Risky Biz News: US Treasury sanctions North Korea's hacking school, two cyber units
In other news: FinFisher execs charged in Germany; White House nominates next NSA and CYBERCOM chief; spyware vendor code leaks on GitHub.
This newsletter is brought to you by Thinkst. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
The US Treasury has imposed sanctions on five North Korean entities, including a university where the government trains its cyber forces and two cyber units part of its intelligence apparatus.
Sanctions were levied against the Pyongyang University of Automation, which US officials say has trained many of the cyber units of the Reconnaissance General Bureau (RGB)—North Korea's primary intelligence bureau and main agency behind the country's cyber espionage and cyber thefts.
Officials also sanctioned two of the RGB's bureaus—the Technical Reconnaissance Bureau and its subordinate cyber unit, the 110th Research Center.
The US Treasury Department says the Technical Reconnaissance Bureau developed the cyber tools used by North Korean hackers in past intrusions.
These tools are used by several of the bureau's subunits, including the 110th Research Center, which officials formally linked to the DarkSeoul hacking campaign of 2013 [PDF].
In addition, the sanctions list also included the Chinyong Information Technology Cooperation Company and one of its executives, named Kim Sang Man. US officials say North Korea uses this company as a front to send IT workers abroad in countries such as Russia and Laos to work and generate profits for the regime's weapons of mass destruction and ballistic missile programs.
The FBI previously warned that North Korean IT workers were posing as other nationalities to gain access to Western jobs to steal funds or intellectual property.
According to the US State Department, the sanctions this week are the result of a recently signed cooperation treaty between the US and South Korea.
In 2019, the US Treasury also imposed sanctions on three North Korean APTs—Lazarus, Bluenoroff, Andariel.
Breaches and hacks
Rheinmetall confirms ransomware attack: German weapons manufacturer Rheinmetall has confirmed it was hacked by the BlackBasta ransomware gang. The incident took place last month but only came to light over the weekend when the BlackBasta gang listed the German company on its dark web leak site. The incident came to light days after the German company announced plans to build tanks at a Ukroboronprom plant in Ukraine. [Additional coverage in The Record]
Hospital closes, cites cyber-attack: An Illinois hospital has announced it will cease operations in June. The administrators of St. Margaret's Health in Spring Valley cited several reasons for their decision, such as the COVID-19 pandemic, a shortage of staff, and a recent cyber-attack.
Tornado Cash hijack: A threat actor has hijacked the governance model of Tornado Cash, a cryptocurrency mixing service that has been widely abused by hackers to launder their profits. Two days after the malicious takeover, the threat actor—going by the spectacular name of Mr. Tornadosaurus Hex—has hinted about the possibility of returning control of the service to its developers.
General tech and privacy
Meta fined €1.2 billion: The Irish Data Protection Commission has fined Meta €1.2 billion for not complying with the EU's GDPR laws. Officials say Meta illegally transferred the personal information of EU users to the US without their approval. The IDPC has ordered the company to cease any data transfers and delete existing user data within six months. It is the largest fine imposed under the EU's GDPR to date. In a press release, Meta says it will appeal.
You can edit WhatsApp messages: Meta has rolled out the ability to edit WhatsApp messages up to 15 minutes after they've been sent. The 15-minute timeframe is to help users fix typos but prevent them from maliciously modifying past conversations.
Google open-sources Rust crate audits: Google has open-sourced the security audits for the Rust crates (packages) the company uses for its software. These are Rust crates that have been audited by either Google's security team or trusted third-party entities.
Chrome root store: Google has published more details about its root store program it shipped with Chrome last September.
Windows 365 Boot: Microsoft launched the first public preview of Windows 365 Boot, the company's Windows-in-the-Cloud service.
Netflix rolls out password-sharing restrictions: Netflix has started enforcing its new password-sharing policy that prohibits users from sharing and accessing an account from outside the same household. If a Netflix user wants to share their account with someone living outside their main household, they'll have to pony up $7.99/month going forward.
Government, politics, and policy
Russia to charge foreign companies for internet traffic: The Russian government is exploring the possibility of charging foreign internet companies for the traffic that passes through the network of Russian telecom operators. And while countries are experimenting with four-day work weeks, the Russian government is going backward in time and is looking at six-day work weeks, like it's the 1930s.
The Cyber Gulag: The AP has a good write-up on Russia's monitoring and censorship systems that it's been using since its invasion of Ukraine to clamp down on dissenters.
CISA event: The US Cybersecurity and Infrastructure Security Agency will hold a special event named SBOM-a-Rama, dedicated to advancing the use of SBOM technologies. The event is scheduled for June 14, 2023, and non-US practitioners are also welcome.
White House nominates next NSA&CYBERCOM chief: The Biden administration has nominated US Air Force Lt. Gen. Timothy Haugh to lead the National Security Agency and the US Cyber Command. Gen. Haugh will take over from Gen. Paul Nakasone, who announced plans to step down by September this year. Gen. Nakasone has held both positions since 2018 and initially wanted to leave last year but was asked by the White House to remain for another year. Haugh is a CyberCom veteran, holding multiple positions at the agency already. He was also the inaugural head of the 16th Air Force, the branch's first cyber unit. [Additional coverage in Politico]
Sponsor section
This edition is brought to you by Thinkst Canary. Most companies find out way too late that they've been breached. Thinkst Canary changes this. Deployed and Loved on all seven continents.Thinkst Canary. Deploys in minutes; almost zero admin overhead. It just works!
Cybercrime and threat intel
QuaDream leak: Israeli spyware maker QuaDream accidentally leaked the source code of its REIGN surveillance platform via an exposed GitHub repository back in 2020. The misconfigured repository contained the code for REIGN's admin panel but not for any of QuaDream's exploits or the REIGN spyware itself. However, the REIGN admin panel menu structure revealed the capabilities of the REIGN spyware, according to an analysis by OCCRP reporter Jurre van Bergen. Van Bergen says that at the time, the REIGN spyware could only infect iOS systems and had not yet received support for Android devices. The admin panel suggests the spyware could retrieve information from all major iOS apps, including E2EE instant messaging clients such as Signal, Viber, and Wickr. The QuaDream spyware maker shuttered operations last month, days after CitizenLab and Microsft published an exposé on its operations.
FinFisher execs charged in Germany: German prosecutors have charged four executives of now-defunct spyware vendor FinFisher. Officials say the company sold its spyware to the Turkish government without obtaining an export license from German authorities. Instead, FinFisher created and operated a front company in Bulgaria that enabled the sale. The company's spyware was used in 2017 to spy on Turkish opposition parties, including current presidential candidate Kemal Kılıçdaroğlu. German authorities started an investigation into the company after several freedom of the press and human rights organizations filed a criminal complaint against FinFisher in 2019. FinFisher's headquarters were raided in 2020, and the company went into insolvency in 2022.
iSpoof admin gets 13 years: The administrator of an online service that allowed cybercriminals to make calls and send SMS messages using spoofed identities has been sentenced to 13 years in prison. 35-year-old Teejay Fletcher ran iSpoof, a website that had more than 59,000 registered users before it was taken down in an international law enforcement action in November 2022. Authorities say Fletcher made £2 million worth of Bitcoin from running the site. iSpoof has been linked to at least £100 million in losses across the world.
Hacker sentenced: US authorities have sentenced 38-year-old Chirag Patel to 51 months in prison for hacking into the network of an Arizona hospitality company. Officials say Patel stole and tried to sell the credit card numbers and personal information of the company's customers. In addition, Patel also fraudulently transferred and redeemed customer reward points from the company's customer loyalty program.
Rogue IT worker convicted: A British man was convicted of blackmail and unauthorized access to a computer network after he tried to hijack a ransomware payment from his employer. The incident is related to a February 2018 ransomware attack that hit an Oxford-based company where Ashley Liles was working as an IT security analyst. UK officials say that after his employer got hit by a ransomware gang, Liles abused his position in the company's IT staff to secretly log into his boss' email account and change the Bitcoin payment address shared by the attackers with one under his control in the hopes of hijacking any future ransom payment. While that wasn't bad enough, investigators say Liles also created an email nearly identical with one used by the attackers and pressured his employer to pay. The scheme collapsed when the company's security team noticed the unauthorized access to the executive's email, and a subsequent investigation tied the intrusions to Liles' home IP address.
DOJ scam crackdown: The US Justice Department says it took more than 4,000 legal actions against online scammers over the past three months as part of its efforts to disrupt online fraud and money mule operations across the globe. Disrupted schemes included lottery fraud and romance scam gangs, but also business and pandemic fraudsters. The DOJ's efforts are the fifth US law enforcement campaign over the past years that targeted these groups. So far, officials say they've collectively taken over 12,000 actions.
FBI pig-butchering warning: The FBI says that criminal organizations are using fake job ads to lure people into applying for lucrative jobs in Southeast Asia, but applicants are often trapped and coerced into executing cryptocurrency investment scams. Also known as "pig-butchering," such operations are often run out of Cambodia and Myanmar by Chinese organized crime groups. The FBI says these groups will often trap job applicants using debts or by confiscating their travel documents, and then traffic the workers across borders or compounds following the pattern of classic labor trafficking schemes.
StopRansomware guide update: CISA, the FBI, and the NSA have updated their joint #StopRansomware guide [PDF], initially released way back in 2020. Lots of things changed in the ransomware landscape over the past three years—to put it mildly.
KEV update: CISA has updated its KEV database with three new vulnerabilities that are currently being actively exploited. All three are the zero-days that Apple patched last week (CVE-2023-28204, CVE-2023-32373, and CVE-2023-32409).
Malicious iOS app: An iOS app named iOSKeePass has been caught exfiltrating the clipboard content from devices where it was installed. The app was available through the official App Store, but its listing was removed this week after a victim confronted the developer on GitHub. The app's author claimed the clipboard data collection behavior was just a "clumsy" attempt at data analytics.
SuperMailer abuse explodes: Abuse of the SuperMailer newsletter-sending app has exploded over the past three months. According to email security firm Cofense, around 14% of phishing emails that land in user inboxes today have been sent using SuperMailer. Cofense credited the app's appeal to phishing operators to its support for easy templates, multi-thread emailing capabilities, and its broad compatibility with email systems.
Team Insane PK: Pakistani hacktivist group Team Insane PK has taken credit for the DDoS attacks that targeted 44 Indian banking and finance services last week.
ExposedVC: CyberInt researchers have a profile on ExposedVC, a new dark web forum that wants to be the next go-to destination for data leaks and PII data trading.
Inferno Drainer: A new Phishing-as-a-Service platform named Inferno Drainer has been linked to thefts of more than $5.9 million worth of cryptocurrency assets. According to Web3 security platform ScamSniffer, the service allows threat actors to create phishing pages for more than 220 cryptocurrency brands. ScamSniffer says that since it launched, Inferno Drainer has been linked to thefts from more than 4,800 accounts.
Sneaking Leprechaun: Russian security firm BI.ZONE says it is tracking a new threat actor known as Sneaking Leprechaun that hacks into enterprise servers, steals sensitive data, and then extorts companies with threats to publish the stolen information. BI.ZONE says the group has been active for the past year, and they usually gain access to corporate systems by leveraging vulnerabilities in outdated versions of Bitrix, Confluence, and Webmin servers running Linux.
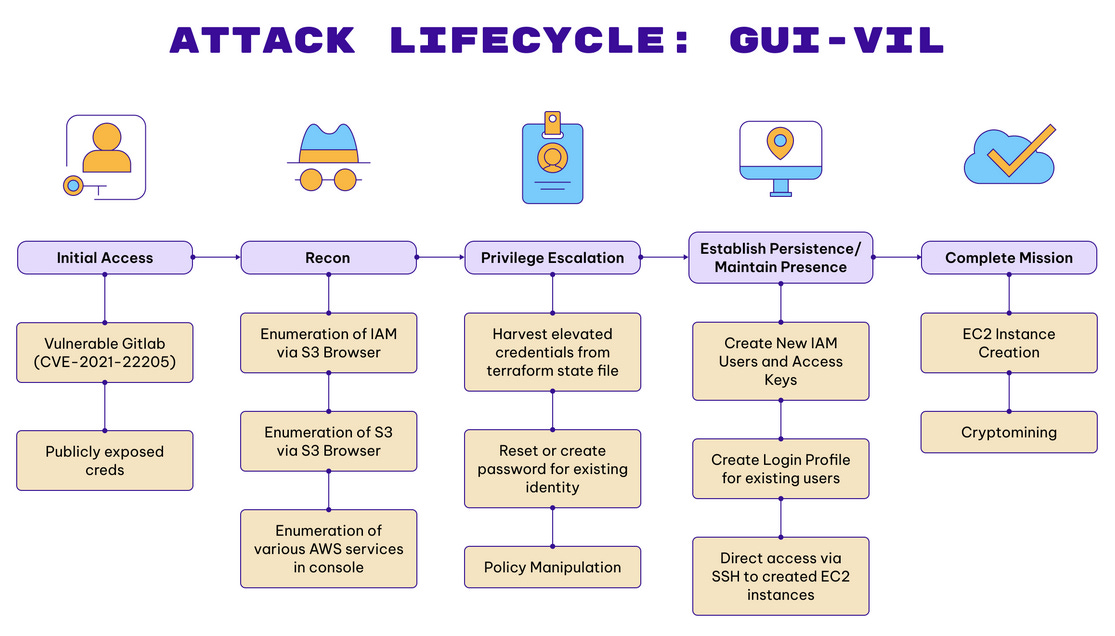
GUI-Vil: Cloud security firm Permiso has discovered a new threat actor that is targeting cloud infrastructure in order to deploy crypto-mining tools. Named GUI-vil, the group has been launching attacks since November 2021. GUI-vil typically gains entry to cloud environments via exposed credentials or vulnerable GitLab servers. The group uses this initial access to elevate privileges and deploy an AWS EC2 instance that solely mines cryptocurrency for the group's profit. Permiso named the group GUI-vil (Goo-ee-vil) due to their preference for using hacking tools with a graphical user interface. Researchers say the group appears to operate from Indonesia.
Malware technical reports
AhRat: ESET researchers have discovered a new Android malware strain. Named AhRat, the malware can secretly record users through their microphones and search and steal local files. So far, the malware has been found inside one single Android app that was available through the Play Store. Because of its limited spread and capabilities, ESET believes the malware may have been used in an espionage operation. Researchers say AhRat appears to be an evolution of an older open-source Android malware strain known as AhMyth, which was used in previous years by the Transparent Tribe group, also known as APT36.
IcedID to Nokoyawa: The DFIR Report team has published a deep dive into infection chains that use the IcedID malware to deploy the Nokoyawa ransomware.
BlackCat: Trend Micro has a report on how the BlackCat ransomware gang is deploying a signed kernel driver in recent attacks to bypass and disable security solutions on infected hosts.
Medusa ransomware: SecurityScorecard has a deep dive into the Medusa ransomware. The group launched in June 2021 and is still active today.
WINTAPIX: Fortinet researchers have discovered a new malware strain deployed in attacks against Middle East targets. Named WINTAPIX, the malware has been used in attacks as far back as 2020. The malware was hidden inside a Windows kernel driver, and its primary function appears to be to establish persistence on a compromised system and then act as a backdoor, proxy, and shellcode executor. Fortinet says that 65% of its WINTAPIX detections came from Saudi Arabia, but the company didn't have sufficient evidence for a conclusive attribution of the attacks.
GuLoader: Lab52 researchers have published a report on the GuLoader malware and how it has been used in recent attacks to drop the AgentTesla infostealer. Check Point has also published a report on the same gang, noting a spike in GuLoader activity over the past three months.
Risky Business Demo
In this Risky Business demo, Tines CEO and co-founder Eoin Hinchy shows off the Tines no-code automation platform to host Patrick Gray.
APTs and cyber-espionage
Lazarus: South Korean security firm AhnLan says the Lazarus North Korean APT is scanning the web for vulnerable IIS servers to exploit.
BlueNoroff APT: Sekoia has published a breakdown of RustBucket, a new malware loader used by the BlueNoroff North Korean APT group. The report covers both the macOS and Windows versions of the malware, initially discovered by Jamf and Kaspersky researchers, respectively. Sekoia believes the malware was used in attacks targeting entities involved in fund management and venture fund, crypto assets, and blockchain, located in Europe, Asia, and North America.
Kimsuky: SentinelLabs has observed an ongoing campaign by Kimsuky, a North Korean APT group, targeting North Korea-focused information services, human rights activists, and DPRK-defector support organizations. Researchers say the campaign uses new infrastructure and focuses on file reconnaissance and information exfiltration using a variant of the RandomQuery malware.
UAC-0063: CERT-UA says it detected a spear-phishing campaign targeting government organizations in Ukraine. CERT-UA says the same group also appears to be targeting other government organizations from Mongolia, Kazakhstan, Kyrgyzstan, Israel, and India.
GoldenJackal: Kaspersky has uncovered a new APT group that has been targeting government and diplomatic entities in the Middle East and South Asia. Named GoldenJackal, the group has been active since June 2019. Kaspersky says GoldenJackal operates its own specific toolset of .NET malware, which includes five malware families known as JackalControl, JackalWorm, JackalSteal, JackalPerInfo, and JackalScreenWatcher. The group has launched very few attacks, and most victims have been government or diplomatic entities, suggesting its primary focus is cyber-espionage.
Fata Morgana: ClearSky researchers have published details on a series of watering hole attacks that took place on at least eight Israeli websites. Researchers named the campaign Fata Morgana and attributed the attacks to an Iranian state-backed actor. The company attributed the attack to a threat actor known as Tortoiseshell (also called TA456 or Imperial Kitten), but with low confidence.
Vulnerabilities and bug bounty
Google Mobile VRP: Google has launched a new bug bounty program named the Mobile VRP, through which the company plans to reward security researchers who find vulnerabilities in official Google Android applications. Apps in scope include Gmail, Google Chrome, Google Cloud, Google Play Services, Chrome Remote Desktop, and the Google quick search box (AGSA). Rewards vary from $500 to $30,000, based on the vulnerability's severity and the quality of the bug report.
NVD data feed retirement: The US NIST National Vulnerabilities Database plans to retire all data feeds in September 2023. NIST asked users to use its existing CVE and CPE APIs to retrieve information on new vulnerabilities.
Windows RDP RCE: Cyolo has published an analysis of CVE-2023-24905, a remote code execution bug in the Windows RDP service that they found and reported to Microsoft. The bug was fixed earlier this month.
Broadcom vulnerability: BugProve researchers have published details on CVE-2023-31070, an out-of-bounds write vulnerability in Broadcom IoT chips. PoC included.
ColdInvite (CVE-2023-27930): Jamf researchers have published a write-up on CVE-2023-27930, a vulnerability known as ColdInvite. Jamf says they discovered the bug while analyzing an Apple zero-day from last year known as ColdIntro (CVE-2022-32894). Both vulnerabilities are similar, allowing an attacker to escape a co-processor and initiate memory corruption.
Azure AD CAP vulnerability: Secureworks researchers have discovered a flaw in Azure AD that enables threat actors to tamper with Conditional Access Policies (CAPs). The vulnerability allows adversaries to install backdoors, modify access rights to bypass MFA without proper logging, and gather information on policy configurations to enable future attacks. The vulnerability was discovered in May 2022, and it took Microsoft almost a full year to recognize it as a threat vector and roll out changes to its cloud infrastructure.
"In May 2022, Secureworks® Counter Threat Unit™ (CTU) researchers investigated which APIs allow editing of CAP settings and identified three: the legacy Azure AD Graph (also known as AADGraph), Microsoft Graph, and an undocumented Azure IAM API. AADGraph was the only API that allowed modification of all CAP settings, including the metadata. This capability lets administrators tamper with all CAP settings, including the creation and modification timestamps. Modifications made using AADGraph are not properly logged, endangering integrity and non-repudiation of Azure AD policies."
MikroTik patches Pwn2Own zero-day: MikroTik has released firmware updates for its routers to patch a vulnerability that was used at the Pwn2Own hacking contest last December. Details about the vulnerability (CVE-2023-32154) were published online last week by contest organizer ZDI, which said that MikroTik had not responded to its messages for nearly six months. In a blog post, MikroTik claimed it never received any such messages.
Arm side-channel attacks: A team of academics says it discovered multiple side-channel attacks on Arm SoCs and GPUs, popular chipsets that are at the heart of Apple MacBooks, iPhones, and many modern smartphones. The attack uses software running on the device to adjust the chipset's power, temperature, and frequency and then researchers use internal sensors to measure executed instructions to infer processed data. In one example, the research team says they used JavaScript code to steal browsing histories and pixel (screen) layouts from Chrome and Safari, even when the devices had all known side-channel countermeasures enabled. The research is the latest in a long line of side-channel attacks that target Dynamic Voltage and Frequency Scaling (DVFS), a power-saving feature in modern chipsets. Chips from Intel and AMD have also been found vulnerable in the past.
Infosec industry
New tool—NixImports: Nextron Systems security researcher Dr4k0nia has open-sourced a new tool named NixImports, a proof-of-concept .NET malware loader that uses API-Hashing and dynamic invoking to evade static analysis.




