Risky Bulletin: BlackBasta implodes, internal chats leak online
In other news: Microsoft patches a Power Pages zero-day; Meta sues account hacker; Russian military hackers target Signal comms.

This newsletter is brought to you by Rad Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Internal strife and conflicts appear to have led to the implosion of another successful Ransomware-as-a-Service platform—this time, BlackBasta, one of last year's most active ransomware groups.
Everything came crashing down last week when one of the BlackBasta members leaked the group's internal Matrix chat logs on the dark web.
The leaker said they shared the data after one of the BlackBasta affiliates launched brute-force attacks targeting Russian banks—a move the leaker didn't agree with because they feared it would trigger an aggressive response from Russian authorities.
The internal chat leak appears to have been the last twitch of an already dead body, according to Swiss security firm Prodaft, which first spotted the leaked files.
The company told Risky Business the leak was only scratching the surface of a much broader internal conflict and that the gang had effectively ceased almost all operations at the start of the year.
"Most operators have moved on to other groups, such as Cactus ransomware," the company told us. "Plus, some team members scammed victims, took the money, but never provided the decryptor."
The leak includes almost 200,000 messages sent between September 2023 and September 2024. Even though the messages aren't recent, they will certainly contain extensive OPSEC data. In addition, the leaker made several other claims and statements, summarized below by Prodaft threat intel analyst 3xp0rt.
- Lapa is one of the key administrators of BlackBasta and is constantly busy with administrative tasks. Holding this high-trust position, Lapa is frequently insulted by his boss, who persistently demands major changes. The role causes Lapa significant stress, yet he earns significantly less compensation compared to others in the group. It appears that ransom payments might be an additional source of income for him to support his family during these difficult times. Under his administration, there was a brute force attack on the infrastructure of some Russian banks. So far, no actions seem to have been taken by law enforcement, suggesting that this situation could pose a serious problem and potentially provoke reactions from these authorities.
- Cortes is associated with the Qakbot group, which had dealings with Americans last year, likely attracting the attention of intelligence services. When BlackBasta conducted these attacks on Russian banks, Cortes distanced himself from these actions, probably surprised that this Russian group would target its own country. This might be why Qakbot didn't participate in the attacks against Russia.
- YY is also a main administrator of BlackBasta, seemingly very busy with support tasks and receives a good salary. The arrest of BlackBasta's leader creates significant risks for the remaining members of the group. It turns out that the personal financial interests of Oleg, the group's boss, dictate the operations, disregarding the team's interests. Under his administration, there was also a brute force attack on the infrastructure of some Russian banks. It seems that no measures have been taken by law enforcement, which could present a serious problem and provoke reactions from these authorities.
- When Trump and Bio worked together in Conti, disputes over fees issues were common. Bio is paid more in his current position to continue managing such high-level risks. Bio changed his nickname from "Bio" to "Pumba" while working at Conti, but has now reverted to his old nickname in BlackBasta, so his reputation in BlackBasta should not be associated with the nickname Pumba. The recent arrest of Bio and the police's treatment likely caused concern among the BlackBasta group members.
- Bio identifies GG as Trump. It can be inferred that GG, AA, and Trump are all aliases used by Oleg Nefedov, the group's boss.
The leaker doxes one of the BlackBasta members and claims they've been arrested, although we could find any public reporting of an arrest for that name.
The BlackBasta group launched in early 2022 and was set up by former individuals who worked inside the larger Conti ransomware group. It was one of the many Conti offshoots that spun out of the gang after it disbanded.
Ironically, Conti also disbanded following a leak of its internal chats and source code. That time around, the leak occurred shortly after Russia's invasion of Ukraine and is believed to have been the work of a Ukrainian national.
After its spun-off, BlackBasta continued like nothing happened and was constantly in the Top 10 most active ransomware gangs every quarter.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Genea hack: Australian IVF clinic Genea is investigating a breach after it detected suspicious activity on its network.
Coast Guard data breach: The US Coast Guard has taken its personnel and pay systems offline to investigate a security breach. The service discovered the breach after a junior petty officer noticed strange activity in their pay account last week. The Coast Guard has delayed payments for over 1,100 members as it investigates the incidents. This is the branch's second data breach over the past year. [Additional coverage in Military.com]
NioCorp BEC incidents: American mining company NioCorp says it lost $500,000 in a BEC attack last week.
General tech and privacy
Google Search quality declines: A WalletHub report looks at how the quality of Google search results has fallen in recent years and theorizes this may be part of a deliberate strategy to avoid monopoly accusations.
Government, politics, and policy
Japan's active cyber defense bills: The Japanese cabinet of ministries has proposed two bills this month that would grant its cyber forces the right to carry out offensive cyber operations designed to protect critical infrastructure. The concept is known as active cyber defense and has been used by some Western countries in the past. The bills have been forwarded to the Japanese Parliament, where they aren't expected to face any obstacles. [Additional coverage in The Japan Times]
SEC replaces cryptocurrency fraud unit: The US Securities and Exchange Commission has created a new team to protect investors from bad actors active in new and emerging technologies. Named the Cyber and Emerging Technologies Unit (CETU), the team will be staffed by 30 fraud specialists. The new team will also replace the SEC's existing Crypto Assets and Cyber Unit. The new CETU will still cover cyber and crypto-enabled fraud but also domains like AI, machine learning, and social media.
New CISA layoffs: The White House is firing new CISA employees. Details are still murky, but the Trump administration previously fired 130 CISA workers last week.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Jimmy Mesta, CTO and Co-Founder of Rad Security (formerly KSOC). Jimmy talks about how companies adopting new AI-based technologies may accidentally expose their infrastructure and data to new threats.
Arrests, cybercrime, and threat intel
Meta sues Instagram hacker: Meta has filed a lawsuit against a Las Vegas man for hacking and extorting Instagram users. The company claims Idriss Qibaa ran Unlocked 4 Life, an online service that sold likes, followers, and the ability to disable and reinstate Instagram accounts. Qibaa allegedly used the service to ban users and charge fees to restore their accounts. The service also supported other social networks, such as Twitter, YouTube, TikTok, Snapchat, and Telegram. The DOJ also charged Qibaa in August last year for sending death threats to victims who refused to pay. [Additional coverage in CourtWatch]
Sanctioned crypto entities thrived last year: According to a new Chainalysis report, sanctioned crypto entities thrived last year and received over $15.8 billion, accounting for 39% of all illicit crypto transactions in 2024.
New Pegasus infections spotted: Mobile security firm iVerify says it found traces of the Pegasus spyware on 11 devices. The infections were found following scans of 18,000 devices during the month of December last year. This number adds to seven other devices the company found infected with Pegasus throughout last year.
New JS obfuscation technique: Juniper analyzes a new JavaScript obfuscation technique used in the wild in attacks against a major American political action committee (PAC) in January this year.
Cloud threats: France's cyber agency has published a report—currently in French only for now—on the threats companies can expect to their cloud environments. It's a pretty comprehensive 46-page report, so if it ever gets an English version, it is a pretty good point to start looking into cloud attacks.
Email marketing platforms abused for BEC: Trustwave analyzes how BEC gangs are abusing email marketing platforms for their attacks as part of a recent shift from targeted spear-phishing to mass mailing.
Malware technical reports
Ghost ransomware still active: CISA warns that a ransomware group named Ghost that was first spotted four years ago is still active and launching new attacks against corporate environments. The agency says the group has expanded from targeting Fortinet devices to Microsoft Exchange and ColdFusion servers. The ColdFusion attacks used two 15-year-old vulnerabilities. The group operates from China and has hacked organizations in over 70 countries since its emergence in 2021. Besides Ghost, the gang is also known under other names such as Cring, Crypt3r, Phantom, Strike, Hello, Wickrme, HsHarada, and Rapture.
Snake Keylogger: Fortinet has published a report on the Snake Keylogger, also known as 404 Keylogger.
Darcula V3: Netcraft researchers have published a report on the third iteration of the Darcula PhaaS. The key difference for this new version is that it allows for brand new customized phishing attacks to be created for any website in minutes without needing the technical know-how that traditional phishing kits took to develop.
XLoader: ASEC has published a look at a recent Xloader malware distribution campaign.
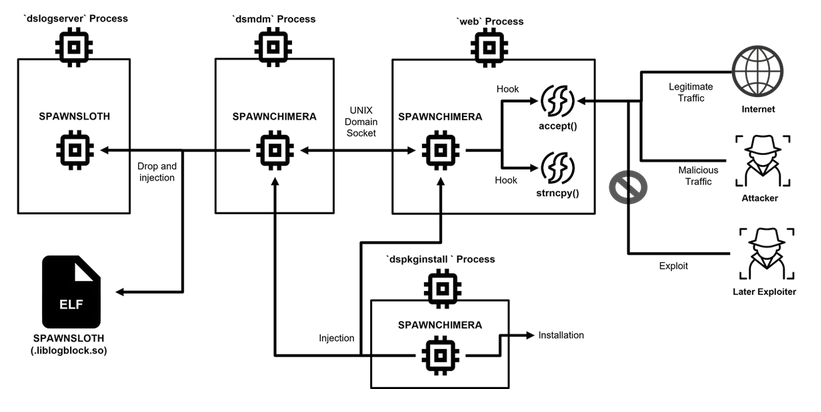
SPAWNCHIMERA: Japan's CERT has published a report on SPAWNCHIMERA, a malware strain deployed on hacked Ivanti Connect Secure devices. Previous strains from the SPAWN malware family have been linked to Chinese APT activity.
Sponsor section
Explore the future of cloud security with signatureless, behavior-based threat detection. In this video, we tackle the pressing question: "Is the cloud too noisy for behavioral detection to work?" We'll break down the limitations of signature-based methods and introduce runtime verification as a more effective solution for identifying threats in dynamic cloud environments.
APTs, cyber-espionage, and info-ops
Equation Group: Xintra founder Lina Lau has published a report that untangles and puts more clarity on how Chinese authorities claim the Equation Group (US NSA) hacked the Xi'an Northwestern Polytechnical University in 2022. Chinese officials made the accusation in September 2022 in confusing reports laced with propaganda.
Sandworm targets Signal comms: Russian military hackers are abusing a Signal feature designed to pair user accounts to new devices by scanning a QR code. Cyber units connected to Russia's Sandworm group are spreading invites to Signal groups that contain malicious QR codes. If scanned, the QR codes secretly pair a target's account to a Russian device where Sandworm operators can intercept and surveil communications. According to Google, the campaign has primarily targeted individuals in Ukraine's government and military. In some cases, Russian forces have linked Signal accounts collected from Ukrainian soldiers on the battlefield to their own devices and used it for further Signal phishing.
DPRK Contagious Interview: Apple security firm Kandji has published an analysis of macOS malware used by North Korean hackers during its Contagious Interview campaign.
"It's clear that these most recent applications share code and are used to capture the credentials of the unsuspecting victim. Understanding how these applications work is crucial to better detection of this activity."
DeceptiveDevelopment: ESET has published its own report on North Korea's typical "fake interview" campaign targeting freelancers, programmers, and crypto developers. The company calls this campaign DeceptiveDevelopment.
Pangu Team profile: Natto Thoughts has published a profile on the Pangu Team, one of China's top white-hat hacker groups known for its iOS jailbreaks and its place in the country's cyber ecosystem—as an elite vulnerability research hub.
Stately Taurus: PAN's Unit42 has linked the Stately Taurus APT to Bookworm, a mysterious trojan used in espionage campaigns for the past decade.
Salt Typhoon: Cisco Talos has published a report on Salt Typhoon attacks against its network devices—attacks first covered by Recorded Future last week (oh, the irony). The report covers JumbledPath, the malware the group deploys on hacked switches and routers. The malware can perform packet capture, modify device configurations, and clear logs to hide its presence.
Chinese APT tools found in ransomware attacks: Orange, Symantec, and Trend Micro have found Chinese APT malware in ransomware attacks across 15 countries. The tools are versions of PlugX and Shadowpad, complex backdoors used by Chinese APTs for over a decade. The two malware strains were deployed on hacked networks before the ransomware was unleashed at the end. The attackers gained access via remote network attacks, exploited weak passwords, and bypassed multi-factor authentication. Successful ransomware deployments were confirmed across two companies in Europe and a software company in South Asia. Ransomware payloads used in the attacks included RA World and a new strain named NailaoLocker.
Vulnerabilities, security research, and bug bounty
Power Pages zero-day: Microsoft has patched a zero-day (CVE-2025-24989) in its Power Pages website builder. The zero-day was exploited in the wild and allowed threat actors to register accounts with high-privileged rights on customer websites. The company has not provided other details about the attacks but says it notified all affected customers.
PAN warns of new exploit chain: Threat actors are abusing a three-bug exploit chain to hack and take over the web panels of Palo Alto Networks firewalls. The attackers are chaining recent vulnerabilities. Two bugs were patched last week (CVE-2025-0108 and CVE-2025-0111) and another in November (CVE-2024-9474). GreyNoise first spotted the attacks, and Palo Alto Networks uncovered the full exploit chain.
Cisco security updates: Cisco has released three security advisories for various products.
Atlassian security updates: Atlassian has released ten security updates this week, part of the company's February Patch Tuesday.
Invanti credential coercion vulnerabilities: Horizon3 has published a write-up on four credential coercion vulnerabilities the company found and Ivanti patched in January.
"The vulnerabilities discovered allow an unauthenticated attacker to coerce the Ivanti EPM machine account credential to be used in relay attacks, potentially allowing for server compromise. [...] Our proof-of-concept exploit can be found on our GitHub."
Lernraum Berlin security audit: Recurity has found 17 vulnerabilities in Lernraum Berlin, an LMS used by over 400 schools in the Berlin area. The bugs were part of a security audit commissioned by local authorities.
Infosec industry
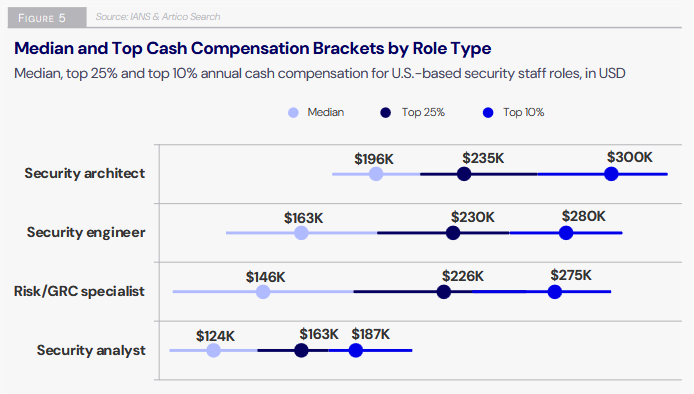
Threat/trend reports: Artico+IANS, BVP, CyberVandals, DarkTrace, HITRUST, HP Wolf Security, Kaspersky, Keep Aware, KELA, Sekoia, Symantec, and WatchGuard have published reports and summaries covering various infosec trends and industry threats. From the Artico+IANS report:
"Only a third of respondents are likely to recommend their employer, and over 60% are contemplating switching jobs within the next 12 months. Among those considering a change, dissatisfaction with career progression stands out as a key issue, while work-life balance is less of a concern. Dissatisfaction with career progression is highest among functional department heads—professionals already in senior roles—underscoring the importance of clear pathways for continued growth in improving retention."
Acquisition news: Cybersecurity provider WatchGuard has acquired ActZero, a provider of MDR services.
New tool—JDBG: A software engineer named roger1337 has released JDBG, a "powerful runtime Java debugger that leverages an injected DLL along with JNI and JVMTI to provide deep insight into Java applications."
New tool—PowerChell: SensePost's Clement Labro has released PowerChell, a rewrite of the PowerShell console in C/C++ but without the security restrictions—just perfect for the red teamers.
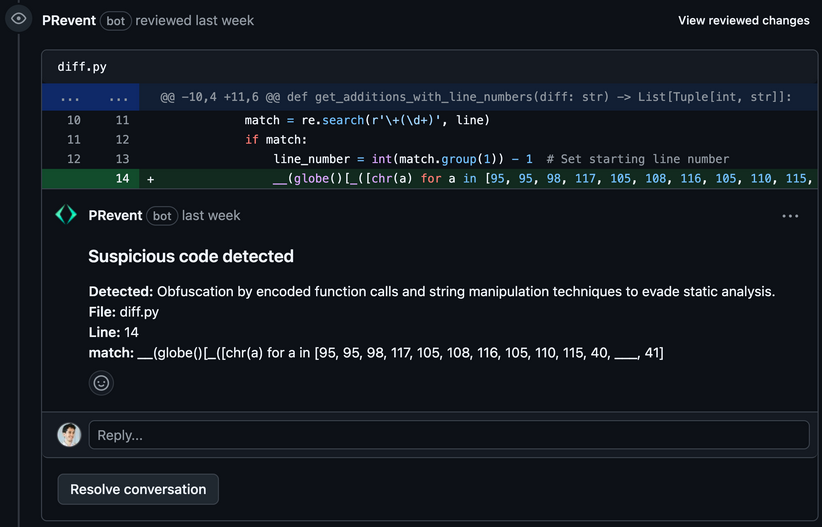
New tool—PRevent: AppSec company Apiiro has released PRevent, a tool to block malicious code submitted in pull requests.
Risky Business Podcasts
In this podcast, Tom Uren and Patrick Gray talk about the idea of launching a retaliatory campaign to hack Chinese telcos in response to Salt Typhoon's targeting of US ones. US Senator Mark Warner floated the idea as a way to persuade the Chinese government to pull back Salt Typhoon, but we think that kind of campaign has merit regardless.
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about the United State's Vulnerabilities Equities Program, which balances the need for intelligence collection with the need to protect the public. The government recently revealed that in 2023, it released 39 vulnerabilities, but what does this really tell us?




