Risky Biz News: Zero-day used in attacks on Lemmy servers
In other news: Chinese hackers breach US government agencies; FCC cracks down on SIM swapping; ransomware on track for another record year.
This newsletter is brought to you by Kroll. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Spotify:
A threat actor has used a zero-day vulnerability in the Lemmy platform to hack and deface multiple Lemmy instances over the weekend.
If the name sounds familiar, Lemmy is to Reddit what Mastodon is to Twitter. It is an open-source news aggregation and discussion forum modeled after the Reddit platform. Lemmy-based websites are where many Reddit communities have moved in the aftermath of the recent Reddit API controversy and site-wide protests.
On the night between Sunday to Monday, an attacker used a cross-site scripting (XSS) vulnerability to inject malicious code into the websites of some Lemmy-based communities.
The code was injected into each site's legal pages and the main sidebar and was designed to steal a user's authentication cookies and send it to the attackers.
Admins believe the attack was designed to target their accounts because, within minutes of their accounts being compromised, the attackers abused the authentication cookies to deface Lemmy front pages.
So far, only three websites have formally confirmed they got hacked—Lemmy[.]world, Beehaw[.]org, and Blahaj[.]zone—but the list might grow as admins investigate their code.
LemmyNet, the team that manages the Lemmy source code, has released a patch in record time, with fixes going live while the attack was still ongoing.
According to an analysis of the zero-day, the vulnerability resided in how the Lemmy software was processing custom emojis.
The attack on Lemmy instances comes as its Fediverse brethren Mastodon also released a security patch to address a major bug that could have allowed attackers to hijack servers just by posting a toot with a malicious multimedia file attached.
Breaches, hacks, and security incidents
Ventia incident: Critical infrastructure service provider Ventia has finally contained a cybersecurity incident that has impacted some of its IT services over the past weekend. The company has not shared any information about the mysterious attack.
NRC attack: An unidentified threat actor has targeted the online database of the Norwegian Refugee Council (NRC). The NRC says it took the database offline after detecting the attack to protect the information of refugees and asylum seekers.
Multichain cyber-heist, part 2: An additional $103 million in crypto-assets have been moved out of the accounts of the Multichain cryptocurrency exchange. The new transfers come after an initial batch of $126 million was mysteriously moved from the company's accounts over the past weekend. The company has not provided any updates after the initial transfers. Many of its users fear the company was either hacked or its staff is executing a rug pull and running away with their funds. [Additional coverage in Decrypt]
Rodeo Finance cyber-heist: A threat actor has stolen $1.53 million worth of crypto from the Rodeo Finance DeFi platform. The attacker used an oracle manipulation attack. The company is now begging the hacker to return the funds in exchange for a "bug bounty." [Additional coverage in CoinTelegraph]
General tech and privacy
Tax data shared with Meta and Google: An investigation by seven US Senators has found that tax preparation and filing services TaxAct, H&R Block, and TaxSlayer have shared the personal data of taxpayers with Google and Meta. The three services used Google Analytics and Meta Pixel to track taxpayers on their sites, inadvertently sharing sensitive information with the two Silicon Valley companies. The senator group, which also includes the Chair of the Senate Finance Committee, Richard Blumenthal, says this behavior violates taxpayer privacy laws.
Privacy Sandbox requires consent: French privacy watchdog CNIL has ruled that Google's new Privacy Sandbox tracking technology also requires user consent before tracking users, even if Google says the data it collects on users is far smaller and anonymized.
VanMoof going under: Electric bike maker VanMoof has told customers to make copies of their Bluetooth encryption keys as this is the only way customers can connect to their bikes. The company has already shut down some online services as it deals with an impending total shutdown and possible bankruptcy.
Windows 11: More Rust code has made it into the Windows kernel.
Passkeys on GitHub: GitHub now supports passkeys.
"To use passkeys with your GitHub account, navigate to your 'Settings' sidebar, locate the 'Feature Preview' tab, and click 'enable passkeys'. Once you've enabled passkeys, you'll be able to upgrade eligible security keys to passkeys and register new passkeys."
Government, politics, and policy
FCC cyber-funds for schools: The FCC plans to allow K-12 schools and libraries to use funds from the E-Rate program to purchase cybersecurity products. E-Rate funding could previously only be used to purchase internet subscriptions and networking devices. The FCC plans to make available up to $200 million over the next three years via E-Rate so school districts can harden their cyber defenses. [Additional coverage in StateScoop]
FCC announces SIM swap protections: The US Federal Communications Commission has proposed new rules meant to protect consumer accounts from SIM swapping attacks and port-out scams. Under the proposed rules, wireless providers would be required to adopt "secure methods of authenticating a customer" before porting a SIM card to a new device or a phone number to a new network. Providers will also have to immediately notify customers when a SIM swap or port-out takes place.
NCS implementation plan: The Office of the National Cyber Director unveiled the implementation plan [PDF] for the White House's National Cybersecurity Strategy. Presented in March this year, the NCS is a document that lays out the White House's plan to improve the country's cybersecurity posture. [Additional coverage in The Record]
Cyber and the Mexican cartels: The US Senate wants to authorize the Pentagon and federal agencies to deploy cyberspace capabilities in the fight against Mexican drug cartels. The new provision was included in the 2024 National Defense Authorization Act, and any operation would be done in consultation with the Mexican government. The DOD has a long history of combating drug cartels, but CyberCom's role has been mostly limited to military and intelligence operations, with its cyber capabilities rarely being used against criminal groups (usually just ransomware gangs).[Additional coverage in DefenseScoop]
NATO Vilnius Summit: In a statement released following the NATO Vilnius Summit, NATO officials have re-confirmed that cyberattacks can indeed lead to the triggering of Article 5 but triggering the article and a military response will be analyzed on a case-by-case basis. In addition, NATO also announced the launch of its new Virtual Cyber Incident Support Capability (VCISC), a team meant to help member states respond to significant malicious cyber activities. [Additional coverage in The Record]
Sponsor section
Today’s newsletter is brought to you by Kroll Cyber. Click here to register for Kroll’s upcoming Webinar on Frontline IR Intel for Your SOC: Faster, More Accurate Detection and Response.
You can also listen to this week’s sponsor interview. Catalin Cimpanu chatted with Scott Hanson from Kroll about detection as code:
Cybercrime and threat intel
Manipulated Caiman: A phishing group is believed to have compromised the bank accounts of more than 4,000 Mexican individuals and organizations over the past two years. Based on data gleaned from a control panel operated by the group, Perception Point says the group has access to accounts holding more than $55 million worth of funds.
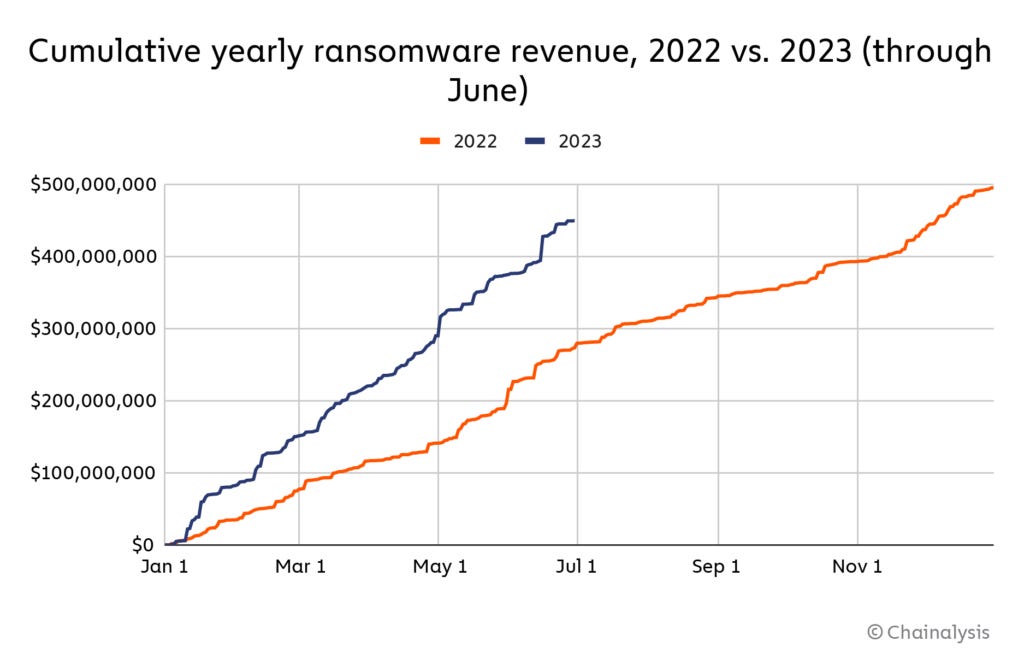
Ransomware returns: Ransomware gangs have extorted at least $450 million from victims in the first half of the year, a figure that shows the slump ransomware gangs experienced after Russia's invasion of Ukraine is now over. Blockchain analytics company Chainalysis expects groups to make $890 million by the end of 2023, which will give ransomware gangs their second most profitable year on record. Their most successful year was 2021—when they extorted around $940 million from victims.
Malware technical reports
USB malware increases: In the first half of the year, the number of USB malware attacks has increased three times. Mandiant says the majority of incidents can be linked to a handful of USB-based operation campaigns, such as the SOGU and SNOWYDRIVE malware strains. Both are strains used in cyber espionage, with the SOGU malware being linked to TEMP.Hex, a China-linked APT that conducts operations in support of Chinese national security and economic interests.
AVrecon botnet: Lumen's Black Lotus security team has discovered a new botnet named AVrecon that has infected more than 70,000 devices with malware. The botnet has been operating since at least May 2021, and most of its infected devices are Linux-based SOHO routers. Researchers believe the botnet's primary purpose is to carry out password-spraying attacks and digital advertising fraud. Lumen says it null-routed the botnet's command-and-control server across its backbone network and recommended that other providers do the same.
TeamTNT: TeamTNT is back, and its latest crypto-mining campaign is targeting Kubernetes, Docker, Weave Scope, Jupyter notebooks, Redis, and Hadoop servers. Details on this campaign are available via AquaSec, Permiso, and SentinelOne.
Xidu: Chinese security firm Huorong has published a report on Xidu, a new Windows backdoor that has been spreading in the wild since April this year.
Lokibot: Fortinet has published a technical analysis of a phishing campaign using the Follina Office vulnerability to distribute the Lokibot infostealer.
CustomerLoader: A new malware loader named CustomerLoader started operations in June 2023 and has been linked to several campaigns distributing infostealers, RATs, and commodity ransomware. Glad to see they're not wasting any time and are already fast friends with the ransomware crowd.
RevolutionRAT: A new infostealer named RevolutionRAT is being advertised on Telegram channels.
"As part of their PR, the operators write blogs as they perform malware analysis on their competitors, such as VenomRAT and Onion Clipper. In their blogs, they show how it is easy to analyze, identify and mitigate their activity. The bottom line is that RevolutionRAT is significantly better and more sophisticated than its competitors."
RustDog: Qihoo 360 has published a report on RustDog, a trojan spread across China using email and IM phishing campaigns.
TeamUnderground ransomware: Chinese security researchers have analyzed a new ransomware strain named TeamUnderground. The ransomware appears to be used in targeted attacks.
BlackLotus source code: The source code for the BlackLotus v2 Windows bootkit has popped up on GitHub.
Sponsor section
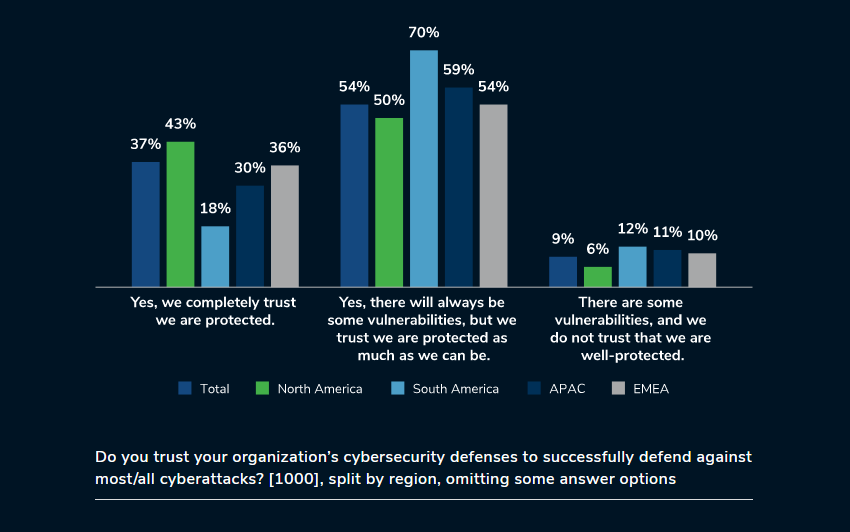
Kroll conducted a survey of 1,000 senior information security decision-makers based in North and South America, APAC, and EMEA. The goal was to understand the current state of cyber defense, the levels of organizational trust, and how true cyber maturity links to trust in facilitating organizations to stay ahead of the curve in a constantly evolving threat landscape.
APTs and cyber-espionage
Storm-0558's Microsoft hack: A Chinese cyber-espionage group has hacked into the Outlook email accounts of approximately 25 organizations, including government agencies across Europe and the US. The hacks were discovered by the US government and confirmed victims include the State and Commerce Departments, according to the Washington Post. Microsoft attributed the attacks to a Chinese espionage group the company tracks as Storm-0558. In a post-mortem, Microsoft says Storm-0558 gained access to a Microsoft account (MSA) consumer signing key that the group used to forge authentication tokens and access victim accounts. According to security researchers, the MSA key is a secret token that only Microsoft has access to, which suggests Storm-0558 might have breached or exploited Microsoft 365 core systems before pivoting to victim accounts. In response to the hacks, CISA has issued an advisory with possible mitigations.
HKLeaks: CitizenLab says the HKLEAKS campaign that doxed members of the Hong Kong pro-democracy movement in 2019 was orchestrated by individuals operating from mainland China. CitizenLab based its conclusion on the extended coverage the leaks received in Chinese state media and some dox packages that appear to have originated from police databases. The report's conclusion contradicts statements made by the HKLEAKS website operators, who claimed they were native Hong Kong residents. The HKLEAKS doxxing sprees stopped in mid-2021 after the COVID-19 pandemic stopped all public protests and after most of the doxxed individuals had been arrested or exiled.
"This, combined with other suspicious signals we have detected, is characteristic of an artificial campaign and not of an organic, community-driven effort, which typically trails off gradually."
APT group exploits ICS equipment: Industrial equipment maker Rockwell Automation has warned customers that a government-backed APT group is exploiting two vulnerabilities in ControlLogix communications modules. The company says the vulnerabilities can be used to run code remotely on unpatched devices and disrupt industrial operations. Rockwell has not disclosed any details about the APT group or its targets. ICS security firm Dragos says one of the vulnerabilities is similar to a zero-day used by the Xenotime group in the 2017 Trisis attacks, but the company has not formally linked the new exploits to any known group. [Additional coverage in SecurityWeek]
CryptoMimic/SnatchCrypto: Japan's CERT team has published a report on the Python and Node.js malware used by the CryptoMimic (SnatchCrypto) North Korean APT group in recent cross-platform operations targeting Windows, macOS, and Linux environments.
ScarCruft: Qihoo 360 has published a report on ScarCruft operations involving the RokRat malware.
GhostWriter: Cisco Talos has more details on some phishing campaigns targeting Ukraine that the country's CERT team linked to the GhostWriter group. Some of these campaigns also targeted Poland.
APT29: Lab52 has a blog post on a suspected APT29 phishing campaign.
APT29's BMW lures: Hackers with Russia's FSB intelligence agency have targeted diplomats working in Ukraine with fake car ads as part of phishing campaigns designed to infect their computers with malware. The phishing campaign used the lure of a BMW car for sale, playing on the need of most foreign missions to provide employees with cars while stationed in Ukraine. Security firm Palo Alto Networks says the campaign targeted 22 of the 80 foreign missions active in Kyiv, Ukraine's capital. The company called the campaign "staggering in scope" because of its broad targeting and scale. Additional details are also available courtesy of Forcepoint.

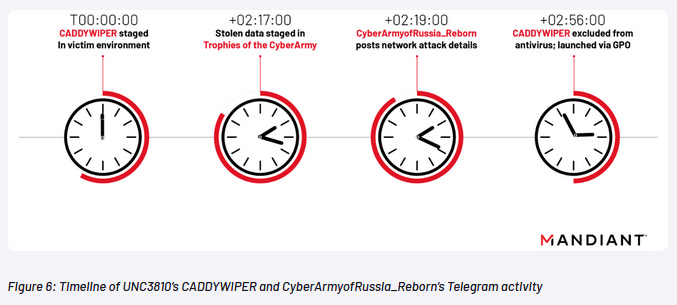
Another fake pro-Kremlin hacktivist group exposed: Mandiant has uncovered new evidence to show coordination between Russia's GRU military hackers and pro-Kremlin hacktivist group Cyber Army of Russia Reborn. Mandiant says it observed the fake hacktivist group boast on Telegram about disrupting the network of a Ukrainian organization 35 minutes before GRU hackers actually disrupted that network by deploying a data wiper. The Cyber Army of Russia Reborn group is one of three fake pro-Kremlin hacktivist groups that appear to have strong ties or are controlled by the GRU military intelligence service. The other two are XakNet and Infoccentr.
Vulnerabilities, security research, and bug bounty
Zimbra zero-day: Team collaboration platform Zimbra is warning customers that threat actors are exploiting a zero-day vulnerability in its platform. The company has released instructions on how customers can mitigate the attacks while they are still working on a patch. The ongoing attacks were discovered by Google's TAG team.
Aerohive RCE: Auro Infosec researchers have discovered a remote code execution vulnerability (CVE-2023-35803) in all Aerohive/Extreme Networks access points running HiveOS/Extreme IQ Engine. The vulnerability targets a service that runs on port 5916 at all times and all the devices' interfaces. A PoC was also released.
SonicWall vulnerabilities: SonicWall has released patches to fix 15 vulnerabilities for the GMS/Analytics software suite. The vulnerabilities were found and privately reported by the NCC Group.
QuickBlox vulnerabilities: Check Point and Claroty researchers have disclosed several vulnerabilities impacting QuickBlox, a chat and video framework used across telemedicine, finance, and smart IoT device applications. The vulnerabilities reside the in the QuickBlox SDK and API and can be used to leak or retrieve user information.
Adobe ColdFusion access control bypass: Rapid7 researchers have published a write-up on CVE-2023-29298, an access control bypass they found in Adobe ColdFusion apps.
Mailgun exposé: An anonymous security researcher claims to have found a weakness in Mailgun's infrastructure.
Apple re-releases security updates: Apple has re-released its recent security updates meant to patch an actively-exploited zero-day. The company was forced to pull the updates after they broke web browsing for some users.
Infosec industry
Blockchain abuse merger: Chainabuse and BTC Abuse, two services for reporting crypto addresses used in online scams, have now merged. The new service now runs on Chainabuse.
New IronNet CEO: IronNet has named a new CEO in Linda Zecher, as part of its plan to restructure its management and delist from the NYSE. [Additional coverage in CybersecurityDive]
Orca sues Wiz: Cloud security firm Orca has sued local rival Wiz alleging patent infringements and intellectual property theft. The lawsuit is quite the read, and Orca claims Wiz even stole some of its marketing strategies, such as copying one of its coffee booths at some security conferences. [Additional coverage in SecurityWeek]
Risky Business Podcasts
In this podcast, Patrick Gray and Tom Uren talk about Citizen Lab's analysis of WeChat's behavior and its privacy policy.




