Risky Biz News: US says RT moved into cyber and intelligence-gathering territory
In other news: Apple files to dismiss NSO lawsuit; Australia sends cyber mission to Fiji; new exploitation wave hits Ivanti devices.

You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

The US government says that RT (formerly known as Russia Today) has morphed from a news organization into a fully active intelligence asset for the Russian government.
The US State Department says that at the start of 2023, the Russian government embedded a Russian intelligence unit with cyber capabilities inside RT.
State officials did not explain the role of this unit but say that since then, RT has engaged in "information operations, covert influence, and military procurement" across Europe, Africa, and North and South America.
The primary target of these operations has been the country of Moldova, where RT and its satellite TV stations have tried to interfere in the country's local 2023 elections and in the upcoming presidential election this October.
According to US officials, RT and its employees are directly involved in planning protests this fall planned to turn violent if Kremlin-preferred candidates do not win the presidency.
Moldova's pro-EU government knew Russian state-controlled media was going to be a problem and has already banned the broadcasting of Russian news programs on radio and television in June 2022 and banned RT and other Russian news websites in October 2023.
Similarly, US officials say RT employees are also involved in Red, a German streaming platform that has organized pro-Palestine protests across Germany.
RT is also behind African Stream, an African news site focused on attacking the West and African countries that have good relations with the EU and the US.
RT's involvement in disinformation and influence operations is not new, and the US sanctioned and indicted the news org and some of its execs last week for running a network of fake news sites and paying social media influencers to publish Kremlin propaganda. [see our previous piece for extended coverage on that topic]
What's new in the State Department is that RT is also involved in raising funds and military equipment for the Russian Army for its war in Ukraine. The State Department says this is done through an online crowdfunding platform managed by RT Deputy Editor-in-Chief and Head of International Broadcasting for Sputnik Anton Anisimov.
The State Department says it imposed its own set of sanctions on RT (three entities and two employees) not because they're publishing fake news and disinformation but because they're now an aggressive intelligence asset involved in destabilizing other countries.
"We are not taking action against these entities and individuals for the content of their reporting, or even the disinformation they create and spread publicly. We are taking action against them for their covert influence activities. Covert influence activities are not journalism."
Russia and RT's reaction to all the recent US sanctions has been unabashed scoff and ridicule, not even bothering to deny any of the allegations.
According to the BBC, RT editor-in-chief Margarita Simonyan thanked the US for allowing its staff to study in the US using US funding.
She was even more brazen when responding to the Washington Post last week when she said: "what do you think — that I get orders from the CIA? Where else would I get my orders from if I head a Russian state media outlet funded by the state? [...] All the employees of RT and the editor in chief only obey the orders of the Kremlin! All other orders are toilet paper!"
The State Department says it plans to engage governments across the globe via diplomatic channels and share information on how Russia uses RT for covert intelligence operations and "encourage them" to take action.
The only mystery left is what exactly is RT's new "cyber" capability that the State Department mentioned in its press release. Our two cents is that it's some sort of unit tasked with hack-and-leak operations, which Russia has used in the past.
Breaches, hacks, and security incidents
23andMe settlement: 23andMe has agreed to pay $30 million to settle a class-action lawsuit over a data breach at the end of last year. The settlement also mandates the company to subject itself to security audits for the next three years, roll out mandatory 2FA for all users, and roll out protections against credential-stuffing attacks. Affected users can try to claim up to $10,000 if the breach at 23andMe led to financial fraud or paying for cybersecurity services. The DNA-testing company was hacked last December when hackers stole and released the personal data of 6.9 million users. [Additional coverage in PCMag]
CDU hack update: Spiegel reports that the CDU can't recover its member lists after being hacked by Russian hackers this June.
TfL in-person password resets: London's public transportation agency says that all its staff will have to go through an in-person appointment to regain access to official apps in the aftermath of a recent security breach. The agency has asked more than 30,000 employees to make appointments to verify their identity and reset passwords for official apps. TfL suffered a security breach on September 2 and some services are still down two weeks after the attack. Authorities arrested a 17-year-old for the hack last week.
Kawasaki ransomware incident: The RansomHub ransomware group has taken credit for an attack on Kawasaki Motors' EU division. The company says the attack was not successful, and it immediately isolated servers and started the recovery process. Kawasaki expects to have 90% of affected servers restored by this week.
General tech and privacy
AI vendors to combat deepfake nudes: Six of the world's largest AI companies have agreed to voluntarily combat the use of their services for deepfake nudes and CSAM. At a White House meeting last week, Adobe, Cohere, Microsoft, Anthropic OpenAI, and Common Crawl said they would remove any nude images from training data sets. The companies also agreed to safeguard models and add systems to prevent the generation of sexual abuse imagery.
Ireland investigates Google's AI: Ireland's data protection agency has launched an investigation to see if Google's artificial intelligence model complies with privacy laws.
Google and Internet Archive partnership: The Internet Archive has announced a deal with Google to show Internet Archive versions of deleted or inaccessible search results.
Chrome PQ features: Google previously deployed a version of the post-quantum algorithm Kyber in Chrome 124. Since then, NIST has standardized the Kyber algorithm as ML-KEM, which is incompatible with the version deployed with Chrome. Google announced at the end of last week that it plans to replace Kyber with the NIST-approved ML-KEM algorithm with Chrome 131.
Programming languages ranking: The RedMonk ranking for most used programming languages for the first half of the year is out. The latest Top 3 is JavaScript, Python, and Java.
Telegram in Russia: A Dossier Center report looks at how Telegram has become a primary tool of Kremlin propaganda and a tool for sabotage operations for its special services.
AWS Cognito: Amazon has added new features to its Cognito user identity service to allow customers to verify mobile users and prevent sign-up fraud and SMS pumping schemes.
BEUC calls for EU investigation of gaming companies: A European consumer protection organization named BEUC has called on the EU to investigate gaming companies for their dark patterns related to the use of in-game (alternate) currencies.
Apple withdraws NSO lawsuit: Apple has filed paperwork to drop its lawsuit against Israeli spyware vendor NSO Group. Apple says that moving forward with the lawsuit would have forced the company to expose some of its security defenses in public court documents. The company says that its lawsuit has weakened NSO but that other new spyware vendors have popped up in its place that would have benefited from this information. Apple also doesn't feel the case would achieve anything after the Israeli government's involvement in a similar NSO lawsuit filed by WhatsApp. Apple sued NSO in 2021 after the discovery of NSO's FORCEDENTRY iOS exploit. [Additional coverage in The Record]
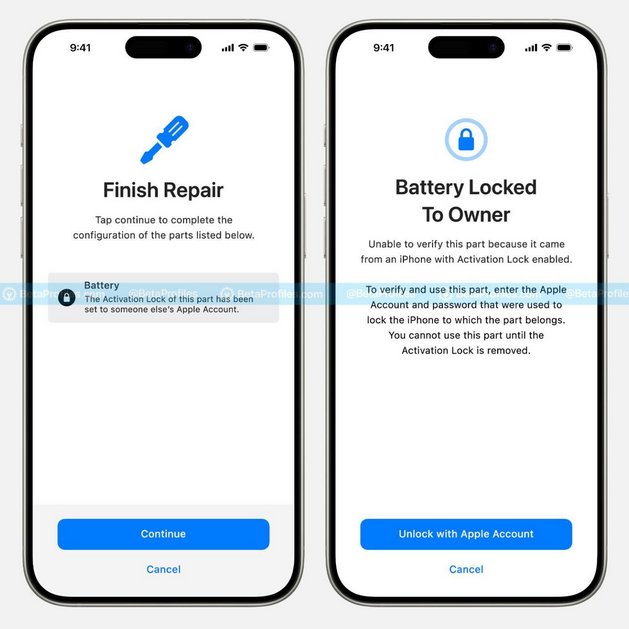
Activation Lock to iPhone parts: Apple is adding a new security feature to iOS 18, scheduled to be released later this week. The company is extending the Activation Lock feature to core iPhone hardware components like cameras, batteries, and screen displays. The new feature will allow Apple to lock iPhones that use stolen components. A negative downside is that Activation Lock will make it harder for independent hardware shops to repair devices if they do not have a strong knowledge of their supply chain.
Government, politics, and policy
Election hacking warning: CISA and the FBI say malicious threat actors will try to undermine public confidence in the security of US election infrastructure by falsely claiming that cyberattacks compromised voter registration databases.
Election threats Senate hearing: Executives from Meta, Google, Facebook, and Microsoft will testify on Wednesday this week about election threats in front of the US Senate Intelligence Committee. The hearing will be livestreamed on intelligence.senate.gov.
SNAP fraud protection extensions: A government program that reimburses victims of SNAP (formerly known as food stamps) card skimming incidents will expire at the end of September. According to an NBC News report, the program is unlikely to be extended as the US Congress is currently busy to avoid a government shutdown on October 1. Legislation meant to upgrade SNAP (Supplemental Nutrition Assistance Program) cards to use chip technology has also not passed through Congress.
Australia helps Fiji in cyberattack: The Australian government sent cyber specialists to Fiji this year to help the country investigate a Chinese hack. According to the ABC, Chinese state-backed hackers breached the secretariat of the Pacific Islands Forum and stole communications with member states. The hack took place in February, and sources described it as "extensive."
Sponsor section
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Cybercrime and threat intel
Card skimming gang dismantled: American and Romanian authorities have dismantled a card cloning gang that operated inside the US. The group installed ATM skimmers, cloned cards, and withdrew cash from victim accounts. Officials say the gang is made up of Bulgarian and Romanian nationals and has stolen more than $1 million since 2021 when it started operating in California.

Ex-Ticketmaster boss sentenced for hacking: A US court has sentenced a former Ticketmaster executive to one year of supervised release for hacking rival platform CrowdSurge. British national Stephen Mead left CrowdSurge in 2012 to join Ticketmaster and then used his former credentials to access CrowdSurge's network until 2015. According to court documents, Mead shared his credentials with other Ticketmaster employees and even accessed CrowdSurge's network while projecting onto a large screen during a meeting. Another Ticketmaster exec also pleaded guilty to the same charges and is awaiting sentencing. The DOJ also fined Ticketmaster $10 million for the hack. CrowdSurge merged with another company and eventually shut down in 2017. [Additional coverage in the BBC]
BEC losses stats: The FBI says that between October 2013 and December 2023 companies across the world lost over $55 billion to BEC scams.
The Com: Brian Krebs looks at the activity of some members of The Com, an underground community that spawned the Scattered Spider group but which is also the home of lots of individuals involved in online harassment and violence-as-a-service incidents.
XSS accounts for sale: Threat actors are selling access to accounts on XSS, a Russian-speaking hacking forum, according to CodeAIntel. The sudden desire for accounts comes after XSS went private and the forum has become a central meeting place for the major initial access broker players.
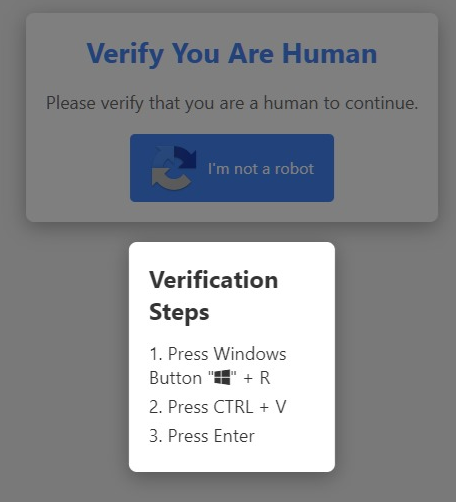
New copy-pasta attack: Security researchers have spotted a new variation of the copy-pasta attack where threat actors are using JS code to write malicious PowerShell instructions to a site visitor's Windows clipboard and are then asking them to open a Run window, press the Paste shortcut, and press Enter. That's a pretty clever variation, ngl!
Selenium Grid abuse: The cryptomining campaign abusing Selenium Grid cloud servers spotted by Wiz earlier this year is still going strong, according to Cado Security.
New npm malware: Twenty-eight malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
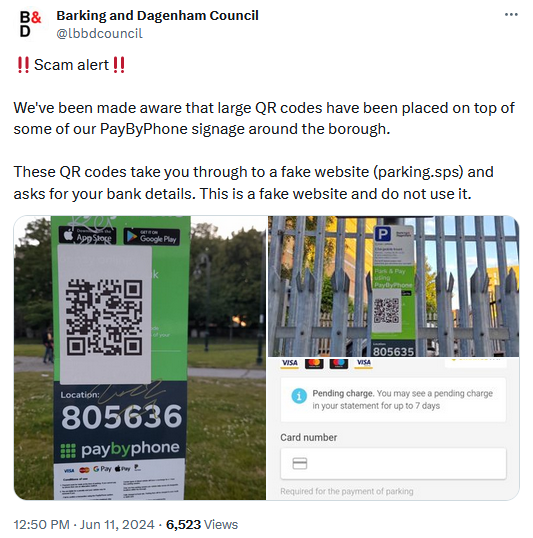
QR phishing in the UK: The Royal Automobile Club has warned UK drivers to be very vigilant when scanning QR codes to pay for parking. The organization says drivers were scammed after scanning fake QR codes glued on top of city-owned parking machines. Incidents have been reported across five UK councils since June this year. Drivers made payments via fake websites, lost money, and also shared sensitive card data with the scammers.
Malware technical reports
RansomHub ransomware: Chinese security firm Antiy has published an analysis of the RansomHub ransomware gang.
ShrinkLocker ransomware: Splunk's team looks at how the ShrinkLocker ransomware is abusing BitLocker to lock victim data.
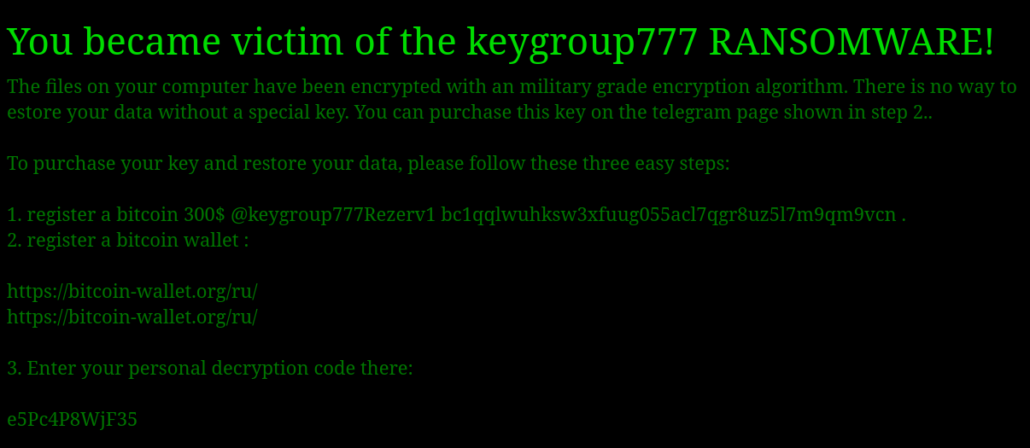
Key Group ransomware: SonicWall's security team has published an analysis of Key Group, a Russian-speaking ransomware gang that launched operations at the end of 2023.
Gomorrah Stealer: CyFirma looks at the new features added to v5.1 of the Gomorrah Stealer.
HZ RAT: Intego's Joshua Long has discovered a macOS version of the HZ RAT Windows remote access trojan.
Xworm: Security researcher Phan Kien has looked at a recent phishing campaign spreading a new version of the Xworm.
FIN7's PackXOR: Harfang Labs looks at PackXOR, a new packer used by FIN7 in some of their campaigns. More on FIN7 from Intel471.
WooCommerce skimmer: Sucuri's Ben Martin looks at a new e-skimmer found on WordPress WooCommerce stores.
Gigabud+Spynote: Zimperium says it found shared infrastructure and connections between the Spynote and Gigabud Android malware operations.
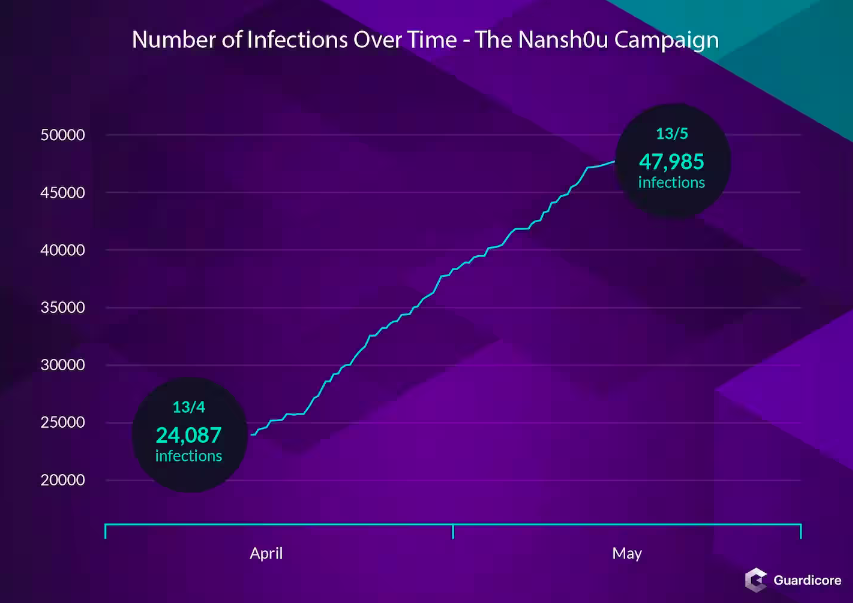
Nansh0u: Akamai's Ophir Harpaz and Daniel Goldberg have published a report on Nansh0u, a crypto-mining campaign based out of China that targets Windows MS-SQL and phpMyAdmin servers worldwide. The botnet has been active since way back in 2019, and its latest wave of attacks is believed to have infected more than 50,000 servers.
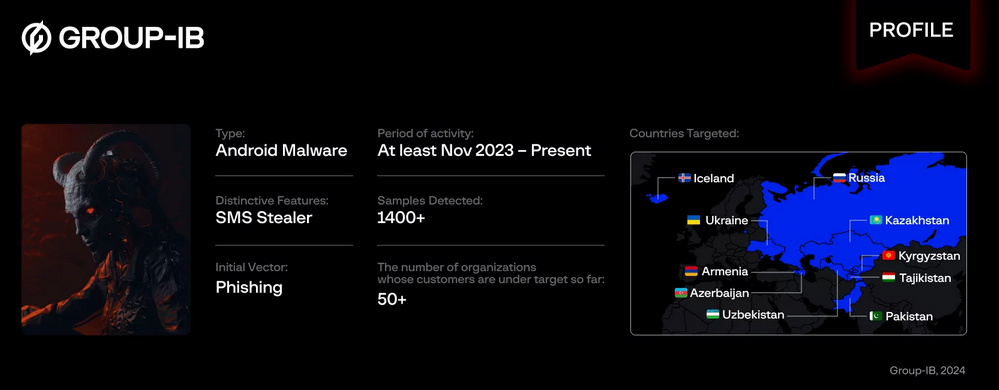
Ajina: Group-IB researchers have found a new Android banking trojan named Ajina that is targeting the customers of banks across Central Asia. The malware was first spotted in November of last year and is primarily distributed through Telegram spam, designed to trick users to side-load malicious apps. Ajina can intercept login operations for e-banking apps through specially designed phishing pages.
Sponsor Section
In this podcast, Tom Uren and Patrick Gray talk about the structure of the spyware ecosystem. It's concentrated, with lots of vendors in India, Israel, and Italy. And its a small pool of talent, with many companies being founded by just a few individuals.
APTs, cyber-espionage, and info-ops
Cuckoo Spear: Cybereason has published a report on Cuckoo Spear, an APT group also known as MirrorFace, and its new NoopDoor backdoor.
"In this report, Cybereason confirms the ties between Cuckoo Spear and APT10 Intrusion Set by tying multiple incidents together and disclosing new information about this group's new arsenal and techniques."
DOJ to charge Trump's Iranian hackers: The Justice Department intends to file criminal charges in the hacking of Donald Trump's presidential campaign. The charges are expected this week. Iranian hackers breached the Trump campaign in June and tried to disseminate some of the stolen documents last month. [Additional coverage in NBC News]
Presidential debate bot activity: Independent Russian news outlet Novaya Gazeta has a small section in its report on the recent presidential debate on how Russian social media bots tried to boost Donald Trump's performance during the Harris debate.
Paris Olympics info-ops: France's disinformation team VIGINUM has published a report looking at all the influence operations that took place during the recently concluded Paris 2024 Olympic Games.
Disrupted info-ops: Google TAG has published a list of info-ops the company disrupted in Q3 this year.
Russia's disjointed cyber warfare: A report at the start of Russia's invasion of Ukraine found that Russia's cyber units were not collaborating with each other. A new report [PDF] from NATO and British academics has found that two years later, almost nothing has changed.
"The research uncovers the profound rivalry among Russian intelligence agencies, notably FSB, SVR, and GRU, marked by their overlapping roles and internal competitions."
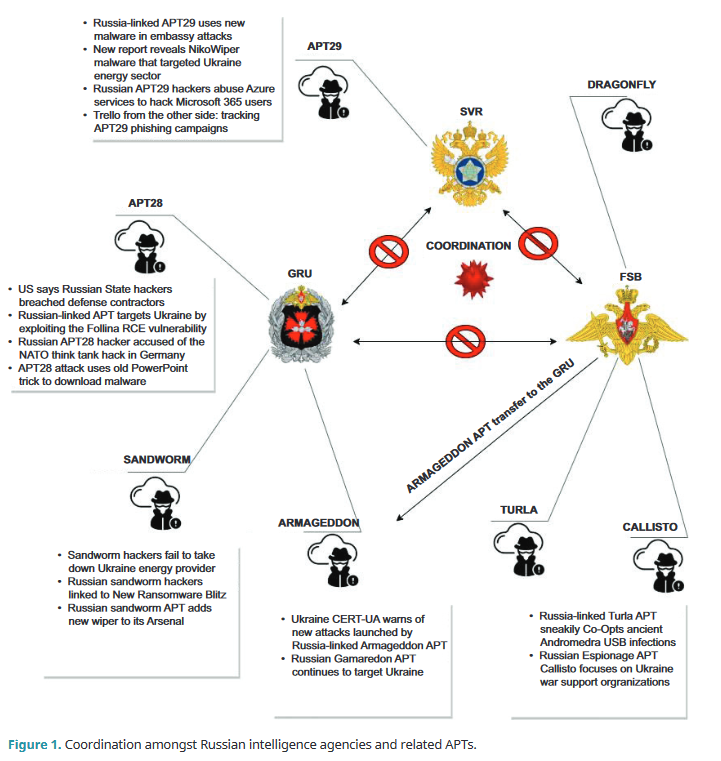
Vulnerabilities, security research, and bug bounty
New Ivanti exploitation wave: Threat actors are exploiting a recently patched vulnerability in the Ivanti Cloud Service Appliance (CSA). Tracked as CVE-2024-8190, the vulnerability is an OS command injection vulnerability the company patched last week. The vulnerability mainly impacts end-of-life versions of the Ivanti CSA. The company and CISA have asked customers to move to a newer version of the software to avoid the ongoing attacks.
Ivanti write-up: Horizon3 has published an analysis of the patch for CVE-2024-29847, an RCE in the Ivanti Endpoint Manager that got patched last week.
Spring framework vulnerability: Security researcher Gabor Legrady has discovered a critical vulnerability in the Spring Java framework. Tracked as CVE-2024-38816, the vulnerability allows attackers to access any file inside an app built using the Spring framework or is accessible to the Spring app process. Attacks can be carried out remotely via the internet using malicious HTTP requests. VMware released patches to address the issue last week.
FlowiseAI vulnerability: Tenable's Joshua Martinelle has published a write-up on CVE-2024-31621, an authentication bypass in FlowiseAI, an open-source tool for building conversational AI applications and chatbots. Exploit code for this has been available online since April.
AWS Transit Gateway exploit: AWS has fixed an issue in its Transit Gateway service that could have been used to interfere with customer peering traffic.
ScriptBlock Smuggling: BC Security and InfoGuard's Stephan Berger have published details on ScriptBlock Smuggling, a new technique that can allow threat actors to bypass AMSI using PowerShell's script-blocking feature.
macOS Calendar bugs: Mikko Kenttälä has published a write-up on a series of bugs he found two years ago that could have been used for zero-click attacks against macOS Calendar environments. Apple has fixed all vulnerabilities between October 2022 and September 2023, and Kenttälä even presented his findings at the Disobey security conference earlier this year.
Infosec industry
CrowdStrike whistleblowers: Several former CrowdStrike workers have spoken with Semafor on some of the company's past failings that led to its mid-July global IT outage. It's not a good look for CrowdStrike, with employees describing it as a place where speed was prioritized over quality.
New tool—Microsoft Incident Response Ninja Hub: Microsoft has launched a new portal to host a compilation of guides and resources that the Microsoft Incident Response team has developed on threat hunting, case studies, incident response guides, and more.
New tool—Restart Manager Artifacts: Security firm Hunt & Hackett has released Restart Manager Artifacts, a forensic tool that can capture the state of the Restart Manager database on Windows systems. The Akira ransomware gang was recently spotted abusing the Restart Manager API for its attacks.
New tool—GlobalUnProtect: Security researcher James H. has released GlobalUnProtect, a tool for decrypting and collecting GlobalProtect configuration, cookies, and HIP files from Windows client installations.
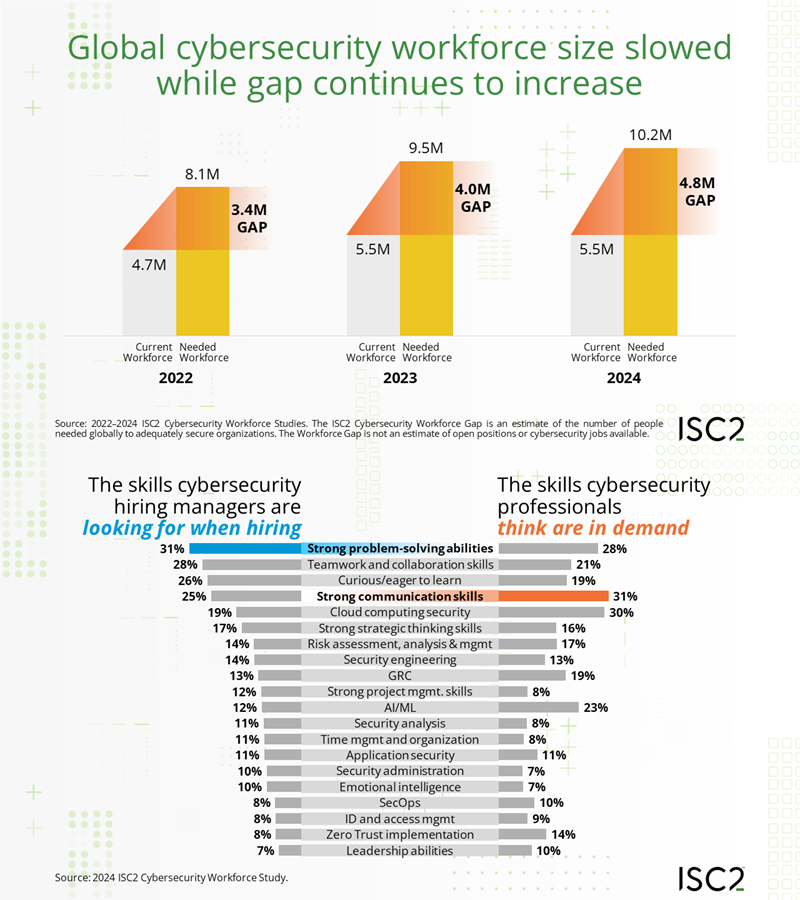
Threat/trend reports: CISA, Claroty, Dell'Oro, Google TAG, ISC2, Symantec, VulnCheck, and Wordfence have recently published reports covering infosec industry threats and trends. An interesting tidbit from the Dell'Oro report.
"The network security device market saw its first growth after six consecutive quarters of deceleration, according to telecom market research group Dell'Oro. The market saw a 6% year-over-year growth in the second quarter of the year to reach $5.9 billion. Dell'Oro says the growth came from increased demand for cloud-native security solutions and virtual firewalls. The demand for hardware-based solutions experienced its fourth consecutive quarter of decline. Dell'Oro expects the market for network security solutions to reach $40 billion by 2028."
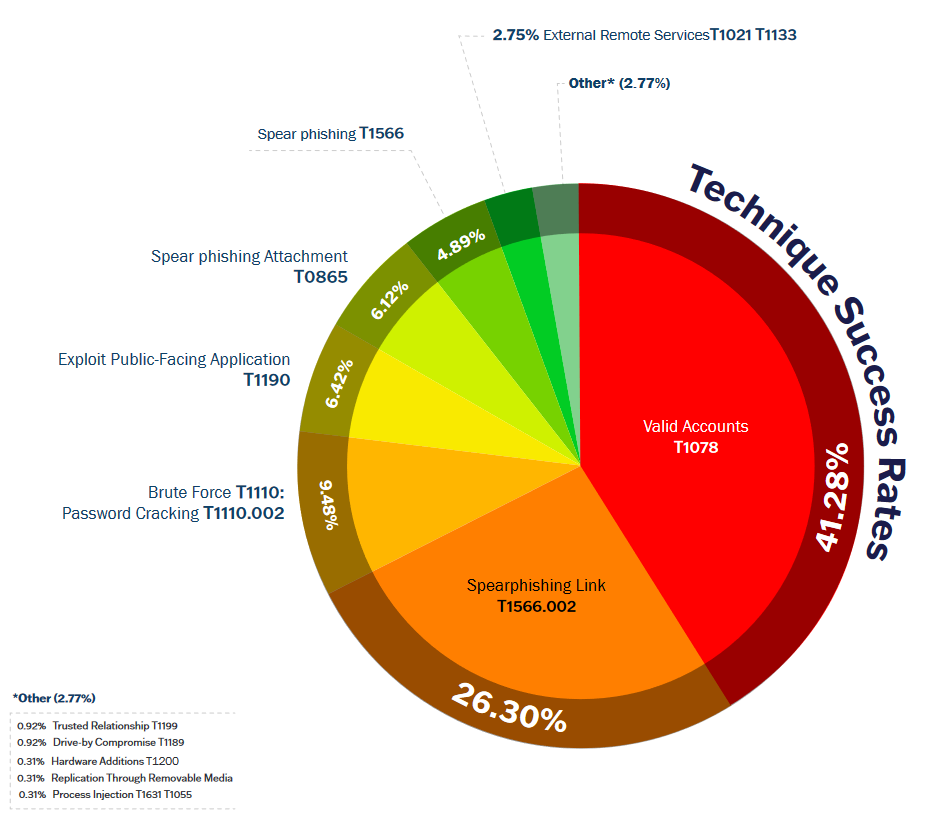
There's also this interesting summary of the CISA report.
"CISA says that the abuse of valid accounts and spear-phishing have been the primary initial access vectors into US critical sector and government organizations over the past year. CISA collected the data during 143 security audits and risk vulnerability assessments conducted over the past fiscal year. The agency has reiterated the need for the use of strong password policies and phishing-resistant MFA across critical sectors."
The graphs are from the ISC2 report.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq dissect an FBI advisory about North Korean groups targeting cryptocurrency firms with social engineering.





