Risky Biz News: VMProtect source code leaks (again)
In other news: Intrusion Truth points at Chinese APT nest in Wuhan; NSA and CyberCom's Gen. Nakasone expected to resign later this year; new PPLFault and GoldFault attacks disclosed.
This newsletter is brought to you by Proofpoint. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
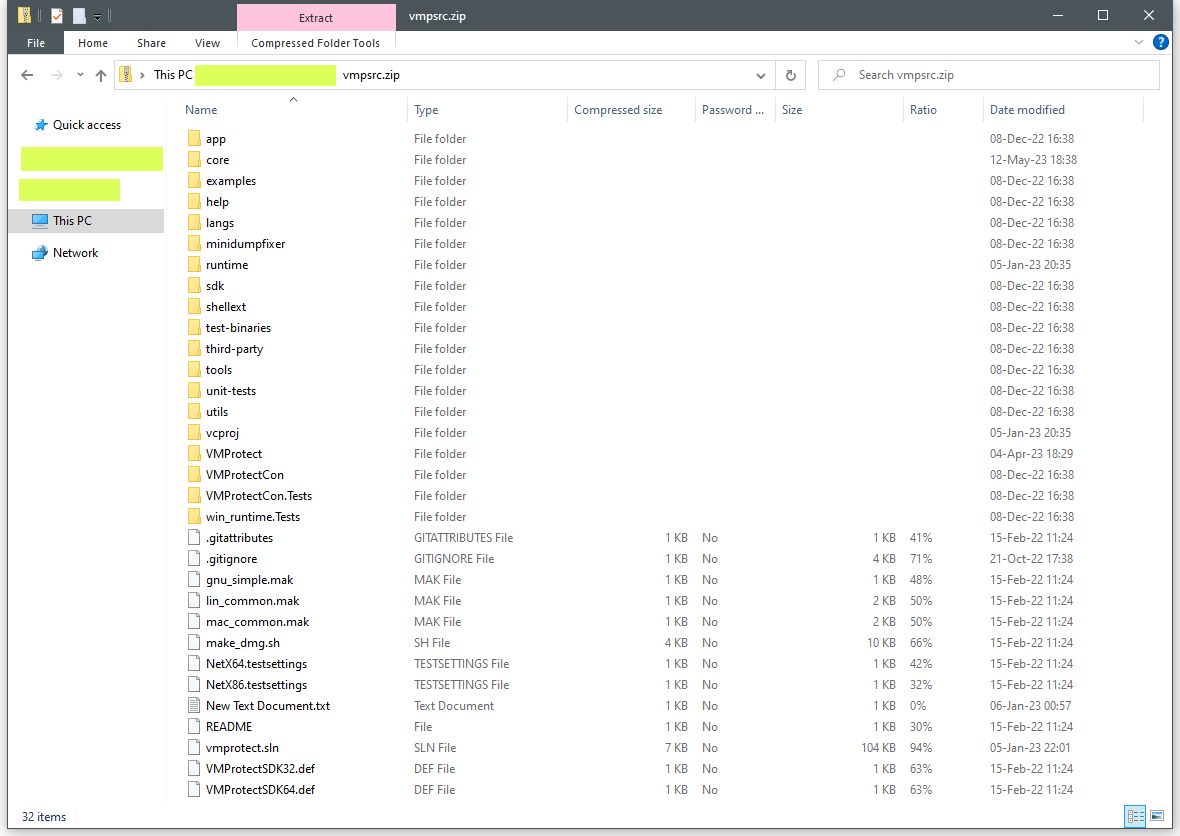
Source code for the VMProtect software has leaked online not once but twice over the past year. The first leak happened in August last year, while the second took place last week via a Chinese IT forum.
Made by a Russian company, VMProtect is a popular solution for protecting software applications by running an app inside a customized virtual machine.
VMProtect has its legitimate uses in the software development community, especially in games and enterprise applications, but it has also been broadly adopted by malware developers to protect malicious payloads—with multiple cybersecurity companies automatically detecting VMProtect-enveloped software as a potential threat.
Threat actors such as APT31, ZINC (Diamond Sleet, Lazarus), the Hacking Team, the Darkside and Rorschach ransomware gangs, the PrivateLoader MaaS, and others, have all used it.
While the cybersecurity research community has created several tools to de-virtualize VMProtect-packed malware, a leak of this nature is of huge interest to researchers, as it can be used to craft better detections and better analysis tools alike.
While the leak was uploaded and then removed from GitHub, the files are still broadly available on anonymous file upload portals.
The Risky Business News podcast:
A reminder that every edition of this newsletter is also available as a podcast:
Breaches and hacks
ABB ransomware attack: Electrification and automation company ABB confirmed last week that it fell victim to a ransomware attack. The incident allegedly took place on May 7 and was the work of the Black Basta gang. The attackers gained access to the company's Windows Active Directory and spread through its internal network. ABB allegedly had to terminate VPN connections with customer networks to prevent the ransomware from spreading further. The attack impacted ABB operations at some of its factories. ABB is one of the world's largest companies and has been a member of the Fortune 500 for more than 25 years.
Discord breach: VoIP and instant messaging service Discord is notifying users of a security breach after a threat actor gained access to the account of a third-party customer support agent. The company says the attacker gained access to the support agent's ticketing queue. This exposed the information for some users with active support requests. Exposed information included email addresses, support messages, and attachments added to any ticket.
0VIX crypto-heist: The 0VIX cryptocurrency platform published a post-mortem on its $2 million crypto-heist from last month.
EswatiniBank cyber-heist: A threat actor has breached the network of EswatiniBank, silently transferred 140 million emalangeni ($7.3 million) to several accounts, and then attempted to cash out the stolen funds via the bank's ATM network. EswatiniBank's manager Enock Mavimbela has confirmed the breach. Mavimbela says the bank detected the attack during the ATM cash-out phase, and it stopped the attack after the attackers liquidated only 700,000 emalangeni ($36,000) of the stolen funds. [Additional coverage in The Times of Swaziland]
US DOT breach: The US Department of Transportation has disclosed a security breach that has exposed the personal information of more than 237,000 current and former federal employees. The incident impacted TRANServe, a system for tracking and reimbursing government employees for commuting costs. The incident is a recent one, and the DOT notified the US Congress of the breach last week, according to an email seen by Reuters.
Toyota customer leak: Japanese carmaker Toyota says it misconfigured one of its cloud environments and exposed vehicle information for more than 2.15 million of its customers in Japan. Exposed information included vehicle IDs, chassis numbers, and historical vehicle location information collected at certain times of day. Toyota says the server has been exposed for more than 11 years, since January 2012, meaning the leaked data can be used to track the movement of past and current customers.
General tech and privacy
Forgetful Browsing: The Brave browser has announced a new feature named Forgetful Browsing meant to block the recent rise of third-party tracking and re-identification, a technique that has become widely adopted since the rise of modern ad-blockers. Brave engineers say Forgetful Browsing works by clearing the browser's first-party storage for a domain a few seconds after all tabs for that site have been closed. Brave says this feature will release in the near future with version 1.53 on the desktop and version 1.54 on Android.
FCC spam: The New York Attorney General has fined three US companies $615,000 for spamming the FCC with fake comments in support of repealing net neutrality (which eventually took place). Fines were levied against LCX, Lead ID, and Ifficient, which collectively posted more than 3.84 million fabricated comments. The NYAG says the same companies also fabricated and submitted millions of comments in support of other US regulatory efforts at the Environmental Protection Agency and the Bureau of Ocean Energy Management.
More Gmail ads: After Google began experimenting with an anti-ad-blocker message on YouTube last week, there are reports that the company is now showing even more ads inside Gmail. The problem is that the ads are not shown at the top or the sides, as most email providers do, but they are secretly inserted between your emails, looking like an unopened message. [Additional coverage in 9to5Google]
Google enters the Bluetooth tracker device market: Google says it plans to update its "Find My Device" service over the summer to support Bluetooth-based tracker devices—similar to Apple's AirTags service. According to Google, the service will be able to seamlessly keep track of trackers from third-party companies like Tile, Chipolo, and Pebblebee.
Government, politics, and policy
EU AI Act: The European Parliament's Civil Liberties and Internal Market committees have given the green light on a final version of the EU AI Act, new rules meant to regulate the use of Artificial Intelligence across the EU market. The AI Act now heads to the European Parliament for a first vote, to be held in June. If passed, the Act would forbid the use of AI tools to provide real-time biometric identification in public spaces and restrict the use of AI tools for biometric identification only to law enforcement purposes. The EU AI Act also bans the use of any predictive policing systems, emotion recognition systems, and the development of any high-risk AI tools that can harm people's health or rights.
Gen. Nakasone expected to step down: Gen. Paul Nakasone is expected to step down from his positions of NSA Director and US Cyber Command head in the coming months. Gen. Nakasone has told colleagues in the Biden administration he's eyeing an exit in August or September this year. The official has spent five years running both agencies. Gen. Nakasone initially wanted to leave last year but was asked by the White House to remain for another year. [Additional coverage in the Wall Street Journal / non-paywall]
Russia explores dark web ban: Speaking at a youth conference, State Duma deputy Anton Gorelkin says he is looking into banning and making the use of the dark web illegal. Gorelkin called the dark web a US military project and described the Tor Browser as a US-funded tool. [Additional coverage in Riamo]
Sponsor section
Proofpoint, this week's sponsor, has published its 2023 edition of Voice of the CISO, a yearly report featuring insights and experiences from more than 1,600 CISOs from around the world. The report covers recent threat actor trends, insights into better defenses, and the latest dynamics in board-CISO relations.

You can also hear Seriously Risky Business editor Tom Uren interview Proofpoint’s Selena Larson in this sponsor interview:
Cybercrime and threat intel
Russian malware dev sentenced: A man from the Russian city of Kostroma was sentenced to 7.5 years in prison for developing malware for a criminal organization. Officials say the group used the malware to steal more than 2 million rubles ($25,000) from Russian banks. The Kostroma man made between $1,000 and $3,000 every month from renting the malware.
Bot network dismantled in Spain: Spanish authorities have arrested the members of a cybercrime gang that used an online bot to take over all reservation spots for Spain's migrant and asylum-seeking services. The group operated an online bot that used different VPNs to bypass government security systems and register reservations on official websites. Spanish police say the gang resold reservations to foreign citizens via an official company at prices ranging from €30 to €200. Officials have detained 69 members. The arrests also included the gang's leaders, four individuals detained in the cities of Barcelona and Valencia.
New gTLDs: Google has announced the public availability of the eight new custom top-level domains. Among the new additions is .zip and .mov, two classic file extensions. For good reasons, cybersecurity experts are criticizing the company and raising concerns the two gTLDs would be abused to confuse users and may lead to a form of phishing and malware distribution. The SANS ISC team has already advised that companies block the two new domains.
MEME#4CHAN: Securonix has published a report on MEME#4CHAN, a phishing campaign distributing versions of the XWorm malware. The company calls the campaign "unusual" because the threat actor used "meme-filled code and complex obfuscation methods."
AI tool ads to malware: Trend Micro has spotted a malware distribution campaign using malicious search engine ads for AI tools to have users infect themselves with malware. Pretty sure there are more of these around.
CryptNet RaaS: ZeroFox researchers have spotted a new Ransomware-as-a-Service named CryptNet. The service is advertised on the dark web cybercrime forum RAMP. CryptNet launched in early April and is currently offering a massive 90% share of any successful ransom payments to affiliates.
"This represents one of the highest shares seen within the RaaS market, with affiliates typically receiving between 60 to 80 percent from most groups."
KillNet: CyFirma has a report on KillNet's evolution from fake hacktivists to a wannabe private hacking company.
New npm malware: One-hundred-sixty-three new malicious npm packages were spotted last week. Check out GitHub's security advisory portal for more details.
Mastodon spam: Mastodon instances have been flooded with cryptocurrency spam over the weekend after a network of accounts registered on Mastodon.social sent out waves of private messages [1, 2, 3, 4, 5, 6].
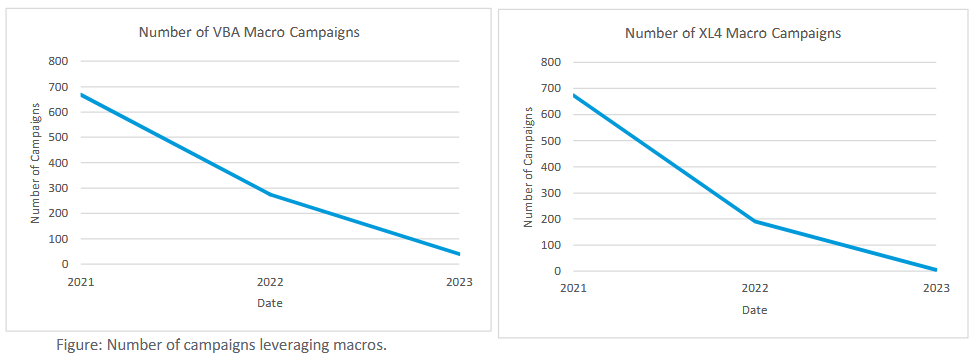
Malware distribution landscape: Email security company Proofpoint says that following Microsoft's decision to block XL4 and VBA macros for Office users last year, it has seen threat actors change their distribution chains and adapt to the new landscape. The company says it observed widespread threat actor experimentation in malware payload delivery, such as using old filetypes and unexpected attack chains. Old file types that have seen new life in malware campaigns include LNK shortcuts, the good ol' PDF, ISO images, but also Windows Script File (WSF) and Excel add-ins (XLL). Proofpoint says it also saw threat actors go back to an old technique named HTML smuggling, while some groups successfully experimented and refined the art of OneNote malspam. More in the company's "Crime Finds a Way: The Evolution and Experimentation of the Cybercrime Ecosystem" report.
KEV update: CISA has updated its KEV database with seven new vulnerabilities that are currently being actively exploited. The list includes:
- CVE-2023-25717 — Ruckus routers
- CVE-2021-3560 — Red Hat Polkit
- CVE-2014-0196 — Linux Kernel
- CVE-2010-3904 — Linux Kernel
- CVE-2015-5317 — Jenkins
- CVE-2016-3427 — Oracle Java SE
- CVE-2016-8735 — Apache Tomcat
CISA ICS security alerts: CISA has published security alerts for 15 vulnerabilities in industrial control systems. Six of the advisories are for vulnerabilities that have a CVSSv3 score of 9.9 or 10 (out of 10). (h/t Ravi Nayyar)
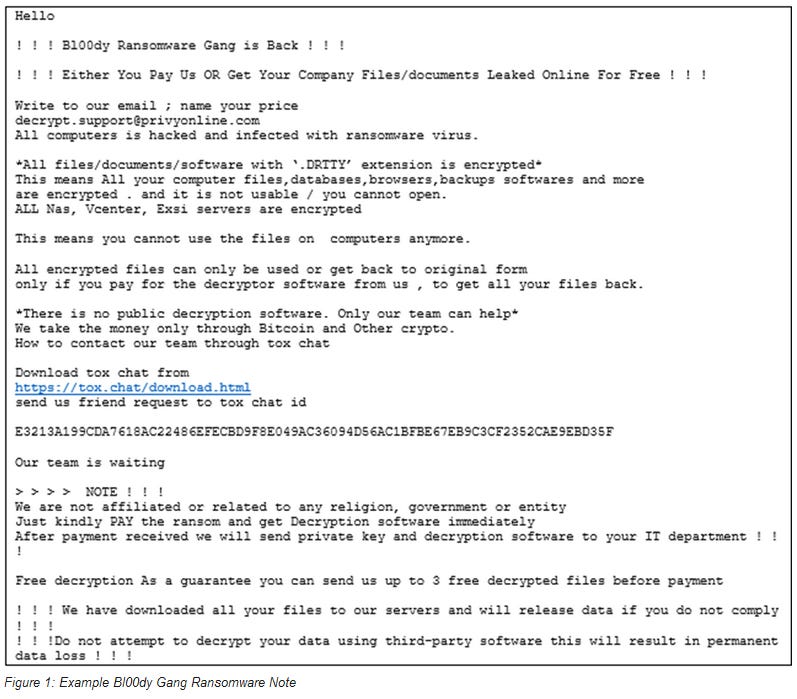
PaperCut exploitation: CISA and the FBI have published a security advisory warning that a new ransomware gang named Bl00dy is exploiting a recently-disclosed vulnerability (CVE-2023-27350) in PaperCut print management servers to gain access to vulnerable servers and deploy their file encrypter. Officials say the gang appears to target the education sector. The Bl00dy gang now joins the Clop ransomware gang and at least three Iranian APTs as groups who are actively exploiting this PaperCut vulnerability.
Malware technical reports
Yayaya Miner: Chinese security firm Antiy has discovered a new threat actor launching SSH brute-force attacks against Linux systems in order to gain access and deploy a new crypto-miner named "Yayaya.
Metastealer: OALABS has published IOCs for Metastealer, an information stealer advertised on underground forums since March of last year.
Maori ransomware: Fortinet's research team has a write-up on the new Maori ransomware.
Risky Business Demo
Proofpoint is one of this newsletter's main sponsors. Below is a product demo Patrick Gray, the host of the main Risky Business podcast, recorded with them last year, where they show off Nexus People Risk Explorer, the company's product for mitigating insider threats:
APTs and cyber-espionage
Intrusion Truth dox: Intrusion Truth, a shadowy online group known for exposing suspected Chinese cyber-espionage operations, has returned to life after nine months of inactivity and published a trio of reports last week. The reports claim to reveal details on a cluster of suspected Chinese hacking operations located in the city of Wuhan. The first report claims that a private company named the Kerui Cracking Academy is training hackers for the Chinese MSS. Intrusion Truth expands on this first report in a second article where they give out the names of five former Kerui graduates, with the authors hinting they might be members of Chinese APT groups. In the last, Intrusion Truth looks at a Wuhan company hiring "vulnerability miners and foreign language experts" using job ads that have identical text with two Shenzen-based companies, one of which is ZIONSEC—an infosec company dedicated to national defense and intelligence work. We'll just leave you with the group's conclusion:
"We also have government clients, a CEO with official PRC government titles, and a bonus link to a shifty hacking school.
You know the drill by now. If it walks like a duck and quacks like a duck…. (should we get that printed on merch?)."
OceanLotus: Chinese security firm Xitan has published a write-up on recent spear-phishing operations carried out by the OceanLotus (APT32, APT-C-00) Vietnamese APT against organizations in mainland China.
CryptoMimic/SnatchCrypto: Japan's CERT team has more details about a new campaign carried out by CryptoMimic (SnatchCrypto), a North Korean APT group specialized in attacks targeting cryptocurrency exchanges.
Vulnerabilities and bug bounty
PPLFault and GoldFault: Elastic security researcher Gabriel Landau has revealed details and published proof-of-concept code on PPLFault and GoldFault, two new attacks against the Windows Protected Process Light (PPL) security mechanism. The attacks can be used to dump PPL process data and gain administrator privileges on a Windows system, respectively. Landau says he reported the attacks to Microsoft last year, but the company declined to patch them. The researcher says he released the exploit code so cybersecurity companies can defend against these new techniques. The two attacks are considered successors for the classic PPLDump attack that Microsoft finally patched last year.
Libssh auth bypass: GitHub security researcher Kevin Backhouse has discovered an authentication bypass (CVE-2023-2283) in the Libssh library that can allow a remote attacker to gain unauthorized access to a user's account via SSH. The vulnerability does not affect the more popular OpenSSH tool.
Netgear router exploit: Claroty's Team82 research unit has published details on a five vulnerabilities exploit chain they used at the Pwn2Own hacking contest last year to hack a Netgear Nighthawk RAX30 router.
CS:GO RCEs: Cybersecurity firm Neodyme has discovered three RCEs in the popular Counter-Strike: Global Offensive game. Valve has silently fixed all issues on the server-side of the game.
Infosec industry
New tool—resocks: RedTeam Pentesting has open-sourced a tool named resocks, a reverse/back-connect SOCKS5 proxy tunnel that can be used to route traffic through a system that can't be directly accessed (due to NAT).
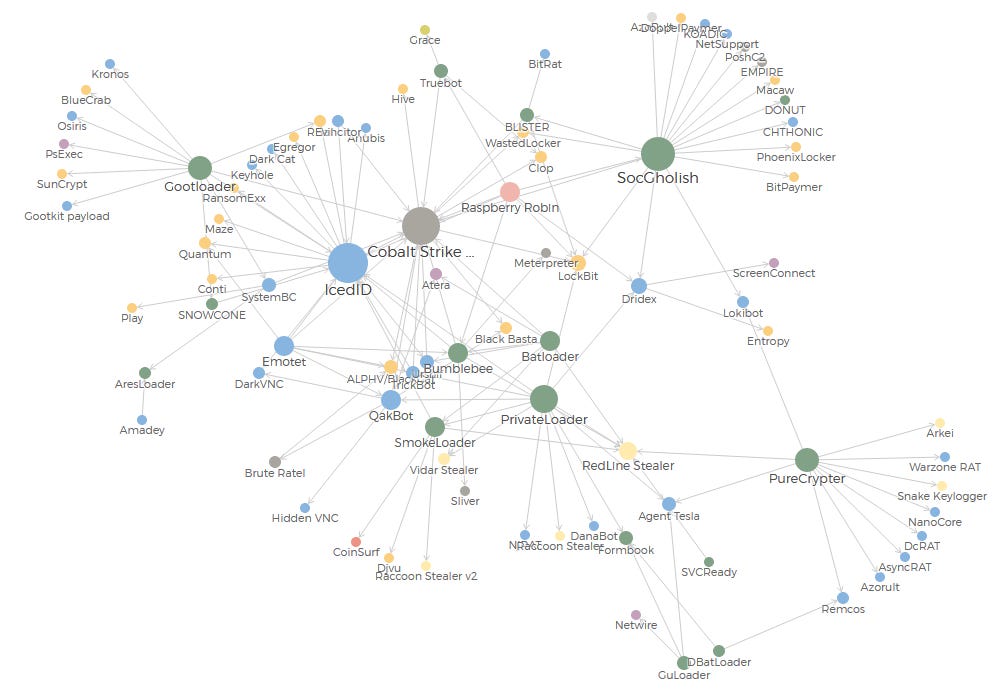
Interactive map: Threat intel analyst Scott Small has created an interactive map of the current initial access and malware delivery landscape. The map shows the most common infection chains spotted in recent attacks and campaigns.
VirusTotal Code Insight update: Google has expanded the VirusTotal Code Insight service with support for new scripting languages. The Code Insight feature was launched at the RSA security conference in March. It works by using an AI model to analyze malware samples and generate natural language descriptions of what the code does. Code Insight initially launched with support for PowerShell malware, but Google has now expanded the service with support for command prompt, VBScript, Batch, and Shell script malware. Google has also doubled the size of file uploads, allowing for the analysis of larger malware samples.
Cost of supply chain attacks: A Juniper Research study estimates that businesses around the world are expected to incur almost $46 billion in losses to software supply chain incidents this year. Juniper expects the same losses to jump by 76% and reach $81 billion by 2026. [Additional coverage in CybersecurityDive]
LinkedIn hibernate: And we're closing this edition with some advice from the indomitable and always excellent SwiftOnSecurity. Hibernating your LinkedIn account should be a must for most infosec practitioners that are at risk of facing some sort of doxing payback.