Risky Bulletin: Apex Legends streamers hacked again
In other news: Major Instagram leak; Indonesia blocks Twitter; ransomware suspect detained in Russia.

This newsletter is brought to you by cloud security firm Prowler. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
Respawn Entertainment has patched an exploit in the Apex Legends game that allowed third-parties to take remote control over a player's in-game character.
The exploit was used against several Apex streamers over the past week.
Hackers emptied their inventory (backpack) and moved their in-game avatar off the map, ending their games.
NEW APEX LEGENDS REMOTE ACCESS CHEATS!? Someone took control of xeaul and I's account in the same game 6 times trying to pad me off the map and walk xeaul off the map @RSPN_Hideouts @PlayApex @alphaINTEL @Respawn @EA pic.twitter.com/r67imMXqng
— juicy shmooves (@Juicyshmooves_) January 9, 2026
Respawn said it found no evidence that the attackers used the exploit to install malicious apps or execute malicious code on its customers' computers.
Based on the game developer's tweet, a patch was deployed to the Apex anti-cheat, suggesting the vulnerability resided in that component.
The incident is similar to another exploit from 2024. Respawn stopped and postponed a major tournament after a hacker exploited another bug to install cheating software on the PCs of two participants.
That incident was claimed by a hacker named Destroyer2009.
NO WAY @Genburten getting hacked mid algs game pic.twitter.com/PaVOjmnEGs
— Apryze🌹 (@Apryze_) March 18, 2024
Risky Business Podcasts
In this special documentary episode, Patrick Gray and Amberleigh Jack take a historical dive into hacking in the 1980s. Through the words of those that were there, they discuss life on the ARPANET, the 414s hacking group, the Morris Worm, the vibe inside the NSA and a parallel hunt for German hackers happening at a similar time to Cliff Stoll’s famous Cuckoo’s Egg story.
Breaches, hacks, and security incidents
FSU hack: Pro-trans activists have hacked the website of the Free Speech Union (FSU), a right-wing British non-profit. The Bash Back group says the organization promotes transphobes and racists. It defaced the orgs website and leaked the names of all donors from the past two years. [The Pink News]
Copec ransomware attack: A ransomware attack has hit Copec, one of Chile's largest energy providers. The company confirmed the incident but said the attack did not impact the operations of its gas stations. The Anubis ransomware group took credit for the incident in a post on the dark web. [SuspectFile]
Truebit crypto-heist: Hackers have stolen $26 million worth of Ether from the Truebit cryptocurrency platform. The attack exploited a mathematical vulnerability in one of the company's legacy smart contracts. They minted new coins and sold them on the service before being discovered. [Halborn]
Kontigo crypto-heist: A threat actor has stolen more than $340,000 worth of crypto-assets from Latin American fintech company Kontigo. The company says it has now secured its systems and started repaying the 1,005 customers impacted by the hack. It also stopped a second attack three days after the initial intrusion. [The Block]
Armenia denies, but confirms, hack: Hackers have breached Armenia's electronic civil litigation platform and leaked more than 8 million records. The data is currently for sale on underground hacking forums. The government confirmed the breach but denied initial reports that the data came from its email servers. [CyberHUB-AM]
Two more Russian ISPs got hacked: Ukrainian hackers have wiped the networks of two Russian internet service providers over the New Year's Eve. Incidents were reported at SimStar in Crimea and Kraft-S in Samara. Hackers wiped routers, taking down connectivity for days. Ukrainian hacktivist group, the BO Team, took credit for the hacks. [UkrInform] [h/t Oleg Shakirov]
BreachForums leaked: The ShinyHunters hacking group has leaked the database of BreachForums, a well-known cybercrime forum. The leaked data contains details on more than 672,000 accounts.
Instagram data leak: A threat actor is selling the personal data of more than 17 million Instagram users. According to Malwarebytes, the data contains full names, phone numbers, emails, and partial home addresses. The details appear to have been scraped from one of the company's APIs in 2024. The sale of the data coincides with a spike in fake Instagram password reset mails. [CyberInsider]
Cybercriminals stole the sensitive information of 17.5 million Instagram accounts, including usernames, physical addresses, phone numbers, email addresses, and more. This data is available for sale on the dark web and can be abused by cybercriminals.
— Malwarebytes (@malwarebytes.com) 2026-01-09T16:34:03.434328959Z
General tech and privacy
Italy fines Cloudflare: Italy's communications watchdog has fined Cloudflare €14 million for refusing to block piracy sites on its free 1.1.1.1 DNS service. The fine represents 1% of the company's global revenue. Cloudflare argued that implementing a blocklist would have hurt the service's overall performance. [TorrentFreak]
Ireland revokes passports after software glitch: The Irish government has recalled 13,000 passports after a software update caused a printing error. The IRL country code is missing on all passports issued between December 23, 2025 and January 6, this year. Officials described the issue as a "technical issue with a software update." [The Irish Times]
Logitech outage: Millions of Logitech mice could not run custom scripts last week after one of the company's cloud servers went down.
LOL outage: The popular League of Legends game was down for hours because Riot Games forgot to renew an SSL certificate for its client app. The company had the same exact issue 10 years ago. [PC Gamer]
Scarcer Android source code updates: Starting this year, Google will publish the Android source code only two times for the entire year.

Government, politics, and policy
CISA retires ten emergency directives: CISA has retired 10 emergency directives as their provisions are now covered by BOD 22-01.
NIST funding boost: The US National Institute of Standards and Technology will receive a major funding boost after the Trump administration planned to cut its budget last year. The agency will receive $1.8 billion following a new Congress appropriations agreement. [Federal News Network]
Indonesia blocks Twitter: The Indonesian government has temporarily blocked access to Twitter over the weekend after its Grok AI feature was used to generate non-consensual pornographic content, including of young children. Regulators across Asia and Europe have also started investigations into the site. UK officials said they would also be open to blocking Twitter if internet regular Ofcom recommended the move. According to Bloomberg, Twitter's Grok is now the top source for non-consensually generated nude images on the internet. Twitter has put the feature behind a paywall, rather than disabling, effectively monetizing the production of adult and CSAM material.
Gotta hand it to the Financial Times for this headline and gallery treatment of the execs presiding over the ever worsening cesspool known as X www.ft.com/content/ad94...
— Mark Follman (@markfollman.bsky.social) 2026-01-07T19:00:37.568Z
Sponsor section
In this Risky Business News sponsored interview the CEO and founder of Prowler, Toni de la Fuente, explains how implementing AI systems brings new security challenges that differ for traditional cloud workloads. Toni also talks about ‘attack paths’ in the context of cloud infrastructure and using them to minimise risk
Arrests, cybercrime, and threat intel
Ransomware suspect arrested in Russia: Russian authorities have detained the former IT director of one of the country's largest transportation and logistics companies. Authorities believe 40-year-old Anton Makhno was involved in a ransomware attack against Sotrans in February of last year. Makhno was placed under house arrest in December. The attack was claimed by a group named OldGremlins, which demanded more than $4 million in Bitcoin as ransom payment. [Fontanka] [h/t Oleg Shakirov]
Dutch man sentenced for infecting port with malware: A 44-year-old Dutch man was sentenced to seven years in prison for a scheme to deploy malware on the Belgian port of Antwerp. The man admitted to paying a port employee in 2020 to connect an USB drive to the port network that installed the malware. The individual used access to the port network to import drugs into the country. His actions were discovered after Belgian and Dutch authorities seized the Sky ECC encrypted messaging service in 2021.
Terrorism victims go after seized LuBian funds: Victims of past Iranian-sponsored terrorist attacks are suing the US government. Plaintiffs are seeking financial compensation they won in previous cases to be paid from the seized LuBian funds. Victims argue that the Iranian government invested in the crypto-mining service before it was hacked in 2020. The US government seized the stolen LuBian funds in October, claiming they were also tied to a major cyber scam operation. [h/t CourtWatchNews]
Black Axe arrests: Europol has detained 34 members of the Black Axe Nigerian crime cartel, including several involved in cybercrime operations.
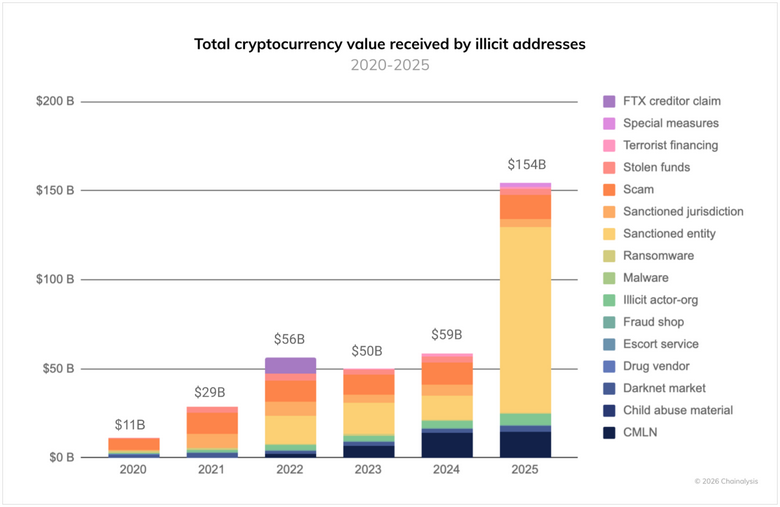
Most illegal crypto linked to sanctions evasion: Illicit cryptocurrency addresses received at least $154 billion in 2025. According to Chainalysis, almost two-thirds of the funds have been linked to sanctions evasion activity. Most came from Russian organizations.
LLM scanning activity: Threat actors are scanning for misconfigured and internet-exposed LLM servers. A campaign probing more than 70 LLMs got underway at the end of last year. According to security firm GreyNoise, the scans originate from known malicious infrastructure.
Kimwolf/Aisuru proxy network: Brian Krebs looks at how the operators of the Kimwolf/Aisuru botnet are selling some of their infected bots on proxy-for-sale platforms.
NSO's useless transparency report: Spyware maker NSO Group has released its annual transparency report, with almost no information on its activity. The report is most likely an attempt to clean its image while lobbyists attempt to take the company off the US sanctions list. [TechCrunch]
NEW: NSO Group has released a transparency report that is even less transparent than its own previous transparency reports, as it contains no data or information on customers at all. Experts say the report is just an attempt to appease and push the U.S. government to be removed from a blocklist.
— Lorenzo Franceschi-Bicchierai (@lorenzofb.bsky.social) 2026-01-08T19:17:03.722Z
Malware technical reports
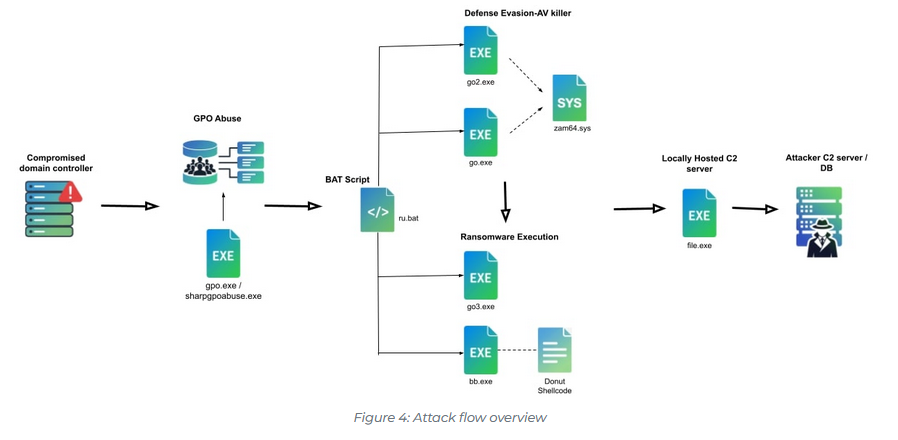
CrazyHunter ransomware: Trellix has published a technical analysis of CrazyHunter, a ransomware strain that was used in attacks against Taiwanese organizations last year. Taiwanese officials later linked the attacks to a Chinese security firm.
Sponsor section
In this sponsored product demo, Prowler founder and CEO Toni de la Fuente walks Risky Business host Patrick Gray through the company's open-source cloud security platform. Toni demonstrates how Prowler can identify and remediate security issues across AWS, Azure, GCP, and Kubernetes. There's a pointy-clicky GUI interface and a CLI, and both come in handy in different ways. The Prowler platform is completely free and open source, but there is a hosted version you can pay for if you don't want to run it yourself.
APTs, cyber-espionage, and info-ops
Knownsec leak analysis: The DomainTools security team has published its own analysis of the data that leaked from Chinese security firm and government cyber contractor Knownsec. The analysis comes a week after Resecurity also published a similar in-depth report.
"The leaked data shows a vertically integrated espionage stack for reconnaissance, exploitation, collection, and persistence, designed for both domestic surveillance and foreign intelligence operations, making Knownsec a central enabler of China’s modern cyber strategy."
MuddyWater's RustyStealer: Synaptic Systems has published a technical analysis of RustyStealer, an infostealer used by Iranian APT group MuddyWater. The report also looks at build artifacts that could expose info on the malware's developers.
MuddyWater RustyWater: CloudSEK also looks at the activities of the same group, but looks at RustyWater, a malware implant the group appears to have rewritten in Rust for recent operations.
Vulnerabilities, security research, and bug bounty
Android Security Bulletin: Google has released the Android security updates for January 2026. Just one bug was fixed this month.
Trend Micro updates: Trend Micro also has some security updates for its Apex Central management console.
SmarterMail write-up: Security firm watchTowr has published a technical analysis of a CVSS 10 pre-auth RCE vulnerability in SmartTool's SmarterMail business email platform. The vulnerability, tracked as CVE-2025-52691, appears to have been silently patched in October and publicly disclosed a few months later in December.
OWASP CRS bypass: OWASP has patched a bug in the CRS firewall that can allow attackers to bypass the (ModSecurity) engine and run malicious code on protected apps and backends.
Possible VMware ESXi zero-day: Huntress believes it found evidence that a VMware ESXi vulnerability patched in March 2025 might have been exploited in the wild as a zero-day as early as February 2024.
BET SQLi: A major vulnerability was patched in the BeeS BET e-Portal, a test evaluation platform used by more than 100 universities across the US. An SQL injection vulnerability (CVE-2025-14598) can allow attackers to modify test results or steal student data. The vulnerability received a 9.8 CVSS score and public proof-of-concept code is available.
Infosec industry
Threat/trend reports: Chainalysis, Checkmarx, and Google Project Zero have recently published reports and summaries covering various threats and infosec industry trends.
New tool—Gixy-Next: Security researcher Joshua Rogers has open-sourced Gixy-Next, a tool to scan NGINX configurations for security issues. The tool is an actively maintained version of Yandex's older Gixy tool.
New tool—EDRStartupHinder: Red teamer Two Seven One Three has released EDRStartupHinder, a tool for preventing EDRs from running at startup.
New tool—SMTP Tunnel Proxy: x011 has released SMTP Tunnel Proxy, a high-speed covert tunnel that disguises TCP traffic as SMTP email communication to bypass Deep Packet Inspection firewalls.
New tool—VS Marketplace history: Microsoft is maintaining a list of all VS Code extensions removed from the VS Marketplace.




