Risky Biz News: Windows to get a new admin protection system
In other news: Snowflake hacker arrested in Canada; mandatory MFA coming to Google Cloud; EU sanctions Myanmar cyber scam compound operators.

This newsletter is brought to you by vulnerability management and analysis platform Nucleus Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Microsoft will add a new security system to Windows 11 that will protect admin accounts when they perform highly privileged and sensitive actions.
Named "Admin Protection," the system is currently being tested in Windows 11 canary builds.
The new feature works by taking all the elevated privileges an admin needs and putting them into a separate super admin account that's—most of the time—disabled and locked away inside the core of the operating system.
When users select the "Run as Administrator" option, they will receive a prompt from the Admin Protection feature.
The difference from a classic UAC prompt that features "Yes" and "No" buttons is that the Admin Protection features will ask the user to authenticate with a password, PIN, or other form of authentication to continue.
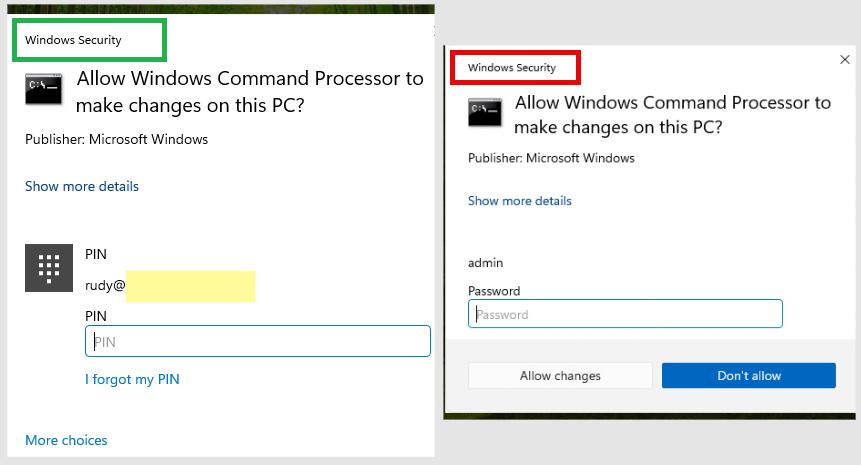
But a change in the prompts is not the only major change. According to technical and non-technical write-ups from Microsoft MVP Rudy Ooms, who first spotted the feature, Admin Protection is a lot more powerful and innovative than you might expect.
It changes how the entire Windows OS assigns admin privileges. In past versions, Windows created two tokens for an admin account, one to use for normal operations and one for when the admin needed to do admin things, with the user switching between the two.
This allowed threat actors to develop UAC bypass techniques and abuse admin accounts for malicious purposes.
The new Admin Protection basically locks away all those highly privileged actions into a separate, system-managed account.
A threat actor wouldn't be able to switch to that super admin account unless they could now bypass the extra authentication options.
How this exactly works or will work is still a mystery. Microsoft is set to provide more details about the new Admin Protection feature at its Ignite developer conference later this month, and we hope these extra authentication prompts will be able to support some sort of MFA. If they do, threat actors that compromise admin accounts will have a much harder time exploiting those accounts for high-privileged actions.
Breaches, hacks, and security incidents
Housing authority breaches: There have been reports of breaches at the Houston and Los Angeles housing authorities.
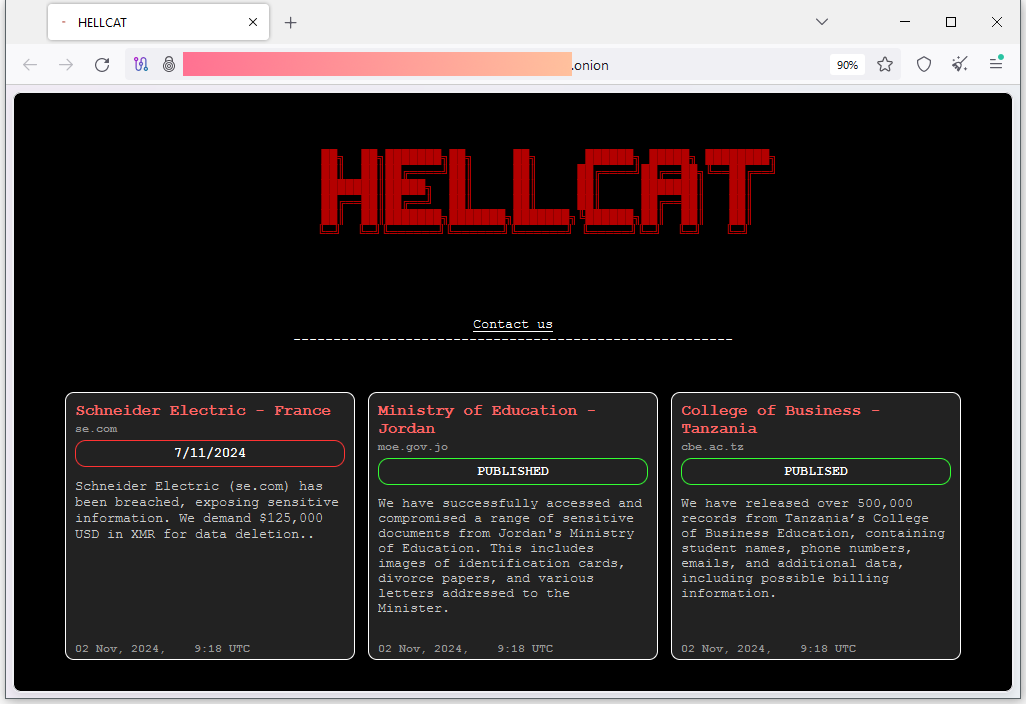
Schneider Electric ransomware attack: Energy and automation equipment maker Schneider Electric has fallen victim to a ransomware attack. A new ransomware group called HellCat took credit for the attack. It threatened to publish the company's data unless it was paid a $125,000 ransom. This is Schneider's second ransomware incident this year after the first one in January and the company's third over the past 18 months. Schneider is also HellCat's third victim listed on its leak site. [Additional coverage in The Record]
General tech and privacy
Google Maps update reveals UA army systems: An October update to Google Earth and Google Maps has exposed Ukrainian military systems and positions. Ukrainian officials discovered the images over the weekend after they were shared across Russian Telegram channels. This is the second time this year that a Google update exposed military positions after a similar incident in February. [Additional coverage in Kyiv Post]
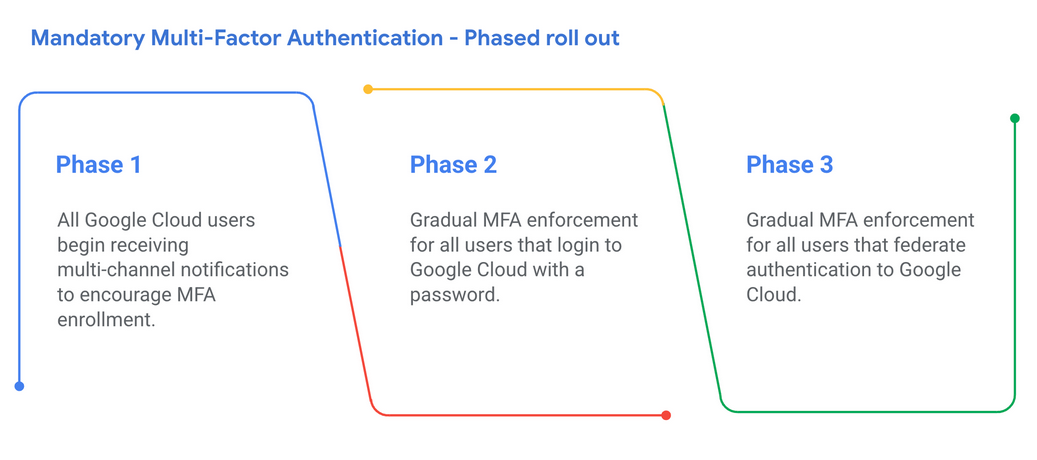
Mandatory MFA on Google Cloud: Google will enforce mandatory multi-factor authentication (MFA) for all Google Cloud accounts starting next year. The company plans to require MFA from all users in a phased rollout over 2025. The MFA enforcement will also apply to federated accounts. Companies will receive a notification in their dashboards before the enforcement kicks in.
Government, politics, and policy
EU sanctions Myanmar scam compound operators: The European Union has sanctioned three individuals and a company for running cyber scam compounds in Myanmar. The three individuals are officers in the Myanmar Armed Forces and the Border Guard Forces. They allegedly control scam compounds in the town of Myawaddy, near the Thai border.
South Korea fines Google: South Korea's privacy watchdog has fined Meta $15.6 million for illegally collecting and then sharing its citizens' private data with online advertisers. [Additional coverage in ABC]
Russia fines Apple, Mozilla, and TikTok: A Moscow court has fined Apple, Mozilla, and TikTok for failing to remove content the Russian government deems "illegal." Apple was fined for not removing two podcasts, Mozilla for failing to remove some add-ons from its store, and TikTok for failing to remove videos related to the war in Ukraine. The fines range from $35,000 to $40,000 in Russian rubles.
Sponsor Section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Adam Dudley, Senior Director for Strategic Initiatives & Alliances at Nucleus Security, on how the company works with partners and customers to constantly improve its service. Adam also touches on how executives are now inquiring about vulnerability management more than low-level practitioners.

Arrests, cybercrime, and threat intel
Snowflake hacker arrested in Canada: Canadian authorities have arrested a suspect for hacking over 165 customers of cloud storage provider Snowflake. Authorities have detained Alexander "Connor" Moucka, who went online under the hacker pseudonym of Judische. He was detained at the request of US authorities, which are now seeking his extradition. Moucka is believed to have bought credentials for Snowflake accounts, accessed and stolen customer data, and then extorted the companies. Companies affected by the Snowflake hacks include AT&T, Ticketmaster, Santander Bank, Lending Tree, and Advanced Auto Parts. [Additional coverage in KrebsOnSecurity]
Interpol seizes malicious infra: Interpol has seized more than 1,000 servers used for illegal cyber activities. The servers were used to host infrastructure for ransomware, infostealers, and phishing operations. The takedowns took place as part of Operation Synergia II, which took place between April and August this year. The operation led to the arrest of 41 individuals, with 65 others also under investigation.
npm campaign: Checkmarx has spotted a malicious npm package that masquerades as a popular testing utility but delivers a cross-platform malware strain that uses Ethereum smart contracts as its C2 mechanism.
Anonymous Sudan's infrastructure: Cloudflare's security team has published an analysis of Anonymous Sudan's server infrastructure and techniques. Cloudflare calls the group LameDuck.
ClickFix: Sekoia has published the second part of a report where it analyzes malware campaigns using the ClickFix social engineering tactic. Part one is here.
Venture Wolf: Russian security firm BI.ZONE has published a report on Venture Wolf, a threat actor targeting Russian businesses with the Meta infostealer.
CRON#TRAP campaign: A novel malware delivery campaign is infecting Windows systems with the help of a Linux virtual machine image. Securonix researchers say the goal is to trick users into running the Linux VM, which contains a built-in backdoor. The benefit of such an approach is that local Windows security tools won't be able to spot the malware running inside the Linux VM container.
VEILDrive campaign: Security firm Hunters has spotted a phishing campaign using various Microsoft services as C2 infrastructure. The company believes the threat actors behind the attacks is based in Russia.
DocuSign spam abuse: Threat actors are abusing the official DocuSign APIs to send fake invoices to targeted organizations. Security firm Wallarm says threat actors are signing up for paid DocuSign accounts and then abusing an API function named "Endpoints: create" to send out massive waves of emails to targets. Some of the victim orgs have reported the phishing incidents to DocuSign via its forums after the company allegedly failed to act on reports sent to its abuse and admin emails.
Malware technical reports
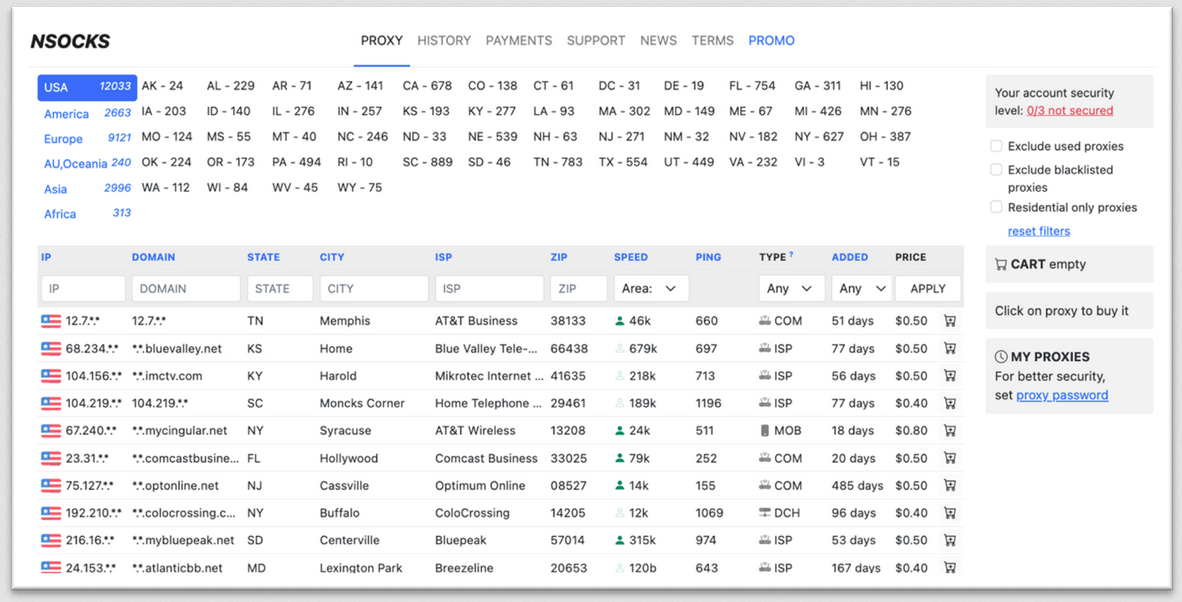
Ngioweb proxy botnet still active: The Ngioweb proxy botnet has grown in size almost ten times over the past four years and is currently boasting more than 30,000 infected daily systems. The botnet is known for selling access to infected systems via a proxy black market named Nsocks. According to AT&T's security team, around three-quarters of the botnet consists of residential users and their devices, such as routers, cameras, and other IoT devices.
G700 RAT: CyFirma researchers have discovered a more advanced version of the Craxs Android RAT named G700.
ToxicPanda: A new Android banking trojan named ToxicPanda has infected more than 1,500 devices across Europe and Latin America. Security firm Cleafy says the new trojan appears to have started operations last month and is the work of a Chinese-speaking group. The malware also appears to be a variation of another banking trojan named TgToxic that is active across Southeast Asia. Cleafy says ToxicPanda contains advanced features to bypass behavioral detection systems used by banks but appears to be in its early stages of development.
GoZone ransomware: SonicWall researchers look at the new GoZone ransomware.
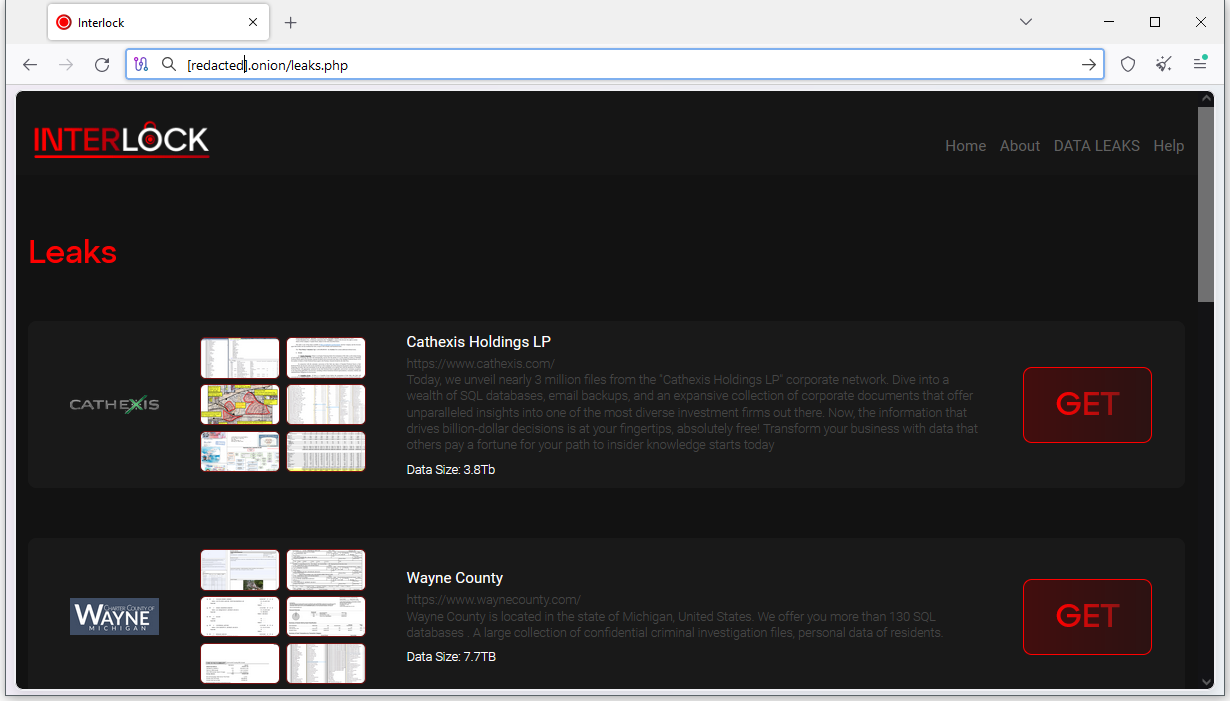
Interlock ransomware: There's a new ransomware gang around—Interlock. This one launched in September, and besides its Windows encrypter, it also developed one for FreeBSD.
Sponsor Section
Nucleus Security's COO Scott Kuffer shows Patrick Gray their vulnerability management platform. It ingests scan outputs from a number of vulnerability identification tools, normalizes that information, and then allows vulnerability management teams to do things like assigning responsibility for certain types of bugs to the correct people.
APTs, cyber-espionage, and info-ops
CISA info-ops warning: CISA, ODNI, and the FBI have warned of last-minute Russian and Iranian election info-ops. Both this newsletter and podcast go out after the election, but we included the link, just in case, since disinfo experts are already seeing new campaigns get underway, although with no formal attribution so far.
Andariel's keylogger: Malware analyst Vlad Pasca has published an analysis of a new keylogger used by North Korean hacking group Andariel. It's the one mentioned in this Symantec report here.
APT37: South Korean security firm Genians has published a report on an APT37 campaign targeting "North Korean human rights groups, defectors, reporters covering North Korea, and experts and professors in the fields of unification, national defense, foreign affairs, and security."
Contagious Interview and WageMole: Zscaler researchers have published a report that looks at Contagious Interview and WageMole, two DPRK APT campaigns. The first targets job seekers with malware during the job interview, while the second one aims to plant North Korean IT workers at Western companies.
Ocean Lotus: QiAnXin researchers analyze how Vietnamese APT group Ocean Lotus is exploiting the MSI TRANSFORMS parameter in MSI executable files for its operations.
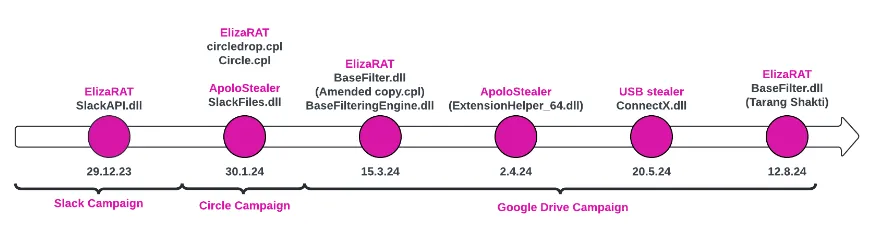
Transparent Tribe's ElizaRAT: Check Point looks at the evolution of ElizaRAT, a remote access trojan employed by Pakistan-based APT group Transparent Tribe.
Vulnerabilities, security research, and bug bounty
Android Security Bulletin: Google has released the Android security updates for November 2024. This month, the company has patched two zero-days. The first ( CVE-2024-43047) is a Qualcomm zero-day from last month that has been included in Android's security updates. The second (CVE-2024-43093) is an EoP with little details.
PfSense PoC: A proof-of-concept exploit has been published for CVE-2024-46538, a stored XSS in PfSense that can lead to RCE attacks.
Google AI finds SQLite vulnerability: Google says that its Big Sleep AI system has found its first valid vulnerability in a real-world project—the SQLite open-source database engine. The vulnerability was described as a stack buffer overflow and was patched on the same day of the report. The issue was found in a development version of the database and was fixed before the vulnerable code was ever shipped to consumers. Google launched its Big Sleep project (formerly Project Naptime) in June this year.
Infosec industry
New tool—LOLAD: A team of security researchers has launched a new project named LOLAD. The project indexes a list of Active Directory techniques, commands, and functions that can be used for red team exercises and by threat actors. The project is similar to other initiatives that track benign tools that can be abused for attacks on Windows (LOLBAS, LOLDrivers, LOFLCAB, and LOLRMM), Linux (GTFOBins), macOS (LOOBins), CI/CD pipelines (LOTP), and ESXi VMs (LOLESXi).
New tool—BucketShield: Security firm Permiso has open-sourced BucketShield, a monitoring and alerting system built for AWS S3 buckets and CloudTrail logs.
New tool—Lightyear: Security firm Ambionics has released Lightyear, a tool to dump files using PHP filters.
New tool—OpenHashAPI: Scorpion Labs has open-sourced OpenHashAPI, a server designed to store and maintain hashes and plaintext in a centralized database.
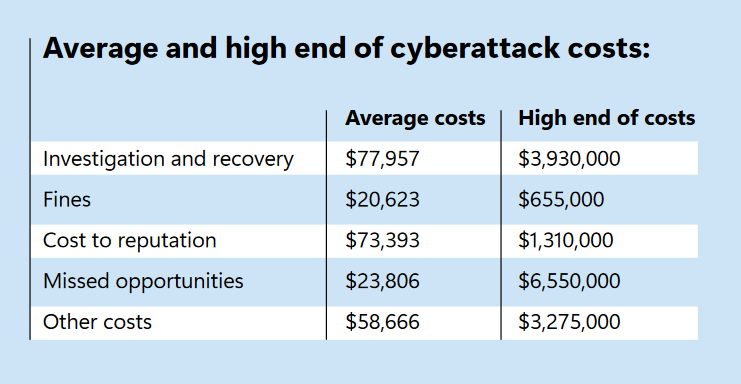
Threat/trend reports: Microsoft and Trend Micro have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss what the Russian state gains and loses from hosting a ransomware ecosystem.
In this podcast, Tom Uren and Patrick Gray talk about the evolving relationship between Russian intelligence services and the country’' cybercriminals. The GRU's sabotage unit, for example, has been recruiting crooks to build a destructive cyber capability. Tom suspects that GRU thugs are not so good at hands-on-keyboard operations but excellent at coercing weedy cybercriminals to hack for the state.
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!





