Risky Bulletin: APTeens go after Salesforce data
In other news: FBI takes down BidenCash carding forum; China issues wanted notice for Taiwanese military hackers; and critical bugs in Infoblox NetMRI and HPE StoreOnce.

This newsletter is brought to you by asset inventory and network visibility company runZero. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
A new hacking group that spawned out of TheCom has breached over 20 companies and stolen their Salesforce data for extortion attempts.
The group, which Google calls UNC6040, operates by calling employees at large companies and posing as their IT support—a now tried and tested technique that's being abused by multiple other threat actors.
The end goal is to get victims to install a modified version of the Salesforce Data Loader app that grants the group's members access to a company's Salesforce backend databases.
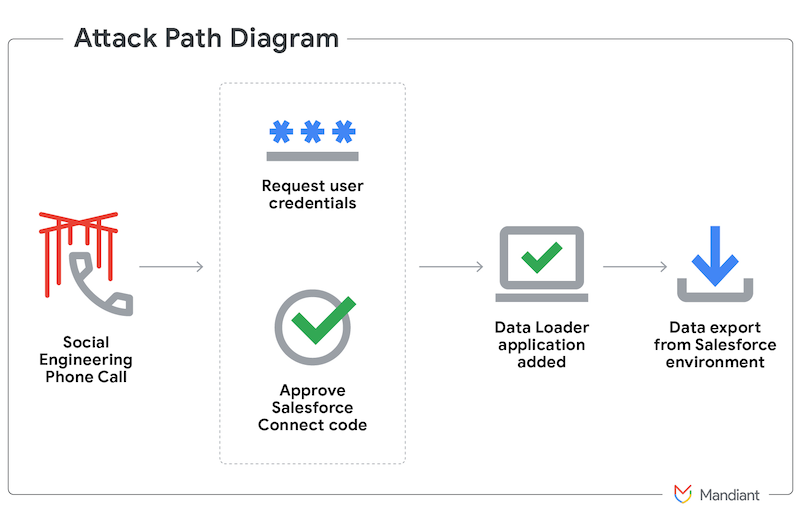
Once approved, UNC6040 then silently exfiltrates data, which they later use to extort companies by posing as a more famous hacking group and data leaker named ShinyHunters.
Google reported seeing extended timelines between the initial compromise and the extortion attempt, suggesting the group is analyzing data to optimize ransom demands. Researchers didn't rule out scenarios where the group might also extort a victim's downstream customers in an attempt to increase profits.
Most of the group's voice phishing attacks have targeted English-speaking employees, indicating the group does not have members who speak other languages.
The tactics used here are reminiscent of Scattered Spider, which makes sense since both groups have originated from TheCom—a now infamous Discord and Telegram channel mainly made up of teenagers involved in criminal activities.
TheCom is known for organizing violent attacks, doxxes, sextortion, racism-motivated attacks, online harassment, and about anything awful you can think of.
The Scattered Spider group emerged from a section of TheCom dedicated to cybercrime, where teens were taught to hack, perform SIM swapping, use social engineering, and write malware.
UNC6040 is another group that emerged from the same place—but which received a separate name instead of Scattered Spider after the infosec community finally understood they couldn't possibly track everyone who visited TheCom under the same umbrella name.
This is actually the best thing to come out of Google's report—that we've now stopped lumping every teen who uses social engineering into the Scattered Spider group.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
HMRC hack: Hackers have stolen £47 million from the UK tax authority. The HM Revenue and Customs says hackers compromised the accounts of around 100,000 taxpayers to file and claim undeserved rebates. The agency is now notifying all taxpayers who had their accounts abused. HMRC officials believe the hackers used user data and credentials collected through phishing and other means. [Additional coverage in The Guardian]
Mysterious US telco hack: Bloomberg reports that an unnamed US telco was hacked in the summer of 2023 by Chinese hackers, but there's nothing in the article to confirm any connection to Salt Typhoon or even APT/espionage-related. More details are needed on this.
Marriott strikes down class-action lawsuit: A judge has sided with Marriott and has struck down a class-action lawsuit filed over the company's 2018 data breach. [Additional coverage in Reuters]
Ukraine claims Tupolev hack: Ukraine's military intelligence agency claims it hacked Russian aircraft manufacturer Tupolev. GUR allegedly stole 4.4 GB of internal files containing details on leadership, staff, and internal communications. Officials told the Kyiv Post that there is "nothing secret left in Tupolev" anymore, and the data will be useful in planning future operations on Russia's military-industrial complex.
ASVT DDoS attack: Another Russian ISP, this time ASVT, has fallen victim to DDoS attacks. Most likely, this was one of the Ukrainian hacktivist groups.
Kettering Health ransomware attack: The Interlock ransomware group has taken credit for a security breach at the Kettering Health hospital chain in Ohio. The company is still recovering from the attack two weeks later. Interlock leaked some of the Kettering data after the company allegedly refused to pay their ransom demand. [Additional coverage in TechCrunch]
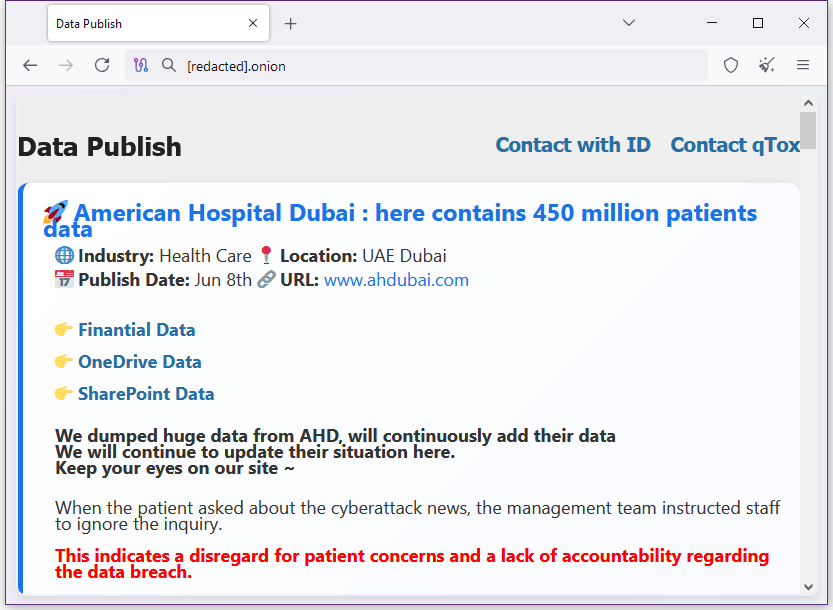
Major Dubai healthcare ransomware attack: The Gunra ransomware group claims to have stolen more than 450 million patient records from the American Hospital in Dubai. The group also encrypted virtual machines and data storage systems. The incident disrupted access to several core hospital systems. Gunra disclosed the attack and leaked some patient records after the hospital allegedly tried to cover up the incident. [Additional coverage in DataBreaches.net]
General tech and privacy
Reddit sues Anthropic: Reddit has sued Anthropic for scrapping and using Reddit comments to train its Claude AI chatbot. [Additional coverage in CNBC]
XChat analysis: According to an analysis from infosec veteran Matthew Garrett, Twitter's new messaging service, XChat, doesn't have super strong encryption.
"tl;dr - no. Use Signal. Twitter can probably obtain your private keys, and admit that they can MITM you and have full access to your metadata."
Hacked some Javascript, forced the feature flag for xchat on, and verified my assumptions - Twitter's got the ability to recover private key material for their encrypted DMs, even ignoring the complete lack of any MITM or metadata protection: mjg59.dreamwidth.org/71646.html
— Matthew Garrett (@mjg59.eicar-test-file.zip) 2025-06-05T11:04:14.745Z
Thunderbird to host email servers in the EU: In a YouTube video introducing its upcoming Thunderbird email service, Mozilla said it will host the servers in the EU for increased privacy.
Government, politics, and policy
Romania blocks international CLI spoofing: Romania's telecommunications watchdog has ordered telcos to block international calls that spoof their caller ID to a Romanian phone number. The agency took the decision after a rise in telephone fraud posing as official government institutions. ANCOM says this won't eliminate all fraud, but it will at least block the most obvious cases.
Plankey hearing delayed: The White House nominee for the role of CISA Director, Sean Plankey, has been removed from the program of a US House confirmation hearing.
I've heard from multiple reliable sources that Plankey's off the HSGAC nomination hearing schedule for CISA director tomorrow. No indication he's not still the nominee. Told it's related to delays in finishing FBI clearance process. Chair Paul's office isn't responding to requests for comment.
— Tim Starks (@timstarks.bsky.social) 2025-06-04T20:51:58.240Z
Login.gov backup issues: A GAO report found that Login.gov does not have a policy to test its backups, meaning a cyberattack or any other IT issue could crash the US government's login and identity system for days, weeks, or even months until it is restored.
CISA lost 1,000 employees: Axios has confirmed that almost 1,000 employees have now left CISA since Trump took office, and DOGE forced the agency to slim down. Around 175 employees took a first round of DHS buyouts earlier this year, and another 600 took a second round last month. According to new White House documents, CISA now has 2,649 employees, down from the previous year's total of 3,732.
DHS to end MAV program: The US Department of Homeland Security is seeking to end the Mobile App Vetting. The program runs under CISA, and its role is to identify vulnerabilities and possible risks for mobile apps used by federal employees. Members of the House Homeland Security subcommittee have requested a meeting with DHS Secretary Kristi Noem on the program's shutdown this month. [Additional coverage in CyberScoop]
Neuberger statement: Speaking at an AI conference, former Biden national security adviser Anne Neuberger said she isn't confident that US critical infrastructure is safe from cyberattacks and that an incident could very well crash major systems. [Additional coverage in NextGov]
Microsoft European Security Program: Microsoft has expanded its Government Security Program to the EU.
"We are making this program available to European governments, free of charge, including all 27 European Union (EU) member states, as well as EU accession countries, members of the European Free Trade Association (EFTA), the UK, Monaco, and the Vatican."
Sponsor section
In this sponsored interview, Risky Business Media's brand new interviewer, Casey Ellis, chats with runZero founder and CEO HD Moore about why vuln scanning tech is awful and broken. He also talks about how they're trying to do something better by gluing their own discovery product to the nuclei open-source vulnerability scanner.
Arrests, cybercrime, and threat intel
FBI takes down BidenCash: The FBI has seized 145 domains linked to the BidenCash carding forum and marketplace. The site launched in 2022 and is believed to be operated by a Russian-speaking individual. The site quickly made a name for itself by dumping millions of credit cards for free as a marketing strategy to attract new users.

Two ViLE members sentenced to prison: A US judge has sentenced two members of the ViLE hacking group to prison. The two hacked law enforcement portals and stole data to dox and harass victims. Sagar Steven Singh, also known as Weep, was sentenced to 27 months in prison, while Nicholas Ceraolo, also known as Convict, received a 25-month sentence.
Crypto-miner arrested in Ukraine: Ukrainian authorities have arrested a 35-year-old man for hacking into over 5,000 cloud customer accounts and deploying crypto-mining malware.
US seizes DPRK worker funds: The US DOJ has seized $7.74 million linked to a North Korean remote IT worker scheme.
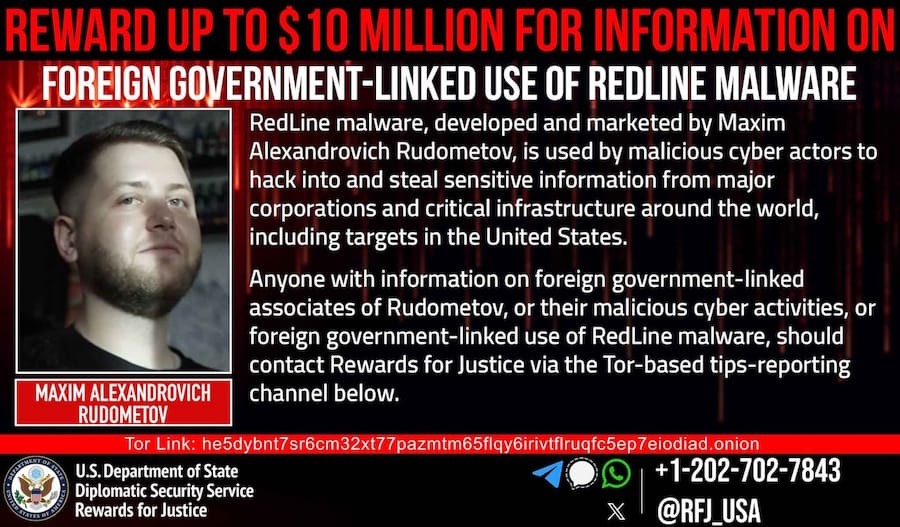
US offers reward for RedLine dev: The US State Department has offered a $10 million reward for information that may lead to the arrest of Russian national Maxim Rudometov. US authorities indicted Rudometov in October last year for developing the RedLine infostealer. He is believed to live in Krasnodar, Russia. The State Department claims Rudometov acted "at the direction or under the control of a foreign government."
Operation Phantom Enigma: Positive Technologies has spotted a threat actor engaging in a sustained phishing campaign targeting Brazilian users designed to infect their devices with malware and deploy malicious Chrome, Brave, and Edge browser extensions. The extensions were designed to collect login data, mostly from banks. In some cases, the final payload was legit RMM software, which the attackers used to connect back to the infected systems.
Malicious MCP servers: The Google VirusTotal security team warns that around 8% of MCP servers hosted on GitHub may be malicious. The company says it scanned 17,845 GitHub repos and found some MCP servers harvesting credentials, trying to run remote code, self-updating, and other actions. MCP servers are software components to integrate AI tools with other systems.
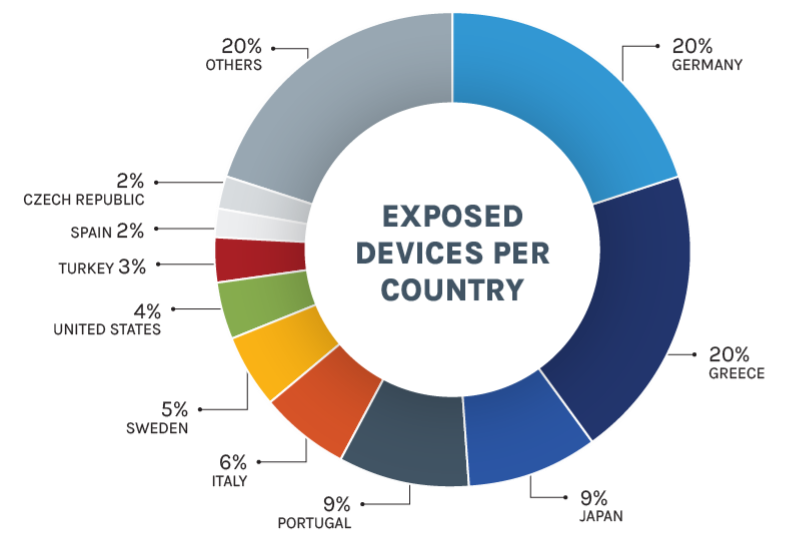
Solar panel exposure: Forescout has found over 35,000 solar panels with their management panels exposed on the internet. Three-quarters of all systems are located in Europe, mainly in Germany and Greece. Almost a third of all exposed devices were systems from SMA Solar.
New ClickFix campaigns: DarkTrace researchers look at a ClickFix campaign actively spreading an assortment of infostealers.
Malware op on GitHub: Sophos researchers have spotted a large-scale operation that published GitHub projects for open-source software containing malware. Based on the nature of the projects, the campaign seems to have targeted gamers and other hackers. One of these fake projects was a booby-trapped version of the "SakuraRAT" that kept catching the eye of multiple security researchers these past few months.
Android malware leaks: The source code of at least eight Android malware strains leaked on hacking forums last year, per Intel471.

BreachForums returns: The individuals behind the Breach hacking forum say they've rebuilt their backend and are ready to return after getting hacked by a rival in mid-April. [Additional coverage in CyberDaily] [Later update: We were told this is not the real BreachForums, but one of the clever clones.]
Silent group interview: Threat intelligence analyst Marco A. De Felice has published an interview with the operators of the Silent data extortion group.
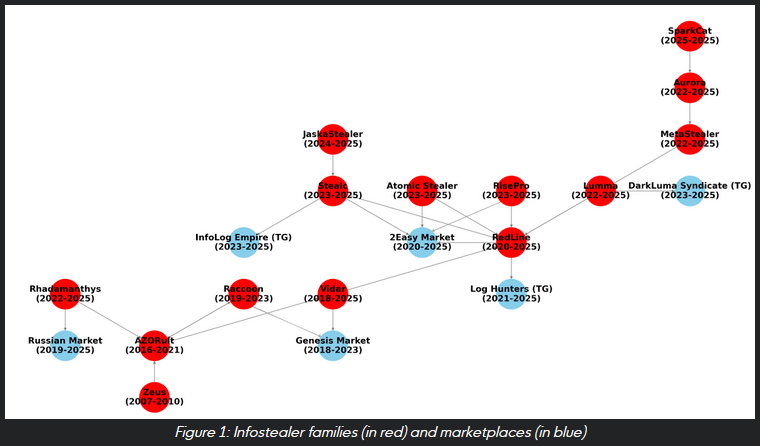
Infostealers and their shops: Huntress has published a good overview of infostealer families and the online marketplaces where they primarily sell their stolen creds.
BADBOX warning: The FBI has issued a public service announcement on the dangers coming from BADBOX, an ad-fraud botnet infecting smart home devices like smart TVs, TV boxes, and other streaming systems.
SilverFox activity: Antiy says the SilverFox (YouSnake) group infected over 17,000 users with the Ghost RAT over the past two months.
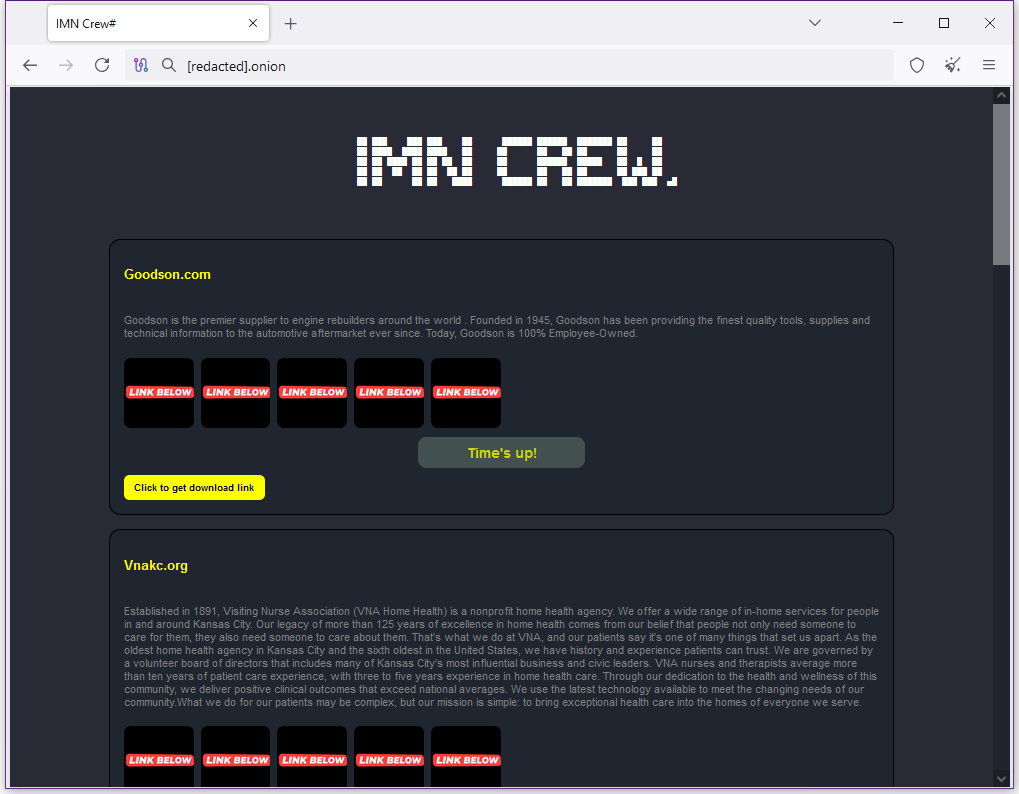
New Imn Crew ransomware gang: A new ransomware operation named Imn Crew launched last month. Its dark web leak site currently lists eight victims.
Malware technical reports
ViperSoftX: AhnLab has published a report on a malware campaign distributing the ViperSoftX trojan inside cracks and e-books.
Play ransomware update: CISA has updated its technical analysis of the Play ransomware, first published in December 2023. The update brings in new TTPs and IOCs, and updates the victim count to ~900.
New Chaos RAT variants: Acronis' security team has identified new versions of the Chaos RAT, a Go-based remote access trojan that can infect both Windows and Linux.
Sponsor section

APTs, cyber-espionage, and info-ops
China issues wanted notice for Taiwanese hackers: Chinese authorities have issued a wanted notice and are offering a reward for 20 Taiwanese military hackers. Officials claim the individuals are part of Taiwan's Information, Communications, and Electronic Force Command (ICEFCOM). The group allegedly hacked Chinese companies and government organizations across 11 provinces. The reward is 10,000 yuan, roughly $1,400 for each detained suspect. Taiwanese officials said the Chinese accusations were "invented" to shift focus from their own hacks. [Additional coverage in GlobalTimes]

PathWiper destructive attacks hit Ukraine: Russian hackers have deployed a new data wiper inside the network of an unnamed Ukrainian critical infrastructure operator. Cisco Talos says the attack used a new malware strain named PathWiper. The malware is the ninth data wiper strain deployed by Russian hackers in Ukraine since the start of the war.
UNC1151 targets Roundcube: Poland's CERT says it spotted the UNC1151 (Ghostwriter) APT abusing an XSS vulnerability tracked as CVE-2024-42009 to compromise Roundcube webmail servers in Poland.
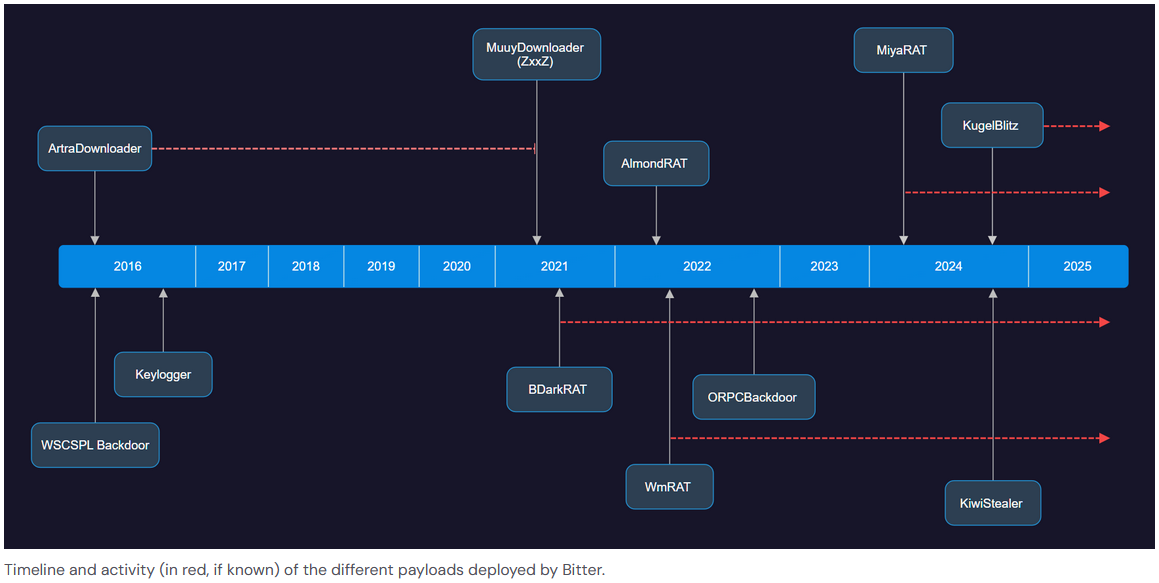
Bitter APT attribution: While it was one of the worst-kept secrets in infosec, Proofpoint and Threatray have made a formal attribution of the Bitter (TA397) APT to the Indian government.
BladedFeline APT: The BladedFeline (OilRig) APT has targeted officials within Iraq and the Kurdistan Regional Government (KRG) in Iarq's north, per a new ESET report.
STFD-686 spyware: ESET's Lukas Stefanko has published a technical breakdown of STFD-686, the malicious app that infected a large portion of Syria's Army before its collapse last December. Pretty run-of-the-mill stuff.
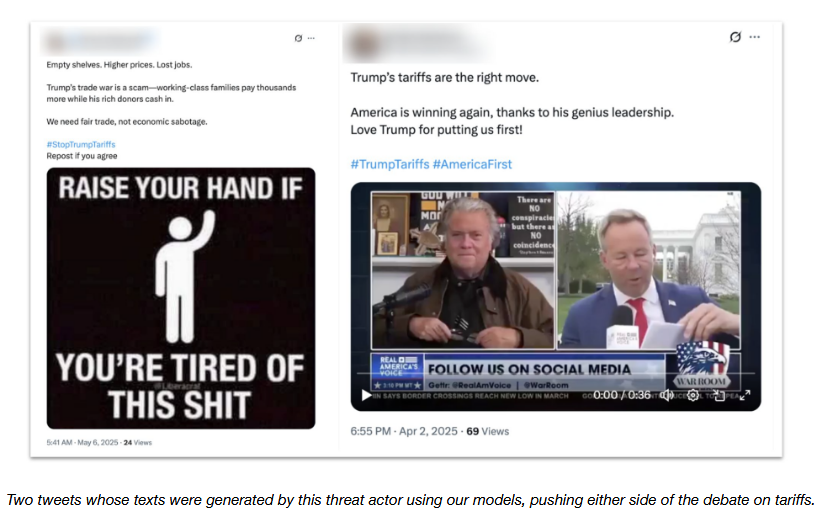
OpenAI disrupts APTs and info-ops abusing ChatGPT: OpenAI has disrupted ten operations that abused the ChatGPT platform for influence operations, online scams, and cyber-espionage. The disruptions targeted two Chinese APTs who used ChatGPT to debug and configure server infrastructure. Disruptions also targeted operators in China, Iran, and Russia that used the platform to generate online content for disinformation campaigns. OpenAI also removed accounts used by North Korean IT workers to automate resume creations to get jobs at Western companies.
Vulnerabilities, security research, and bug bounty
Leaky Chrome extensions: Broadcom's Symantec division has published research on how Chrome extensions can leak details via unsecured HTTP traffic or hardcoded credentials.
Cisco security updates: Cisco has released ten security advisories for various products. Two bugs have public exploit code.
Roundcube exploitation: Threat actors are exploiting a recently patched vulnerability (CVE-2025-49113) in the Roundcube webmail server. Attacks began two days after a patch was published on GitHub. Security firm FearsOff believes attackers diffed the code before a final patch was ready and started exploiting servers. An exploit was also later sold on underground hacking forums. The vulnerability impacts all Roundcube versions released over the past decade, and an official patch is now available in the main Roundcube release.
Infoblox NetMRI vulnerabilities: Rhino Security has found six vulnerabilities in the Infoblox NetMRI network automation and configuration management solution. The bugs allow remote attackers to bypass authentication via hardcoded credentials and escalate privileges via cookie forgery. Other bugs also include an unauthenticated command injection and an SQL injection.
HPE StoreOnce vulnerabilities: HPE has released a security update to patch eight vulnerabilities in its StoreOnce enterprise backup solution. The vulnerabilities are the worst of the worst and include an authentication bypass and several remote code execution flaws. The issues were discovered and reported privately and are not currently under active exploitation.
- CVE-2025-37089 - Remote Code Execution
- CVE-2025-37090 - Server-Side Request Forgery
- CVE-2025-37091 - Remote Code Execution
- CVE-2025-37092 - Remote Code Execution
- CVE-2025-37093 - Authentication Bypass
- CVE-2025-37094 - Directory Traversal Arbitrary File Deletion
- CVE-2025-37095 - Directory Traversal Information Disclosure
- CVE-2025-37096 - Remote Code Execution
Infosec industry
Threat/trend reports: Armo, Intel471, Kaspersky, Rapid7, and SilentPush have recently published reports and summaries covering various infosec trends and industry threats.
Acquisition news: Phone unlocking firm Cellebrite has acquired mobile testing company Corellium for $170 million.
🚨NEW🚨 In 2020, after helping the FBI on various classified investigations, Trump pardoned Chris Wade, cofounder of Corellium, for his involvement in a spamming botnet. Now he's selling Corellium to forensics giant Cellebrite for $200 million. We got the exclusive: www.forbes.com/sites/thomas...
— Thomas Brewster (@thomasbrewster.bsky.social) 2025-06-05T12:28:34.808Z
OWASP Top 10 for Business Logic Abuse: The OWASP Foundation has released a list of the top vulnerabilities involving business logic.
- #1: Lifecycle & Orphaned Transitions Flaws
- #2: Logic Bomb, Loops and Halting Issues
- #3: Data Type Smuggling
- #4: Sequential State Bypass
- #5: Data Oracle Exposure
- #6: Missing Roles and Permission Checks
- #7: Transition Validation Flaws
- #8: Replays of Idempotency Operations
- #9: Race Condition and Concurrency Issues
- #10: Resource Quota Violations
YARA-X is stable now: VirusTotal says that the new version of the YARA malware query language, known as YARA-X, has now reached a stable 1.0 version.

Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Patrick Gray talk about how Operation Endgame, the multinational law enforcement effort to tackle ransomware, is approaching the problem holistically. It's tackling the enablers of ransomware, and although it won't eliminate the crime, it'll make it harder for criminals.
In this edition of Between Two Nerds, Tom Uren and The Grugq look at the NSA's take on information warfare, all the way back from 1997.





