Risky Biz News: White House bars federal agencies from using rogue commercial spyware
In other news: France bans recreational apps from government smartphones; Twitter source code leaked on GitHub for months; new WiFi attack disclosed.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
The White House issued an executive order on Monday barring federal government agencies from using commercial spyware products that pose a national security risk.
The ban does not apply to all spyware and surveillance tools. US federal agencies can still use spyware if the vendor has not been linked to any cases of abuse.
Cases of abuse that will automatically apply the label of "national security risk" to a spyware vendor include situations where the vendor's products have been used to spy against the US government.
Another case is for vendors that have not been licensed to operate in the US.
A spyware vendor is also considered a security risk if its tools have been used to spy on victims and led to human rights abuses or the limitation of various freedoms. This includes illegal surveillance operations against activists, academics, journalists, dissidents, or political figures, in both the US and abroad.
The executive order is a proverbial "separate the wheat from the chaff" attempt from the White House in regard to the spyware industry, which has gone largely unchecked and unregulated for the past two decades. Some vendors have been playing by informal rules, while others have been selling their products to anyone with an open wallet.
As Cyberscoop notes, the White House does not intend to create a list of allowed and banned spyware vendors. The purpose of the EO is to steer government agencies away from using vendors that lack a moral compass and could be in a position to leverage information from past engagements and turn on their US employers.
As The Record also notes, the executive order also comes ahead of the second Summit for Democracy, taking place this week in Washington.
"At the event, which is organized by the US and a number of other countries, the administration will release a set of guiding principles for governmental use of surveillance technology — something that was promised during last year's summit."
The White House EO has received generally good feedback, but some also wanted to see a more severe crackdown on misbehaving spyware vendors. For example, Jim Hines, Ranking Member of the House Permanent Select Committee on Intelligence, would have wanted to see the White House also impose sanctions on rogue spyware makers, not just bar them from working with US federal agencies.
In addition, multiple voices in the surveillance tracking business pointed out that the EO only mentions federal agencies and doesn't specifically ban state and local governments from doing business with rogue vendors.
Breaches and hacks
Twitter source code leaks: A portion of the Twitter source code was leaked on GitHub earlier this year. According to the New York Times [non-paywall], Twitter only recently learned of the leak. The code appears to have been available online for several months until Twitter moved last week to file a DMCA request with GitHub. The files are believed to have been leaked by an employee fired at the end of last year and posted on GitHub under an account named "FreeSpeechEnthusiasm"—in a mocking gesture to one of Musk's public statements. In a case filed last week, Twitter asked a judge to order GitHub to reveal details about the user who uploaded the code to its site but also those who downloaded and viewed it.
Latitude hack update: Australian financial services company Latitude says the personal information of nearly 14 million customers was stolen in a security breach. The company says the breach took place after a threat actor obtained a Latitude employee's login credentials and logged into its network to steal data stored on the servers of two service providers. Stolen information includes PII data but also identification documents, with the bulk being copies of customer driver's licenses. This marks the fourth update Latitude has posted on the breach after initially saying that only 330,000 customers were impacted.
Sun Pharma ransomware attack: Sun Pharma, one of India's largest pharmaceutical companies, says it expects to lose some revenue after suffering a ransomware attack at the start of this month. According to BQPrime, the company is currently in the process of recovering its network.
Leaks summary report: Security firm ThreatMon has published an analysis of 20 lesser-known leaks that have been reported on social media and dark web forums throughout the past year.
General tech and privacy
Push notifications are now universal: With the release of Safari 16.4 for iOS, the W3C's Push API and the Notification API are now universally supported across all major web browsers. The two APIs were formally adopted in 2016, but their adoption has been slow on Safari and Apple devices, where Apple tended to use its own proprietary technology.
Windows 12: The first leaks have appeared about Windows 12, Microsoft's next Windows OS iteration. The project appears to be a spiritual successor to Windows 10X, a now-canceled Windows version.
GitHub adds SBOM support: GitHub has added a new feature to allow users to generate NTIA-compliant SBOM files for any code repositories that have a dependency graph.
Government, politics, and policy
France bans recreational apps from govt devices: The French government has banned public officials from installing any type of "recreational apps" on their work phones. The ban covers TikTok but also other social media applications. The French government cited national security concerns for imposing the ban. More in the government's press release [PDF].
Bug bounty bill stalls in Russia: A proposed law to legalize white-hat bug bounty programs in Russia has hit a roadblock following criticism filed by the FSB intelligence agency, according to Vedomosti.
Iran receives Russian cyber-weapons: The Russian government is supplying advanced cyber weapons to Iran. The deal is part of an exchange where Iran has provided Russia with drones and ammunition to be used in its war in Ukraine. Sources who spoke with the WSJ [non-paywall] say the Tehran regime has received advanced software to hack the phones and systems of dissidents and adversaries. In addition, Russia has provided Iran with equipment and software for internet censorship and allow Tehran officials to monitor, intercept, redirect, or degrade the mobile communications of its citizens.
South Korea to review CCTV and IP cameras: South Korean intelligence agency NIS has published new guidelines that forbid government agencies from using any CCTV or IP security cameras that have not gone through a formal "security verification" process. Government agencies and local government administrations have been told to ask for verifications and remove non-compliant gear. According to local media, NIS updated its guidelines on the use of CCTV and IP cameras following a major security incident at a Seoul plastic surgery hospital. During the incident, hackers stole video footage from its CCTV systems on private medical examinations and advertised it on underground Chinese adult forums. Authorities linked the hack to the clinic's use of vulnerable IP security cameras.
50+ US government employees hacked: At least 50 US government employees in at least ten countries overseas have had their mobile phones targeted with commercial spyware, the Washington Post [non-paywall] reports. Officials described the number to be larger than what they expected, a number they also believe will grow as the investigation continues. US officials did not want to say which spyware maker's tools were used and what entity (entities) was behind the attacks.
Data center security bill: US lawmakers have reintroduced a bill to improve the physical and digital security practices of federal data centers. If passed, the Federal Data Center Enhancement Act would require the Office of Management and Budget to work with federal agencies to develop minimum requirements for federal data centers. The first version of this bill failed to pass the Senate last year. [More in NextGov]
North Dakota to teach cybersecurity: North Dakota officials have passed a bill [PDF] mandating that public K-12 schools teach basic cybersecurity and computer science as part of their coursework. North Dakota becomes the first US state to approve legislation requiring cybersecurity education. North Dakota School Superintendent Kirsten Baesler says EduTech, a division of North Dakota Information Technology that provides information technology support and professional development for K-12 educators, will be developing examples of cybersecurity and computer science education integration plans that may be used to assist local schools in developing their own plans.
Call for a US Cyber Force: The Military Cyber Professionals Association (MCPA), a US-based nonprofit made up of US veterans and scholars, has asked the US government to establish a new branch of the US Armed Forces dedicated solely to cyber operations. The organization argues that for years, each branch of the military has had its own cyber units and approach to cyber operations with "inconsistent readiness and effectiveness."

Risky Business Demo
In this Risky Business demo, Tines CEO and co-founder Eoin Hinchy shows off the Tines no-code automation platform to host Patrick Gray.
Cybercrime and threat intel
Nigerian scammer sentenced: The US Department of Justice has sentenced a Nigerian national to four years and one month in prison for his role in a cybercrime group that engaged in financial scams. Officials say that Solomon Ekunke Okpe, 31, of Lagos, was part of a larger cybercrime crew that operated out of Nigeria and Malaysia. Between 2011 and 2017, the group stole at least $1 million from US victims through BEC, romance, work-from-home, credit card, and other financial scams. A second gang member, Johnson Uke Obogo, was sentenced earlier this month to one year and one day in prison in connection with his role in the gang's scams.
npm spam attack: The npm package repository has been flooded with more than 50,000 new libraries over the course of a few days. According to security researcher Jossef Harush Kadouri, descriptions for most of the packages promoted an e-book downloads portal. When users clicked on links in the description, they were typically redirected to various pay-per-click rewards programs and eventually a phishing site.
Pro-Kremlin hacktivist group: Radware has a summary of all the pro-Kremlin hacktivist groups, along with links to their lame Telegram channels.
Google Play fraud: Google says it blocked more than $2 billion worth of fraudulent transaction attempts last year on its official Play Store platform. The company credited its success to a feature called Obfuscated Account ID that allows apps to detect when multiple devices are making purchases via the same account in a short period of time. Another important security feature was the Play Integrity API, a system that detects if user actions or requests are coming from an unmodified app installed by Google Play and running on a genuine Android device—ideal for detecting hacked devices, malware, or automated bot farms.
Telegram's role in disinformation campaigns: The VSquare investigative news consortium has a report on Telegram's primary role in hosting conspiracy theories and disinformation campaigns.
"German language channels play an important role as an extreme opinion hub influencing the rest of Central and Eastern Europe."
Ransomware in February: Security firm NCC Group says the LockBit ransomware group accounted for the vast majority of ransomware attacks that took place in February 2023, with 129 ransomware attacks out of a total of 240. It marks a 150% spike in the group's activity compared to January when it hit only 50 victims.
Red Canary threat detection report: Cybersecurity firm Red Canary has published its yearly report that compiles data from nearly 40,000 threat detections across the company's network of 800+ customers. The report covers multiple cybercrime trends, from ransomware to stealers and from IABs to email threats.
Malware technical reports
NullMixer update: Security researcher Luc4m says that during March 2023, the NullMixer malware operation infected more than 8,000 devices across North America, Italy, and France. The NullMixer malware, first spotted last year by Kaspersky, uses SEO poisoning to lure users into infecting themselves and then renting access to their computers to other cybercrime gangs—mostly infostealers. Luc4m says this recent NullMixer malware has mostly infected Windows 10 users but has also managed to land on some Windows Servers and IoT devices running the Windows Embedded OS. A noticeable change in tactics for the March campaign was the gang's use of YouTube videos where they walked victims through a step-by-step process of installing cracks and pirated software—which contained their hidden malware.
Makop ransomware: Security researcher Luc4m has a report on the Makop ransomware. The report's main conclusion is that the Makop gang is still successful in compromising companies even if they had not updated their attack arsenal for almost three years, since 2020, when they were first spotted.
Rhadamanthys: CheckPoint has a report out on Rhadamanthys, an advanced infostealer that debuted on the dark web in September of last year to a warm reception from cybercrime groups. CheckPoint describes it as "malware that tries to do as much as possible" and that its success can be explained by the motto that "a strong brand is everything."
LimeRAT: ANY.RUN has a breakdown of the LimeRAT malware.
DBatLoader: Zscaler researchers have spotted a DBatLoader campaign targeting various businesses in European countries, where they drop payloads like the Remcos RAT and Formbook infostealer.
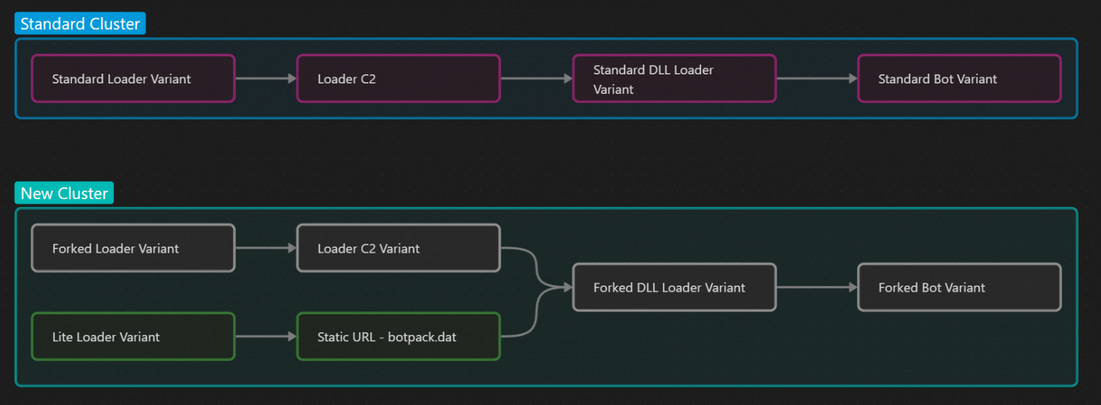
IcedID goes light: Proofpoint has spotted two new versions of the IcedID banking malware, both of which appear to have had their banking fraud-related features removed and are being used as a classic malware loader only. The first version is named IcedID Lite and was first spotted in November of last year. The second version, named Forked, was seen last month, in February 2023. The Lite version was deployed as a second-stage payload on systems previously infected with Emotet. The Forked version is being dropped on user systems via mal-spam campaigns, similar to the original IcedID infection chain.
Sponsor Section
Proofpoint is one of this newsletter's main sponsors. Below is a product demo Patrick Gray, the host of the main Risky Business podcast, recorded with them last year, where they show off Nexus People Risk Explorer, the company's product for mitigating insider threats:
APTs and cyber-espionage
New APT43 group: Mandiant has a comprehensive report on the activities and modus operandi of a new APT group it tracks as APT43, a cyber-espionage group the company has linked to the Reconnaissance General Bureau (RGB), North Korea's main foreign intelligence service. Some of this group's operations have been previously covered in past public reports under Kimsuky and Thallium. Mandiant says the group primarily engages in strategic intelligence collection, usually around foreign policy and nuclear security issues. The group operates on a high tempo and typically focuses on spear-phishing and credential collection operations. Mandiant says it has not seen the group abuse zero-days. APT43 has also coordinated with "other elements of the North Korean cyber ecosystem." In addition, Mandiant says APT43 also engages in crypto-mining operations as a way to generate cryptocurrency to fund its cyber-espionage operations.
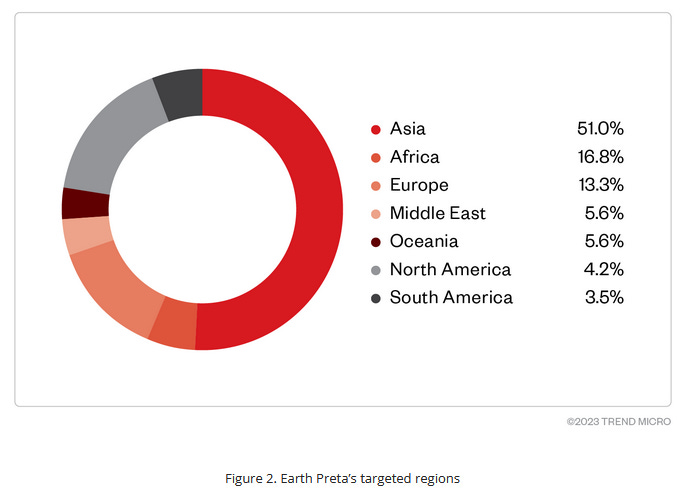
Earth Preta: Trend Micro says it identified more than 200 organizations that have been compromised by subgroups of Earth Preta, a suspected Chinese cyber espionage group. Some sub-groups focused on the cyber-espionage of government and diplomatic entities, while others focused on stealing intellectual property and sensitive business information. Trend Micro says it also recorded cases where victims were compromised by two groups simultaneously, indicating possible overlaps in collection requirements between the groups. More than half of the victims are located in Asia.
Vulnerabilities and bug bounty
Apple security updates: Apple has released security updates for almost all its major products this week. Hidden in the updates is also a second patch for CVE-2023-23529, a zero-day it first patched last month. This update only applies to iOS 15.x devices, which weren't covered by the initial patch.
AWS Amplify vulnerability: Security researcher Nick Frichette has discovered a vulnerability in the API of the AWS Amplify service that can be used to leak AWS account IDs associated with an Amplify app.
New WiFi attack: A team of academics has discovered a new attack against the 802.11 WiFi standard. The attack targets the power-saving features of WiFi access points, which will often queue network connection frames to be used in future connections. Researchers say their technique allows an attacker to force WiFi access points to encrypt yet-to-be-queued frames using their chosen key and bypass WiFi encryption entirely. The attack can be used to hijack TCP connections and intercept web traffic if it takes place via HTTP. In the case of encrypted HTTPS traffic, even if they can't intercept traffic, attackers will be able to learn the IP address to which a user is connecting. The researchers say the attack has a "widespread impact" and affects "various devices and operating systems (Linux, FreeBSD, iOS, and Android)." In a security advisory, Cisco described the attack as "opportunistic" and said that attackers could only gain information "of minimal value in a securely configured network." Details about the attack [PDF] were presented this week in Tokyo at the Real World Crypto conference.
Infosec industry
Microsoft Security Copilot: Microsoft has launched a new product called Microsoft Security Copilot, a GPT4-powered assistant to help security professionals with incident response investigations and other security tasks. I don't know how I feel about this—my security staff asking an AI about security best practices.




