Risky Biz News: White House working on cybersecurity labels for IoT products
In other news: Germany investigates BSI chief for Kremlin ties; Ukraine Cyber Police chief killed in Russian strike on civilian targets; and Microsoft fixes another NSA-reported crypto flaw.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
The White House said in a press release on Tuesday that it is working on a cybersecurity-themed label that would be applied to smart (IoT) devices and help inform Americans which devices "meet the highest cybersecurity standards to protect against hacking and other cyber vulnerabilities."
The Biden Administration said it plans to meet with vendors, industry groups, and government agencies later this month to discuss how this new labeling scheme should be done.
The announcement this week comes after the White House ordered NIST and the FTC last year to explore two labeling pilot programs on cybersecurity capabilities for IoT devices.
According to Cyberscoop, Deputy National Security Adviser for Cyber and Emerging Tech Anne Neuberger is spearheading the IoT cybersecurity labeling program, which is expected to launch next spring, in 2023.
The White House said the new cybersecurity labels will first be mandated for "the most common, and often most at-risk, technologies — routers and home cameras — to deliver the most impact, most quickly."
Other device types will most likely be included in the program, which is the same approach that the German government took with its own IoT cybersecurity labeling scheme, which it initially launched last year with routers and email services, and then expanded to cameras, speakers, cleaning and gardening robots, smart toys, smart TVs, and then to all smart home consumer products starting this fall.
Currently, Germany and Singapore seem to have the most advanced cybersecurity labeling schemes for smart devices, even if similar labeling schemes also exist in the UK and Finland. Things are certainly moving quicker in the US than in the EU, where talks about an IoT cybersecurity labeling scheme have been taking place since the mid-2010s, but with little results as of yet. Several industry groups have also developed their own cybersecurity labeling schemes, but one sanctioned by either the US or the EU is most likely to get more traction internationally than anything else currently used anywhere else.
Breaches and hacks
Record TV ransomware attack: Brazilian TV station RecordTV was hit by the BlackCat ransomware gang over the weekend. According to local news outlet TecMundo, the attack encrypted the TV station's file storage servers, preventing employees from accessing recorded materials. As a result of the attack, RecordTV changed its regular programming to air sitcoms for half a day until engineers regained control over their network. Some employees were also sent home on Sunday, but programming has since returned to its normal schedule.
DDoS attacks on US airports: Pro-Russian hacktivist group Killnet has carried out a set of coordinated DDoS attacks on the portals of several US airports. Fourteen airport websites were hit, but travel wasn't affected at any location. Targets included airports in Atlanta, Chicago, Indianapolis, Los Angeles, Louisville, Minneapolis, and others.
Massive card leak: The operators of the BidenCash carding forum have leaked more than 7.9 million payment card details in a publicity stunt to draw attention to their service. According to Indian threat intel firm CloudSEK, the majority of cards in the database were issued by Visa in its US region. Details like names, home addresses, emails, telephone numbers, and card numbers and types were included, but no PIN numbers.
Toyota leak: Japanese carmaker Toyota said that the personal details of more than 296,000 users who used the T-Connect mobile app to connect their car to their smartphone might have been stolen. The company admitted that it left one of the access keys for the T-Connect service in one of its GitHub repositories for more than five years, between December 2017 to September 15, 2022; although it's unclear if someone saw it and exploited it to pilfer user data.
IT-Glue credential stuffing incident: Kaseya enforced a mandatory password reset and MFA setup for customers of its IT Glue platform over the weekend. Kaseya denied rumors that appeared on Reddit—that it might have suffered a security breach—and said in a press release on Monday that the password reset was just a precaution after its IT Glue service dealt with a "concerted credentials stuffing campaign."
Mango Markets hack: DeFi platform Mango Markets said it was hacked on Tuesday. While the company didn't disclose the sum, early estimates claim hackers stole ~$112 million worth of cryptocurrency from the platform. Other details are currently unavailable.
Four hacks in one day might be a new record 🤯
— The Defiant (@DefiantNews) 12:01 AM ∙ Oct 12, 2022
More than $115M was stolen from DeFi protocols TODAY.
👇
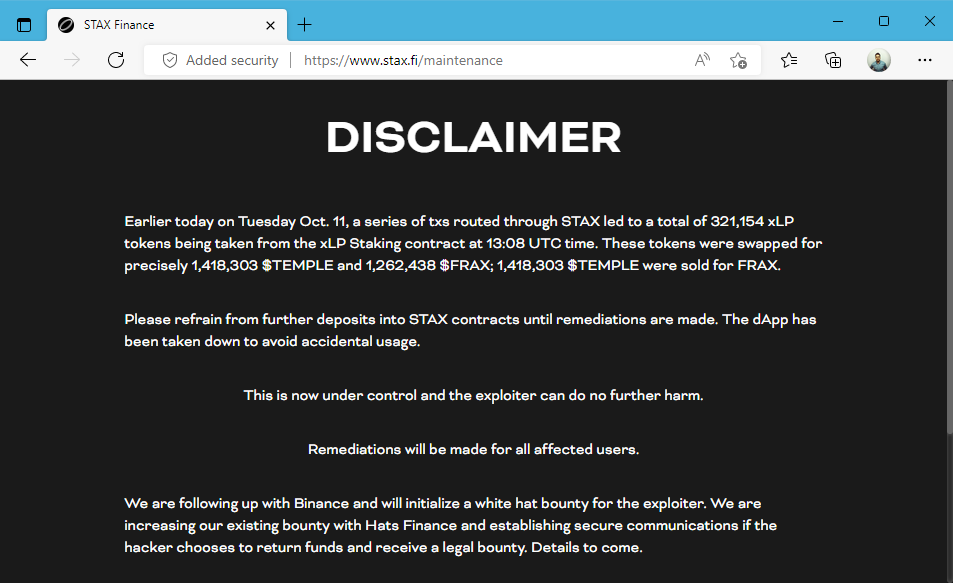
STAX Finance hack: DeFi platform STAX Finance said it lost $2.3 million after an attacker exploited a bug in TempleDAO, the backbone of its service.
General tech and privacy
Forced to delete notebooks and files: Peiter "Mudge" Zatko, Twitter's former head of security, alleged that Twitter management forced him to burn notebooks and delete files in order to get his severance package. According to Bloomberg, citing court documents unsealed this week, this included 10 handwritten notebooks and deleted 100 computer files.
Brute-force protection for local admin accounts now generally available: With yesterday's Patch Tuesday security updates, Microsoft has also enabled a new feature by default for all Windows OS versions that will lock and freeze all local admin accounts for 10 minutes after 10 failed login attempts. The feature is meant to be Microsoft's best protection against brute-force attacks, including those carried out via RDP, that have served as an initial entry for many cybercrime and cyber-espionage operations over the past years. A similar feature to block SMB-based brute-force attacks is also in the works.
New Stealth protocol: The Proton VPN provider said it developed a new protocol called Stealth designed to help its users avoid detection and bypass internet censorship and VPN blocks in oppressive regimes, corporate networks, or annoying ISPs.
Android leaks some VPN traffic: VPN provider Mullvad said it identified a vulnerability in the VPN service of the Android operating system that leaks some of the user's traffic connectivity checks outside of the VPN tunnel in a way that Mullvad and other VPN apps cannot prevent or block, even when the "Block connections without VPN" option is turned on in the Android OS VPN settings. Mullvad said it reported the issue to Google, who said it's intended behavior and does not plan to fix it.
New Pixel security features: With the new Google Pixel 7 smartphone et to be released on October 13, Google engineers have put out an overview of the latest security features that come packaged with their new device. This includes a new Safety Center feature to centralize all privacy and security features in one place, automatically clearing clipboard data after an hour, new hardware, and the ability to clear permissions on unused apps on older Android versions via the Google Play app.
Google just published a blog post highlighting the security of the new Pixel 7 series.
— Mishaal Rahman (@MishaalRahman) 6:18 PM ∙ Oct 11, 2022
- 5 years of security updates (3 years OS)
- Titan M2 HSM
- CC PP0084 with AVA_VAN.5 certified
- pKVM support
- Free Google One VPN
Government, politics, and policy
UA Cyber Police chief killed in Russian bombing: Yuriy Zaskoka, the chief of Ukraine's Cyber Police department, was killed following a Russian missile strike aimed at civilian infrastructure in the Kyiv city center, the agency confirmed on Monday.
US fines Bittrex: The US Treasury's Financial Crimes Enforcement Network (FinCEN) has fined cryptocurrency platform Bittrex $29.2 million for failing to detect and block payments to sanctioned entities and also failing to detect payments related to criminal activity, such as payments to dark web markets and ransomware groups. FinCEN said Bittrex made over 116,000 transactions valued at over $260 million to sanctioned entities and connected to criminal activity over the past few years.
"Bittrex failed to implement effective transaction monitoring on its trading platform, relying on as few as two employees with minimal anti-money laundering training and experience to manually review all of the transactions for suspicious activity, which at times were over 20,000 per day."
Belgium wants better anti-phishing support: Eva De Bleeker, the State Secretary for the Belgian Consumer Protection Agency, has been silently pushing local banks to provide 24/7 customer support for victims of phishing attacks and help them lock accounts before money can be stolen. De Bleeker said that most banks have complied with her request but "it should soon become apparent that some banks remain stubborn."
Germany investigates BSI chief: The German government is investigating Arne Schoenbohm, the head of the Federal Cyber Security Authority (BSI), for undisclosed connections to Russian intelligence agencies, the AFP reported on Tuesday. Schoenbohm's ties to Kremlin were exposed over the weekend following an investigation by German news agency ZDF, which found that the BSI chief founded an industry group called the Cyber Security Council of Germany in 2012. ZDF found that one of the group's members was security firm Protelion, which offered security services to German companies and various political groups. However, ZDF said the company was actually controlled by Russian IT firm Infotecs, founded by a former KGB officer.
Sponsor section
Thinkst is one of this newsletter's four main supporters and this week's featured sponsor. Last week, the company launched a new product called Sensitive Command Canarytoken, a simple canary token that sends an alert every time any command you choose as "sensitive" or "malicious" is executed on your host.
Cybercrime and threat intel
Caffeine PhaaS: Mandiant researchers have published a report documenting the new Caffeine Phishing-as-a-Service (PhaaS) portal, an underground platform that allows unskilled threat actors to carry out highly-advanced phishing operations for the price of a few hundred US dollars per month.
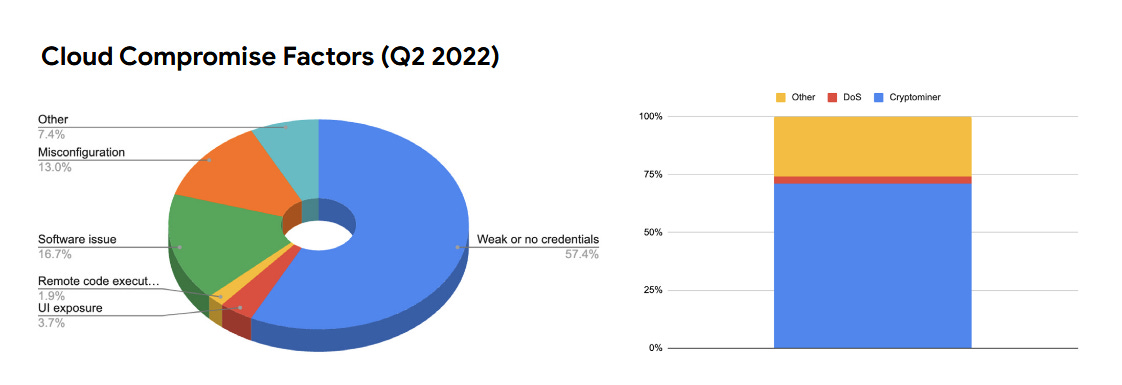
Cryptominers account for 65% of GCP incidents: In its quarterly threat report [PDF], Google Cloud said that 65% of the security incidents that impacted its customers' servers during the second quarter of 2022 were linked to infections with crypto-mining malware. In most cases, the attackers gained access to customer infrastructure by using weak passwords for services like SSH, WordPress, and RDP.
Malware technical reports
Emotet: The VMware Threat Analysis Unit has put out a 68-page report on the activities of the new incarnation of the Emotet botnet, which returned to activity in January this year after being taken down by law enforcement in 2021.
IcedID: And a similar report from Team Cymru on the recent tactics of the IcedID malware botnet.
Gwisin/Ghost ransomware: KISA, the South Korean cybersecurity agency, has put out a technical report on the Gwisin/Ghost ransomware. Other reports on the same ransomware are also available from AhnLab and SK Shielders.
APTs and cyber-espionage
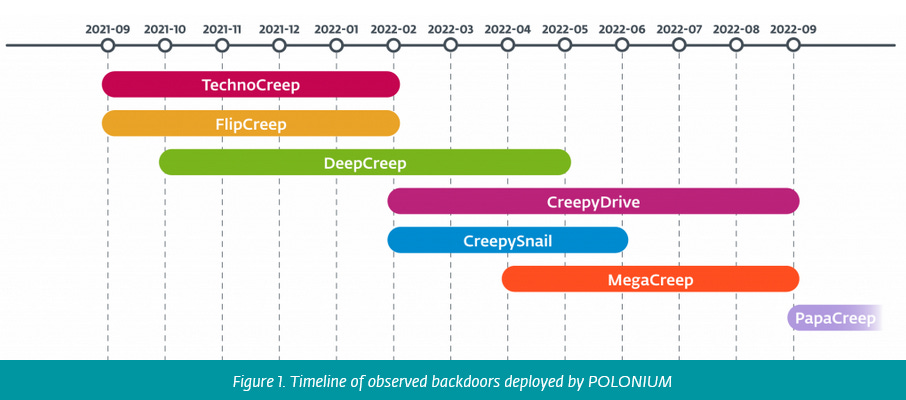
Polonium: ESET researchers published a report this week on a recent campaign of the Polonium APT against Israeli organizations. The Polonium APT is a cyber-espionage group operating from Lebanon and coordinating with Iran's Ministry of Intelligence and Security (MOIS). ESET said they spotted seven backdoors used by the group in their attacks in Israel, including five never-before-seen ones:
- CreepyDrive, which abuses OneDrive and Dropbox cloud services for C&C;
- CreepySnail, which executes commands received from the attackers' own infrastructure;
- DeepCreep and MegaCreep, which make use of Dropbox and Mega file storage services, respectively;
- FlipCreep, TechnoCreep, and PapaCreep, which receive commands from attackers' servers.
Vulnerabilities and bug bounty
Fortinet confirms zero-day: Fortinet said on Monday that the CVE-2022-40684 auth bypass vulnerability it fixed last week was also exploited in attacks in the wild. The company sent a private notification to all customers last week, asking them to install the most recent security patch, but did not say anything about the vulnerability being exploited, which would most likely led to a more rapid patching effort.
A new suspected Exchange zero-day: South Korean security firm AhnLab said it suspects that a webshell it found in a recent LockBit ransomware attack might have been installed using a new undisclosed zero-day vulnerability in the Microsoft Exchange email server. Microsoft, or any other security firm or researcher, has yet to confirm this.
Siemens PLC hardcoded key: Claroty researchers developed a new method to extract master encryption keys embedded within the Siemens SIMATIC S7-1200/1500 PLC and TIA Portal product lines. These keys can be used to bypass security features on these products and compromise devices. [Additional coverage in CSO Online]
Thermal attack recovers passwords: A team of academics from the University of Glasgow has developed a technique called ThermoSecure that uses artificial intelligence to analyze thermal images of keyboards, smartphone screens, or ATM PIN pads, to guess with high accuracy what the user's password might be based on the heat signature of every key. The research is very similar to what University of California, Irvine researchers did with the Thermanator Attack back in 2018.
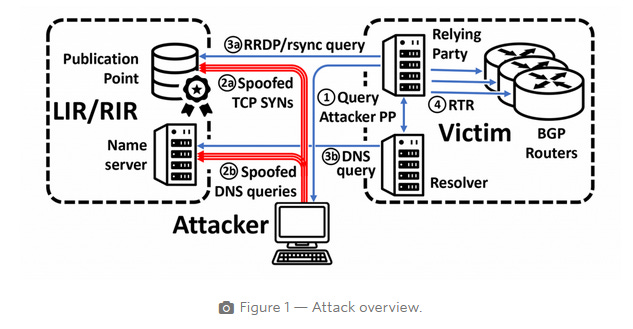
Stalloris RPKI downgrade attack: Something we missed in May was Stalloris, the first-ever downgrade attack on RPKI.
"We demonstrate the first downgrade attacks against RPKI. The key design property in RPKI that allows our attacks is the tradeoff between connectivity and security: when networks cannot retrieve RPKI information from publication points, they make routing decisions in BGP without validating RPKI. We exploit this tradeoff to develop attacks that prevent the retrieval of the RPKI objects from the public repositories, thereby disabling RPKI validation and exposing the RPKI-protected networks to prefix hijack attacks. We demonstrate experimentally that at least 47% of the public repositories are vulnerable against a specific version of our attacks, a rate-limiting off-path downgrade attack. We also show that all the current RPKI relying party implementations are vulnerable to attacks by a malicious publication point. This translates to 20.4% of the IPv4 address space."
Patch Tuesday: Yesterday was October's Patch Tuesday. We had security updates being released by Adobe, Apple, Microsoft, SAP, Google (Android and Chrome), and others. Patches for the two recent Exchange zero-days were not included in yesterday's Patch Tuesday, but there was a fix for another zero-day, CVE-2022-41033, a vulnerability in the Windows COM service.
Another crypto bug reported by the NSA: In addition, Microsoft also rolled out a patch for CVE-2022-34689, a critical-rated vulnerability in the Windows CryptoAPI. Discovered and reported to Microsoft by the US NSA and UK NCSC, this vulnerability can allow attackers to manipulate public X509 certificates "to spoof their identity and perform actions such as authentication or code signing as the targeted certificate," which is the type of vulnerability that you almost certainly don't want in your enterprise environment. This also marks the third or fourth bug (around there, we lost count) reported by the NSA in Windows' cryptographic systems over the past two years.
@RGB_Lights
— Andy Piazza (@klrgrz) 1:41 AM ∙ Oct 3, 2022




