Risky Biz News: US restricts sale of personal data to hostile nations
In other news: Online vigilante hacks Anycubic 3D printers; PrivateLoader botnet expected to reach two million devices; and AlphV launches v2 after law enforcement takedown.

This newsletter is brought to you by no-code automation platform Tines. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

The White House has issued an executive order to ban the sale of Americans' personal data to hostile countries, such as China, Russia, and Iran.
The executive order directs the Department of Justice to issue regulations for the data brokerage market.
The new rules will bar data brokers from selling or transferring abroad certain types of data that are considered to be too sensitive.
This will include genomic data, biometric data, personal health data, geolocation data, financial data, and certain kinds of (yet specified) personal identifiers.
In a phone call with reporters, the White House said foreign governments are increasingly viewing data as a "strategic resource." Officials said foreign governments are collecting the personal data of Americans and using it for espionage and other cyber-enabled activities.
"Bad actors can use this data to track Americans (including military service members), pry into their personal lives, and pass that data on to other data brokers and foreign intelligence services. This data can enable intrusive surveillance, scams, blackmail, and other violations of privacy."
The new executive order is meant to provide US government agencies—and especially the Justice Department—with regulatory tools to hunt down data brokers that turn a blind eye to who they're doing business for the sake of profits.
The Justice Department will be in charge of deciding to what countries the data of American citizens can't be sold to. The list is likely to include the usual suspects, such as China, Russia, North Korea, Iran, Cuba, Venezuela, and Afghanistan.
The effectiveness of the new order is already being questioned. The recent US and EU sanctions on Russia have exposed the sheer size of the sanctions evasion ecosystem. Russian, Iranian, and North Korean rockets found in Ukraine have been found to contain up to 80% Western-made electronic parts despite strict export sanctions being in place for years or decades.
Law firms advertising offshoring services are just a few Google searches away. If Chinese or Russian intelligence services didn't have copies of most Americans' personal data already (and we believe they do), it wouldn't even be that hard to set up some intermediary puppet company somewhere in the Caribbean and then buy all the data they want through that.
Those future DOJ regulations they're supposed to put together better have some serious penalties and repercussions for the "plausible deniability" data broker crowd.

Breaches, hacks, and security incidents
Cutout.Pro breach: Hackers have leaked almost 20 million user records from AI-powered visual design platform Cutout.Pro. The leaked data included email addresses, IP addresses, names, and salted MD5 password hashes.
PCG incident: Meta's technical support for hacked users has reached legendary status and is so hilariously bad these days that the Philippine Coast Guard had to ask the US Embassy in Manilla to help it regain control of its official Facebook account after it was hacked last week. [Additional coverage in the Manilla Bulletin]
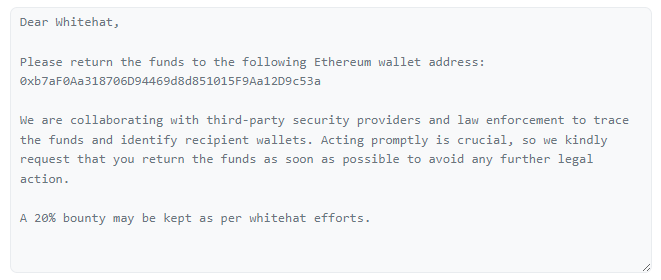
Seneca cyber-heist: A hacker has stolen $6.5 million worth of crypto-assets from cryptocurrency trading platform Seneca. The company confirmed and attributed the hack to a vulnerability in its smart contracts. Seneca recovered 80% of the stolen funds after allowing the hacker to keep 20% as a "whitehat effort"—whatever that means. The speed at which funds were recovered and how generous the "whitehat effort" reward was raises serious questions.
Cencora breach: Pharma giant Cencora disclosed a security breach in an SEC filing this week. The breach took place last week, on February 21.
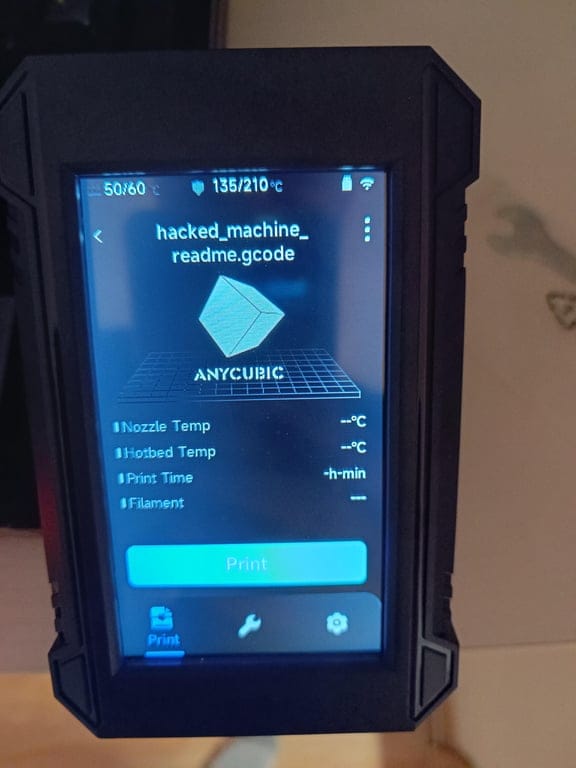
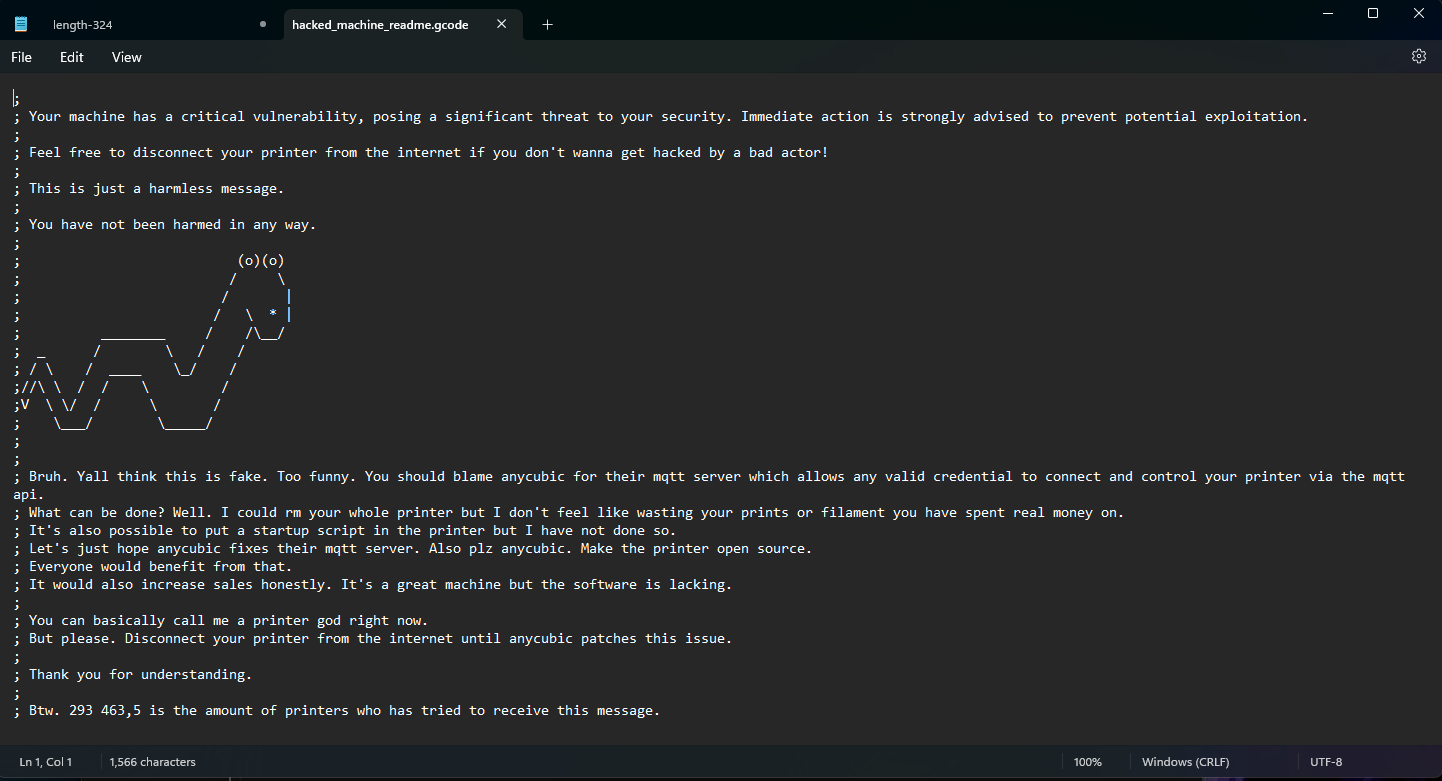
Anycubic 3D printers hacked: An online vigilante is hacking Anycubic 3D printers to warn owners that their devices are vulnerable to attacks. The mysterious hacker has left text notes on hacked devices urging owners to take printers offline until the vendor releases a patch. They claim there is a vulnerability in the printer's MQTT service. The hacker said they left the note on almost 300,000 Anycubic 3D printers. [Additional coverage in TechCrunch]
General tech and privacy
WordPress and Tumblr to sell user data to AI companies: Tumblr and WordPress.com will sell user data to AI companies. The two platforms, both owned by Automattic, have decided to automatically opt-in all their users to their new money-making scheme. Users will have to search through their settings panels to opt out of having all their (legally owned) content sent over to some AI tech bros for free.
DocuSign AI stuff: Add DocuSign to the pile of companies using your data for AI training. The difference is that DocuSign can't be bothered to disclose that it's trawling your files to train its future-s**tty AI.
Windows 11 migration: Microsoft says it will invite more Windows 10 users to migrate to Windows 11 in the coming months. The migration messages will go live in April this year. They will show up for Windows users on cloud-domain and domain-joined business devices. Windows 10 is scheduled to reach end-of-life in November 2025.
Leap year bug: Some petrol stations in New Zealand were out on February 29 for almost ten hours because of a leap year software glitch. The outage impacted Allied Petroleum, Gull, Z, and Waitomo petrol stations. [Additional coverage in NZ Herald]
Government, politics, and policy
US social media policy lawsuit: The EFF has filed an appeal in a US court asking judges to reverse a lower court order that allowed the US government to continue demanding social media usernames from foreigners entering the US—a policy that has been in place since 2019.
US to look at internet-connected vehicles: The US Commerce Department will investigate the national security risks of internet-connected cars. Government officials plan to look at smart cars and technologies sourced from China or other US adversaries. The investigation is in its early phase and could result in the government prohibiting the use of specific technologies sourced from abroad. The ban could cover the use of specific software SDKs and other navigational services. The investigation is the White House's response after China imposed restrictions on foreign cars entering its market.
Kremlin Leaks: A collection of leaked documents named the Kremlin Leaks reveal Russia's plans to rig the upcoming election for Putin, ramp up internal and external propaganda efforts, and boost its internet censorship machinery.
EU Parliament bans Amazon (sort of): The European Parliament has banned Amazon representatives and lobbyists from its premises after the company and its top executives failed to attend several official inquiries and meetings. [Additional coverage in Euractiv]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Tines co-founder and CEO Eoin Hinchy about how the unique features of AI and ML algorithms are more suited to blue teamers and defending networks rather than attackers.

Cybercrime and threat intel
Anti-DDoS ad campaign: Dutch Police have run ads on Google pages for popular DDoS search terms. The ads are meant to warn and discourage young people from using DDoS-for-hire services, which are widely considered to be a gateway for other forms of cybercrime. Dutch officials say the campaign cost the agency €35,000 and resulted in 200,000 impressions and 35,000 clicks. In total, Dutch Police says it spent more than €60,000 on anti-cybercrime Google ad campaigns since 2021.
Threat reports: Some infosec reports covering industry threats and trends came out this week from Dragos, Cado Security, Sygnia, Radware, and Group-IB.
Calendly attacks: Threat actors are adding malicious links to Calendly-based calendars to lure individuals from the cryptocurrency space to macOS malware. [Additional coverage in KrebsOnSecurity]
Predator activity: French security firm Sekoia says spyware maker Intellexa has rolled out new infrastructure after its operations were exposed as part of a leak known as the Predator Files. Sekoia says Intellexa has registered new domains, meaning the company's activity continues unabated. Some of the new domains suggest Intellexa's Predator spyware is now being used in new locations such as Botswana, Sudan, and Mongolia.
Savvy Seahorse: Security firm Infoblox has discovered a new threat actor named Savvy Seahorse that uses a novel technique to redirect users from Facebook ads to financial investment scams. Infoblox says the group operates the first CNAME-based traffic distribution system (TDS) seen in the cybercrime underground. Savvy Seahorse has been active since August 2021, and they operate a sprawling infrastructure.

LabHost PhaaS: Fortra's PhishLabs looks at LabHost, a Phishing-as-a-Service platform that the company says has been recently used to target Canadian banks.
XHelper: Indian security firm CloudSEK looks at XHelper, an Android app used by money mules to launder profits from India to China. The app is linked to a campaign that took place last year and exploited a loophole within India's banking infrastructure.
AlphV jumps on ScreenConnect: Huntress has seen the AlphV (BlackCat) ransomware gang targeting ConnectWise ScreenConnect devices with two recent vulnerabilities. AlphV joins the likes of Bl00dy and Black Basta, groups that are also targeting the same security flaws for initial access to corporate networks.
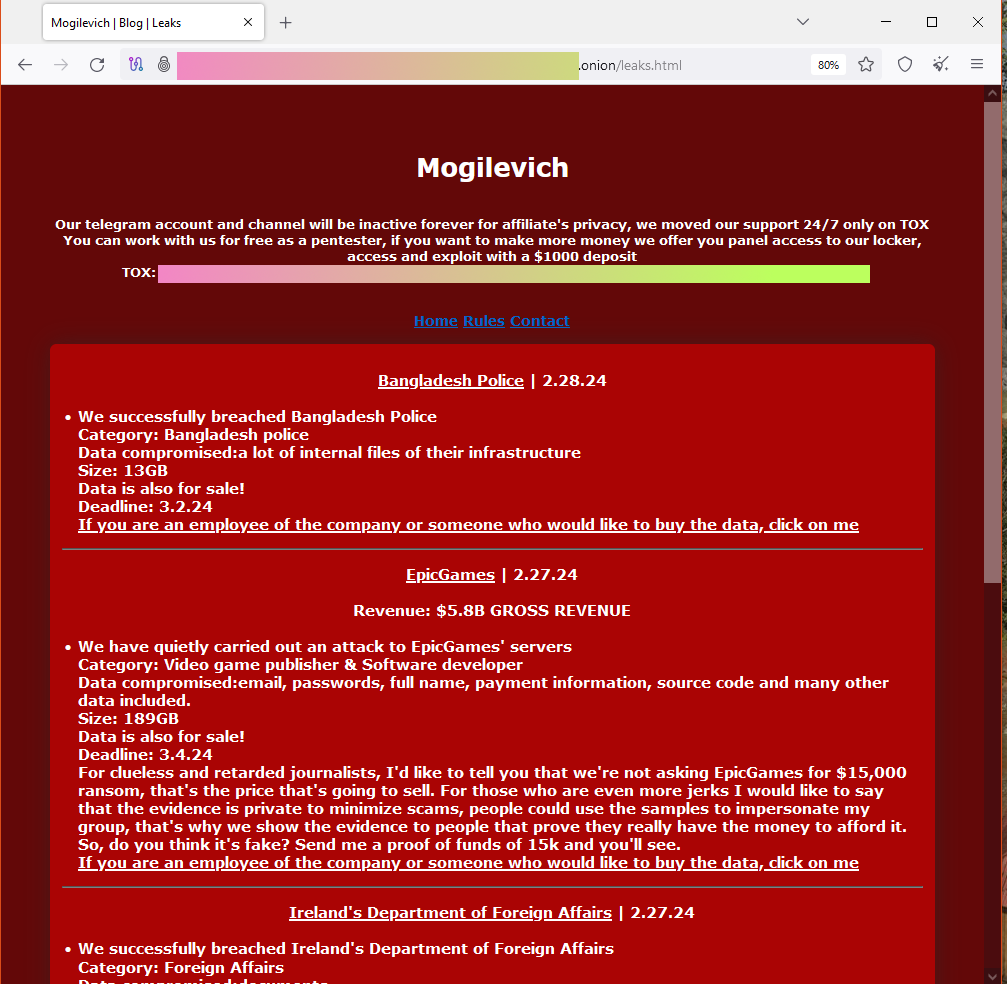
New Mogilevich ransomware gang: Epic Games says there is "zero evidence" that a ransomware gang breached its systems this month. The studio behind the popular Fortnite game denied rumors that it was hacked after a new ransomware gang named Mogilevich listed the company on its dark web leak site. Epic Games says the gang never reached out with a ransom demand, nor did it reply when Epic employees reached out instead. Mogilevich launched operations last week and, besides Epic Games, also claimed attacks on Ireland's Department of Foreign Affairs and the Bangladesh national police. Irish officials also denied getting hacked.
Malware technical reports
AlphV 2.0 (Sphynx): The AlphV cybercrime has launched a new version of its ransomware strain. Tracked as version 2.0 or the Sphynx update, the new version has been seen in the wild in attacks this month. It can encrypt files on Windows, Linux, and VMware systems. Some of AlphV's new attacks hit US healthcare entities, which the group previously promised not to attack. AlphV released the new version shortly after coming back online and resuming operations at the end of January. The group ceased operations in December and January after US law enforcement seized some of its server infrastructure and released a decrypter for past victims.
Phobos ransomware: US cybersecurity agencies have published a technical report on the Phobos ransomware, one of the lower-tier RaaS platforms.
Cactus ransomware: Bitdefender researchers analyze a coordinated attack on five companies with the Cactus ransomware.
Xehook Stealer: Spamhaus has discovered a new version of the Xehook Stealer. This new version is being distributed via SmokeLoader.
Linux Bifrost: Palo Alto Networks has discovered a Linux version of Bifrost (Bifrose), a RAT first spotted in the wild way back in 2004.
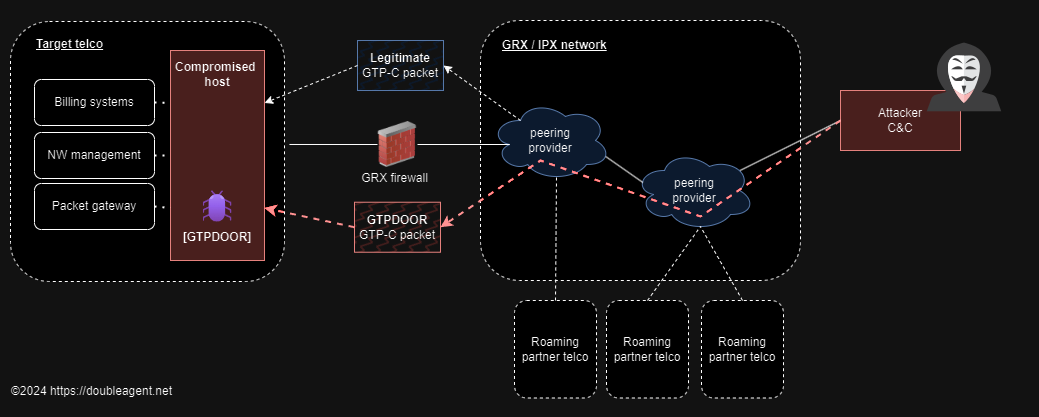
GTPDOOR: Security researcher HaxRob has discovered a new Linux backdoor that is currently used to spy on telco networks. The malware is named GTPDOOR after its use of the GPRS Tunnelling Protocol (GTP) to disguise command-and-control communications. HaxRob believes the malware may be linked to LightBasin, a cyber-espionage group with a long history of telco espionage.
PrivateLoader: Cybersecurity firm Bitsight has seen a spike in the activity of the PrivateLoader malware botnet. The company says PrivateLoader has infected more than one million devices in 2023, making it one of the largest botnets last year. The malware is allegedly infecting 5,000 devices per day and is poised to go over the two million mark this year.
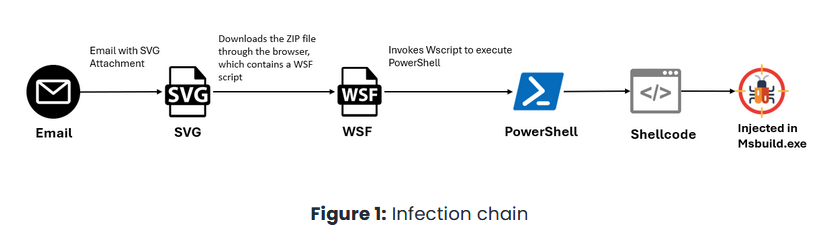
GuLoader: McAfee researchers look at a recent GuLoader campaign abusing SVG files. That's a new attack vector that I've not seen before or knew about—that SVGs can trigger a file download.
Sponsor Section
In this demo, Tines CEO and co-founder Eoin Hinchy demonstrates the Tines no-code automation platform to RiskyBiz host Patrick Gray.
APTs, cyber-espionage, and info-ops
SPIKEDWINE: Zscaler has discovered a new APT group named SPIKEDWINE that has targeted European and Indian diplomats. The threat actor is behind a phishing campaign that attempted to infect targets with the WINELOADER backdoor. Zscaler described the threat actor as a state-sponsored group interested in geopolitical relations between India and European nations.
UNC1549: An Iranian APT group has conducted espionage operations targeting the aerospace, aviation, and defense industries in Middle East countries. Mandiant tracks the group as UNC1549. Past operations have relied on malware such as MINIBIKE and MINIBUS, and the group is currently hosting 125 command and control servers on Azure infrastructure. Mandiant says UNC1549 activity overlaps with what was previously tracked as TortoiseShell, an APT linked to the Iranian IRGC military and intelligence service.
Mysterious Werewolf: Russian security firm BI.ZONE says the Mysterious Werewolf APT group is launching attacks against Russia's defense sector. The group's operations involve the use the Mythic framework's Athena agent and a new backdoor named RingSpy.
Lazarus on PyPI: Japan's CERT team looks at four malicious Python libraries uploaded on the official PyPI portal that researchers believe are operated by North Korean hacking group Lazarus.
Lazarus zero-day: North Korean hackers have secretly exploited a Windows zero-day for months before Microsoft released a fix in February 2024. The attacks were discovered by security firm Avast, which says it initially reported the issue to Microsoft in August of last year. The company linked the zero-day (CVE-2024-21338) to Lazarus Group operations.
Russian disinformation in Africa: The US State Department says that Russian intelligence services are behind a health-related disinformation campaign in Africa. The campaign boosts conspiracies about the work of Western pharmaceutical companies and healthcare philanthropic efforts across Africa. US officials say the campaign originates from a news agency named the African Initiative, managed by a Russian national named Artem Sergeyevich Kureyev. The State Department says some members of the African Initiative " were recruited from the disintegrating enterprises of the late Yevgeniy Prigozhin."
More Russian disinfo: Recorded Future has published a report on an increased Russia mis/disino campaign designed to demoralize Western audiences with "war fatigue" narratives and that Russia is bound to eventually defeat Russia. This campaign is what Ukrainian intelligence appears to call Maidan-3.
Vulnerabilities, security research, and bug bounty
Invanti PulseSecure attacks: Software maker Ivanti has released a new version of its firmware integrity-checking tool. The new version was released after cybersecurity agencies from the Five Eyes countries discovered that threat actors found a way to hide their presence on hacked SecureConnect VPNs. The new technique bypasses integrity checks and also allows threat actors to survive factory resets. Attacks on Invanti SecureConnect VPNs started in December of last year and have involved four different zero-days. In its own update of these attacks, Google's Mandiant division says that at least three suspected Chinese APT groups are currently involved in the attacks (UNC5221, UNC5325, and UNC3886).
MeshCentral vulnerability: Praetorian researchers have discovered a vulnerability (CVE-2024-26135) in MeshCentral, a web-based remote monitoring and endpoint management solution. Researchers described the issue as a cross-site websocket hijacking (CSWSH) vulnerability.
Cisco security updates: Cisco has released or updated five security advisories for various products.
Zyxel vulnerability: Security firm Eclypsium has discovered multiple vulnerabilities in Zyxel's USG line of firewalls and VPN appliances. Unauthenticated attackers can exploit the issues to take over unpatched devices. The vulnerabilities do not impact the latest Zyxel firmware version, so updating devices mitigates any attacks.
EKEN vulnerabilities: Reporters with ConsumerReports have found several vulnerabilities in EKEN smart doorbells.
Facebook account hijack: Bug hunter Samip Aryal has published details about a now-patched vulnerability in Facebook's password reset vulnerability that could have been exploited to hijack accounts.
Malicious Hugging Face ML models: JFrog researchers say they found more than 100 instances of malicious ML models hosted on the Hugging Face platform.
Silver SAML: Security firm Semperis has discovered a new attack named Silver SAML, a variation of the Golden SAML attack repurposed for cloud-based services. Semperis says the technique has not been exploited in the wild so far.
ESC14 abuse: SpecterOps describes how threat actors can abuse
certificate mapping for the Active Directory Certificate Services (ADCS) service, a technique known as ESC14 abuse.
GitHub malicious repos: DevSecOps platform Apiiro has identified a coordinated campaign that has uploaded more than 100,000 malicious repositories on GitHub. The packages use typosquatted names that mimic the names of more popular repositories and attempt to infect users with malware. The malicious packages are advertised via forums and Discord, and their final payload is a basic infostealer named BlackCap-Grabber. Apiiro says the wave of malicious GitHub repos is part of a campaign that started in November of 2023.
Infosec industry
New tool—Cirrus: Security firm Sygnia has open-sourced a tool named Cirrus to help IR teams with collection from Google Cloud environments.
New tool—BobTheSmuggler: Security researcher Harpreet Singh has open-sourced a tool named BobtheSmuggler. The tool can be used for crafting HTML smuggling attack payloads for red-team exercises.
New tool—MultCheck: MultSec has released MultCheck, a tool to test the detection of a file by multiple AV engines.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq apologize for repeating a quote that is purported to be Russian cyber doctrine but is not. They also wonder why this phenomenon has happened before with the so-called Gerasimov doctrine.





