Risky Biz News: Would a tax relief for SMBs improve cybersecurity postures and ransomware defenses?
In other news: Nomad crypto platform robbed for all it has (had); Robinhood fined $30 million; and Samsung debuts "Repair Mode" security feature.
This newsletter is brought to you by Airlock Digital, Rumble Network Discovery, Proofpoint, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
An Atlantic Council report published on Tuesday makes some clever and unique recommendations for US policymakers on addressing the current surge in ransomware attacks.
Entitled "Behind the Rise of Ransomware," the report was put together by John Sakellariadis following interviews with over 50 policymakers, cybercrime experts, law enforcement officials, and technologists.
The report does not foray into the history and technical evolution of the ransomware ecosystem—reports of which there are plenty of, courtesy of threat intel firms—but focuses on putting forward new ways that US lawmakers could explore to stem the ransomware problem in the long run.
Sakellariadis and the experts interviewed in the report reach the same conclusion that everyone else has reached in previous years—namely, that ransomware can't be culled off from the cybercrime ecosystem in totality, citing the fact that most ransomware operations have roots inside Russia and "Russian noncompliance with transnational cybercrime investigations" may never lead to a law enforcement crackdown on miscreant groups harsh enough to scare major players away from orchestrating future attacks.
Instead, the report concludes that authorities need to crack down on cryptocurrency cash-out schemes and nudge organizations towards improving their cybersecurity defenses.
Here, the report makes three recommendations that are original and haven't been publicly explored in any previous reports we have read so far. The three recommendations are summarized below:
- Congress should pass legislation for mandatory reporting of all ransomware incidents. Reports should be made to CISA and should include any details on ransom payments—if they have taken place. The benefit from this is that US law enforcement would have a much better insight into the ransomware threat landscape compared to the most likely very inaccurate stats that we currently have.
- Since the vast majority of (targeted) ransomware attacks are against small and medium-sized businesses (SMBs), who typically can't afford expensive cybersecurity plans and resources, Congress should establish a tax relief program for SMBs to encourage them to implement security best practices, such as deploying MFA, backup solutions, and IR plans.
- Congress should also pass legislation offering federal tax credits to SMBs, money they could use to hire or retain employees with cybersecurity expertise, similar to past minority hiring programs. Similarly, the tax credits could also be spent on cybersecurity training programs.
The report's recommendations go beyond the usual "deploy MFA" that we've heard from cybersecurity experts over the past few years. If implemented, they would effectively signal an actual shift to codify cybersecurity best practices into law, unlike previous efforts that have typically targeted federal organizations, government agencies, or only a small portion of the US private sector (that usually deals with critical infrastructure).
Breaches and hacks
Wiseasy hack: Malware installed on the computer of an employee of fintech company Wiseasy allowed hackers to steal passwords for two cloud dashboards the company was using to manage more than 140,000 Wiseasy payment terminals around the world. TechCrunch reported that while security firm Bugard reached out to Wiseasy to notify the company about the incident, they were ignored while the fintech company silently added 2FA to the two previously exposed cloud dashboards. It remains unknown if the threat actors accessed any of the payment terminals or made configuration changes.
Semikron ransomware incident: Semikron, a German manufacturer of power semiconductor components, said on Monday that its internal network had been hit by ransomware. According to a sample of the ransomware used in the attack that was later uploaded on VirusTotal, the attack appears to have been carried out by the LV ransomware gang, considered an offshoot of the now-defunct REvil gang.
Spanish government ransomware incident: Spain's Ministry of Science and Innovation disclosed a ransomware attack that hit the Higher Council for Scientific Research (CSIC) over the weekend of July 16 and 17. Officials said that after two weeks and a half, only a quarter of CSIC centers have regained access to their IT network, marking yet another case of a slow recovery from a past ransomware attack.
MBDA incident: Italy-based missile maker MBDA confirmed a security breach this week but denied claims that its networks were compromised by hackers. Instead, the company said information advertised by cybercriminals online came from an external hard drive. [More in The Record]
T-Mobile hacker: A former owner of a T-Mobile retail store in Eagle Rock has been found guilty of stealing access credentials from a T-Mobile employee to access the company's internal computer systems to illicitly "unlock" and "unblock" cellphones. US authorities said the suspect, Argishti Khudaverdyan, 44, of Burbank, advertised his unlocking services through brokers, email campaigns, and websites such as unlocks247.com and is believed to have made more than $25 million from unlocking T-Mobile phones that were later re-sold on the black market.
Robinhood fine: New York's State Department of Financial Services fined Robinhood (RHC) $30 million for failing to implement proper cybersecurity and anti-money-laundering measures—in compliance with state laws.
The Department found, following a supervisory examination and a subsequent enforcement investigation, that RHC's BSA/AML compliance program, including its transaction monitoring system, had significant deficiencies. Among other things, RHC's BSA/AML program was inadequately staffed; failed to timely transition from a manual transaction monitoring system that was inadequate for RHC's size, customer profiles, and transaction volumes; and did not devote sufficient resources to adequately address risks specific to RHC. Similarly, the Department found critical failures in RHC's cybersecurity program. The program did not fully address RHC's operational risks, and specific policies within the program were not in full compliance with several provisions of the Department's Cybersecurity and Virtual Currency Regulations.
Solana wallet hacks: Users of the Solana blockchain ecosystem reported on Tuesday losing funds in internet-connected (hot) wallets. Affected wallets include offerings from services like Phantom, Slope, and Trust Wallet, and losses were estimated at around $5 million, according to reports.
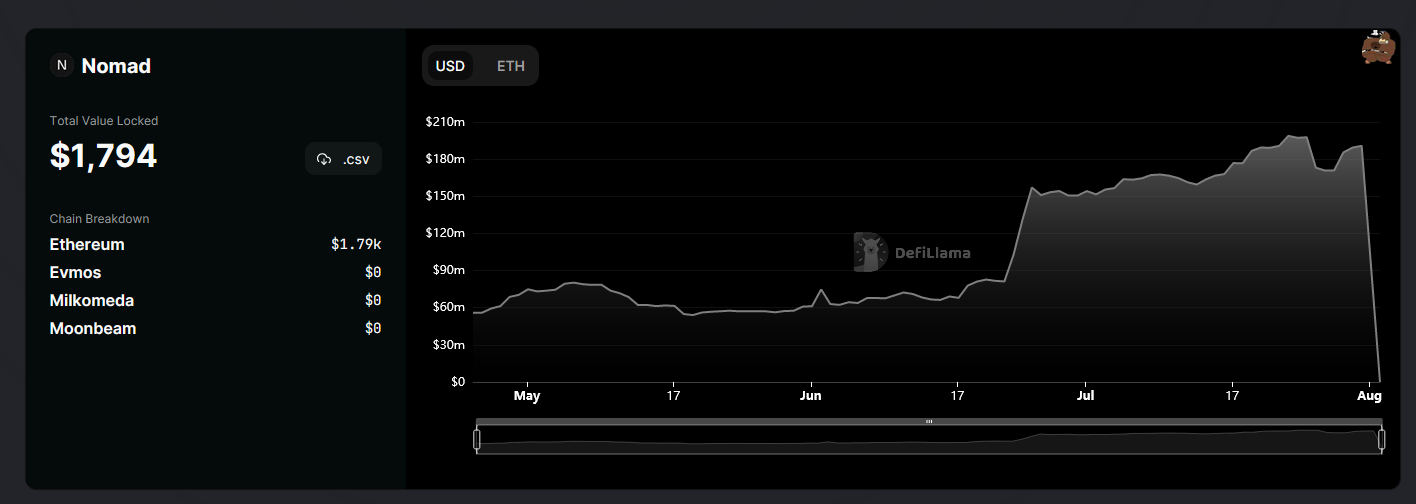
Nomad bridge disaster: The Nomad cryptocurrency bridge platform suffered a security breach on Monday after an attacker exploited a vulnerability in the platform and stole millions of US dollars across various cryptocurrencies. Making matters worse, as news of the hack became public, other threat actors also began exploiting the same bug, leading to currently-estimated losses of more than $190 million. As the Web3 Is Doing Great portal pointed out, "some didn't seem to think through the consequences of using wallets tied to their real-life identities to exploit the vulnerability."
General tech and privacy
Samsung Repair Mode: Samsung said last week that it developed a new security feature for its fleet of Android devices. Named "Repair Mode," the feature can be activated when users send their devices for repairs and works by locking down all personal data on the device to prevent rogue repair technicians from sifting through a user's personal information. Currently, the new Repair Mode is being trialed inside South Korea on Galaxy S21 devices; however, the feature is expected to be made available for more users internationally and to other devices.
Thousands of apps leak Twitter API keys: Cybersecurity firm CloudSEK said it identified 3,207 applications that leak Twitter API keys, exposing their users to situations where attackers can hijack their service and then their users' Twitter accounts.
Government, politics, and policy
DOJ investigating second court system breach: The US Department of Justice said it is investigating a security breach that impacted its court documents management system that appears to have taken place in early 2020. The incident is separate from the SolarWinds-related intrusion the DOJ disclosed last year.
DDoS attacks hit US&Taiwan websites: A wave of DDoS attacks carried out by Chinese hacktivists have hit the websites of US and Taiwanese companies and government portals ahead of Speaker of the House Nancy Pelosi's historic visit to Taiwan on Tuesday. According to ISC SANS, small-to-medium DDoS attacks, along with scans for website vulnerabilities, started last Friday, and most originated from Chinese consumer IP addresses, suggesting that the Chinese government and its Great Cannon have not been deployed (yet).
Cybercrime and threat intel
Apache Spark exploitation: The Shadowserver Foundation said over the weekend that it observed threat actors exploiting a recently-patched vulnerability in Apache Spark data analytics servers. Tracked as CVE-2022-33891, the vulnerability can be used to execute arbitrary code on unpatched servers. Exploiting of the issue appears to have begun less than a week after the patch was released, which most likely also means that most Spark servers have yet to be patched.
DragonForce Malaysia: CloudSEK has published a review of the TTPs employed by hacktivist group DragonForce Malaysia in their attacks against Indian government systems. The group said in June 2022 that it would attack Indian targets in light of recent controversial comments mode on Prophet Muhammad by some Indian politicians. Since then, the group and its supporters have compromised more than 3,000 government and non-government organizations, military websites, and private entities. Compromised entities include BJP (the ruling party of India), Army veteran websites, academic institutes, and more.
Initial access brokers scene: Threat intel outfit Recorded Future has published a report on how the "initial access brokers" scene works and its role in recent ransomware attacks.
Pig Butchering: Gary Warner, a respected security researcher in the ecosystem of online fraud, has called on the infosec community to stop using the term "pig butchering" as a way to refer to victims of online fraud.
Crypto fraud charges: The US SEC charged 11 individuals for their roles in creating and promoting Forsage, a fraudulent crypto pyramid and Ponzi scheme that raised more than $300 million from millions of retail investors worldwide.
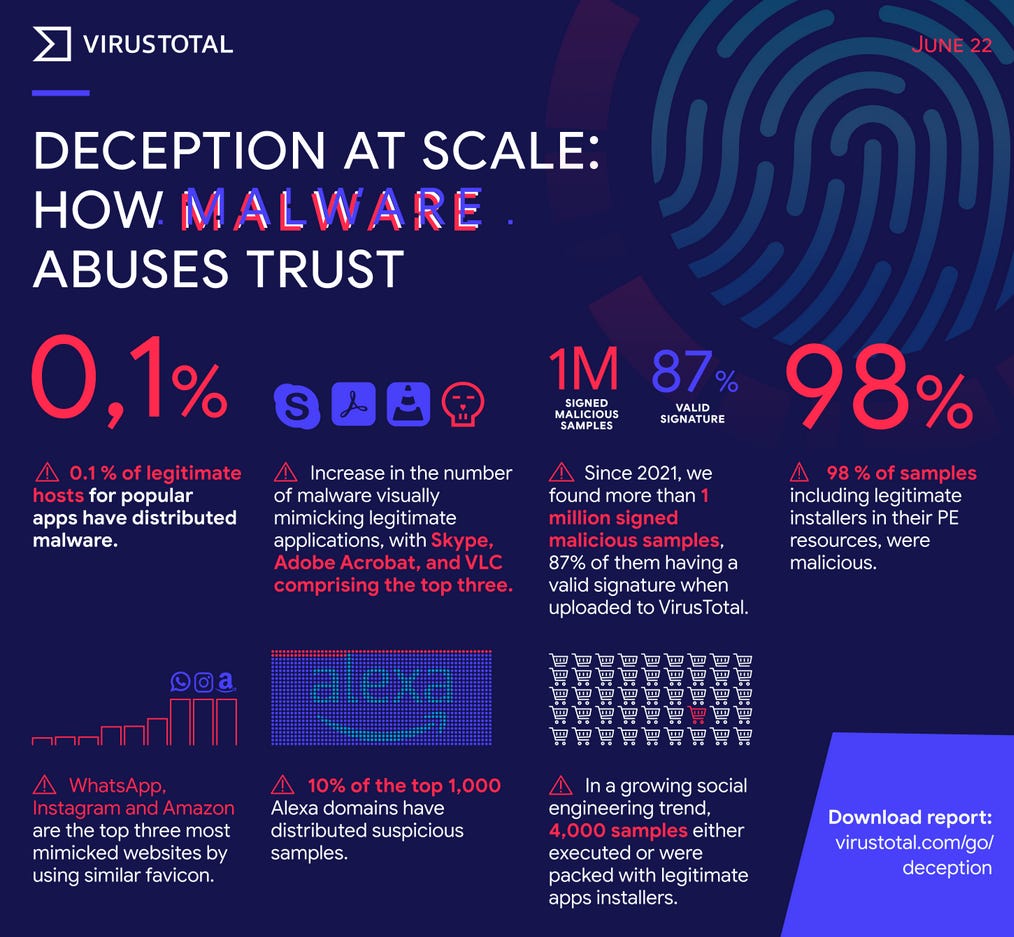
VirusTotal insights report: Google has published a report based on trends its security team has observed in malware samples submitted to its VirusTotal portal. The report's findings are summarized in the image below.
Malware technical reports
RedLine Stealer: Malware reverse-engineer Vlad Pasca has published another one of his infamous breakdown reports—this time on the RedLine Stealer.
Gootkit: Something we missed from last week—Trend Micro's report on recent tactics employed by the Gootkit Loader.
Manjusaka: Cisco Talos said it recently discovered a new attack framework called "Manjusaka" being used in the wild that has the potential to become prevalent across the threat landscape. This framework is advertised as an imitation of the Cobalt Strike framework.
SolidBit ransomware: Trend Micro's team published a report on SolidBit, a new ransomware strain that targets gamers and social media users.
Industrial Spy ransomware: Similarly, Zscaler's threat research team also published an analysis of Industrial Spy, a new ransomware gang that was first spotted in April and which engages in double-extortion ransomware attacks.
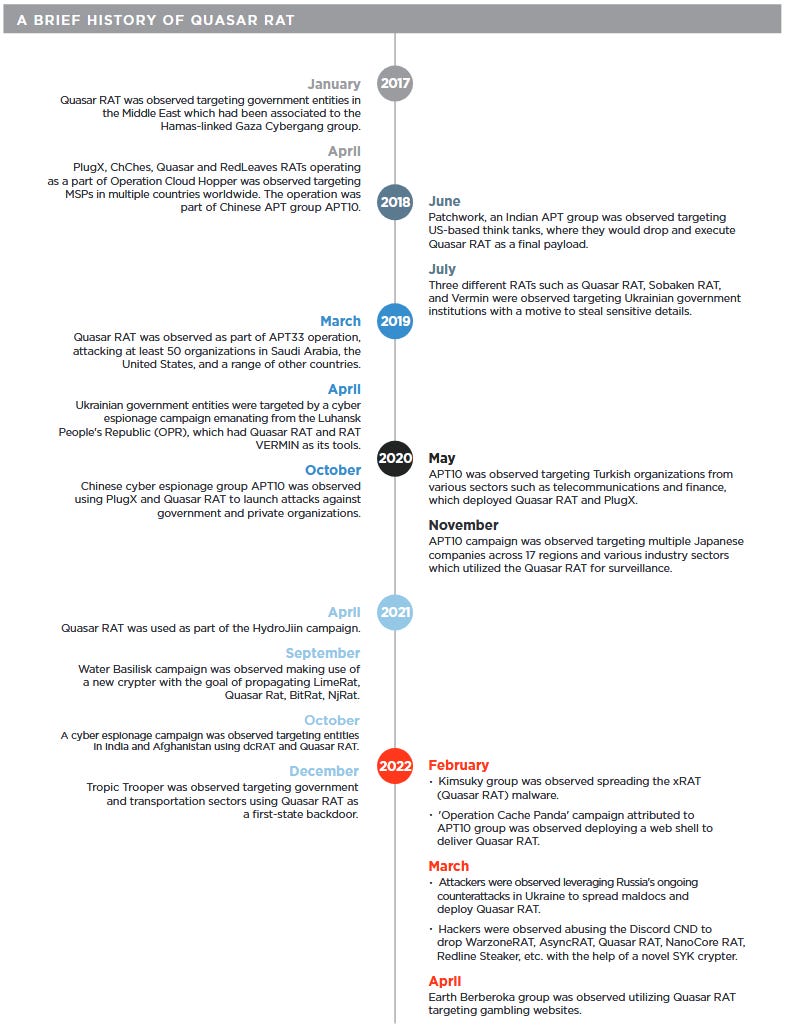
Quasar RAT: The Qualys research team published a report last week on Quasar RAT, aka CinaRAT or Yggdrasil, an open-source remote access trojan that has been widely deployed by multiple threat actor groups targeting both government and private organizations in Southeast Asia.
APTs and cyber-espionage
Gamaredon: Cybersecurity firm NSFOCUS published a report last week on the recent operations of the Gamaredon APT inside Ukraine, including spear-phishing campaigns using malicious documents disguised as police files, the use of decoy SFX self-extracting files to drop remote access trojans, and run-of-the-mill malicious HTML files sent as email attachments.
Vulnerabilities and bug bounty
Dahua ONVIF vulnerability: Security firm Nozomi Networks published a report last week about a vulnerability in Dahua's implementation of the Open Network Video Interface Forum (ONVIF) standard, and which can be exploited to take full control over the company's security cameras. Dahua has released a security update for this issue, tracked as CVE-2022-30563.
Zoho Password Manager RCE: There's now a detailed write-up of a recent RCE vulnerability (CVE-2022-35405) in the Zoho Password Manager, which the company patched last month.
Android monthly security updates: Google has released the monthly security updates for Android and Pixel/Nexus devices.
Jenkins plugin vulnerabilities: The Jenkins project has published a security advisory warning about vulnerabilities in 27 plugins.
VMWare security updates: Enterprise software giant VMWare pushed out security updates on Tuesday to fix ten security vulnerabilities rated critical, including an authentication bypass and several RCEs.
Rsync security update: The Rsync project released a security update to address an arbitrary file write vulnerability (CVE-2022-29154) in the rsync utility that allows malicious remote servers to write arbitrary files inside the directories of connecting peers.
DeathSleep: Cybersecurity researcher Yxel published PoC for a new Windows evasion technique.
This is neat - a detection strategy theory for this technique is to focus on thread pools:
— Ollie Whitehouse (@ollieatnccgroup) 10:43 AM ∙ Aug 1, 2022
- use the TEB to get ThreadPoolData;
- walk it looking for the heuristic as I suspect it will stand out
@modexpblog has been good enough to do the heavy lifting in github.com/odzhan/injecti…
Infosec industry
Q2 2022 infosec research: Cybersecurity firm Thinkst has published an overview [PDF] of the 16 most impactful infosec research projects that were published in the second quarter of 2022.
Mikko book: Cybersecurity pioneer Mikko Hyppönen published his book today, "If It's Smart, It's Vulnerable," a deep dive into the world of IoT security.




