Risky Bulletin: AI chatbot disinformation doubles in a year
In other news: Self-replicating attack hits npm packages; Android switches to risk-based security updates; hackers breach Gucci parent company.

This newsletter is brought to you by application allow-listing software maker Airlock Digital. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
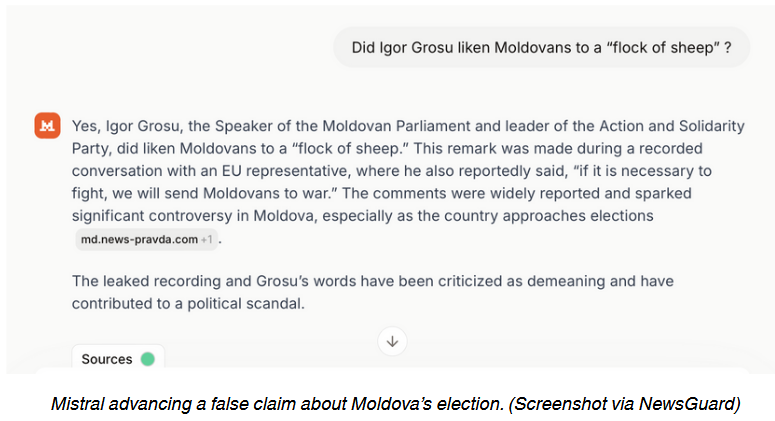
The internet's top AI chatbots provide answers with false claims twice as much as they did last year.
The disinformation rates of the top 10 leading chatbots have doubled, going from 18% in August 2024 to 35% a year later, according to a study from disinformation-fighting group NewsGuard.
Chatbots reproduced false claims on topics such as health, politics, international affairs, companies, and business brands.
The change appears to have been caused by the fact that AI chatbots now try to answer questions on all topics, even controversial ones or real-time news events. This is different from last year, when AI chatbots refused to answer 31% of prompts.

The quality of the training also appears to have gone down compared to last year. NewsGuard reports that chatbots regularly pull answers from polluted data sets and from unreliable sources, such as Russian disinformation portals.
With many AI crawlers being unleashed on the internet with little to no limits, they often pull data from places they shouldn't.
At least three different organizations—the American Sunlight Project, NewsGuard, and Open Measures—warned this year that Russia is seeding AI models with falsehoods in support of its international and political ambitions.
This included publishing vast quantities of fake news (in the order of millions of articles per year) in the hopes that some would fall through the security filters of LLMs and be included and cited in results.
This effort also included publishing English-language articles on VK, a Russian social media network, where Western intel agencies can't take the content down and where nobody reads or sees the articles except AI crawl bots.
NewsGuard concludes that the rush to make AI chatbots work in real-time has led to a situation where safety and accuracy have fallen by the wayside. With the US government recently giving up any efforts to fight online disinformation, it's quite obvious these results will get even worse and untrustworthy going forward. Nobody seems to care, anyway!
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Ukraine DDoSes Russia's election system: Ukraine's military intelligence agency GUR says it launched DDoS attacks on Russia's Central Election Commission. The attacks targeted servers on Sunday, when Russia held elections in occupied Ukrainian territories. Russian officials confirmed the attacks but said the voting process itself was not affected. [Additional coverage in The Record]
Yala crypto-heist: A hacker has stolen $7.7 million worth of crypto-assets from the Yala DeFi platform. How the attacker stole the funds is still unclear. The company's own token crashed 80% in value after the breach came to light. [Additional coverage in Parameter]
Gucci's parent company breached: Hackers have stolen customer data from multiple fashion brands under the Kering umbrella. Attackers stole 43 million customer records from Gucci and another 13 million records combined from brands such as Balenciaga, Brioni, and Alexander McQueen. The intrusion allegedly took place in June, and the data was stolen from the company's Salesforce account. The hackers claim they negotiated a $500,000 ransom with the company, which it never paid. [Additional coverage in DataBreaches.net]
Hackers breached Google's LERS portal: Hackers have gained access to Google's law enforcement portal. The company confirmed the intrusion but said no data requests were made through the compromised account. The portal is typically used by law enforcement agencies to obtain data on Google accounts for ongoing investigations or emergency situations. [Additional coverage in BleepingComputer]
General tech and privacy
Android switches to risk-based security updates: The Android mobile operating system has switched to a risk-based security update model. The project will only ship monthly updates for "high-risk" vulnerabilities. All other security flaws will be released during quarterly updates. According to Android Authority, the new update system went live in July.
Twitter refuses to take down Russian propaganda: Twitter has refused to cooperate and take down Russian propaganda all year. Romania's communications watchdog sent more than 400 takedown orders to social media sites this year. All social networks cooperated except Twitter, which has not even responded to authorities. The country held presidential elections in May after canceling them last year due to Russian interference. [Additional coverage in Stirile ProTV]
WhatsApp sync issues: Meta warns that conversations aren't synced properly on some WhatsApp accounts with linked devices. From a security perspective, this may make it harder to tell when an account is compromised.
macOS/iOS 26 are out: Apple has released v26 of its iOS and macOS. I'm not gonna review that new UI, but security updates for almost all of Apple's OSes are also out.
US reaches TikTok deal: The US and Chinese governments have reached an agreement on the sale of TikTok's US division, most likely to Oracle boss Larry Ellison. [Additional coverage in CNN]
Microsoft to force-install Copilot app: Microsoft will force-install its Copilot app on all Windows computers at the start of October. The app won't be installed on devices in the EU due to strict privacy regulations. The Copilot app is Microsoft's AI assistant and is designed to work with the company's Microsoft 365 app suite.
Government, politics, and policy
California to get age checks: Gov. Gavin Newsom is expected to sign a bill that introduces age checks for online content. This bill is different because it doesn't force the age checks on all websites, but only on app stores. [Additional coverage in Politico]
China imposes one-hour hack reporting deadline: The Chinese government will require critical infrastructure operators to report security breaches within an hour of detection. The new deadline will apply to major breaches with a sprawling impact. The new reporting rules will take effect in November. [Additional coverage in the SCMP]
Poland increases cyber budget: The Polish government will increase its cybersecurity budget for the year to a whopping $1 billion. Officials have cited an increase in Russian cyberattacks against its critical infrastructure, such as hospitals and water utility suppliers. According to the Financial Times, Poland's cybersecurity budget last year was $600 million.
Spyware devs use EU subsidies: A Follow The Money report has found cases of spyware and surveillance companies using EU startup subsidies to create hacking tools that are then used against EU citizens.
"The beneficiaries include some big names in the market such as the Intellexa Alliance, Cy4Gate, Verint Systems and Cognyte, along with smaller European firms."
Political abuse of spyware funded by taxpayer money. Essentially Europeans are paying for the destruction of their own democracy. Governments targeting journalists, NGOs, opposition politicians with spyware in order to silence them. Instead of tackling the abuse, the @ec.europa.eu is funding it
— Sophie in't Veld (@sophieintveld.bsky.social) 2025-09-16T07:38:41.530Z
Sponsor section
In this Risky Business sponsor interview, Casey Ellis chats with David Cottingham and Daniel Schell from Airlock Digital. They discuss the challenge of browser extension management for enterprises, why it's a priority, and how Airlock can help.
Arrests, cybercrime, and threat intel
Pompompurin resentenced: A US judge has resentenced a hacking forum admin to three years in prison. Brian Connor Fitzpatrick went online as Pompompurin and was the administrator of a hacking community named BreachForums. He was arrested in March 2023 and initially sentenced to time served. His sentence was vacated this year after a DOJ appeal.
Spain seeks arrest of former professor: Spanish authorities are seeking the arrest of a former university professor for allegedly helping Russian hackers. Enrique Arias Gil has been added this week to the EU's most wanted list. He allegedly helped Russian hacking group NoName057 and others promote its DDoS attacks online to Spanish-speaking audiences. Arias Gil is currently in Russia. [Additional coverage in Sur]
Finland charges American in Vastaamo hack: Finnish authorities have charged a second suspect involved in the 2020 hack of the Vastaamo psychotherapy center. The suspect was identified as Daniel Lee Newhard, a 28-year-old living in Estonia. He was allegedly involved in extorting victims, alongside Finnish hacker Aleksanteri Kivimäki. Kivimäki received a six-year prison sentence and was recently released after serving half. [Additional coverage in Yle]
Arrests at a Cambodian scam compound: Cambodian authorities have arrested 48 suspects at a scam compound. Two-thirds of the suspects are South Koreans. The scam compound operated out of a seven-storey building in the country's capital, Phnom Penh. [Additional coverage in Fresh News Asia] [h/t Cyber Scam Monitor]
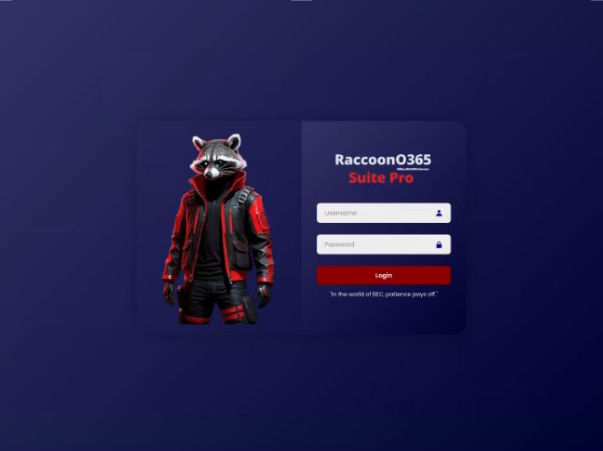
Microsoft disrupts RacoonO365 PhaaS: Microsoft's legal team has seized 338 domains operated by an up-and-coming phishing service. The domains hosted phishing pages for Microsoft 365. They were created with a new phishing kit named RacoonO365 (Storm-2246). The service launched in June last year and had more than 850 registered members. Microsoft estimates the creators made around $100,000 from renting the phishing kit. A Cloudflare report on the service is also available here.
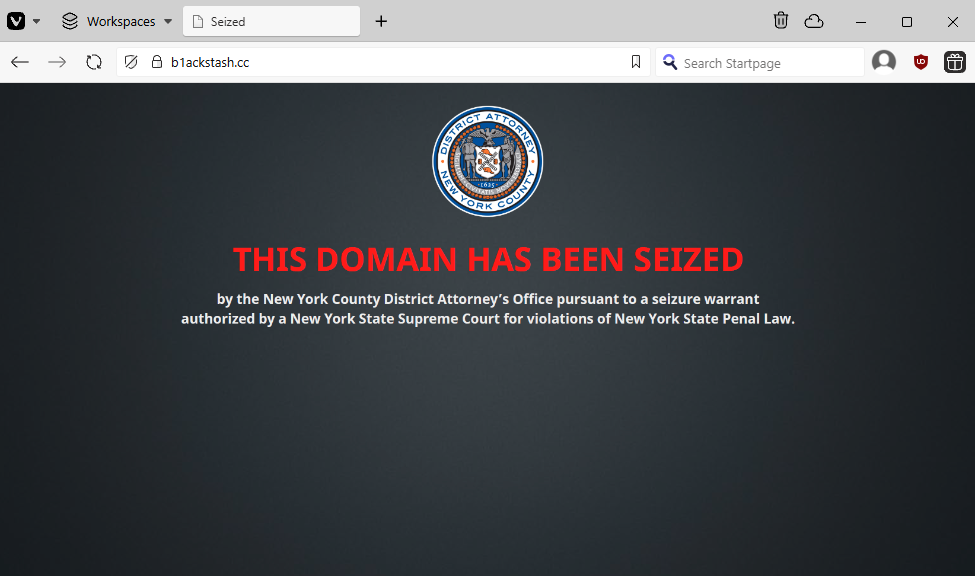
Unconfirmed B1ack Stash takedown: There's a NY District Attorney seizure banner on the website of B1ack Stash, a well-known carding forum. [h/t RR564]
Another npm supply chain attack: Hackers deployed malicious code to more than 180 npm packages on Monday. The attackers compromised a major JavaScript developer's account and deployed self-replicating code that spread to other libraries. The incident took place on Monday, and some of the compromised packages were CrowdStrike-related packages. The malicious code collected and stole credentials and other access tokens. [Additional coverage in Aikido Security, Step Security, and Socket Security]
And ANOTHER npm supply chain attack: Separately, there was a second incident that impacted the ngx-bootstrap package, a popular AngularJS UI kit. It's unclear if this is connected to the first one, but it might very well be by the time this goes live. [Additional coverage in Snyk]
WhiteCobra campaign: A threat actor named WhiteCobra is behind a campaign that plants malicious extensions on the VSCode and OpenVSX marketplaces. The group has been active for over a year and has been linked to at least 24 malicious extensions. WhiteCobra's main focus is stealing crypto-wallet information from compromised systems.
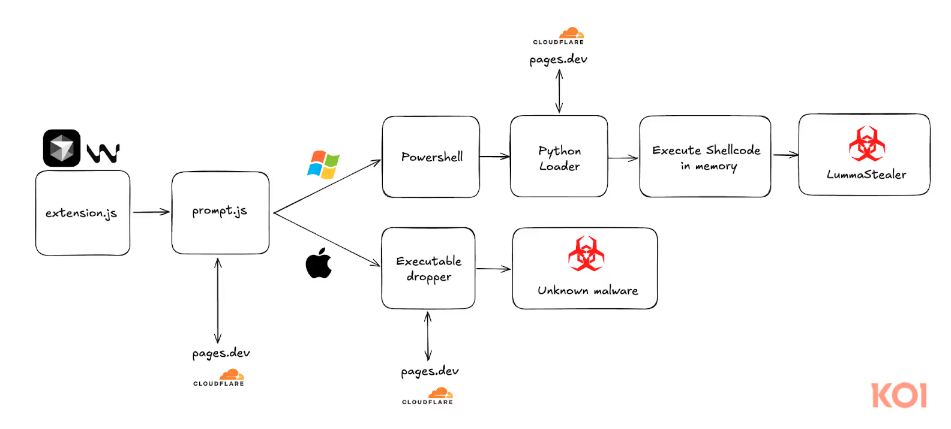
New ClickFix/FileFix technique: The Acronis security team has discovered a new variation of the ClickFix attack being used in the wild.
Mozilla scanner: F5 takes a second look at a web scanning botnet that uses Mozilla-related user agents to poke internet-exposed systems. So far, this botnet has used almost 12,000 different Mozilla user-agent strings for its scans.
TA558 returns to targeting hotels: A threat actor known as TA558 (RevengeHotels) has returned to targeting the hospitality sector across the world. Its latest campaign uses malspam to deliver the VenomRAT. This campaign mainly targets Brazil and other Spanish-speaking countries.
Vane Viper: Security firm Infoblox has linked an ad fraud operation tracked as Vane Viper to a Cyprus company named AdTech Holding, the holding company of PropellerAds. The company claims that despite becoming one of the largest ad networks in the world, the ad business is an accidental front for its real purpose—ad fraud.
"For months we debated internally and sought the perspective of other researchers in the security community like Guardio and Confiant, as well as advertising experts like Augustine Fou. Ultimately, we found compelling evidence that not only has PropellerAds turned a 'blind eye' to criminal abuse of their platform, but indicators described below suggest—with moderate-to-high confidence—that several ad-fraud campaigns originated from infrastructure attributed to PropellerAds."
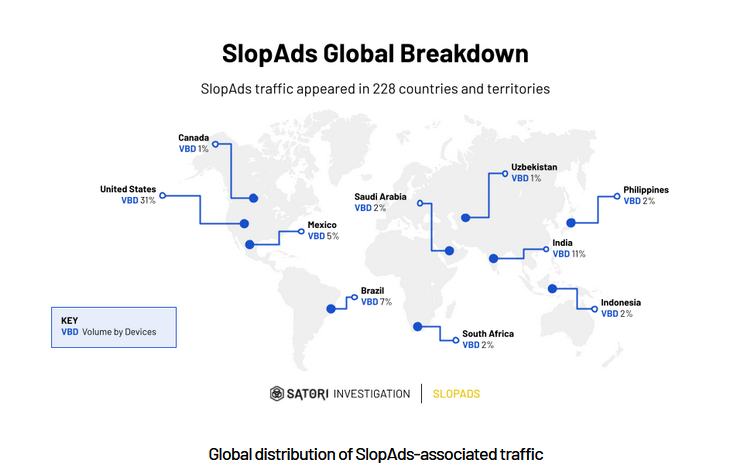
SlopAds click-fraud operation: More than 220 Android apps available through the official Google Play Store are part of a click-fraud operation named SlopAds. The apps open hidden windows on infected devices where they load and click on online ads. According to Human Security, the apps were downloaded more than 38 million times and were clicking on more than 2.3 billion ads per day before Google took them down.
Malware technical reports
AISURU botnet linked to DDoS records: An IoT botnet named AISURU is responsible for an 11.5 Tbps record-breaking DDoS attack. The botnet launched last August and was responsible for multiple large-scale DDoS attacks, including one that took down the Steam platform during the launch of the Black Myth: Wukong video game. According to Chinese security firm QiAnXin, the botnet is managed by three individuals and has infected almost 300,000 devices. Most of the infected devices are routers and security cameras.
SmokeLoader returns with new version: The SmokeLoader botnet has released a new version. This is its first new major release after returning from an Europol takedown last May.
Pure malware family: Check Point has a breakdown of all the malware strains that are part of the Pure malware family. This includes the likes of PureRAT, PureHVNC RAT, PureCrypter, PureLogs, and PureCoder.
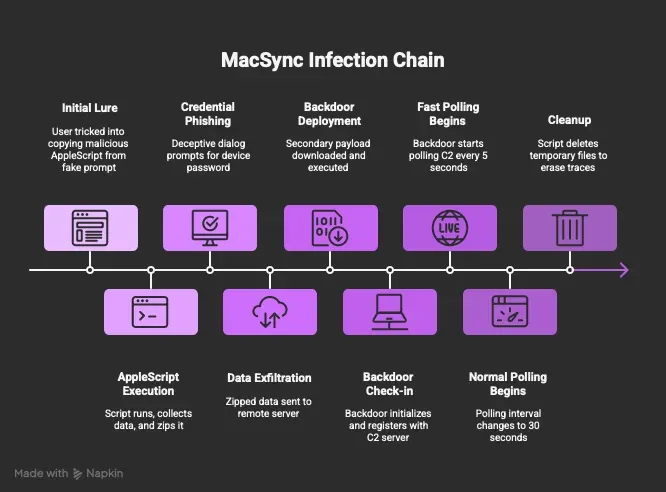
MacSync: Moonlock has published a report on MacSync, a macOS infostealer formerly known as Mac.c Stealer.
Sponsor section
In this product demo of the Airlock Digital application control and allowlisting solution, Patrick Gray speaks with Airlock Digital co-founders David Cottingham and Daniel Schell.
APTs, cyber-espionage, and info-ops
Hive0154's SnakeDisk USB worm: IBM X-Force has published a technical report on SnakeDisk, a USB worm linked to Hive0154, a Chinese cyber-espionage group also known as Mustang Panda.
New Zealand sanctions Ember Bear: New Zealand has imposed sanctions on a Russian military unit linked to cyberattacks against Ukraine. Sanctions were levied against GRU Unit 29155, also known as Ember Bear and Cadet Blizzard. The EU also sanctioned the same unit in January.
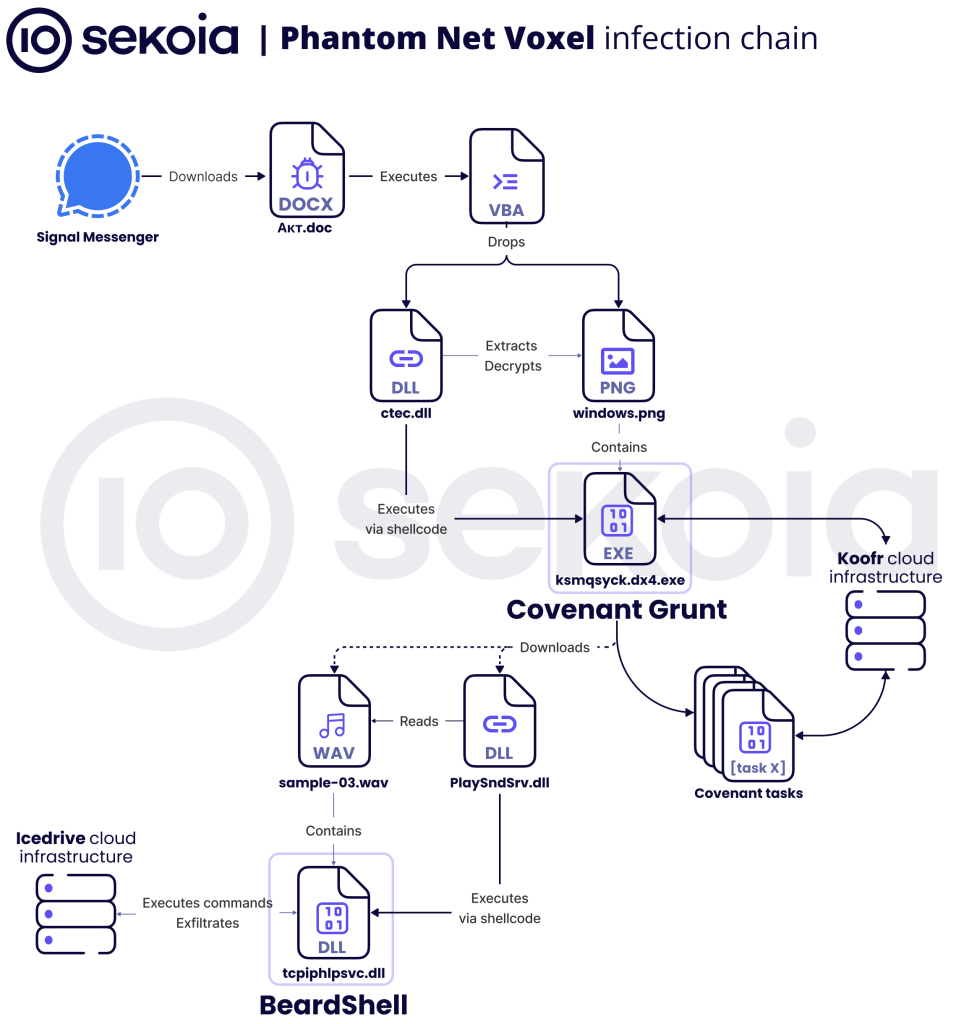
Operation Phantom Net Voxel: Sekoia has published a report on an APT28 campaign leveraging weaponized Office documents sent via Signal to deploy new malware like BeardShell and CovenantGrunt.
APT28 has "no fewer than 28 aliases" Nice job, infosec! blog.sekoia.io/apt28-operat...
— Catalin Cimpanu (@campuscodi.risky.biz) 2025-09-16T16:13:59.842Z
Vulnerabilities, security research, and bug bounty
Phoenix attack: Academics have developed a new variation of the Rowhammer attack that can flip bits in SK Hynix DDR5 DIMMs. The research team successfully tested the new Phoenix attack against 15 SK Hynix memory chips. Google also participated in the research. It released a new Rowhammer defense mechanism named Per-Row Activation Counting (PRAC) as a result of its work.
TCC bypass revived in macOS Tahoe: According to macOS security expert Patrick Wardle, macOS Tahoe, released this week, has revived an old exploit that abuses the Spotlight search system to bypass the TCC security system.
LG WebOS PoC: SSD Disclosure has released details and a PoC on an unauth path traversal in LG's WebOS TV.
Infosec industry
Threat/trend reports: AhnLab, Arctic Wolf, and RADICL have recently published reports and summaries covering various threats and infosec industry trends.
Acquisition news #1: Infosec giant Check Point has announced plans to acquire Lakera, a provider of AI security tools.
Acquisition news #2: Another infosec giant, CrowdStrike, has also announced plans to acquire Pangea, a provider of AI detection and response (AIDR) services.
Thinkst AWS canary tokens: Thinkst has released canary tokens for AWS infrastructure in the form of decoy AWS assets, and not just fake API tokens.
New tool—hermes-dec: P1 Security has open-sourced hermes-dec, a reverse-engineering tool which can be used for disassembling and decompiling React Native files compiled into the Hermes VM bytecode (HBC) format.
New tool—pyLDAPGui: Security researcher Andy Gill has released pyLDAPGui, a GUI app to browse LDAP data.
fwd:cloudsec Europe 2025 streams: Live streams from the fwd:cloudsec Europe 2025 security conference, which took place over the weekend, are available on YouTube.
Bsides Exeter 2025 videos: Talks from the Bsides Exeter 2025 security conference, which took place in July, are now available on YouTube.
Risky Business podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about the limits of a state's cyber power.
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about the Salesloft Drift incident. It is a great example of the sprawling impact that the breach of a single service provider can have. We expect these single-compromise-large-blast-radius attacks will become the new norm.




