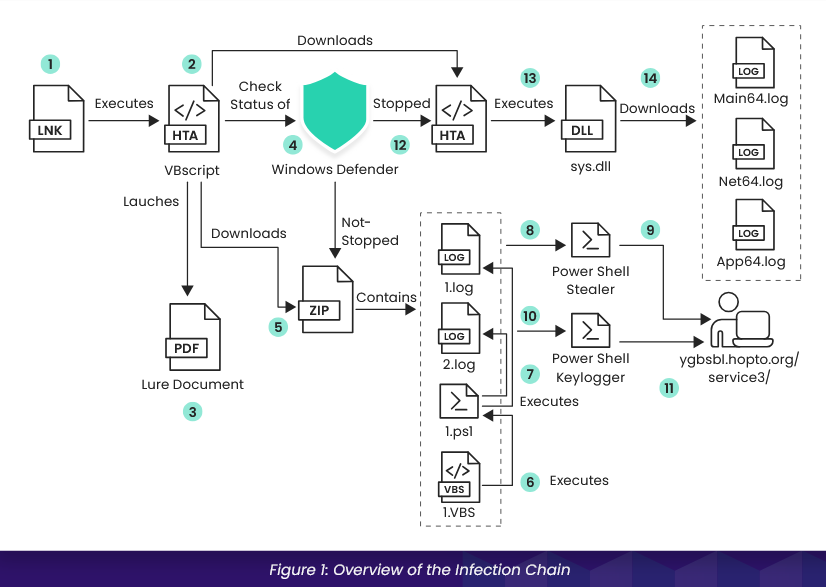
Vulnerabilities, security research, and bug bounty
MSFT bug bounty program update: Microsoft has boosted the rewards for some .NET and ASP.NET Core bug reports, and some can now go up to $40,000, depending on the bug type and report clarity.
Lovense threatens lawsuit over security flaws: Sex toy maker Lovense is threatening legal action over the recent disclosure of security flaws in one of its products. The company didn't specify if the threats would target security researchers or news outlets. A security researcher named BobDaHacker disclosed two bugs last week. The bugs would have allowed attackers to leak the emails of Lovense users and even take over their accounts. Lovense fixed the bugs only after the disclosure. [Additional coverage in TechCrunch]
Better late than never: MITRE has finally assigned a CVE to a bug that has been exploited in the wild for the past two years to disable and bypass EDR solutions. [h/t Patrick Garrity]
CurXecute vulnerability: Anysphere has patched a vulnerability in the Cursor AI-powered IDE that could have allowed malicious actors to run remote code on user systems. The vulnerability is named CurXecute and was discovered by Aim Security.
Netgear hidden debug pages: Security researchers have found a slew of hidden debug pages in Netgear routers that can be used to dump debug logs and even change router settings.
Volt Boot attack: Academics have developed Volt Boot, a method for executing physical memory disclosure attacks on SRAM by exploiting the SoC's power domain separation. This works like a classic cold boot attack, where data still remains on the chip after an unexpected shutdown.
Splunk security updates: Cisco has patched three security flaws in its Splunk SIEM product.
Infosec industry
Threat/trend reports: APWG [PDF], Cobalt, Flashpoint, Nozomi, Pew Research, and Semperis have recently published reports and summaries covering various infosec trends and industry threats.
DEFCON bans a fifth individual: The DEFCON security conference has banned a fifth individual from attending its events. [h/t Eva Galperin]
New Adobe CISO: Adobe has named Aanchal Gupta as its new CSO. She replaces Maarten Van Horenbeeck, who served in the role for the past three years. Gupta previously served in various security roles at Microsoft, Meta, and Yahoo.
New tool—Starchive: Andrew Arrow has open-sourced Starchive, a browser extension and local backend system that automatically archives YouTube videos when visited.
New tool—Warren: The Security Monitoring Lab has released Warren, an AI-powered security alert management system.
BalCCon 2024 videos: Talks from the Balkan Computer Congress 2024 security conference, which took place last September, are available on YouTube.
FOSDEM 2025 videos: Talks from the FOSDEM 2025 security conference, which took place in February, are available on the conference's website.
IEEE S&P 2025 videos: Talks from the 10th IEEE European Symposium on Security and Privacy, which took place at the end of June, are available on YouTube.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about how the recent SharePoint exploitation is a blow-by-blow repeat of the 2021 Microsoft Exchange mass compromise event. The international response to that clearly didn't deter Chinese hackers, so it is time to try something different.




