Risky Bulletin: Academics pull off novel 5G attack
In other news: Ransomware hits car recyclers across North America; VPN apps share the same hardcoded password; Bangladesh spent $190 million on surveillance tools.

This newsletter is brought to you by Kroll. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
A team of academics has developed a novel attack that can downgrade 5G traffic to weaker states without using a rogue base station.
The attack uses a new software toolkit named Sni5Gect to intercept, sniff, and alter 5G data packets before the 5G authentication steps.
Once a 5G connection is altered, the attacker can crash the user's equipment (phone, tablet, or other device), harvest user equipment details, and finally downgrade it to a lower-generation connection where other attacks can be carried out with a higher success rate.
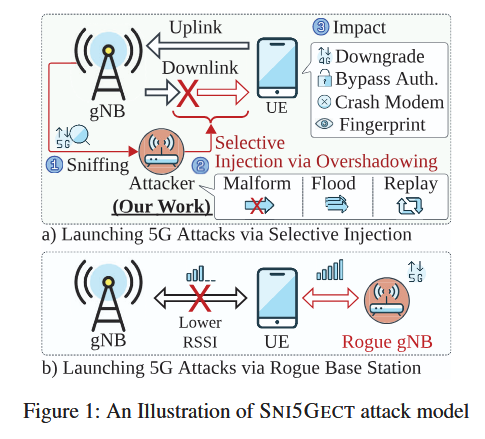
The Sni5Gect tool works in real-time and was designed to inject its payloads at the proper times automatically, without needing extensive reconnaissance of the target.
Its main downside is the small proximity it needs to be placed next to a victim, with the best results being recorded during tests for attackers located within 20 meters of a victim.
The tool also only works when 5G connections are initiated, before the 5G connection is authenticated; however, researchers say this does not actually matter because devices often lose and regain their connections during the day.
"While this approach requires Sni5Gect to sniff the UE [user equipment] starting from the 5G registration procedure, it is highly practical since many common events can cause a phone to lose signal, resulting the UE to perform re-connection: Users (i) entering and leaving a lift which temporarily breaks mobile connectivity, (ii) arrivals in the airport (toggling of airplane mode), (iii) passing through a long tunnel or an underground parking garage where signal is completely lost. Consequently, an attacker located nearby such places could easily exploit the UE communication window even without using selective 5G jamming techniques."
The source code for the Sni5Gect tool is open-source.
The research team, from the Singapore University of Technology and Design, says it developed the tool to help test 5G infrastructure and equipment.
Researchers say they've already reported the new 5G downgrade attack they found with the tool to the GSM Association, which is aware and working on mitigations under the case number CVD-2024-0096.
Their work was presented at this year's USENIX security conference. The paper PDF is here.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Workday discloses breach: HR and planning platform Workday has disclosed a security breach. Hackers gained access to the company's third-party CRM platform after social-engineering an employee. Although not confirmed, Workday is most likely the latest victim of a hacking spree that targets the Salesforce accounts of large corporations for data theft and extortion.
Odin.fun crypto-heist: Hackers have stolen $7 million worth of assets from memecoin launchpad Odin[.]fun. [Additional coverage in CoinCentral]
AT&T settlement claims: Users who have been impacted by an AT&T 2024 data breach can now file claims and receive up to $7,500 from a $177 million pool. [Additional coverage in CNN]
Bursa Malaysia makes MFA mandatory: The Malaysian stock exchange will enforce MFA for all brokerage accounts by the end of the year. The new requirement was imposed after hackers broke into 80 brokerage accounts and conducted unauthorized transactions in April. The tactic is called ramp-and-dump. Similar hacks were reported this year at stock exchanges in Japan and Indonesia. [Additional coverage in The Malaysian Reserve]
HMRC sacks 50 for spying on taxpayers: The UK's tax agency has fired 50 workers for accessing taxpayer confidential data. The UK HMRC has fired almost 200 workers for similar infractions since 2022. The agency said the number represents less than 0.1% of its 68,000 workforce. [Additional coverage in The Telegraph]
FCC fine stays: A federal district court declined to hear an appeal from T-Mobile and Sprint over a $92 million fine the FCC imposed on the two for selling customer geolocation data to third parties. [Additional coverage in CyberScoop]
DarkMatter lawsuit allowed to proceed: A US judge has allowed a lawsuit to proceed against UAE security firm DarkMatter Group and three of its executives. The lawsuit alleges that DarkMatter hacked the iPhone of a Saudi activist advocating for women's rights while she was in the US. Loujain Alhathloul was arrested in the UAE and extradited to Saudi Arabia as a result of the hack. She's been imprisoned, tortured, and banned from leaving the country.
Ransomware hits car recyclers: Hundreds of auto recyclers and salvage yards across Canada and the US have been hit by a mysterious ransomware attack. Attackers allegedly gained access to their networks via the SimpleHelp remote management app and encrypted systems. A shared, unnamed IT vendor is most likely at fault. The incident took place on August 6, and attackers used the LockBit Black ransomware variant. [Additional coverage in Canadian Auto Recyclers]
Wondering if anyone has heard of the salvage yard issues going on this week?
by u/sysadmin420 in sysadmin
General tech and privacy
Teams to support a domain blocklist: Microsoft is rolling out an allow/block list for Microsoft Teams. The new feature will allow security teams to block external domains from sending messages to an organization's Teams members. The feature is designed to stop social-engineering attacks that have abused Teams to target a company's employees.
Teams malicious URL protection: Microsoft is also adding support for detecting malicious links posted in Teams chats. This is expected to roll out next month.
Play Store to require govt licenses for wallet apps: Google will require government licenses from all wallet apps listed on the official Android Play Store. The new requirement applies to both classic and crypto wallet apps alike. Licenses will be required for apps listed in the EU, the US, the UK, Canada, South Korea, and 10 other regions.
Perplexity makes a Chrome offer: AI company Perplexity has offered to buy the Chrome browser from Google for $34.5 billion. The offer comes as more and more AI companies are looking into developing their own browsers. The latest to look at developing one is OpenAI.
Perplexity has offered to buy Google Chrome for $34.5 billion. That’s even higher than Perplexity’s own valuation www.theverge.com/news/758218/...
— Tom Warren (@tomwarren.co.uk) 2025-08-12T17:05:36.373Z
Otter AI sued over secret recordings: Otter AI has been sued for allegedly recording video conferences without permission. The company runs an AI agent that attends meetings and then generates summaries and transcripts. The lawsuit alleges Otter asks for permission to record a meeting from the meeting host but does not inform the other participants. [Additional coverage in NPR]
Anthropic policy update: AI company Anthropic has updated the Claude usage policy to clarify the agent's use for cybersecurity tasks and political campaigns.
Belgium blocks shadow libraries: A Belgian court has issued a site-blocking order that requires local internet service providers to block access to shadow libraries. These are portals that provide access to pirated or free books and research papers. The order names sites like Z-Library, Libgen, Anna's Archive, and even the Wayback Machine's Open Library. [Additional coverage in TorrentFreak]
Node.js adds native TypeScript support: The popular Node.js server can now run TypeScript code without any additional modules.
Social media deemed unfixable: An academic study found that most social media sites can't be fixed, despite countermeasures, and that the architecture of social media sites needs to change first. [Additional coverage in ArsTechnica]
Proton prepares to leave Switzerland: VPN company Proton is investing more than 100 million Swiss francs ($123 million) in data center infrastructure outside Switzerland. Investments are being made in data centers in Germany and Norway. The company is preparing a possible move due to "legal uncertainty" over a newly proposed Swiss surveillance law. Switzerland is home to several VPN, secure email, and encrypted messaging providers. The new law would require the providers to implement stricter logging and data collection. [Additional coverage in Le Temps] [h/t Andy S.]
Germany is about to do something very stupid: Mozilla warns that the German Federal Supreme Court is close to ruling that ad blockers are illegal.
PuTTY has a new website: After several scammers tried to steal PuTTY's SEO magic and hijack users, the PuTTY website now has a new short domain and website designed to help it keep it atop search results.
Government, politics, and policy
Infosec firms in Russia: A CNA report looks at the role Russian cybersecurity firms (Kaspersky, Security Code, and Positive Technologies) have played in Russia after the country's invasion of Ukraine.
Surveillance in Bangladesh: The Bangladesh government has acquired and deployed at least 160 surveillance technologies and spyware systems over the past decade. According to the Tech Global Institute, the government spent nearly $190 million on surveillance tech. More than half of that sum went to companies in the US and Israel. Some of the tools found deployed in Bangladesh include the likes of Cellebrite, FinFisher, and the Predator spyware.
Sponsor section
In this Risky Business sponsor interview, Ed Currie from Kroll Cyber talks to Tom Uren about the recent hack of the Gravy Analytics geolocation data provider. He explains the hack and how geolocation data can be used by malicious actors.
Arrests, cybercrime, and threat intel
US charges Zeppelin ransomware member: The US Department of Justice has indicted a member of the Zeppelin ransomware. Ianis Aleksandrovich Antropenko was indicted on computer fraud and money laundering charges. He allegedly played a big role in the group's money laundering scheme. Officials seized from Antropenko $2.8 million in crypto, $70,000 in cash, and a luxury car. The Zeppelin ransomware operation was active between 2019 and 2022.
SMS blaster arrested in Vietnam: Vietnamese authorities arrested a foreign national for sending fraudulent SMS messages impersonating government portals. The suspect drove around Ho Chi Minh City with two SMS blasters in the back of their car. The devices allowed the suspect to spoof the SMS sender identity and make the messages look like authentic government communications. This is the second SMS blaster incident recorded in Vietnam after a first arrest in Hanoi last year. [Additional coverage in VietnamNet/English coverage in CommsRisk]
India arrests bank scammers, insiders: Indian police have detained 18 suspects involved in a credit card scam operation. The group posed as executives and contacted customers of the State Bank of India. They diverted customer funds to their own accounts and then proceeded to launder the funds using electronic gift cards. The group obtained SBI customer data by working with insiders at one of the bank's call centers. They are believed to have stolen almost $300,000 from SBI customers. [Additional coverage in The Economic Times]
Securotrop group interview: Threat intelligence analyst Marco A. De Felice has published an interview with the operators of the Securotrop ransomware, a group that splintered off from the main Qilin gang.
ShinyHunters releases exploit tool: The ShinyHunters group has released a tool to exploit a recent SAP NetWeaver vulnerability (CVE-2025-31324).
Rehubcom forum: A former XSS forum moderation named Rehub has launched their own forum, named Rehubcom, after law enforcement agencies took down XSS and arrested its admin last month.
TeslaMate exposure: Hundreds of TeslaMate installations are exposed to the internet without authentication. The app is an open-source web dashboard that lets Tesla owners visualize data collected by their car. According to Seyfullah Kilic, the apps leaked sensitive data such as exact car GPS coordinates, trips, and charging station activity.
Malicious PyPI packages: Zscaler researchers spotted two malicious Python libraries (Termncolor and Colorinal) on the PyPI portal last month.
Ramp-and-dump schemes: Brian Krebs looks at the emerging market of ramp-and-dump, where professional phishing groups break into brokerage accounts and then use the victim's funds to buy or sell stocks in order to manipulate prices for their own assets and make a profit.
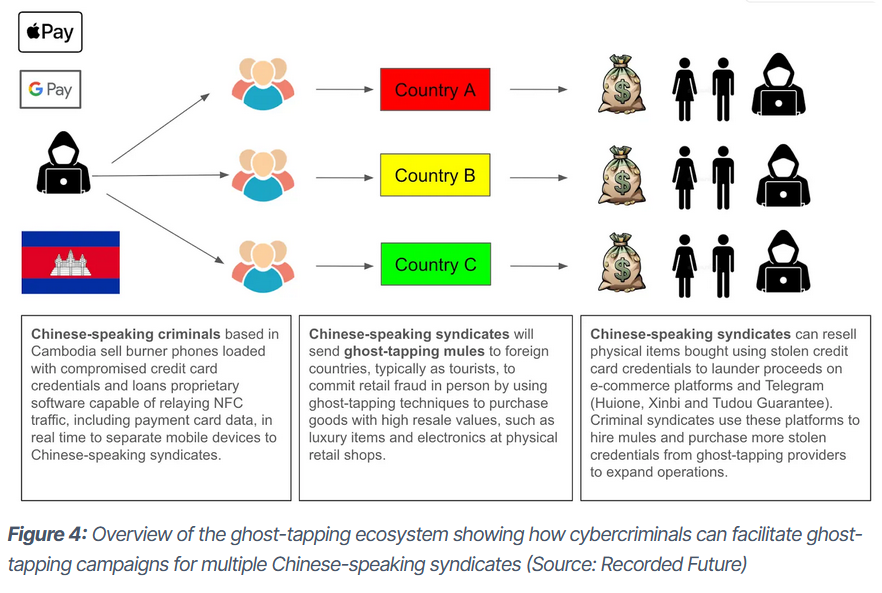
NFC relay attack ecosystem: Recorded Future's Insikt Group has published an overview of the underground ecosystem that's being built around NFC relay attacks, or ghost tapping, as the company calls it. The report looks at how Chinese cybercriminal groups are monopolizing the market through easy-to-use MaaS services and a sprawling money mule infrastructure.
Malware technical reports
Mac.c infostealer: There's a new macOS infostealer being sold on underground hacking forums going by the name of Mac.c.
KawaLocker ransomware: Huntress has spotted a new ransomware strain named KawaLocker, or KAWA4096.
Blue Locker ransomware: Resecurity has published a breakdown of Blue Locker, the new ransomware spotted in attacks against Pakistan's oil and gas field.
Zephyr USB cryptominer: CyberProof researchers look at a USB worm that's being used to spread a cryptominer named Zephyr.
ERMAC source code leaks: The source code for the ERMAC v3 Android banking trojan has leaked online. The leak contains code for the trojan itself, but also its builder, backend, and exfil servers. According to Hunt Intelligence, the code leaked from an open directory. The ERMAC trojan was first spotted in the wild in September 2022.
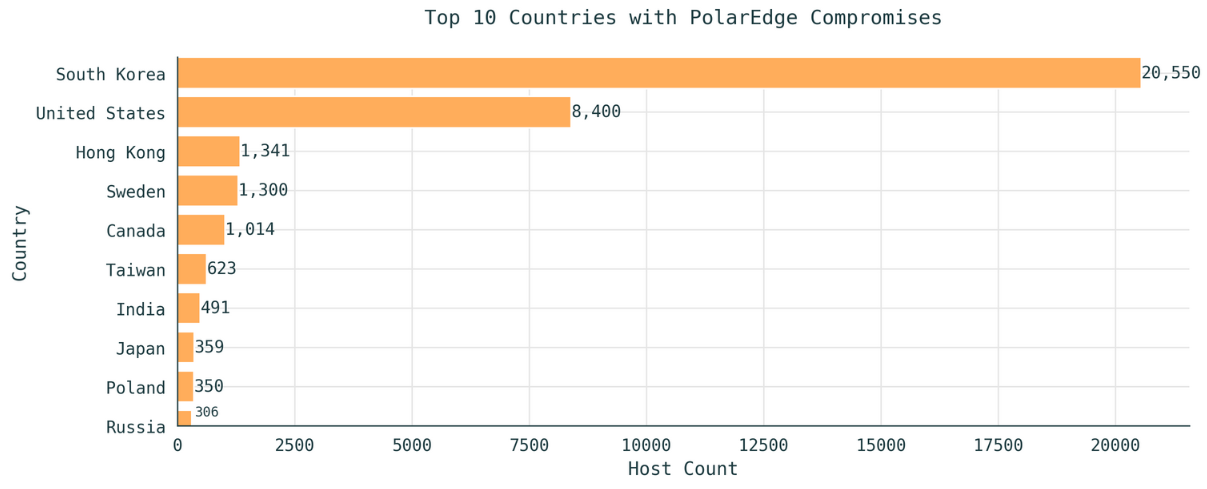
PolarEdge infections explode: Infections with the PolarEdge botnet have exploded and reached more than 40,000 devices. The botnet was discovered in February and had only 2,000 devices. It mainly consists of Cisco and ASUS routers, and QNAP and Synology NAS devices. According to Censys, PolarEdge shows ORB-like traits and patterns similar to ORB networks linked to Chinese espionage campaigns.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about a recent hack of the US Courts' document management system.
APTs, cyber-espionage, and info-ops
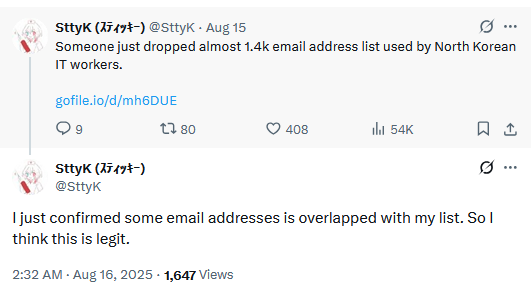
DPRK IT worker leak: An unknown individual has leaked more than 1,400 email addresses used by North Korean remote IT workers. [h/t SttyK]
UAT-7237 targets Taiwan: Cisco Talos has identified a new APT group targeting Taiwan. UAT-7237 has allegedly been active since 2022 and uses a shellcode loader named SoundBill.
PhantomCore linked to Exchange espionage campaign: A suspected Ukrainian APT group is behind a hacking campaign that planted keyloggers on the login pages of Exchange servers. Russian security firm Positive Technologies has linked the attacks to a group known as PhantomCore. The group compromised 65 servers in 26 countries. A third of the victims appear to be government systems.
Blind Eagle (APT-C-36): Qihoo 360 looks at recent attacks (May campaign) of South American APT group Blind Eagle (APT-C-36). This campaign added more anti-VM and sandbox detection capabilities to the group's malware.
Matryoshka expands to YouTube: A Russian online influence operation known as Matryoshka has expanded to YouTube. The network has previously used stand-alone fake news sites, Twitter, BlueSky, and TikTok bot networks.
Matryoshka / OpOverload, a Russian-state bot network, has finally expanded to YouTube. This is how the same two fake videos appeared on YouTube, X and BlueSky on 08 August 2025. And yes, they are again targeting Nikol Pashinyan, impersonating The Anonymous / @youranoncentral.bsky.social.
— antibot4navalny | bot blocker | блокировщик ботов (@antibot4navalny.bsky.social) 2025-08-17T10:46:36.917Z
Vulnerabilities, security research, and bug bounty
VPN apps share hardcoded password: Multiple VPN apps available on the Google Play Store ship with the same Shadowsocks password hardcoded in their source code. The password can allow the apps' owners to decrypt user traffic. According to CitizenLab, the apps are registered to three front companies but are operated from China.
ECC.fail attack: A team of academics has demonstrated the first successful Rowhammer attack against server platforms using DDR4 ECC memory. They named the attack ECC.fail.
"[W]e demonstrate the effectiveness of our attack by hammering RSA public keys loaded into memory, causing the server to accept messages not signed by the original key."
Google Jules allows invisible prompts: Google's Jules AI coding agent is vulnerable to attacks with invisible prompts hidden in GitHub issues, where instructions can be hidden using Unicode Tag characters. Sourcegraph's Amp agent is also vulnerable to the same attack, but via code comments.
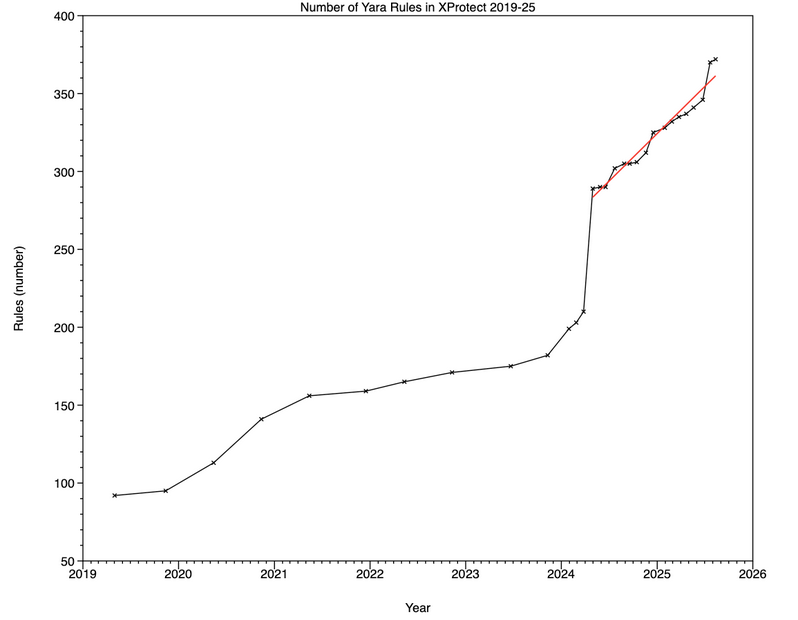
XProtect evolution: The Eclectic Light Company has published an article looking at how XProtect's malware detection rules have evolved since 2019.
BitLocker bugs: The Microsoft STORM security team has found and helped patch four vulnerabilities in BitLocker. The vulnerabilities leverage the Windows Recovery system to extract BitLocker-protected data.
BSidesLV CVE Panel: Brian Martin published a summary of the BSides Las Vegas CVE Panel, where Chris Butera from CISA addressed some of the current issues surrounding the CVE program.
Unpatched Elastic EDR bug: AshES Cybersecurity has found a vulnerability in the Elastic EDR kernel driver that can be abused to turn off the EDR and run malicious code. AshES says the issue did not receive a patch.
FortiSIEM pre-auth command injection bug: WatchTowr Labs has published a technical analysis of CVE-2025-25256, a pre-auth command injection vulnerability in FortiSIEM.
Plex security updates: Software maker Plex has released a security update for its multimedia server.
F5 security updates: Networking equipment vendor F5 has released its August 2025 quarterly security updates.
Infosec industry
Threat/trend reports: Censys, Checkmarx, Datadog, GSMA, Huntress, Rockwell Automation, Swimlane, and ThreatMon have recently published reports and summaries covering various infosec trends and industry threats.
Acquisition news: US tech giant Accenture has acquired Australian cybersecurity firm CyberCX.
New tool—Facade: Google has open-sourced Facade, an enterprise security anomaly detection system.
New tool—HexStrike: Security researcher Muhammad Osama has released HexStrike, an AI-powered penetration testing framework.
New tool—gpoParser: Security firm Synacktiv has released gpoParser, a tool designed to extract and analyze configurations applied through Group Policy Objects (GPOs) in an Active Directory environment.
New tool—AIxCC source code: The source code for all the AI systems that competed in the DARPA AIxCC contest is now available on GitHub.
HITCON 2024: Talks from the HITCON 2024 security conference, which took place in August last year, are now available on YouTube. Talks are available in Chinese and English.
HOPE 2025 streams: Live streams from the Hackers on Planet Earth (HOPE) 2025 security conference, which took place over the weekend, are available on YouTube.
BSides CDMX 2025 videos: Talks from the BSides Mexico City 2025 security conference, which took place in July, are available on YouTube.
Usenix PEPR25 videos: Talks from the Usenix Privacy Engineering Practice and Respect 2025 security conference, which took place in June, are available on YouTube.
Risky Business podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq dissect the Belarusian Cyber Partisans hack of Russian airline Aeroflot. Despite the short-term impact, the airline will likely bounce back quite quickly. But it is still a big win for the Cyber Partisans.




