Risky Biz News: White House unveils National Cybersecurity Strategy
In other news: First Windows 11 UEFI bootkit discovered; GitHub makes Secret Scanning available to everyone; CISA's KEV catalog tripled in 2022.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
The Biden administration has published its long-awaited National Cybersecurity Strategy, a document that lays out the White House's plan to improve the country's cybersecurity posture.
The role of the 39-page document [PDF] is to provide a roadmap for lawmakers, federal agencies, and the private sector for dealing with online threats that may impact the national security of the United States.
The document groups strategies into five main "pillars," each with its own recommendations and goals:
- The defense of critical infrastructure (establish new cybersecurity requirements/legislation for critical sectors, harmonize existing regulation, pass enforceable and cheap cybersecurity rules, expanding public-private collaboration to defend infrastructure, further integrations of various federal cyber centers to benefit from shared intel, updating incident response procedures)
- The disruption and dismantling of foreign threat actors (pass new rules and procedures for going after threat actors, encouraging public-private partnerships in going after malicious actors—even for temporary collaboration cells, prevent US cloud infrastructure from being abused by threat actors, increase the speed of threat intel sharing and victim notification, increase actions against cybercrime and especially ransomware)
- Shaping the market to improve and drive/prioritize cybersecurity (hold data stewards accountable, drive the development of secure IoT devices, shift liability to vendors for insecure software, use federal funds to encourage better security practices, use federal procurements to create accountability for cybersecurity, explore a federal cybersecurity insurance system)
- Strategic investments to boost cybersecurity resilience and R&D (secure the technical foundation of the internet and its protocols, invest in federal cybersecurity R&D, prepare for a post-quantum future, make sure the clean energy sector is secure, develop secure digital identity solutions, invest into a cyber workforce)
- Forging international partnerships to pursue shared cybersecurity goals (build international coalitions to counter threats, expand US’ ability to help allies, set global norms for responsible state behavior in cyberspace, secure global supply chains)
The document is a long-term plan, a framework, or a list of goals the US government wants to achieve rather than a set of predefined rules to follow. The White House will need Congress to pass laws to aid in reaching those goals.
A Biden administration official tells Axios they expect lawmakers to pump out laws based on the new strategy for the next ten years.
The document was put together by the White House's Office of the National Cyber Director (ONCD), which is expected to publish an implementation plan for the National Cybersecurity Strategy with finer details in the coming months.
Breaches and hacks
T-Mobile's alleged 100+ breaches: An analysis of multiple Telegram channels reveals that three threat actors have claimed to have breached T-Mobile's backend network more than 100 times throughout 2022. According to infosec reporter Brian Krebs, many of these breaches have been carried out by threat actors who provide account hijacking services and who needed access to T-Mobile's network to execute SIM-swapping attacks. Most of the breaches appear to have been carried out by phishing T-Mobile employees and gaining access to their internal accounts.
Polish tax portal attacks: Polish officials have blamed Russian hackers for DDoS attacks that have taken down the government's national tax-filing portal this week.
General tech and privacy
Russia fines Wikipedia: The Russian government has fined the Wikimedia Foundation, the organization behind the Wikipedia portal, 2 million rubles (~$27,000) for failing to delete "misinformation" about the Russian military and its invasion... oops... special operation in Ukraine. This marks the third fine Wikipedia has received in Russia since the country's invasion of Ukraine, according to Reuters. Wikipedia said the recent fine was related to articles on its Russian language portal related to Russian Invasions of Ukraine (2022), Battle for Kyiv, War Crimes during the Russian Invasion of Ukraine, Shelling of Mariupol Hospital, Bombing of the Mariupol Theater, and the Massacre in Bucha.
Secret Scanning reaches GA: GitHub has made its Secret Scanning security feature generally available to all its users. The feature works by scanning GitHub source code repositories for any strings that look like API access tokens, secrets, or passwords and then notifying the repo owner and the API provider about the accidental leak. Secret Scanning currently supports more than 100 API token formats. The feature has been under limited beta tests for years and is currently enabled on roughly 70,000 GitHub accounts. Starting this week, any GitHub user can enable it through their GitHub profile section.
Government, politics, and policy
Cyber Command intelligence group: US Cyber Command plans to establish its own cyber intelligence center where it plans to aggregate and disseminate information gathered through its collection sensors. The new entity will be named the Cyber Intelligence Center and will include both military and civilian staff. While it will operate under CyberCom, the new center will be a joint effort between Cyber Command, the Defense Intelligence Agency, and the National Security Agency. According to Federal News Network, the new center will focus on the offensive cyber capabilities of foreign adversaries.
GAO report on cybercrime: A GAO report has concluded that it is unclear if US efforts such as threat intel sharing and training programs with foreign partners made a dent in the fight against international cybercrime, such as online identity theft, credit card fraud, and ransomware attacks.
CISA red-team exercise: CISA says it carried out a secret red team exercise against the network of a "large critical infrastructure organisation with a mature cyber posture" and "obtained persistent access to the organisation's network, moved laterally across multiple geographically separated sites, and gained access to systems adjacent to the organisation's sensitive business systems." CISA says it red team triggered "measurable events" that should have gotten it caught on at least 13 occasions, events the organization failed to detect and act upon. Officials didn't name the organization but said that while they breached its network, they also found the organization had good cybersecurity policies in other parts of its network, such as up-to-date and hardened perimeter infrastructure and good password policies. (via this week's Seriously Risky Business newsletter)
Russia bans foreign messengers: The Russian government has banned the use of foreign messaging applications inside Russian financial institutions and state-owned companies. The law has entered into effect this month and bans the use of apps such as Discord, Microsoft Teams, Skype for Business, Snapchat, Telegram, Threema, Viber, WhatsApp, and WeChat.
EU digital driving license: The EU has announced new revamped rules for driving licenses and cross-border enforcement, including the creation of a "digital driving license" that will be valid all across the EU. The new digital driving license is meant to be accessible via smartphones and other devices and will allow drivers to authenticate to authorities when their physical license cards aren't at hand. The digital driver licenses will be issued side-by-side with physical licenses automatically, according to an EU Q&A page.

Risky Business Demo
In a Risky Business demo, Tines CEO and co-founder Eoin Hinchy demonstrates the Tines no-code automation platform to host Patrick Gray.
Cybercrime and threat intel
Australian woman charged for spamming politician: The Australian Federal Police charged a suspect for spamming the email inbox of an unnamed federal Member of Parliament. The AFP says the suspect, a 34-year-old woman from the city of Werrington, New South Wales, sent more than 32,000 emails over a 24-hour period to the MP's email server in an effort to harass and disrupt their government work.
Trezor phishing warnings: Cryptocurrency wallet provider Trezor has warned users about an ongoing phishing campaign targeting its users via email, SMS, and phone calls.
Law firms targeted: eSentire researchers say they spotted a spear-phishing and watering hole attack targeting law firms with the SocGolish and GootLoader malware strains.
GuLoader phishing: Similarly, Red Canary says it's seeing a wave of tax-themed phishing emails distributing the GuLoader malware.
LockBit malspam: Something rare these days—a malspam campaign that leads to LockBit infections.
MyDoom phishing: Something you won't believe—a phishing campaign dropping MyDoom, a malware from 2004.
PY#RATION update: Securonix has an update on the PY#RATION Python-based RAT they first spotted last year—now at v1.6.0.
BidenCash dump: To mark the one-year anniversary of their service, the operators of the BidenCash carding forum have dumped the personal and financial details of more than 2.1 million cardholders. According to Flashpoint, almost half of the cards belong to US nationals.
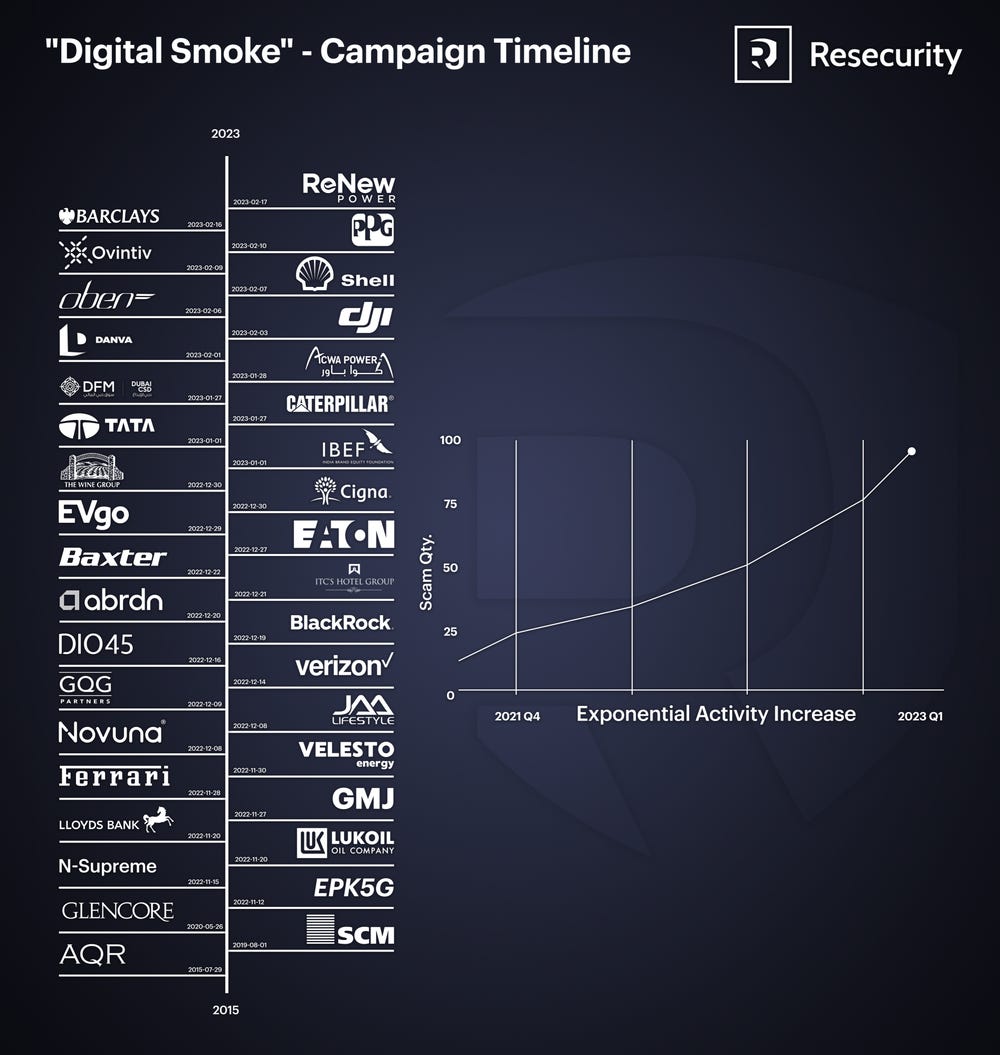
Digital Smoke campaign: Security firm Resecurity is tracking a cybercrime gang it calls Digital Smoke that has made millions from investment fraud scams. Resecurity says the group operates thousands of malicious domains that were registered with names similar to more than 100 companies from across the globe. The group uses black hat SEO and traffic hijacked from legitimate sites to lure visitors to these domains and trick them into making investments either via cryptocurrency or real fiat money transfers. According to Resecurity, the group has been active since the fourth quarter of 2021, and their activity spiked around December 2022.
KEV update: CISA has updated its KEV database with one new vulnerability that is currently being actively exploited. The vulnerability is tracked as CVE-2022-36537, a bug in the ZK Framework. The vulnerability has been under attack since last year as part of a campaign [cached] that targeted R1Soft backup servers.
Recorded Future annual report: Recorded Future has published its yearly annual report detailing the major threats and trends of last year. The report is a good retrospective of what happened in cyber last year, covering everything from ransomware to APTs, and from IABs to hacktivist activity.
Google TAG Q1 2023 takedowns: Google's Threat Analysis Group has published its report for takedowns for coordinated inauthentic behavior across Google websites for the month of January. The vast majority of takedowns targeted Russian influence operations that misconstrued the country's invasion of Ukraine, attacked Ukrainian refugees living abroad, criticized foreign governments for helping Ukraine, and praised Wagner paramilitary troops and the Putin regime. Google also took down thousands of Chinese language YouTube channels pushing scams, but also a small operation criticizing the US for its China-related policies. In addition, Google also cracked down on a rare Azerbaijani operation attacking Armenia, which is not surprising in light of the recent military conflict between the two countries.
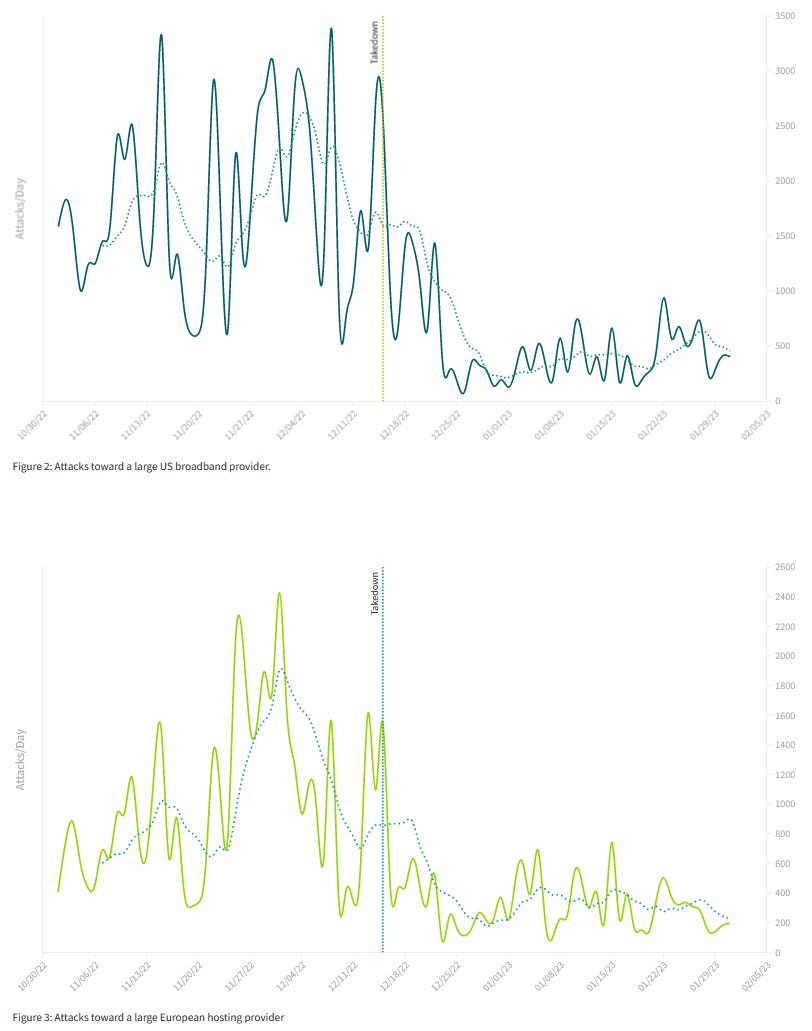
Takedown had effects: Network security provider Netscout says the takedown of more than 50 DDoS-for-hire services in December of last year by Europol and the FBI has led to a measurable decline in DDoS attacks. Declines in attacks have been recorded at broadband providers across both the US and EU, the company says. Not only that, but Netscout says DDoS traffic has remained at lower levels even three months after the takedown, suggesting no major players have appeared on the underground DDoS market to fill the demand after last year's takedowns.
Sponsor Section
Proofpoint is one of this newsletter's main sponsors. Below is a product demo Patrick Gray, the host of the main Risky Business podcast, recorded with them last year, where they show off Nexus People Risk Explorer, the company's product for mitigating insider threats:
Malware technical reports
QakBot: Netresec researchers have a video breakdown of the QakBot C2 network traffic.
Colour-Blind RAT: Kroll's security team has an analysis of Colour-Blind, a remote access trojan hidden inside a malicious Python library named "colourfool."
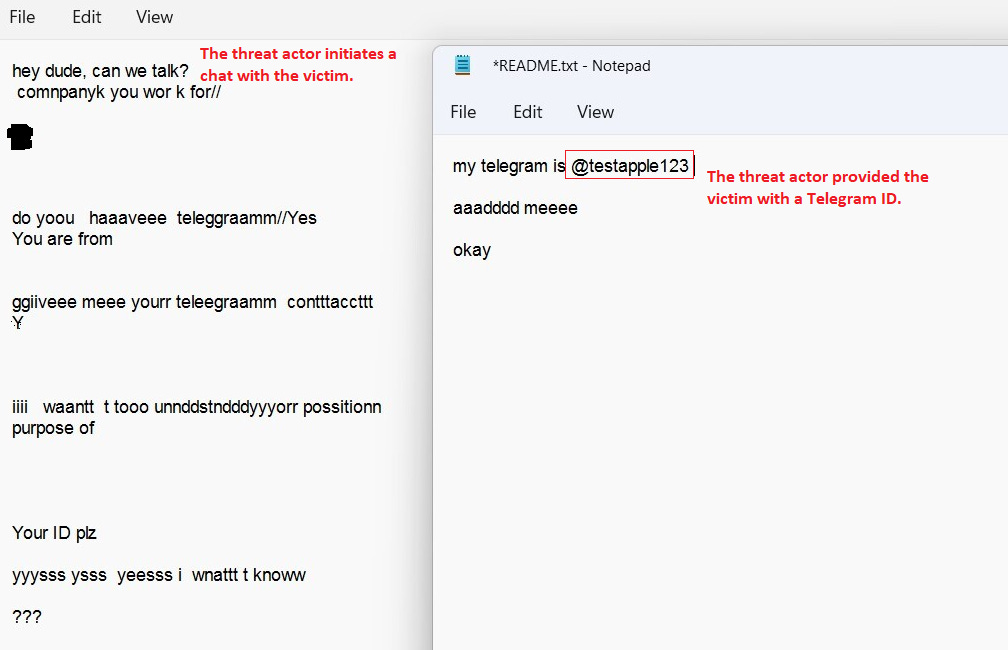
Parallax RAT: Uptycs researchers say they have spotted a phishing campaign aimed at cryptocurrency companies that tries to infect their employees with a version of the Parallax RAT. The weird/novel part of this attack is that once it infects a target, the malware leaves messages to the victim via Notepad files on their computer, urging the victim to connect to a Telegram channel for further communications.
Royal ransomware: CISA and FBI officials have published a joint malware analysis report (MAR) on the Royal ransomware operation, a gang that has a history of targeting US healthcare organizations. The gang is also known for making giant ransom demands from victims, often ranging from $1 million to $11 million in Bitcoin.
Redis miner: Cado Security has discovered a cryptomining campaign targeting Redis database servers.
PIPEDANCE: Elastic's cybersecurity team has discovered PIPEDANCE, a new backdoor strain targeting Windows systems. Elastic says it discovered PIPEDANCE as part of an attack chain targeting a Vietnamese organization in December of 2022. The malware was used to move laterally across a network by abusing the Windows named pipe communication mechanism and then drop second-stage payloads, such as Cobalt Strike beacons.
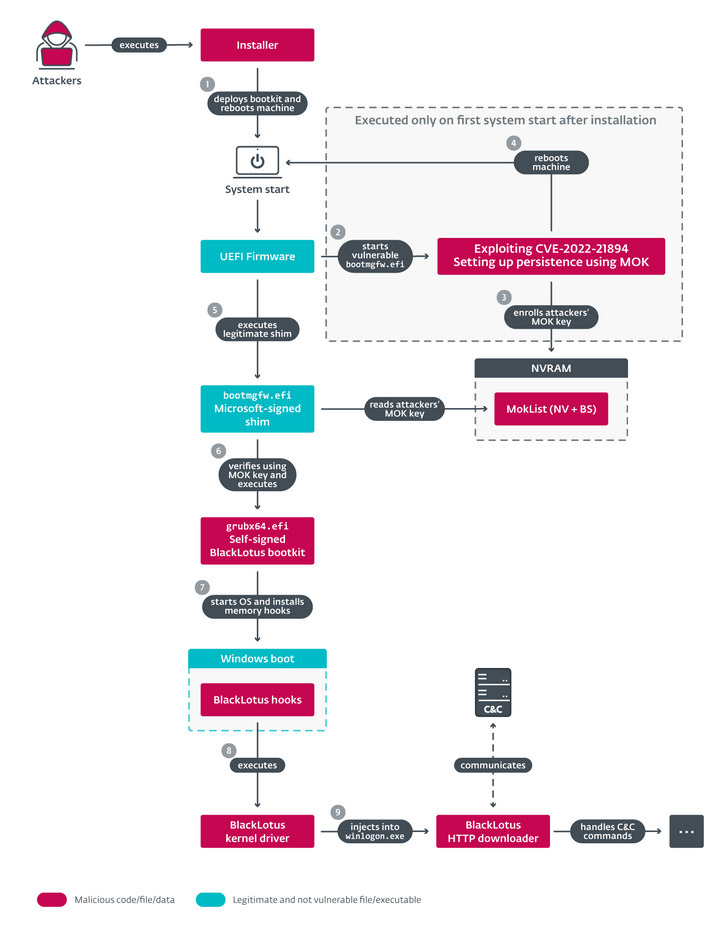
BlackLotus now supports Windows 11: ESET researchers say they have discovered the first-ever bootkit that can infect a fully up-to-date Windows 11 operating system, even if the UEFI Secure Boot protection is enabled. The bootkit is named BlackLotus and was spotted for the first time in October 2022, being advertised on an underground cybercrime forum. ESET says that recent BlackLotus attacks are installing a vulnerable driver, which then BlackLotus exploits to take advantage of a Secure Boot bypass vulnerability (CVE-2022-21894) and install itself in the Windows 11 boot. ESET says although Microsoft patched the Secure Boot bypass vulnerability in January of last year, BlackLotus operators have identified valid binaries that have yet to be added to the UEFI revocation list, which they are now bringing on targeted systems to exploit in what security researchers call a BYOVD (Bring Your Own Vulnerable Driver) attack. BlackLotus won't install on systems from CIS states.
APTs and cyber-espionage
Belgium govt member targeted by China: Belgium's Ecologist Party says one of its members was targeted by Chinese cyberspies. Party officials say that Samuel Cogolati, a member of the Belgium Parliament, was the target of a spear-phishing attack carried out by Chinese hackers disguised as journalists. EColo says Cogolati was targeted because he was one of the Belgian officials who publicly called for an investigation into China's Xinjiang labor camps, its treatment of the Uyghur minority, and the country's respect for basic human rights.
Chinese activists targeted too: The same tactic of posing as journalists to approach targets was also used in a separate operation. Reuters says that Chinese cyberspies spoofed the identity of two of its reporters from Shanghai and Hong Kong to reach out to anti-government activists in China and abroad. The operation began in November of last year and targeted activists via Telegram and Instagram.
Iron Tiger APT: Trend Micro reports they have seen the Iron Tiger APT group launch new attacks throughout 2022, including with a new version of the SysUpdate malware that can now infect Linux systems.
Mustang Panda: ESET has published a technical analysis of MQsTTang, a new backdoor used by the Mustang Panda APT. The malware was used in attacks in January 2023 targeting governmental institutions in Taiwan. ESET says the malware appears to be a new strain written from scratch, as they have not spotted any similarities with the group's past tools. The malware has been named MQsTTang because it uses the MQTT protocol to communicate with its C&C server.
Solar Sunrise retrospective: The GWU National Security Archive has published a retrospective on the Solar Sunrise attacks, one of the oldest known cyber-espionage campaigns (together with Moonlight Maze, 1996) targeting the US government. The attacks took place in February 1998 and targeted DOD networks using a Solar OS vulnerability.
Vulnerabilities and bug bounty
TCG TPM vulnerabilities: Quarkslab researchers have discovered two buffer overflow vulnerabilities in libraries implementing the TPM 2.0 security specification. An attacker with access to the TPM command-line interface can abuse the vulnerabilities to corrupt the TPM's memory and access sensitive information handled by the TPM, such as encryption keys. TPM implementations from IBM, TCG, RedHat, SUSE Linux, and others are affected. Patches were released at the end of last month.
CVE-2023-095 (Gitpod): Snyk has a write-up on a vulnerability in the Gitpod SaaS that allows RCE attacks.
All In One SEO vulnerabilities: More than three million WordPress sites running the All In One SEO plugin will need to be updated to fix a set of vulnerabilities that could be used to hijack sites.
CISA KEV catalog tripled in 2022: The CISA KEV catalog, a database of actively exploited security flaws, has almost tripled in size in 2022, growing from 311 entries to 868 by the end of the year. While this suggests new bugs are being exploited, the reality is quite the opposite. According to researchers at VulnCheck, the vast majority of new CISA KEV entries are for older vulnerabilities that companies failed to address for years and came under attack last year, with the oldest being a bug patched two decades ago, in 2002.
Infosec industry
NATO hiring cybersecurity staff: NATO is hiring cyber threat analysts for its Brussels branch. Pay is €6,211.72/month, per the ad.
Acquisition news: Trend Micro has announced plans to acquire Anlyz, an Indian company, a provider of security operations center (SOC) technology active in the MSSP market. Also, Cisco plans to acquire Valtix, a security firm specializing in securing cloud infrastructure.
New tool-Aladdin: Cybersecurity firm Nettitude has open-sourced a new tool called Aladdin. The tool is meant for red-teamers and can generate payloads to bypass misconfigured Windows Defender Application Control (WDAC) and AppLocker setups.
New tool—Decider: CISA has open-sourced a new tool named Decider that assists network defenders, analysts, and researchers in the process of mapping adversary behaviors to the MITRE ATT&CK framework.




