Risky Biz News: Western countries lack robust knowledge on Ghostwriter group
In other news: Platypus hackers detained in France; US Marshals Service hit by ransomware; Activision employee data leaked online.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Western countries don't appear to have an answer or robust knowledge about the operators behind Ghostwriter (aka UNC1151), a threat actor that has been engaged in a mixture of hack-and-leak and dis/misinformation campaigns over the past half-decade, a report [PDF] from Cardiff University has concluded.
The group, believed to contain a mixture of Belarussian and Russian operators, has been active since 2016. Its activities have included hacking news sites to post fabricated stories, planting manufactured documents on government websites, and leaking doctored evidence across social media.
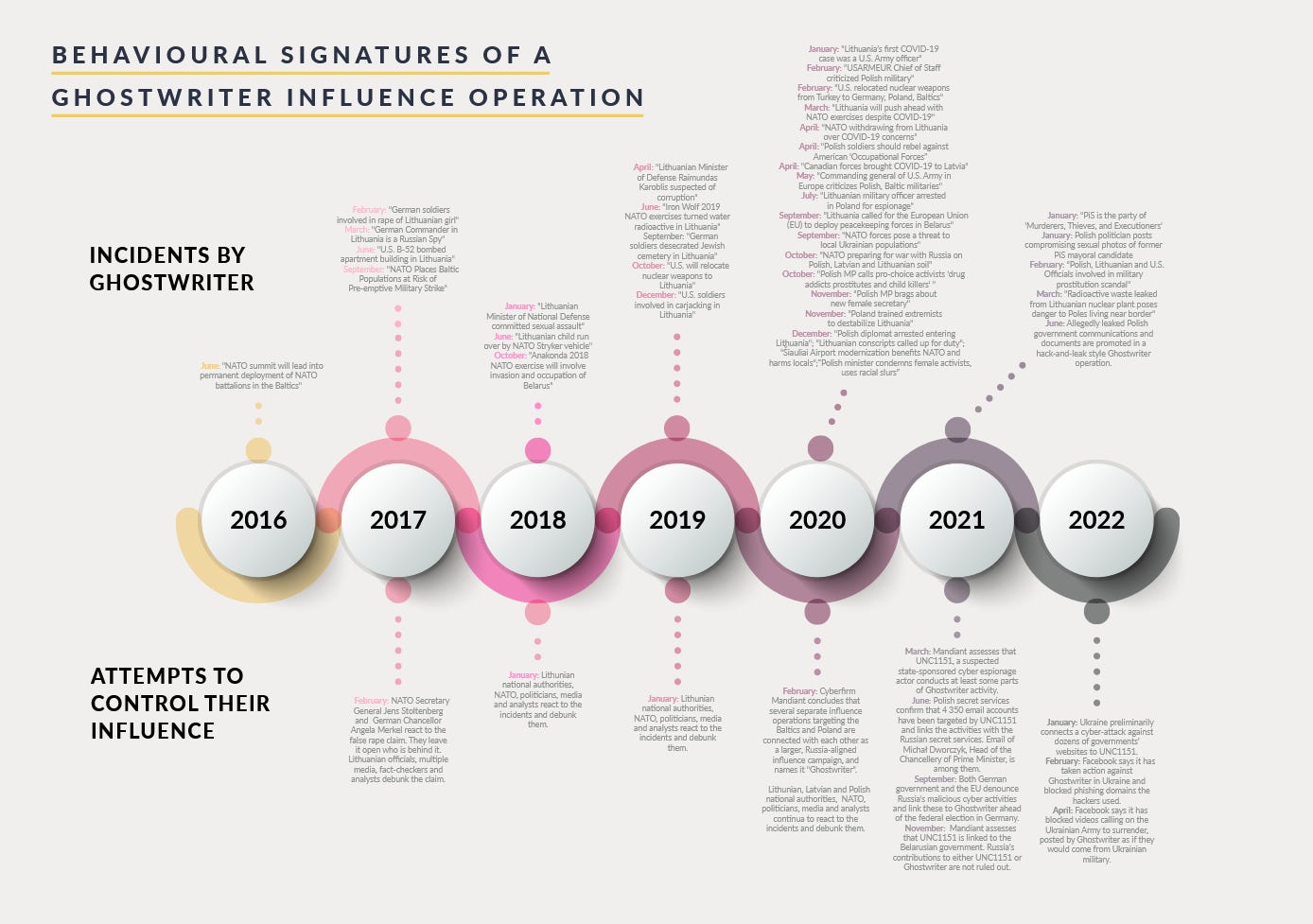
Unlike the IRA and Russia's other internet troll farms and influence operations, Ghostwriter works on a higher level. Operations are timed and planned to coincide before or during important political events or military exercises, often requiring public rebuttals and clarifications from the targeted governments or politicians.
Researchers say because the group mixes both cyber (hacking) and psyop (influence) components, the group has gone under the radar for many years and has yet to be fully understood. Their theory blames the West's confusion about who's supposed to investigate GhostWriter. Is it a country's cybersecurity or its intelligence agency? Is it the private infosec community, or is Ghostwriter official government spook business?
As the researchers point out, this confusion and lack of understanding of the level where GhostWriter operates had allowed the group to run around for four years between 2016 and 2020 before people caught on to what they were doing and that the group existed.
The Cardiff University team believes Western countries are completely unprepared to deal with a group of GhostWriter's level. They lack "robust knowledge of the specific operators behind it," and they are accustomed to using a playbook for dealing with influence operations that was designed to go after low-level social media meme spam from the Internet Research Agency.
"The EU has not put its cyber sanctions toolbox into use and designated sanctions on those responsible for Ghostwriter's activity. [...] No countries, at least based on public knowledge, have used offensive cyber capabilities to target Ghostwriter's activities. Likewise, none of the social media platforms have public reporting on Ghostwriter's activities on their platforms equal to that provided for the IRA, where the public pressure for accountability led the companies to change their policies."
The research team's main proposals focus on more collaboration and intelligence sharing, both between the countries typically targeted by the group and government and private sector players.
It's these cracks that GhostWriter has exploited in the past, knowing that getting a coordinated response from multiple governments, social media networks, and private companies has always been difficult—time during which Ghostwriter was able to cultivate and spread their dis/misinformation.
Just like law enforcement and cybersecurity firms have gotten together to go after, disrupt, and dox ransomware operators, the same level of success can be achieved against Ghostwriter once a more coordinated and centralized effort is put into countering its operations.
"Ghostwriter's partial successes in evolving and expanding its activity is likely due to a mix of limitations in attribution; intelligence sharing; varying level of understanding; requiring responses to the threat in different countries to involve different political actors, as well as social media platforms."
Breaches and hacks
US Marshals Service ransomware attack: The US Marshals Service has been hit by a ransomware attack. Officials say the incident took place on February 17 and was limited in scope, affecting only one of its computer systems. That system contained administrative data and PII data for some employees and suspects under active investigations. The incident did not involve data from the Witness Security Program, commonly known as the witness protection program. The Marshals Service confirmed that both encryption and data exfiltration took place.
LastPass breach update: LastPass has provided a significant update in the investigation into the two security breaches it disclosed last year, in August and in December. LastPass says that after the August incident, the threat actor behind the hack also targeted one of its senior DevOps engineers. This attack leveraged an exploit in a third-party media software toolkit to install a keylogger on the engineer's personal laptop. Using the keylogger, LastPass says the threat actor was able to capture the engineer's master password for their LastPass corporate vault, from where they stole passwords for the company's corporate network and AWS accounts. Together with data from the first breach, LastPass says the threat actor was able to connect to its cloud servers and exfiltrate sensitive data, including some of its customers' encrypted password vaults. Even if some LastPass cloud resources were encrypted, the company says the threat actor managed to obtain decryption keys from the engineer's device and password vault.
US labor union scammed: Pipefitters Local 537, a Boston-based labor union, says it fell victim to a cyberattack and lost $6.4 million from their health fund. Union officials say the incident won't impact member benefits in any way and that law enforcement was optimistic they could recover most of the funds.
MyAlgo hacks: MyAlgo, a company that provides wallets for the Algorand cryptocurrency, has urged users to withdraw funds from mnemonic-based wallets, citing a wave of hacks using an unknown exploit. The company says the original wave of hacks took place last week, and no new exploitation attempts have been seen since. MyAlgo didn't say how much the hackers stole from customer wallets, but a blockchain expert estimated the losses at around $9.2 million worth of assets. John Woods, CTO of the Algorand Foundation, estimated the number of hacked MyAlgo wallets at around 25 and claimed the exploit didn't target an issue with the Algorand protocol or its SDK.
New radio/TV hacks in Russia: More Russian radio and TV channels were hacked to broadcast fake air raid alarms on Monday, similar to what happened last week. The difference this time is that some suspected Ukrainian drones also hit targets in Russia, although no human casualties were reported.
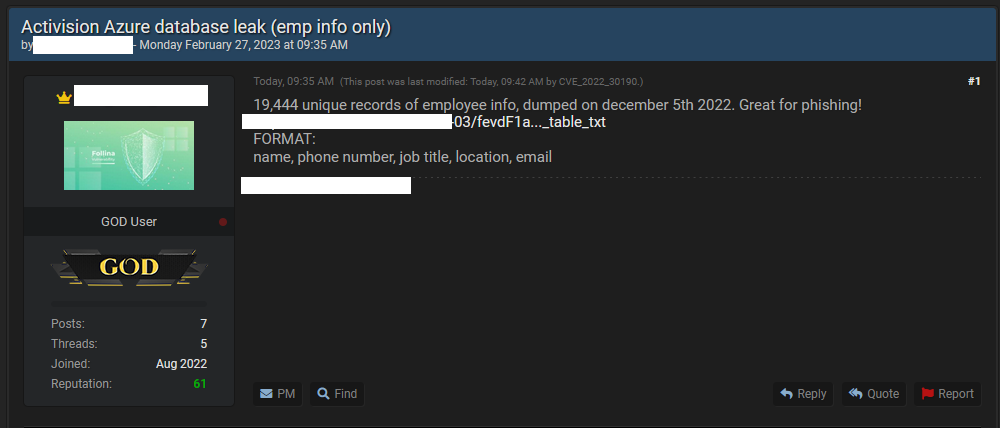
Activision data leaks: The data of thousands of Activision employees has been dumped on a hacking forum. The data originates from a hack that took place in December of last year. Activision confirmed the breach last week after hackers leaked details about upcoming content in the Call of Duty franchise. The leak of employee data comes to contradict Activision's initial statement in which the company claimed that only game-related content was stolen and that no employee or user data was exposed.
General tech and privacy
Client-side encryption for Gmail: Gmail's client-side encryption feature is now generally available for all Google Workspace customers. The feature went in a limited beta test last December.
Government, politics, and policy
TikTok banned in Canada: The Canadian government has banned the use of the TikTok application on government-issued mobile devices. Canada now joins the EU, Taiwan, and the US as countries that have banned the use of the app on government devices, citing fears of Chinese spying. Officials from the Netherlands and the UK are exploring imposing similar bans, while the app is banned in some but not all Australian federal government departments already.
TikTok also investigated in Canada: In addition, on the same day it banned TikTok on government devices, Canada's Office of the Privacy Commissioner has also launched an investigation into TikTok in relation to the company's collection and handling of personal user data, especially children's information.
Easterly proposes to hold software companies liable for bugs: In a speech at Carnegie Mellon University, CISA Director Jen Easterly has floated the idea that tech companies should be held liable for the security flaws in their software. Easterly called for new legislation that would prevent companies from disclaiming liability through contracts and terms of service and being held liable for shoddy products, an avenue the CISA execs believes would lead to better products and better security practices.
Throw another cyber on the barbie: The Australian government plans to set up a new cybersecurity agency to help coordinate responses to hacker attacks and to oversee investment in the field. The new agency will operate within the Department of Home Affairs and will be led by a Coordinator for Cyber Security. The agency will report to Home Affairs Minister Clare O'Neil, who has promised to improve the country's cybersecurity posture after the Optus and Medibank incidents last year. [Read more in 9News]
BSI review on e-commerce platforms: The BSI, Germany's cybersecurity agency, says it reviewed the cybersecurity features of the most popular e-commerce platforms. The study looked at over 400 vulnerabilities disclosed across 29 online shopping solutions over the past five years and found that 78 security flaws were still unpatched. In addition, the study also found that many e-commerce solutions use outdated components, leaving sellers and their customers exposed to attacks.
Age verification on adult sites in France: CNIL, France's privacy watchdog, plans to test an experimental age-verification system for users accessing adult websites across France. The test will run throughout March 2023, and CNIL says the system is fully GDPR compliant. Officials say the system works separately from the adult websites, only tells the adult portals if a user is age-verified or not, and does not track what websites users are visiting.
Sponsor section
Proofpoint is one of this newsletter's main sponsors. Below is a product demo Patrick Gray, the host of the main Risky Business podcast, recorded with them last year, where they show off Nexus People Risk Explorer, the company's product for mitigating insider threats:
Cybercrime and threat intel
REvil funds seized: The US government has seized $317,000 worth of cryptocurrency linked to a payment made to the REvil ransomware gang. According to court documents [PDF], the funds were being stored in an account owned by a Russian national named Danill Shchukin, believed to be located in the city of Krasnodar.
Platypus hackers detained in France: France's National Police has arrested two brothers, aged 18 and 20, for stealing more than $9.5 million worth of cryptocurrency assets from US-based DeFi platform Platypus Finance. The two were detained after a blockchain investigator named ZachXBT identified the Twitter and Instagram accounts of one of the attackers. Speaking to police, one of the brothers who is believed to have orchestrated the hack told police he only wanted to demonstrate a proof-of-concept exploit and then negotiate a bounty with the exchange. Following the hack, Platypus managed to recover $2.4 million worth of assets while the rest was frozen on the blockchain by various exchanges. Police said the brothers only managed to get away with €270,000, of which €210,000 was found stored on a Ledger wallet at their home and seized. [More in ZDNet France]
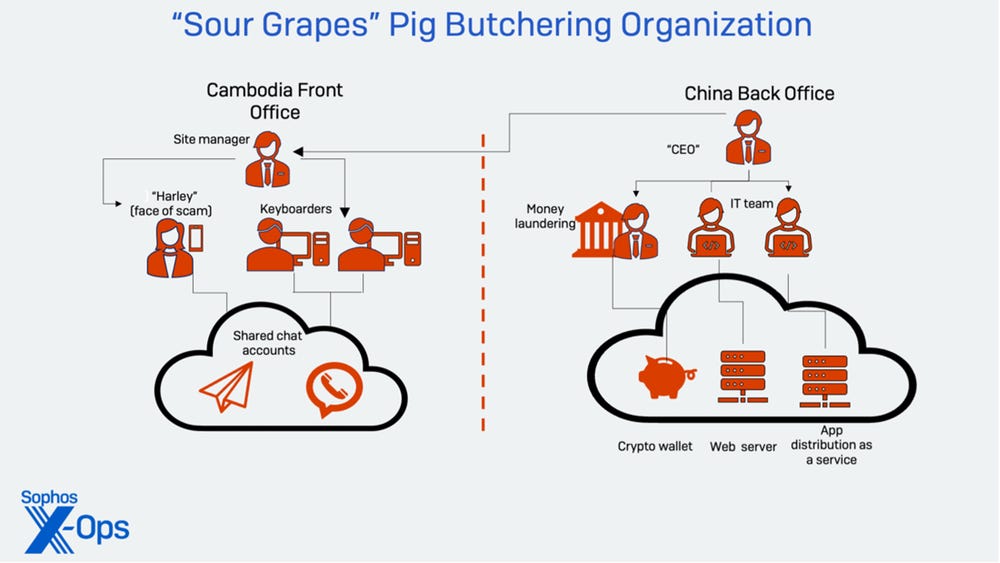
Sour Grapes group: Sophos researchers have uncovered a threat actor they are naming Sour Grapes that has made more than $3 million in cryptocurrency over a period of five months via pig-butchering scams. Pig butchering is a relatively new term that is used to describe a type of scam where threat actors approach victims on dating sites and move conversations to financial topics, trying to lure victims into making various financial or cryptocurrency investments. Sophos says the group operates from offices located in Cambodia, but its leadership is based in China. The gang's membership includes a young man or woman who act as the face of the scam, "keyboarders" who keep the victim engaged in text chats, and a team that generates media content to support various fabricated backstories.
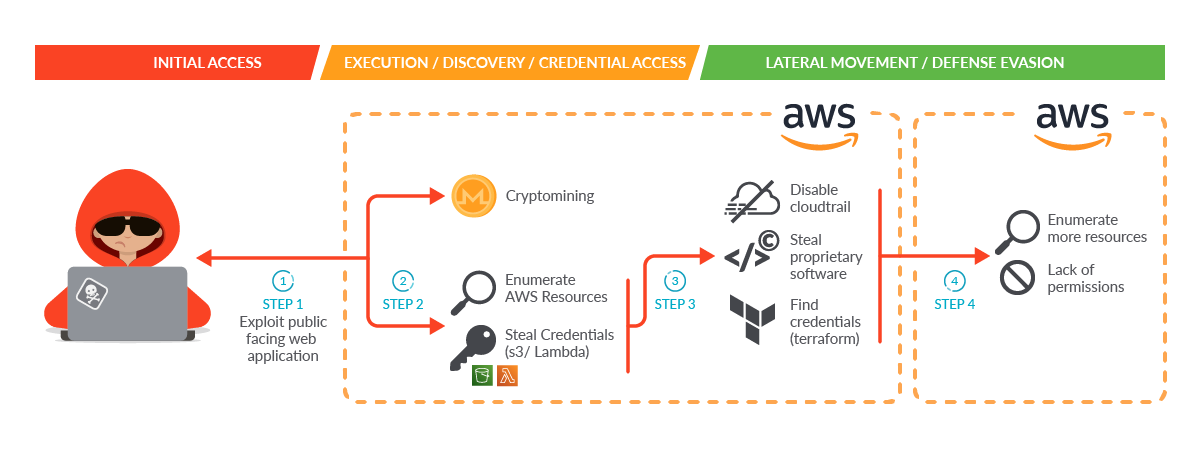
SCARLETEEL group: The threat intel team at cloud security company Sysdig has identified a new threat actor they are naming SCARLETEEL that exploits vulnerabilities in public-facing web apps to breach cloud environments. The group typically installs cryptominers in the compromised environments, but Sysdig says it also saw SCARLETEEL spread across a victim's network and even exfiltrate proprietary data.
PyPI malspam continues: The threat actor spotted last week uploading more than 1,300 malicious Python libraries to the PyPI index is still at it, with hundreds of new uploads per day. Now at more than 3k in total.
WordPress exploitation: Two vulnerabilities in the Houzez WordPress theme and in one of its built-in plugins are being exploited in the wild to hijack WordPress sites.
"The vulnerability in the theme and plugin is currently exploited in the wild and have seen a large number of attacks from the IP address 103.167.93.138 at the time of writing."
OneNote malspam: We've had a few of these reports featured here before, but OneNote malspam campaigns are getting out of hand. Here's a summary of what's been happening via InQuest.
CrowdStrike Global Threat Report: CrowdStrike has published its yearly Global Threat Report, one of the most comprehensive analyses of the current threat landscape. Below are some of the report's main findings.
- IAB adverts have slowly increased each month throughout 2022.
- The "breakout" time from when a host is compromised and then accessed by threat actors has gone down from 98 minutes in 2021 to 84 minutes in 2022.
- The number of malware-free intrusions has gone to 71% of incidents in 2022, up from 62% in the previous year.
- The number of hands-on-keyboard interactive intrusions has increased by 50% in 2022.
- China dominates the cyber-espionage landscape, with Chinese threat actors targeting nearly all 39 global industry sectors last year.
Proofpoint State of the Phish Report: Proofpoint has also published tis annual State of the Phish Report, including an infographic summarizing the findings.

Malware technical reports
Kaiji botnet: QiAnXin has linked the Kaiji DDoS botnet to a cybercrime group the company is tracking under the name of Ares. QiAnXin confirms that while the botnet has dropped cryptominers once in a while, the botnet's main function appears to be to support "several" DDoS-for-hire platforms. QiAnXin has also confirmed previous reports from MalwareMustDie and Intezer that claimed the botnet's operators were based in China.
Hoze cryptominer: Antiy researchers have a technical report on what they call the Hoze cryptominer.
Snip3 Crypter: Zscaler has a report on Snip3 Crypter, a Crypter-as-a-Service that has been available to the underground hacker community since 2021.
Lumma Stealer: S2W researchers have discovered a spear-phishing campaign targeting YouTube account owners with a version of Lumma Stealer.
PikaBot IOCs: OALabs has published IOCs for PikaBot, a new malware strain spotted last week being deployed on systems previously infected with QakBot.
MortalKombat decrypter: Romanian cybersecurity firm Bitdefender has released a free decrypter for MortalKombat, a ransomware strain spotted by Cisco Talos researchers earlier this month. While new, both Bitdefender and Cisco say the ransomware is actually based on the older Xorist ransomware strain. Typical infection methods include phishing emails, exposed RDP endpoints, and as a second-stage payload on systems previously infected by the BatLoader malware.
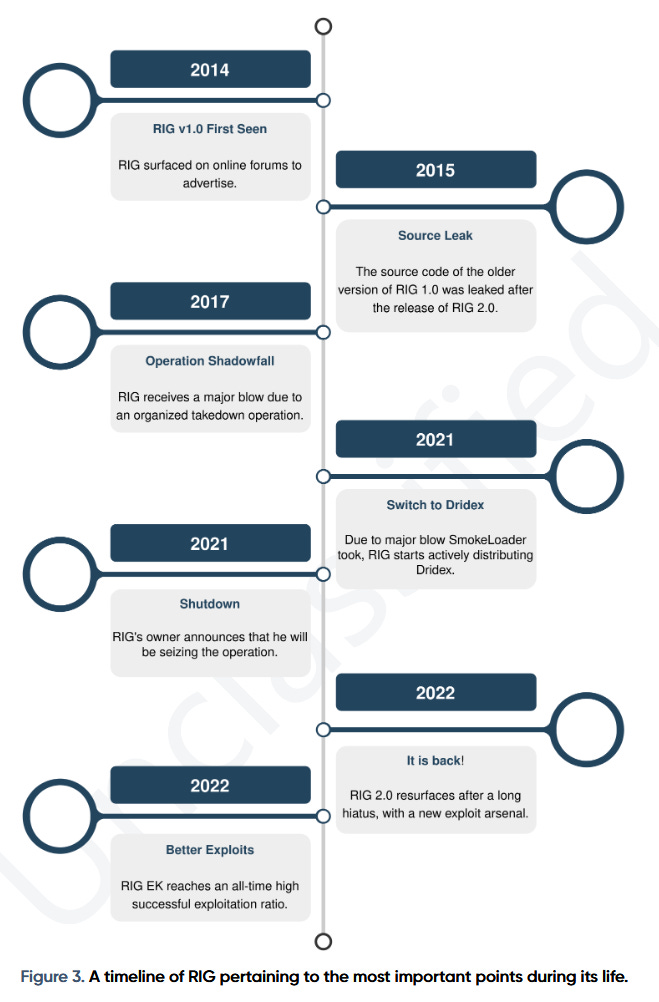
RIG EK still alive: Even if Microsoft has officially retired the Internet Explorer web browser, the operators of the RIG exploit kit are still having tremendous success in infecting IE users with malware. According to a report from security firm Prodaft, the operators of the RIG EK managed to infect almost 30% of the users who visited their malicious websites. Prodaft says users who visited RIG's malicious websites had their IE browsers exploited and malware installed on their devices, including payloads like Dridex, RaccoonStealer. or SmokeLoader. Prodaft credited RIG's high infection rate to gang adding support for two new IE exploits (CVE-2021-26411 and CVE-2020-0674).
APTs and cyber-espionage
APT-C-61: Qihoo 360 has a report on APT-C-61, aka Tengyun Snake, and its recent attacks on organizations across Southeast Asia. Recent attacks have also targeted diplomats from Iran and Turkey as well.
Lazarus zero-day attacks: South Korean security firm AhnLab has spotted Lazarus, a North Korean cyber-espionage group, using a zero-day vulnerability in a local Korean software utility. AhnLab says Lazarus breached a financial company in May of last year and then used a zero-day in a "certificate-related program" to move laterally across the victim's network. Researchers didn’t disclose the name of the vendor because the company has yet to release a patch. AhnLab only described the software as a "certificate-related program widely used in public institutions and universities."
Blind Eagle: BlackBerry has its own report on the Blind Eagle APT, previously covered in reports from Check Point, Qihoo 360, and CNTIC. The report covers the APT's attacks on Colombia and its government agencies.
BlackFly: Broadcom's Symantec has a report out on a Blackfly (aka APT41, Winnti Group, Bronze Atlas) espionage campaign that has targeted two subsidiaries of an Asian conglomerate. Symantec says that both subsidiaries operate in the materials and composites sector, suggesting that the group may be attempting to steal intellectual property.
China's ASEAN hack: Chinese-linked hackers have breached the servers of the Association of Southeast Asian Nations (ASEAN), an international political and economic body of 10 member states across Southeast Asia. The hack, first reported by Wired, took place in February of last year. The hackers allegedly stole gigabytes of data, including thousands of emails and sensitive details from ASEAN member states.
Vulnerabilities and bug bounty
CoD:BO3 hacks: RBN has previously reported on vulnerabilities in games like GTA Online and CoD:Warzone 2 that allowed hackers to run malicious code on players' systems or crash the game servers. Well, there's now another one of these "babies," and this one impacts Activision's Call of Duty Black Ops 3 game, released back in 2015. Basically, if a hacker is in the same lobby, they have a free RCE on player's computer thanks to a vulnerability in the BO3 game. [More in TechCrunch]
CRYSTALS-Kyber side-channel: Academics have published a side-channel attack against CRYSTALS-Kyber, one of the three public-key algorithms currently recommended by NIST as part of its post-quantum cryptography standards.
Tenable Threat Landscape Report: Vulnerability management platform Tenable has published its yearly report [PDF] on the vulnerability threat landscape. Some of the main findings below:
- There were 25,112 vulnerabilities reported in 2022, a 14.4% increase over 2021 and a 287% increase over 2016.
- Old vulnerabilities still plague the software ecosystem, with a set of 2017 bugs being among the most exploited last year.
- 2.29 billion records were exposed in 2022 via data breaches.
- 35% of all security breaches were linked to ransomware attacks.
- Over 3% of all data breaches in 2022 were caused by unsecured databases, accounting for leaks of over 800 million records.
Rapid7 Annual Vulnerability Intelligence Report: A similar report is also available from Rapid7, but this time focused more on the vulnerability exploitation side. Main findings below:
- 28 new vulnerabilities were exploited in 2022, a 15% decrease from 2021.
- Zero-day exploitation went down by 9% compared to 2021.
- 56% of newly exploited vulnerabilities were used in the wild within seven days of their disclosure.
- Only 14 vulnerabilities were known to have been exploited to carry out ransomware attacks.
Infosec industry
BEC attack library: AbnormalSec has a repository of various BEC and phishing techniques spotted being used in the wild.
In a Risky Business demo, Tines CEO and co-founder Eoin Hinchy demonstrates the Tines no-code automation platform to host Patrick Gray.




