Risky Biz News: US removes Sandvine from sanctions list after pinky promise
In other news: Sophos spied on two Chinese exploit development centers; Vodafone fined for insecure wiretapping system; supply chain attack targets crypto-wallet users.

You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
[This newsletter's podcast embed widget]
The US Department of Commerce has removed surveillance gear maker Sandvine from its list of sanctioned entities after the company put out a public statement and promised to exit autocratic countries.
The Canadian company said it had stopped operating in 32 countries already and was planning to exit another 24 by April next year.
Sandvine also changed its CEO, created a Human Rights Subcommittee, and promised to dedicate 1% of its profits to protect internet freedom and digital rights.
The company's sudden exit from the dark side came almost eight months after it was sanctioned by the US government in February.
The US Commerce Department added Sandvine to its "Entity List" for providing internet mass surveillance technology to oppressive regimes.
While Commerce officials didn't name the customer, the company is known for providing internet surveillance and censorship equipment to Egypt, Belarus, Eritrea, the UAE, Uzbekistan, and many other lovely places.
Sandvine's removal from the sanctions list may hint at more similar actions. Israeli spyware vendor NSO Group has been heavily lobbying to get itself off the list for more than a year.
The company is the first surveillance vendor to be removed from the list.
The "pardon" didn't land well with spyware investigators and some government officials. This week, Sen. Ron Wyden asked the Commerce Department to strengthen its export controls to block surveillance software from more countries with known human rights abuses—from the 23 today.
"I can see there are Sandvine installations operating in a number of very problematic countries and probably will be for a while," said Citizen Lab Director Ron Deibert.
Breaches, hacks, and security incidents
Lottie Player supply-chain attack: A threat actor has compromised the Lottie open-source video player and added malicious code to target cryptocurrency users. The incident took place this week when websites using the Lottie player suddenly started prompting users to connect their crypto wallets. Users who connected their wallets reported losing funds. DevSecOps company Sonatype linked the popups to new Lottie player updates released on Wednesday after eight months of inactivity. It's unclear how many funds were stolen, but one user alone reported losing over $700,000 worth of Bitcoin.
DHL tracking system hack: A cyberattack has disrupted a package tracking tool used by German logistics giant DHL. DHL has confirmed the incident and says it's working with the tracking tool's developer to restore systems. According to a report from Better Retailing, the tool was developed by British company Microlise.
Interbank security breach: Peru's fourth-largest bank has confirmed that a threat actor managed to steal data on some of its customers from a third-party company. The admission comes after Interbank suffered a technical glitch earlier this week and after its customer data was flaunted on hacking forums shortly after. The bank is believed to have between 2 and 3 million customers. [Additional coverage in Infobae America]
Colorado election system password leaks: The Colorado Department of State has accidentally posted a document online that contained the partial passwords for the state's voting machines. Officials have since removed the document and changed passwords. They also notified CISA and said the incident won't affect next week's election. [Additional coverage in StateScoop]
PRC's Canada hacks: Canada's cybersecurity agency says that Chinese hacking groups have breached at least 20 government networks over the past four years. Officials described the threat of Chinese hacking as "second to none," targeting multiple fronts, such as intelligence collection, IP theft, and malign influence operations. The agency also warned that China and other foreign states are pre-positioning for future disruptive or destructive cyber operations against both Canada and its allies. The statement echoes the messages that have been coming out of the US over the past year.
General tech and privacy
Vodafone fined for insecure wiretapping system: The Dutch government has fined Vodafone €2,25 million ($2.45 million) for failing to secure its phone wiretapping system. The company failed to screen staff, failed to have staff sign confidentiality agreements, and failed to implement logical and physical security systems. The fine was imposed for an investigation that started in 2021 and is not related to China's hack of US telco wiretapping systems.
Entra enforces MFA: Microsoft has announced that all new Entra accounts must enable an MFA solution the first time a user logs into their profile. The new rule removes a two-week grace period when new accounts were allowed to log in using just a password.
Twitter's right-wing lean: A WaPo investigation has found that tweets from Republicans go viral on a regular basis since Musk acquired the company, while content from Democrats has plummeted in visibility by an order of billions of views. A similar NBC News report found the same thing—that Twitter now seems to favor and revolve around a small number of right-wing disinfo accounts while legitimate sources of information can barely get any views. WaPo and NBC may not have the balls to say it, but Twitter is just mostly troll farm accounts these days. It only takes a few minutes of (doom) scrolling to figure it out. This explains the sudden skew in what goes viral and why there's at least one Hitler or fascist-related topic trending on the platform almost daily. The site is easily manipulated because it lost heaps of users who went on to greener and non-toxic platforms. Twitter is in such a low place that even Truth Social is now worth more.
Right-wing database: Politico has discovered a company named L2 Data claiming to sell a database with the names of Americans who support right-wing militias, QAnon conspiracy theories, and the January 6 insurrection. Experts believe the database represents a national security risk as it could help local or foreign adversaries recruit extremists for violent and other types of attacks.
Meta's ad policing failures: While Meta is blocking phrases like "Hitler is bad" on Threads, the company is raking in millions from deceptive political ads. [Additional coverage in ProPublica]
Government, politics, and policy
US warns of Iran election meddling: US officials expect Iranian threat actor groups to contact Americans directly on election day to sow disinformation, divide society, and even incite violent unrest. [Additional coverage in NBC]
FBI conducted 30+ ransomware disruptions: The FBI has disrupted ransomware infrastructure more than 30 times this year, an official revealed this week. Deputy Assistant Director of the FBI's cyber division Cynthia Kaiser says some of the disruptions caused some gangs to stop targeting US infrastructure. Kaiser says that in many cases, detaining suspects is not possible because they operate out of safe harbor countries like Russia. [Additional coverage in CyberScoop]
Tajikistan bans violent video games: The government of Tajikistan has banned violent video games, such as GTA and CounterStrike. Local police are now warning internet cafes and public gaming halls to remove such games.
Predatorgate cover-up: Greek news site Inside Story claims to have identified crucial evidence that Greek prosecutors ignored evidence and crucial witnesses in the country's investigation of the current government's use of the Predator spyware.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about a new attempt to measure cyber power, the International Institute for Strategic Studies Cyber Power Matrix.
Arrests, cybercrime, and threat intel
Disney employee hacked menu system: US authorities have charged a fired Disney employee for allegedly hacking the company's menu creation software. Michael Scheuer is accused of removing information if foods contained peanuts from foods served at Walt Disney World's restaurants. He also allegedly added profanity to some menus and even changed all fonts to Wingdings. The menu defacements were spotted days after the menus were printed but before they were shipped to restaurants. [Additional coverage in CourtWatch]
Scam compound traffickers plead guilty: Two Chinese nationals pleaded guilty to human trafficking Hong Kong citizens for cyber scam compounds. Officials say the duo sent three individuals to a scam compound in Thailand and two to KK Park, an infamous Myanmar scam center. The two were detained after victims paid ransoms or were freed by police. [Additional coverage in SCMP]
Scam compound traffickers sent to trial: Ugandan prosecutors have charged three suspects with aggravated human trafficking for sending 25 locals into Myanmar cyber scam compounds. Officials say the three are part of a larger network that recruits Ugandans for foreign employment under false pretenses. Victims are sent to Myanmar, where they are forced to work in call centers specialized in internet scams. Two of the suspects are elected councilors in Ugandan local governments. [Additional coverage in The Kampala Report]
Chrome extension turns malicious: A popular Google Chrome extension with more than 100,000 installs has now turned malicious. The Hide YouTube Shorts extension is performing affiliate fraud and collecting the browsing history of all its users. Security researchers say the extension appears to have turned malicious after it was transferred to a new developer.
SYS01 malvertising: Bitdefender has spotted a malvertising campaign targeting owners of Meta Business Pages with the SYS01 infostealer.
UA tax-themed phishing: CERT-UA has published details about a tax-themed phishing campaign targeting accountants of Ukrainian enterprises.
The good ol' copyright infringement tactic: Cisco Talos says it is seeing a new wave of fake copyright infringement emails luring people to malware. Never gets old!
Malicious PyPI packages: Checkmarx has discovered yet another campaign using malicious PyPI packages to target the cryptocurrency space.
Author typosquatting: Besides domain name and package typosquatting, we now have author typosquatting—where threat actors register profiles similar to well-known and trusted developers.
Lunar Spider ops: EclecticIQ has linked a malvertising campaign deploying the Latrodectus downloader to a known Russian cybercrime group tracked as Lunar Spider. The group is suspected of having developed both IcedID and Latrodectus.
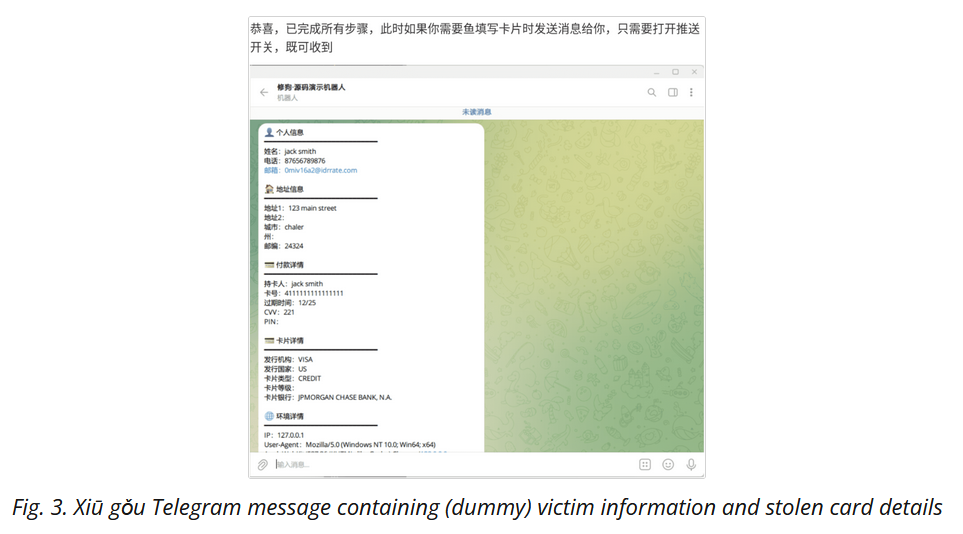
Xiū Gǒu (Doggo) phishing kit: A new phishing kit is seeing widespread adoption and has already been spotted on over 2,000 phishing pages. According to Netcraft, the new Xiū Gǒu (Doggo) phishing kit appears to be the work of a Chinese-speaking developer. So far, the kit has been used for phishing credentials for government portals, postal services, and online banking portals. Xiū Gǒu collects all stolen data on Telegram channels and doesn't seem to support MFA bypassing.
EMERALDWHALE Git scan campaign: A threat actor has stolen more than 15,000 cloud service credentials by scanning the internet for misconfigured Git repositories that leaked their configuration files. The scanning operation was discovered by cloud security firm Sysdig, which found the stolen credentials on one of the attacker's servers. Sysdig says the scanning operation between August and September, and also targeted websites that exposed Laravel environment files. The company named this threat actor EMERALDWHALE.
Phish 'n' Ships: A Chinese-speaking group has stolen tens of millions of dollars over the past five years using a network of fake online stores. According to Human Security, the Phish 'n' Ships group has hacked more than 1,000 websites to promote and legitimize their fake stores. Victims were lured to the sites, made payments for non-existent goods, and also had their financial data collected by the group.
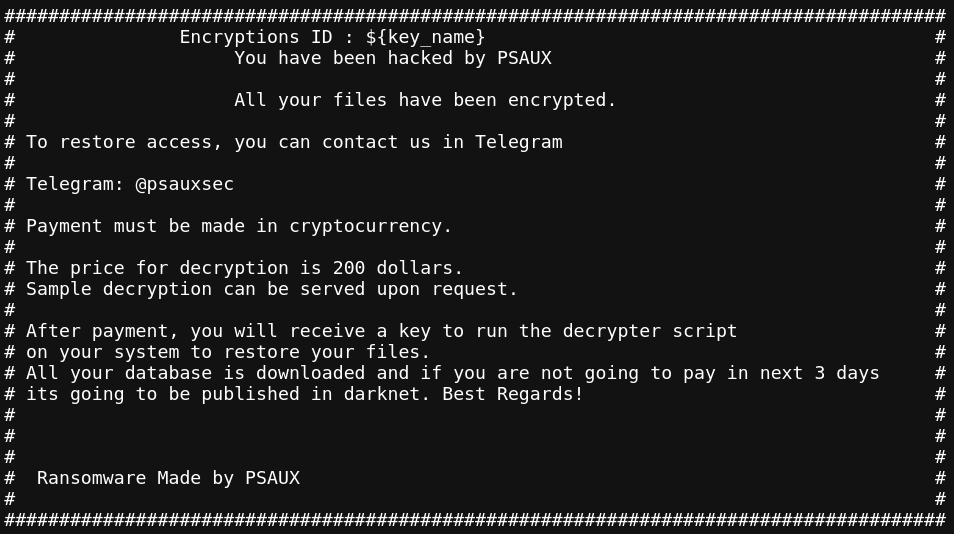
PSAUX ransomware attacks: A threat actor is exploiting a vulnerability in the CyberPanel web hosting system to gain root access to servers and deploy the PSAUX ransomware. The attacks began two days after a security researcher published details about an unpatched remote code execution vulnerability in the software. While CyberPanel has since released a patch, attacks are still ongoing. Security firm LeakIX has also published a free decrypter to help companies recover locked data.
Malware technical reports
BugSleep: Cisco Talos has published a deep dive into the C2 protocol used by BugSleep, a new implant used by the MuddyWater APT.
Titan crypto-miner: Trend Micro looks at a pretty novel crypto-mining operation that targets Atlassian Confluence servers with a miner for the Titan blockchain.
RedLine: Security researcher Anurag has published an analysis of the RedLine infostealer, whose operation was disrupted earlier this week by law enforcement.
PySilon: AhnLab has published a report on PySilon, an open-source Python-based RAT that relies on Discord to collect stolen data.
CraxsRAT: FACCT looks at CraxsRAT, an Android RAT used in attacks against Russian government organizations this year.
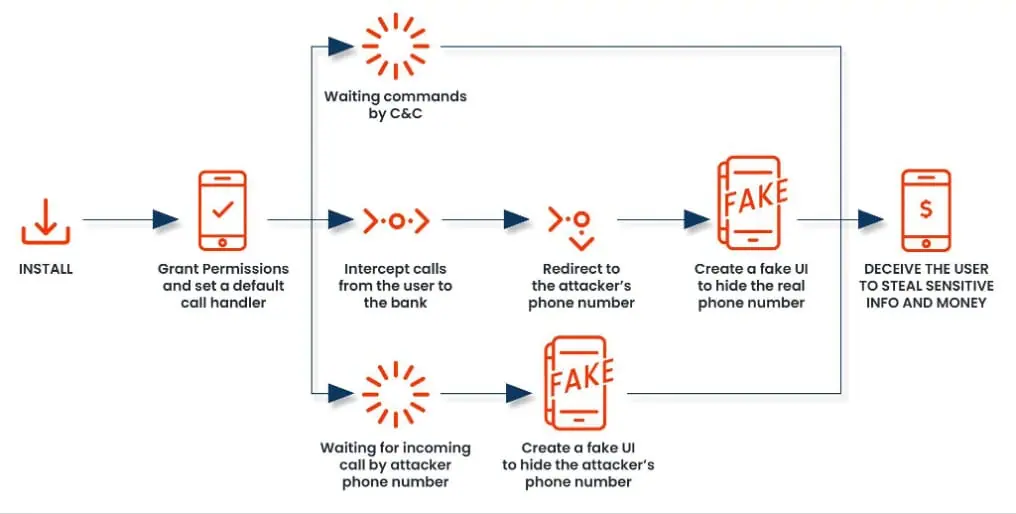
FakeCall: Mobile security firm Zimperium has published a report on the evolution of the FakeCall Android malware and its latest features.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
APTs, cyber-espionage, and info-ops
US efforts to hack Venezuela: A WIRED article looks at the Trump administration's efforts to push out the Maduro regime from Venezuela, including its efforts on the cyber front.
"One of the task force's first goals: an expansion of efforts to hack Venezuelan government networks and other infrastructure targets for intelligence-gathering purposes. Very quickly, the task force ran into roadblocks. It had to fight—sometimes unsuccessfully—for access to important resources, like elite CIA and NSA hacking teams. Those teams usually worked on higher-profile targets, according to a former agency official."
DPRK's love for macOS: Trellix researchers look at how North Koreans increasingly adopted macOS malware as its popularity started growing among the enterprise crowd.
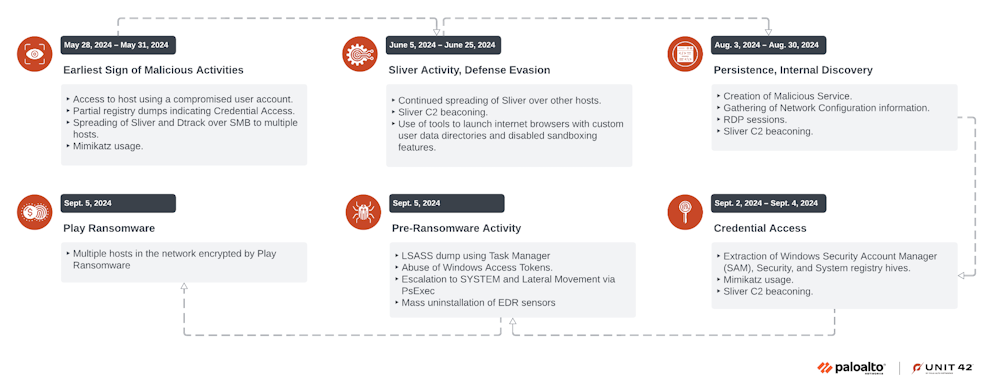
DPRK APT deploys ransomware: A North Korean cyber-espionage group known as Andariel (Jumpy Pisces) has been seen collaborating with a ransomware gang. Security firm Palo Alto Networks says Andariel is now deploying the Play ransomware as part of its attacks. The first known Andariel and Play attacks date back to the start of September. This marks the second time the group deployed ransomware in attacks. It previously developed and used its own ransomware strain named Maui. The group appears to have switched to Play after the US charged some of its members in July for the Maui attacks.
Hoopoe Platform: Alethea looks at the third incarnation of the Hoopoe Iranian influence operation.
Emennet Pasargad rebrands: The FBI says that an Iranian threat actor known as Cotton Sandstorm (Marnanbridge, Haywire Kitten) has rebranded the name of its front company in what appears to be an effort to hide from US authorities. The group now operates from behind a company named Aria Sepehr Ayandehsazan (ASA) [PDF]. It previously operated under a company named Emennet Pasargad [PDF]. The company was sanctioned by the US Treasury for interfering in the US 2020 presidential election. The FBI says that since rebranding, Cotton Sandstorm has run operations targeting the Olympics and the Israeli-Palestinian conflict with "a myriad of cover personas."
Midnight Blizzard new RDP config technique: Microsoft says that a notorious Russian cyber-espionage group is using a clever new technique to compromise victims and deploy malware on their systems. The technique involves sending malicious RDP configuration files to victims via email. If executed, the files connect a victim's PC to a remote RDP server. The connection allows the Russian group to steal data and deploy malware on the compromised device. Microsoft has attributed the operation to Midnight Blizzard, a cyber unit inside Russia's SVR Foreign Intelligence Service. The group has used the new technique since October 22 and has targeted individuals in government, academia, defense, and NGOs across the US and Europe. This is the same campaign also spotted by AWS and CERT-UA.
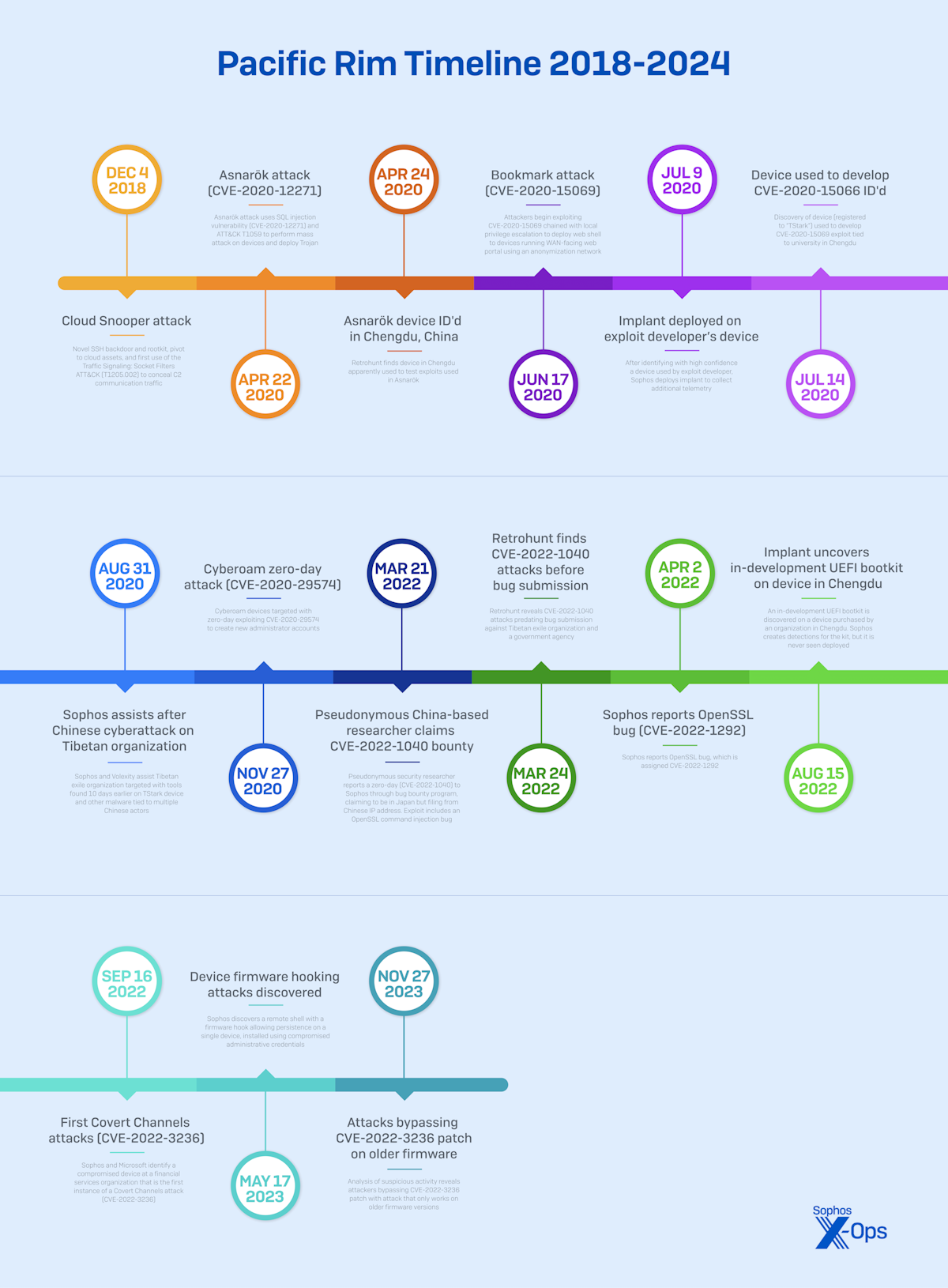
The Chengdu Sophos exploit farm: A university and a private company from the Chinese city of Chengdu have spent years developing exploits for Sophos firewalls that were later used by multiple Chinese state-sponsored APT groups. UK security firm Sophos has linked the two exploit development centers to the University of Electronic Science and Technology of China and the Sichuan Silence Information Technology firm. The security firm says it discovered the exploit development centers after it developed its own surveillance implant to spy and capture exploits as they were being tested on its devices at the two locations. Sophos says exploits developed by these two centers have been used over the past half-decade by groups such as Volt Typhoon, APT31, and APT41 (Winnti). In some cases, Sophos says the exploit centers reported the vulnerabilities via its bug bounty program days after it was used in the wild.
Vulnerabilities, security research, and bug bounty
SharePoint exploitation: Rapid7 has published more details on the attacks targeting Microsoft SharePoint servers that are abusing a vulnerability tracked as CVE-2024-38094. The bug was patched in July but entered active exploitation in mid-October. Rapid7 says the attack went undetected because the attacker installed a version of Chinese antivirus software Huorong that caused the victim's antivirus to crash.
Xlight exposure: More than 3,500 Xlight FTP servers are currently exposed on the internet and may be vulnerable to a recently disclosed pre-auth remote code execution bug. Patches are available.
Splunk security updates: Cisco has patched two security flaws in its Splunk SIEM product.
qBittorrent vulnerability: Sharp Security has published details about a 14-year-old RCE vulnerability in the qBittorrent client.
"In qBittorrent, the DownloadManager class has ignored every SSL certificate validation error that has ever happened, on every platform, for 14 years and 6 months since April 6 2010 with commit 9824d86. The default behaviour changed to verifying on October 12 2024 with commit 3d9e971. The first patched release is version 5.0.1, released 2 days ago."
Ollama vulnerabilities: Oligo researchers have found six new security flaws in the Ollama open-source LLM framework.
Portainer vulnerabilities: CyberArk researchers have found two vulnerabilities in Portainer, an open-source tool for managing Kubernetes and Docker environments.
Keycloak security audit: HN Security has published the findings of a security audit of the Keycloak authentication system.
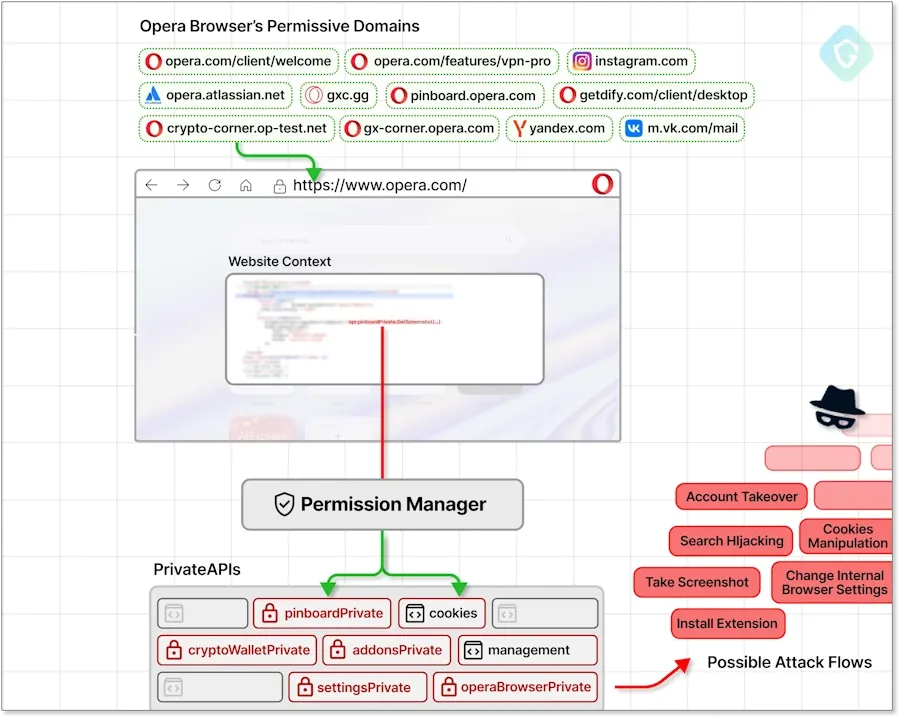
Opera Private API access: Guardio Security has found a vulnerability in the Opera web browser that can allow extensions access to the browser's Private APIs. These are APIs used for the browser's native features, like its crypto-wallet, VPN, Pinboard, and other features. The exploit code is benign in other Chromium browsers. This allows threat actors to create and host malicious extensions on the official Chrome Web Store designed to attack Opera users only. Opera deployed fixes at the end of September, but users remain vulnerable to some narrow attack scenarios.
Infosec industry
New tool—SAIF Risk Assessment: Google has released an interactive tool named the SAIF Risk Assessment.
New tool—Graviola: Cryptographer Joe Birr-Pixton has released Graviola, a collection of high-quality, fast, and easy cryptography for Rust.
New tool—Whispr: Cloud engineer N3N has released Whispr, a CLI tool to inject secrets from a secret vault (ex, AWS Secrets Manager, Azure Key Vault, etc.) into an app's local environment.
New tool—LOLRMM: A team of security researchers has launched a new project named LOLRMM. The project tracks a list of Remote Monitoring and Management (RMM) apps that could be abused by threat actors to bypass security solutions on compromised environments. The project is similar to other initiatives that track benign tools that can be abused for attacks on Windows (LOLBAS, LOLDrivers, and LOFLCAB), Linux (GTFOBins), macOS (LOOBins), CI/CD pipelines (LOTP), and ESXi VMs (LOLESXi).
Threat/trend reports: Au10tix and SonicWall have recently published reports and summaries covering various infosec trends and industry threats.
Transparency.dev 2024 videos: Talks from Google's Transparency.dev 2024 conference, which took place at the start of October, are now available on YouTube.
Risky Business Podcasts
In this podcast, Tom Uren and Patrick Gray talk about the evolving relationship between Russian intelligence services and the country’' cybercriminals. The GRU's sabotage unit, for example, has been recruiting crooks to build a destructive cyber capability. Tom suspects that GRU thugs are not so good at hands-on-keyboard operations but excellent at coercing weedy cybercriminals to hack for the state.




