Risky Bulletin: Belarus deploys spyware on journalists' phones
Suspect arrested for installing malware on ferry boat; France arrests Interior Ministry hacker; and new Cisco and SonicWall zero-days.

This newsletter is brought to you by Push Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Belarusian authorities are deploying spyware on the smartphones of local journalists during police interrogations.
The ResidentBat spyware was spotted this year after a reporter who was interrogated by the Belarusian KGB intelligence service started receiving malware alerts on his device, days after being questioned by authorities.
"Before the interrogation at KGB premises, the individual was asked to place the smartphone in a locker. During questioning, the journalist was required to show content on the device and unlocked the phone in an officer’s presence. Afterwards, the device was placed in the locker again. The individual and RSF believe that the security forces observed the PIN entry, retrieved the phone during the interrogation and installed the spyware."
The spyware can collect call logs, record through the microphone, take screen captures, collect SMS messages and messages from encrypted messaging apps, and exfiltrate local files.
According to a report from RESIDENT.NGO, ResidentBat's server infrastructure has been live since March 2021, when the country was gripped by anti-government protests following Lukashenko's falsification of election results.
Investigators at Reporters Without Borders, have also identified ResidentBat samples uploaded on antivirus platforms to the same period and region.
While the spyware has been used by the Belarus KGB, it's still unclear who developed it.
Belarus joins a list of countries that includes China, Kenya, Russia, and Serbia—countries that deploy spyware on victim devices during police interrogations.
Google was notified and the Android maker will allegedly notify other users infected by the same spyware.
Resident.NGO has an excellent write-up of a case where a journalist was interrogated by the Belarusian KGB and then had spyware installed on their phone. The recommendations are sensible and practical resident.ngo/lab/writeups... See also this @rsf.org report rsf.org/en/exclusive...
— Martijn Grooten (@martijngrooten.bsky.social) 2025-12-17T21:05:19.210Z
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
China's national time service hack theory: A Washington Times report claims that the alleged NSA hack of China's National Time Service Center might be an attempted US ploy to disrupt Chinese missile launches in the event of a military conflict.
FTC orders company to return user funds: The FTC has ordered the operator of the Nomad Bridge to return funds recovered from a 2022 hack back to its users. Illusory Systems recovered $37 million of the $186 million worth of crypto assets it lost during the hack. The FTC has also ordered the company to implement a comprehensive cybersecurity plan, audit its code, and fix vulnerabilities. The FBI attributed the Nomad Bridge hack to North Korean hackers.
Doublespeed hacked: Hackers have breached and released data from Doublespeed, a startup that uses phone farms to spread AI-generated ads on social media sites. [404 Media]
DXS breach: DXS International, a major IT provider for the UK NXS, has disclosed a security breach. There were no major disruptions reported to NHS activity. A ransomware group named DevMan took credit for the intrusion. [TechCrunch]
Former Israeli PM hacked: Iranian hackers have compromised the Telegram account of former Israeli prime minister Naftali Bennett. The Handala group published images of conversations and his contact list earlier this week. Bennett denied the hackers' claims that they compromised his phone and said the hack was only limited to his Telegram account. [The Times of Israel]
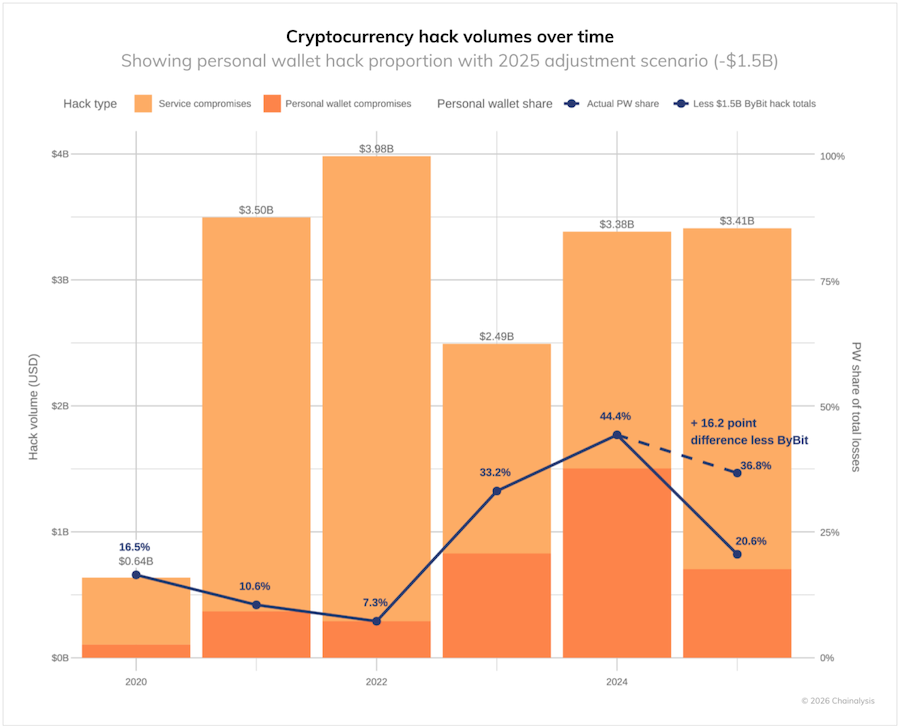
DPRK stole $2b this year: North Korean hackers have stolen more than $2 billion worth of cryptocurrency this year, representing almost 60% of all stolen assets. This brings the country's total to more than $6.75 billion over the past decade. The funds were stolen through hacks of cryptocurrency services, by hacking individuals with large assets, and by planting insiders at crypto companies.
General tech and privacy
TikTok reported for tracking users across the web: TikTok has allegedly been tracking users outside of its official app. An European privacy protection group has filed a complaint against the company in Austria for breaking EU privacy laws. The noyb group says TikTok shares data with third-parties without consent. Complaints were also filed against data broker AppsFlyer and gay dating app Grindr for sharing data with TikTok without consent.
Roblox gives in to Russian censorship: Online game Roblox has agreed to censor some of its content in Russia after authorities blocked access to its servers last week for LGBT and "extremist" content. [Novaya Gazeta]
GitHub postpones Actions price hike: After a wave of criticism, GitHub has postponed a plan to increase prices for GitHub Actions.
Twitter goes nuts in new ToS: X/Twitter is updating its terms of service with a bunch of onerous and aggressive clauses. [TechCrunch]
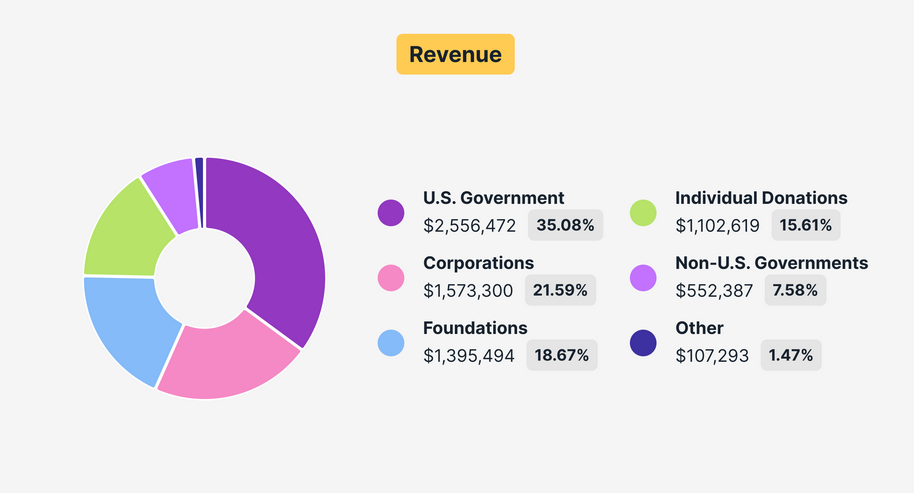
US still Tor's biggest sponsor: The US government has remained the Tor Project's largest sponsor despite the organization's efforts to diversify its funding. The project raised $7.3 million last year, of which, $2.5 million came from the US government.
Government, politics, and policy
Russia explores social media ban for kids: The Russian government is exploring the idea of banning all children under 16 from social media, taking a page out of Australia's book. [Ria Novosti]
MIVD makes cyber a priority: The Dutch military intelligence agency will make it a priority to expose and disrupt cyber operations next year. The MIVD will go after both e-crime and state-sponsored operations. The new shift comes after cyberattacks against Dutch organizations have risen in recent years. [Security.nl] [h/t DvH]
US seeks deepfake crime penalty input: The US Sentencing Commission is seeking input on what penalties should be applied to individuals found guilty of creating nonconsensual deepfake porn and other offenses under the new Take It Down Act. [CyberScoop]
Sponsor section
In this Risky Business sponsor interview, Casey Ellis is joined by Push Security’s Field CTO, Mark Orlando. They chat about the ways that browser-based attacks are evolving and how Push Security is finding and cataloging them.
Arrests, cybercrime, and threat intel
France detains MoI hacker: French authorities have arrested a 22-year old man for a cyberattack on the French Interior Ministry's email servers. The hacker allegedly stole the data of millions of French citizens. Officials said the suspect is a known hacker who was convicted of similar crimes earlier this year. [Radio France Internationale/Official press release PDF]
Suspect arrested for planting RAT on ferry boat: French authorities have arrested a Latvian man for installing malware on a ferry boat. The suspect was a crewmember on Fantastic, an Italian-owned passenger ship. He allegedly installed a remote access trojan (RAT) on the ferry's systems while the ship was docked in the southern French port of Sète. Authorities believe the man worked for an organised group linked to a "foreign power." [France24] [h/t David Shipley]
Dutch police arrests deepfake scammer: Dutch authorities have arrested a 34-year-old man for banking fraud. The suspect opened bank accounts in other people's names using copies of their IDs. Authorities say he applied the eyes, nose, and mouth from the victims' cards to his face to bypass the bank's facial recognition systems when creating the accounts online. [h/t DvH]
US seizes E-Note exchange: US authorities have seized the servers and infrastructure of the E-Note cryptocurrency exchange. The FBI says the portal laundered more than $70 million from ransomware attacks and account hacks. Authorities have also indicted the site's operator, a 39-year-old Russian national named Mykhalio Petrovich Chudnovets.
India dismantles SMS factory: Indian authorities have dismantled a cybercrime platform that sent bulk SMS spam to Indian users. The platform ran on top of 21,000 SIM cards and was used by both domestic and foreign cybercrime gangs. It was sending millions of messages daily, often imitating Indian government services and aiming to collect banking details.
Google sues Darcula PhaaS: Google has filed a lawsuit against the operators of the Darcula phishing service. The company is seeking a court order to seize the group's server infrastructure. The lawsuit names Chinese national Yucheng Chang as the group's leader, along with 24 other members. Chang was previously identified as the Darcula admin in a joint investigation between German, French, and Norwegian journalists in May. [NBC News]
Malicious Firefox add-ons: Koi Security has found a cluster of 17 malicious Firefox add-ons distributed through the official Mozilla portal. The extensions track user traffic and insert affiliate links for Chinese shopping portals. The add-ons have been live since September and have been downloaded more than 50,000 times.
Securotrop group interview: Threat intelligence analyst Marco A. De Felice has published a second interview with the operators of the Securotrop ransomware, a group that splintered off from the main Qilin gang. The first one is here.
Mass fake-shop campaign: BforeAI has spotted a suspected Chinese threat actor registering hundreds of retail-related domains right ahead of the global winter holiday shopping season.
AWS crypto-mining: The AWS security team has uncovered a crypto-mining campaign targeting its EC2 and ECS customers.
Silver Fox's black hat SEO abuse: The NC Group looks at how a Chinese e-crime group named Silver Fox is using SEO poisoning to spread its malware to Chinese-speaking users.
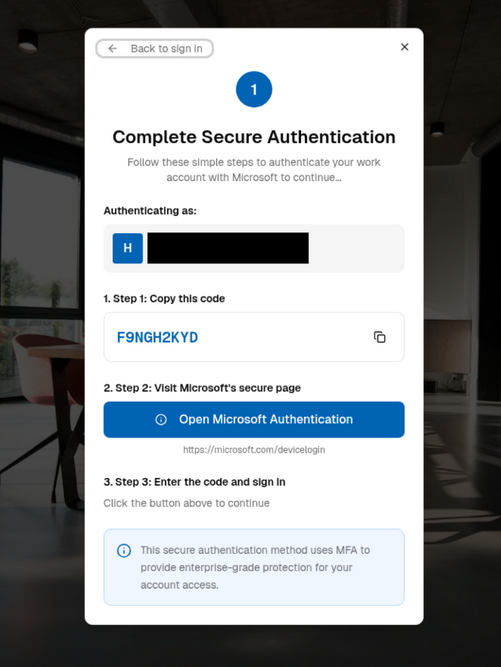
Device-code phishing goes wild: Proofpoint is reporting a surge in OAuth device code phishing campaigns targeting Microsoft 365 accounts. The campaigns have been linked to both e-crime and state-sponsored espionage groups. The attacks seek to trick users into finishing an OAuth authorization process started by the hackers. Completing the process allows attackers access to the victim's accounts.
Malware technical reports
Kimwolf botnet: A new Android botnet has infected more than 1.83 million devices. The Kimwolf has primarily infected smart TVs, set-top boxes, and Android tablets. The botnet has been used to carry out large-scale DDoS attacks on internet providers. According to Chinese security firm QiAnXin, the botnet appears to have been created by the same group behind Aisuru, a botnet that broke several DDoS records this year.
RansomHouse updates encryption: The RansomHouse ransomware group has upgraded its file encryption process to use two different encryption keys to encrypt files as part of their attacks in what Unit42 calls a significant escalation in ransomware operations.
"The upgraded version's code reveals a two-factor encryption scheme where the file is encrypted with both a primary key and a secondary key. Data encryption is processed separately for each key. This significantly increases the difficulty of decrypting the data without both keys."
Stealka: There's a new infostealer in town named Stealka. It targets browsers, crypto-wallets, password managers, messengers, email clients, note-taking apps, VPN clients, gaming launchers, and 2FA apps.
AuraStealer: Gen Digital researchers have published a technical breakdown of the AuraStealer. The malware is widely used in TikTok campaigns, with videos advertising product activation guides and tips that lead to AuraStealer-infected files.
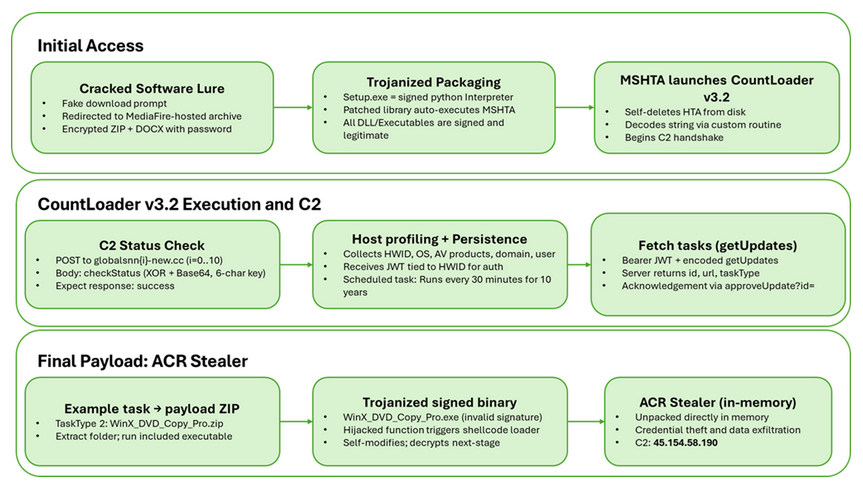
CountLoader: Cyderes has spotted a new version of CountLoader being used in the wild to deploy the ACR Stealer.
GachiLoader: Check Point has published a report on GachiLoader, a Node.js-based malware loader distributed through malicious YouTube videos.

Sponsor section
In this wholly sponsored Soap Box edition of the show, Patrick Gray chats with Adam Bateman and Luke Jennings from Push Security.
APTs, cyber-espionage, and info-ops
APT35 bureaucracy: The DomainTools security team looks at recent APT35 leaks showing how the group operates with extreme government oversight and bureaucracy, rather than a group of loose canon hackers. The report also looks at APT35 and Iran's links to the fake hacktivist group Moses Staff.
"The leaked spreadsheets form the operational backbone of APT35’s infrastructure management system, a triptych of bureaucracy masquerading as tradecraft. Each file exposes a different layer of the machine: procurement, payment, and deployment. Together they illustrate how a state-sponsored threat actor runs its cyber operations not through shadowy improvisation but through clerical precision. The documents track every rented server, every registered domain, and every euro or satoshi spent, all with internal ticketing numbers and service IDs linking actions across datasets. What emerges is a portrait not of hackers but of administrators, a bureaucracy that treats intrusion as an accounting exercise and espionage as a workflow."
Prince of Persia: SafeBreach has uncovered new operations from an Iranian hacking group tracked as Prince of Persia and Infy, which it was believed to have ceased activity back in 2022.
ForumTroll targets Russian scholars: A cyber-espionage campaign has targeted political experts and scholars working at major Russian universities and research institutions. The attacks have been linked to ForumTroll, a group that started targeting Russia and Belarus after its invasion of Ukraine. This campaign used spear-phishing to deploy the Tuoni pen-testing framework. Older ForumTroll operations also used Chrome zero-days and Dante, a new spyware strain made by Italian company Memento Labs.
Arcane Werewolf: Russian security firm BI.ZONE looks at campaigns from the past two months that have targeted Russian manufacturing enterprises. The company linked the attacks to a group tracked as Arcane Werewolf (Mythic Likho).
BlueDelta's UKR.NET campaigns: A Russian APT group known as BlueDelta has conducted a sustained phishing campaign targeting the users of UKR.NET Ukrainian email service. The group is believed to be one of the Russian GRU's cyber units.
BlindEagle: Zscaler has spotted a new BlindEagle campaign targeting the Colombian government.
"In this campaign, BlindEagle targeted a government agency under the control of the Ministry of Commerce, Industry and Tourism (MCIT) in Colombia using a phishing email sent from what appears to be a compromised account within the same organization."
New DPRK APT infra: Acronis and Hunt Intelligence have uncovered new server infrastructure linked to North Korean APT groups Lazarus and Kimsuky.
Chinese APT exploits Cisco zero-day: A suspected Chinese APT is exploiting a zero-day (CVE-2025-20393) in Cisco email security products. The attacks have targeted the Cisco Secure Email Gateway and the Cisco Secure Email and Web Manager. Cisco linked the attacks to a group it tracks as UAT-9686. The zero-day allows the attackers to run commands as root on the devices if certain ports are open on the internet.
LongNosedGoblin: Cybersecurity firm ESET has discovered a new Chinese cyber-espionage group. The LongNosedGoblin group has targeted government agencies across Southeast Asia and Japan for the past two years. The group uses different malware families shared among multiple APT groups. Its main trait is the use of Group Policies to deploy malware on compromised hosts.
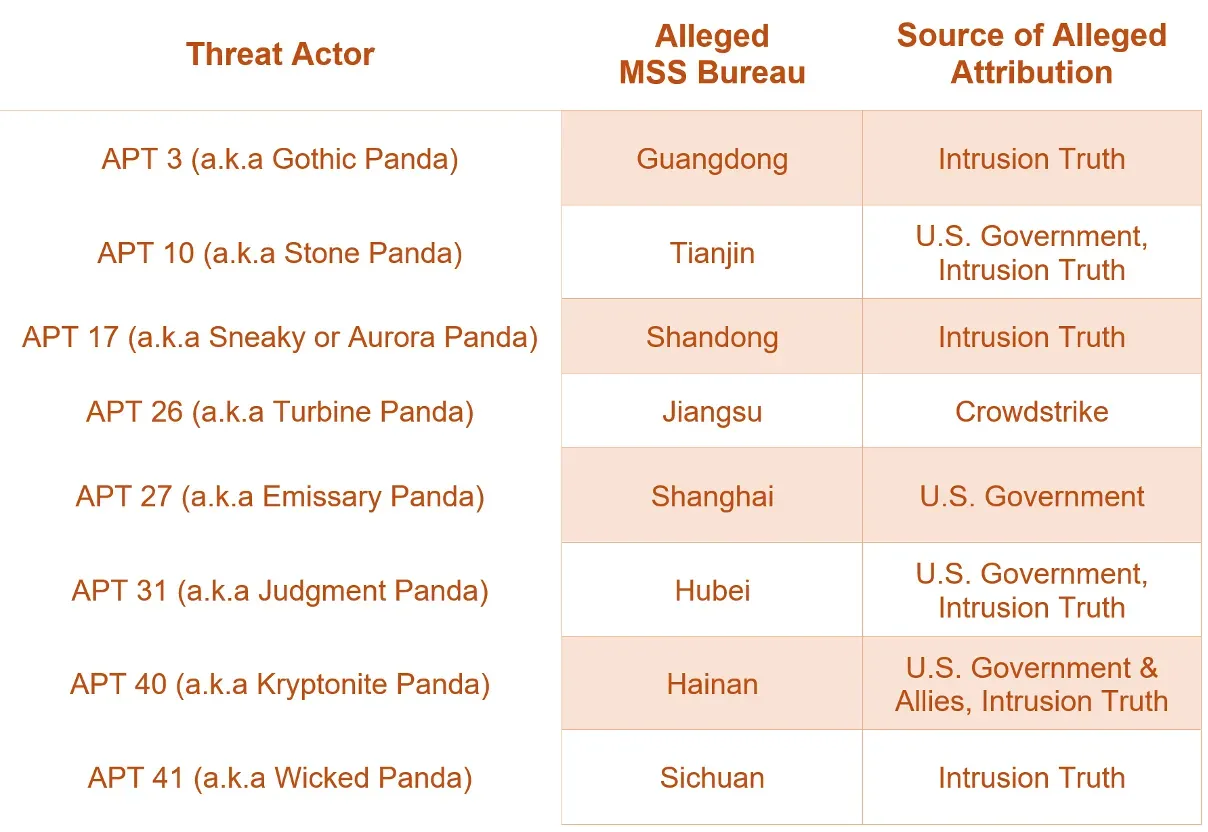
Chinese APTs and their MSS bureaus: Natto Thoughts has assembled some historic research and linked some of the major Chinese APTs to their respective regional MSS bureaus.
Vulnerabilities, security research, and bug bounty
SonicWall patches zero-day: SonicWall has released a security update to patch an actively exploited zero-day in its SMA1000 security gateways. Tracked as CVE-2025-40602, the vulnerability was part of an exploit chain with another zero-day that SonicWall patched in January. The new zero-day was spotted in the wild by Google's security team.
React2Shell used for ransomware: Threat actors are using the React2Shell vulnerability to deploy ransomware. Attackers have been spotted deploying the Weaxor ransomware strain in attacks over the past week. The ransomware has been historically associated with a group that targets MSSQL servers.
It was only a matter of time. In this case a very short time...
— Jake Williams (@malwarejake.bsky.social) 2025-12-18T11:08:58.626Z
HPE RCE: Hewlett Packard Enterprises has released a security update to patch an RCE vulnerability in the OneView IT infrastructure management software. Tracked as CVE-2025-37164, the bug has a 10.0 CVSS score.
FreeBSD RCE: The FreeBSD operating system released a security update to patch a remote code execution attack. Tracked as CVE-2025-14558, the vulnerability resides in the operating system's rtsol and rtsold component. The vulnerability has a severity rating of 9.8/10.
New DMA attacks: A new vulnerability in some UEFI-supported motherboards leaves systems vulnerable to early-boot DMA attacks across architectures that implement UEFI and IOMMU. Affected vendors include ASRock, ASUS, Gigabyte, and MSI.
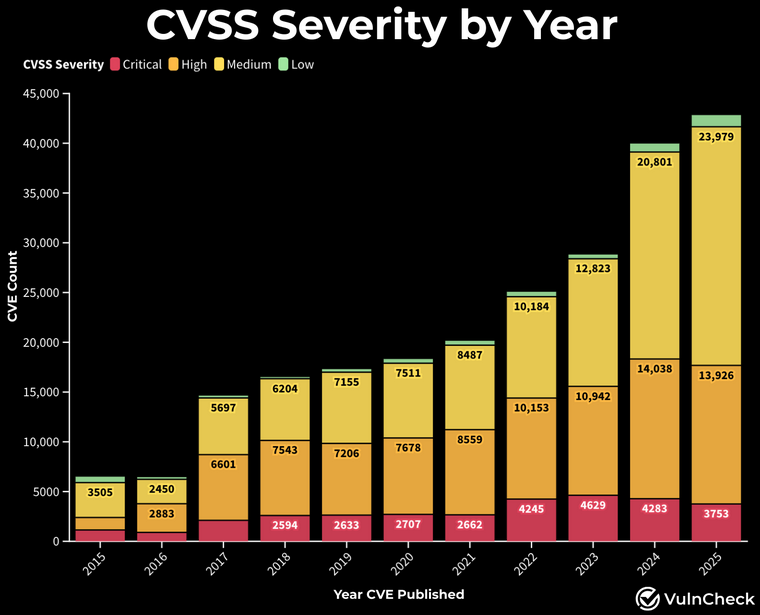
Fewer critical bugs: The number of critical vulnerabilities has gone down in recent years even if the number of vulnerabilities have gone up. The number is even smaller if the new CVSSv4 rating is applied. According to VulnCheck, a quarter of all vulnerabilities reported last year now have a CVSSv4 rating.
Infosec industry
Threat/trend reports: Action1, ANY.RUN, Chainalysis, Dragos, ESET, NCC Group, NCSC-NZ, Ookla, Open Measures, VulnCheck, and Water-ISAC have recently published reports and summaries covering various threats and infosec industry trends.
ZeroDay Cloud hacking contest results: Google's Wiz division has awarded $320,000 to security researchers for 11 exploits used during the ZeroDay Cloud hacking contest last week.

New tool—pathfinding.cloud: DataDog has launched pathfinding.cloud, a database of IAM permissions and permission sets that allow privilege escalation in AWS.
New tool—ATHF: Security firm Nebulock has released the Agentic Threat Hunting Framework (ATHF), a tool to automate threat hunting using AI tools.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Patrick Gray talk about America's increasing dependence on Chinese manufacturers for electrical sector equipment. This doesn't seem like a good idea when China is hacking electric utilities for sabotage and PLA researchers are dreaming up ways to attack the grid.
In this edition of Between Two Nerds, Tom Uren and The Grugq talk to Hamid Kashfi, CEO and founder of DarkCell, about the Iranian cyber espionage scene.




