Risky Biz News: White House recommends prioritizing RPKI ROAs
In other news: Spamouflage returns for the US elections; TfL tells staff to work from home after cyberattack; Russia wants to block foreign web crawlers.

This newsletter is brought to you by GreyNoise. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

The White House has published a roadmap this week with its top recommendations for improving the security of internet routing protocols.
The document [PDF] specifically looks at ways of improving the security of the Border Gateway Protocol (BGP), the technology responsible for directing internet traffic between different networks across all the globe.
The White House started looking into BGP security in 2022 as part of a concerted US government effort to secure internet routing and prevent foreign actors from hijacking traffic from American networks using attacks known as BGP hijacks.
These efforts included the Department of Justice (DOJ), the Department of Defense (DOD), the Federal Communications Commission (FCC), the Cybersecurity and Infrastructure Agency (CISA), and the White House Office of the National Cyber Director (ONCD).
The White House's ONCD recommendations aren't really that groundbreaking. They follow industry best practices, such as asking companies that operate an IP address space to support Resource Public Key Infrastructure (RPKI), Route Origin Authorization (ROA), and Route Origin Validation (ROV).
These are secure technologies that use cryptography to allow organizations (known as Autonomous Systems, or ASNs) to certify they own a specific IP block (via ROA) and that they are an entity allowed to announce it and receive traffic for it (ROV).
The ONCD also recommended the adoption of BGPSec, a security-enhanced extension of the BGP protocol, although not as a priority.
Instead, the White House chose baby steps and recommended that American ASNs prioritize ROAs—as a first step toward securing their BGP space.
The White House will also work with CISA to create an Internet Routing Security Working Group together with members of the private sector. The group will develop a framework and materials to help organizations implement ROAs and ROVs.
Per NIST data shows that almost half of today's internet BGP routes have a valid ROV, and according to Kentik, over 70% of IPv4 BGP routes have an ROA. According to Cloudflare, the problem for the White House is that most of this valid traffic comes from non-US ASNs, and US organizations are lagging behind.
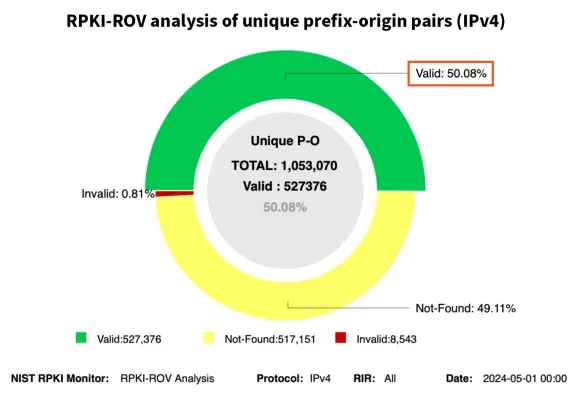
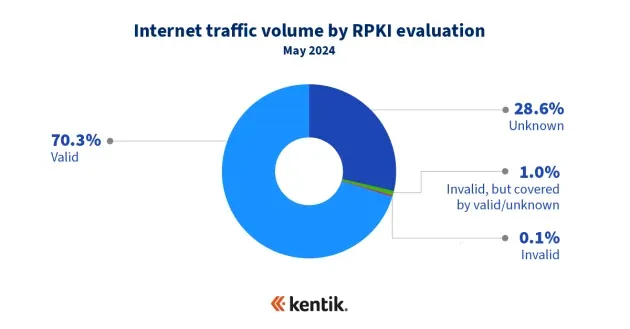
Either way, US officials seem poised to finally address this issue, especially after a slew of incidents of Russian and Chinese state-owned telcos hijacking US network traffic.
In 2022, the DOD and DOJ called internet routing a national security interest and backed the FCC's effort to start working on BGP rules for American telcos.
Earlier this year, White House National Cyber Director Harry Coker pledged to secure half of the US government's IP address space against BGP hijacks by adopting RPKI and its ROA and ROV technologies.
Breaches, hacks, and security incidents
Northern Irish Police leak: The Police Ombudsman for Northern Ireland (PONI) has apologized for leaking the personal information of 160 current and former staff members. [Additional coverage in the Irish News]
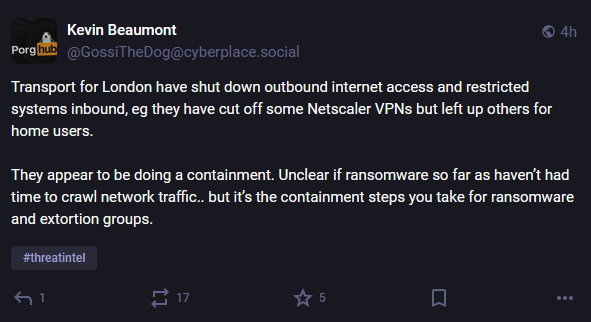
TfL cyberattack: London's public transportation agency has been the victim of a cyberattack on Monday that is impacting some of its networks. Sources have told the BBC that the incident impacted TfL's backend systems and the IT network of its corporate headquarters. Employees were told to work from home, and users reported problems using the agency's contactless payment system. London public transportation has not been impacted.
General tech and privacy
Uber illegally shared data: Dutch media reports that Uber has illegally shared driver data with law enforcement all over the world, suggesting the recent GDPR fine is not an isolated incident.
Clearview AI fined in the Netherlands: The Dutch data protection agency has fined Clearview AI €30.5 million for building an illegal database containing photos with the faces of Dutch citizens. This marks the fifth European country to fine the American company after Italy (€20 million), Greece (€20 million), France (€5.2 million), and the UK (£7.5 million). The Dutch DPA also ordered Clearview to delete its database of Dutch biometrics data and forbade local companies from using its services. Austrian officials also ordered Clearview to delete Austrian data, although they did not fine the company.
OpenSea SEC investigation: The US SEC has sent a Wells Notice to NFT trading platform OpenSea, notifying the company it plans to investigate its activities.
Mastercard wants to get rid of card numbers: Payments processor Mastercard is working on a project to eliminate the use of payment card numbers when making online purchases. The company will expand its token technology with a new pilot program in India. Both Mastercard and Visa have been working on token technology as a replacement for payment card numbers for a decade since the Best Buy and Target hacks. Mastercard and the banks will issue the tokens based on customer biometrics data together with a one-time passcode to be used when making a payment. Mastercard expects all e-commerce transactions to be tokenized in Europe by the end of the decade. [Additional coverage in Bloomberg]
Elasticsearch licensing: Elastic has re-open-sourced Elasticsearch and Kibana, this time under AGPL.
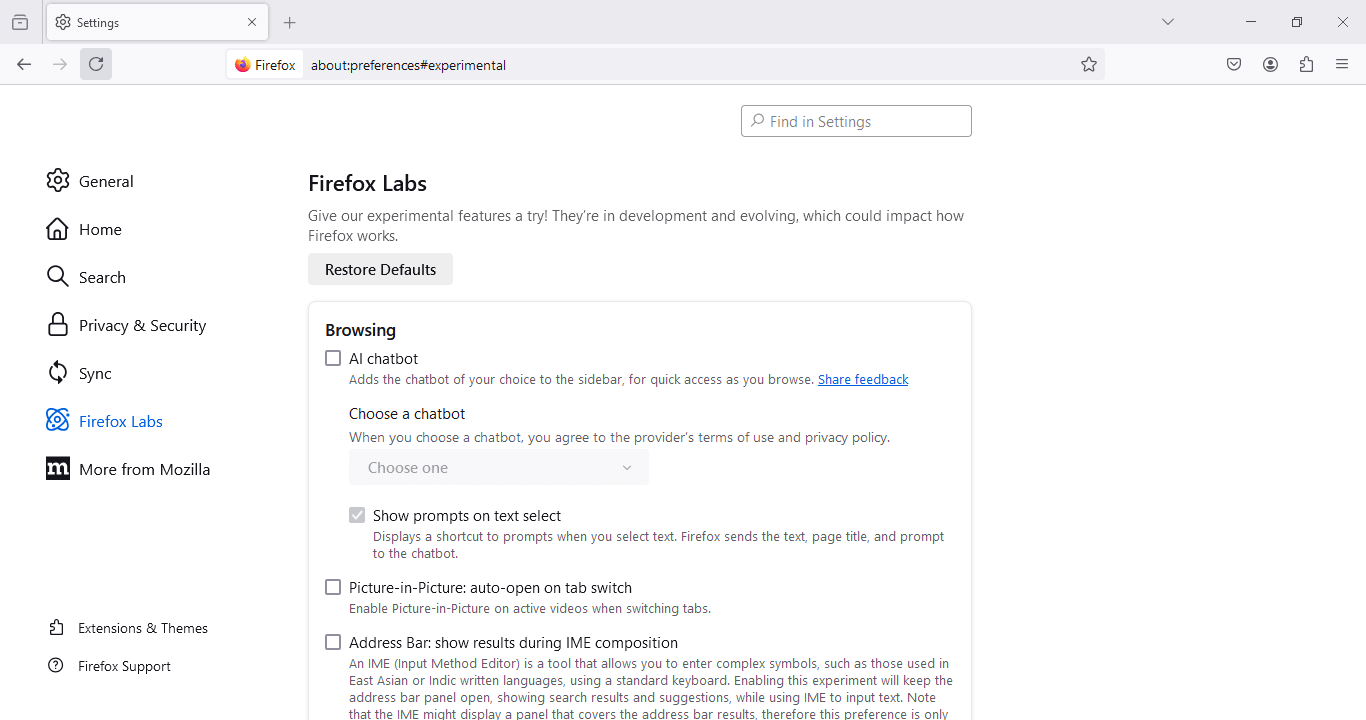
Firefox 130: Mozilla has released Firefox 130. New features and security fixes are included. The biggest feature change in this release include improvements to the text translation feature, a new Picture-in-Picture auto-open feature, and an AI chatbot browsing assistant.
Government, politics, and policy
Army to adopt SBOMs: The US Army will have new rules in place by next February to require SBOM files for all new software acquisitions. The new requirement will apply to contractors and subcontractors but not the Army's cloud services. The Army is the latest US government agency to start adopting SBOMs after several software supply chain incidents and a major push from CISA last year.[Additional coverage in Federal News Network]
China's new internet crackdown: The Chinese government is going after the authors and followers of liberal blogs and online communities. This marks the first time Chinese police have gone after the followers of Chinese liberal accounts. The crackdown appears to have started at the start of the year. Several popular bloggers have confirmed that multiple of their followers in China were questioned by police. [Additional coverage in The Guardian]
Russia wants to block foreign crawlers: A Russian military agency has sent a letter to the Russian government asking officials to ban access of foreign crawlers and automated bots to Russia's internet space. The letter mentions crawlers like OpenAI's GPTBot and search engine bots that crawl robots.txt files. The agency claims crawlers can be used to collect data on Russian state bodies, such as personal data and even vulnerabilities, and use it to train machine learning models. The letter was authored by FSTEC, a military agency under Russia's Ministry of Defence responsible for the export control of dual-use technologies and the military's IT security. [Additional coverage in Kommersant]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Andrew Morris, founder of security firm GreyNoise. Andrew introduces Plasma, a new GreyNoise product that can allow customers to deploy custom GreyNoise sensors anywhere they want—on perimeters, on internal networks, on DMZs, or anywhere else.

Cybercrime and threat intel
Rabobank ordered to share scammer data: A court in the Netherlands has ordered Rabobank to share a scammer's account data with one of their victims. [Additional coverage in Security.nl]
Sandbox evasion techniques: A security researcher going by Fudgedotdotdot has published an overview of recent sandbox evasion techniques used in the wild.
FBI DPRK crypto PSA: The FBI has issued yet another public service announcement about North Korean hackers using complex social engineering attacks to infiltrate and steal funds from blockchain and cryptocurrency firms.
Crypto-hacks overview: Google's Mandiant division looks at all the recent attacks used by threat actors against cryptocurrency platforms. Nothing new, but a good overview.
Head Mare: Kaspersky looks at Head Mare, a pro-Ukrainian hacktivist group that emerged last year and has targeted Russian and Belarus companies with ransomware attacks.
Stone Wolf: Russian security firm BI.ZONE has published a report on a financially motivated group named Stone Wolf that is attacking Russian companies. The group's main tool is the Meduza Stealer, delivered through phishing campaigns mimicking legitimate providers of industrial automation solutions.
Roblox npm malware: DevSecOps company Checkmarx has published a report on a malicious malware campaign that used npm packages designed to look like noblox.js to target the developers of Roblox-themed apps with malware.
"Dozens of malicious npm packages mimicking the popular 'noblox.js' library have been identified in a campaign dating back to August 2023, with the most recent ones appearing in late August 2024."
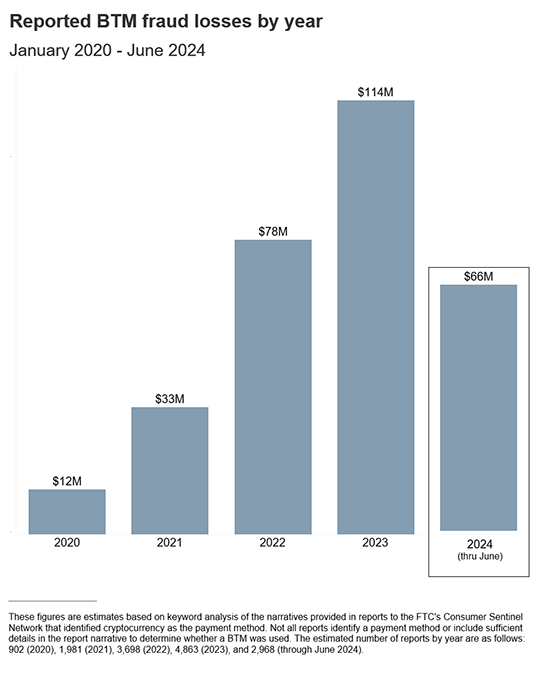
Bitcoin ATM scam numbers: Americans have lost $114 million worth of cryptocurrency to scams involving Bitcoin ATM machines. The US Federal Trade Commission says the losses have increased tenfold over the past four years, from only $12 million in 2020. The current year is expected to match last year's numbers, with over $66 million reported in Bitcoin ATM scams in the first half of the year already.
Malware technical reports
CyberVolk ransomware: ThreatMon has published a report on a new RaaS platform named CyberVolk. The service launched at the start of July and targets home users with small $1,000 ransoms. ThreatMon says the group claims to operate out of India and has aligned with pro-Kremlin hacktivist groups.
Cicada3301 RaaS: Morphisec has published a report on Cicada3301, a new Ransomware-as-a-Service that launched in June this year. The company found several similarities to the AlphV (BlackCat) ransomware code. The report comes after a similar one from Truesec.
MacroPack: Cisco Talos looks at how various threat actors are abusing the MacroPack red-team payload generation framework for attacks in the wild.
DarkCracks: QiAnXin researchers have published an analysis of DarkCracks, a new loader spotted in attacks targeting Korean users. [Later edit: Now in English]
Zharkbot: OALABS researchers have shared IOCs for the new Zharkbot malware loader.
WikiLoader: Palo Alto Networks looks at the campaign that used malicious versions of its GlobalProtect setup utility to infect targets with the WikiLoader malware. This was initially spotted by Trend Micro last week.
ViperSoftX: Trellix has published another report on ViperSoftX, a trojan they've been tracking since 2020. Recent tactics include the wider adoption of AutoIt, mainly for evasion techniques.
Emansrepo Stealer: Fortinet looks at Emansrepo, a new Python-based infostealer that has been used in limited attacks since November 2023 but was only spotted by a vendor last month.
Powershell keylogger: CyFirma has published a report on a yet-to-be-named Powershell-based keylogger.
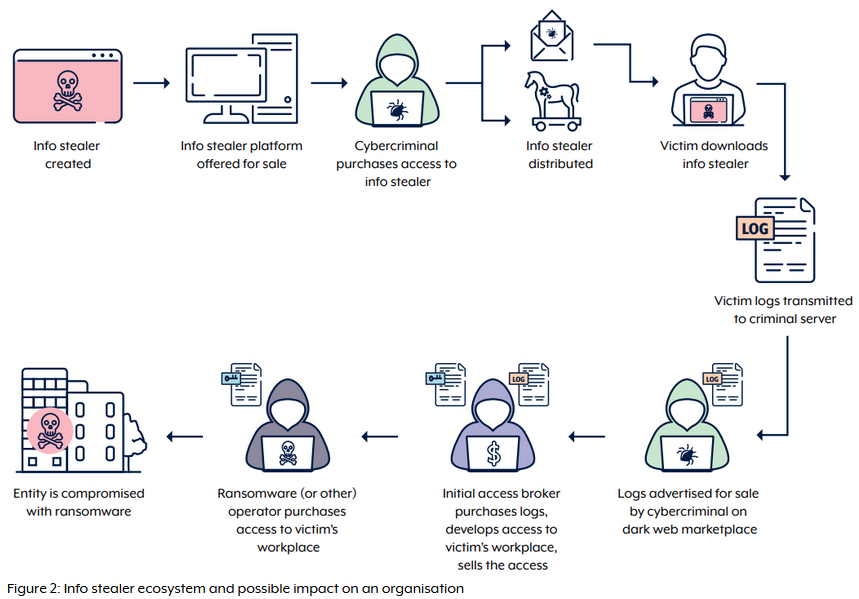
Infostealers warning: Australia's cybersecurity agency has put out a public security advisory about the dangers of infostealer infections and how credentials stolen in these incidents are powering later breaches at private companies and government agencies.
Sponsor Section
GreyNoise founder Andrew Morris demonstrates how people use the GreyNoise sensor network to find threats and detect attacks.
APTs, cyber-espionage, and info-ops
Operation Oxidový: Seqrite researchers have published a report on a spear-phishing campaign targeting the Czechia with NATO-themed lures. Smells like the same old APT28 low-quality spam.
MuddyWater: Qihoo 360 has published a report on a MuddyWater campaign using legitimate remote access and control utilities like ScreenConnect, SimpleHelp, Syncro, and N-Able as replacements for backdoors.
Finland warns of APT router abuse: Finland's police and cybersecurity agency say they've encountered cases where local devices have been used to funnel malicious APT traffic. Foreign espionage groups have infected routers, firewalls, and NAS devices in Finland to proxy attacks and make connections look like they were coming from inside the country. Officials have described the attackers as "non-democratic states." [Additional coverage in Yle]
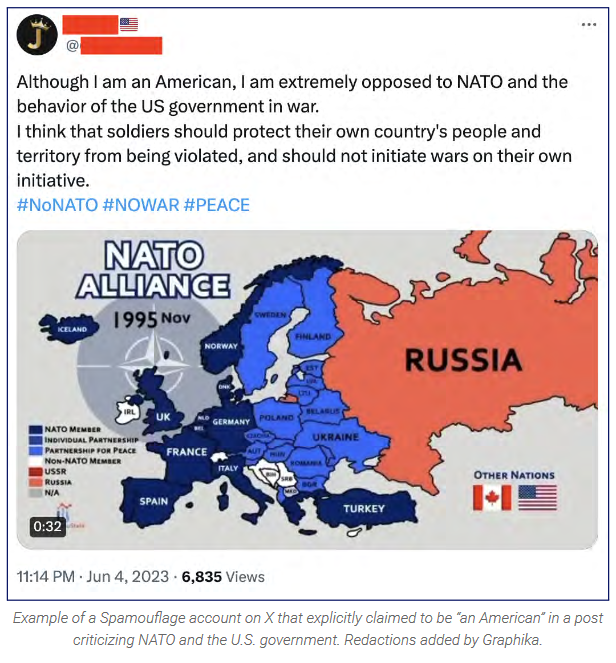
Spamouflage returns for the US elections: China's most prolific disinformation group has ramped up operations targeting the upcoming US presidential elections. Spamouflage operators were identified using Twitter and TikTok accounts to denigrate both Democratic and Republican candidates and sowing distrust in the legitimacy of the US electoral process. The group also spread divisive narratives on sensitive social issues such as gun control, homelessness, drug abuse, racial inequality, and the Israel-Hamas conflict. Research group Graphika says some of Spamouflage's content was "was almost certainly" generated with AI tools. Researchers say the accounts tried to pass as American citizens but failed to gain any traction.
Vulnerabilities, security research, and bug bounty
Windows IPv6 RCE: Russian security firm BI.ZONE has published a technical analysis of CVE-2024–38063, a zero-click RCE in the Windows TCP/IP stack that can be exploited via IPv6 packets. Based on this and on previous reports of the same vulnerability, this is complex to exploit, but once a public PoC is published, this is going to be a major problem.
"Despite the complexity associated with the exploitation of this zero‑click TCP/IP RCE flaw, we recommend you to disable IPv6 at the hosts where it is not used."
Windows EoP zero-day: PixiePoint has published an analysis of CVE-2024-38106, a zero-day in the Windows kernel that was exploited in the wild by a DPRK APT named Citrine Sleet in attacks targeting the crypto community.
Spring Cloud Skipper vulnerability: SecureLayer7 has published a write-up on CVE-2024-37084, a remote code execution in the Skipper server component of the Spring Cloud Data Flow component. This was patched in July.
"This vulnerability arises from the use of a standard Yaml constructor, which permits the deserialization of arbitrary objects. This flaw exposes systems to potential remote code execution (RCE) attacks if malicious YAML data is provided."
D-Link won't patch four bugs: Taiwanese hardware vendor D-Link says it won't patch four recently discovered vulnerabilities impacting a line of now discontinued SOHO routers. The company says the bugs were reported after the affected DIR-846 router series reached End-of-Support. All four vulnerabilities are RCEs that can allow remote attackers to take over a router, and all have severity scores of 8.8 or 9.8. The DIR-846 line reached End-of-Support in December 2022.
VMware security update: VMware has released a security update for its Fusion middleware product.
AVTech PoC: There's a newer PoC (older here) for that unpatched AVTech zero-day that recently made the news. [h/t ScreamingGoat]
EUCLEAK attack: Security firm NinjaLab has discovered a side-channel attack in the cryptographic library of Infineon secure microcontrollers. Named EUCLEAK, the attack can be used to retrieve private keys from devices using Infineon secure chips. The vulnerability went unnoticed for 14 years and affects more than 80 of the company's most secure products. Among the affected products are TPMs, Feitian access cards, and YubiKey hardware security keys, although all attacks require physical access. Yubico has released security updates throughout the year. NinjaLab believes that some crypto-wallets, passports, and some smart cars may also be vulnerable to the attack. [Additional coverage in ArsTechnica]
Infosec industry
New tool—GoffLoader: Security firm Praetorian has released GoffLoader, a tool to facilitate the easy execution of Cobalt Strike BOFs and unmanaged PE files directly in memory without writing any files to disk.
HITB2024BKK talks: Slides from the Hack In The Box 2024 Bangkok security conference, which took place at the end of August, are available on the conference's site.
Off-By-One 2024 videos: Videos from the Off-By-One 2024 security conference, which took place at the end of June, are available on YouTube [Day 1 and Day 2].
TROOPERS 2024 videos: Videos from the TROOPERS 2024 security conference, which took place at the end of June, are available on YouTube.
Free course: Stratosphere Labs is hosting a free "Introduction to Security" 14-week class starting on September 26.
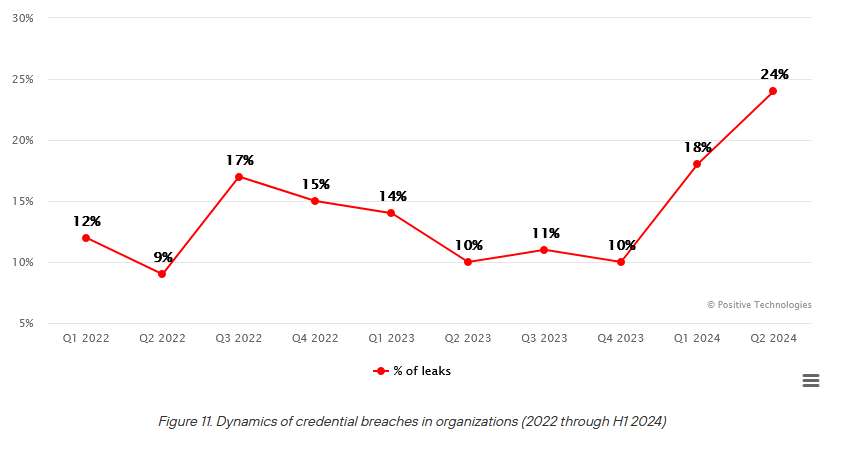
Threat/trend reports: Kaspersky, Positive Technologies, and ThreatMon have recently published reports covering infosec industry threats and trends.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk to Alex Joske, author of a book about how the Chinese Ministry of State Security (MSS) has shaped Western perceptions of China. They discuss the MSS's position in the Chinese bureaucracy, its increasing role in cyber espionage, its use of contractors, and the PRC's vulnerability disclosure laws.
In this podcast, Tom Uren and Patrick Gray discuss an Australian government effort to bridge the gap between online and real identity across the whole economy. It addresses a real need, but Tom doesn't think it will go smoothly.
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!





