Risky Biz News: US imposes visa ban on individuals linked to commercial spyware
In other news: Russia formally bans VPNs; Chinese hackers accessed Japanese diplomatic cables; DEF CON canceled (but only for a day, though).

This newsletter is brought to you by Thinkst, the makers of the much-loved Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

The US government has restricted visas for individuals involved in the development and misuse of commercial spyware.
The Department of State says commercial spyware has facilitated repression and enabled human rights abuses.
"Such targeting has been linked to arbitrary detentions, forced disappearances, and extrajudicial killings in the most egregious of cases. Additionally, the misuse of these tools presents a security and counterintelligence threat to U.S. personnel," Secretary of State Antony Blinken said in a statement.
The visa restriction applies to individuals who developed or sold commercial spyware but also to those who misused it. It also applies to close family members, such as spouses and children.
Officials did not name any commercial spyware vendors. A State Department representative told Axios they plan to decide what commercial spyware vendor falls under the visa ban on a case-by-case basis.
The visa restriction is extremely likely to apply to individuals linked to spyware vendors such as Candiru, NSO Group, Intellexa, and Cytrox. The US has placed the four companies on trade blacklists in 2021 and 2023, respectively.
In March 2023, the White House also issued an executive order banning US federal agencies from contracting commercial spyware from vendors with a known track record of misuse, fearing the dodgy products could be misused to spy on US investigations, posing a national security risk.
In a report this week, Google said it currently tracks around 40 commercial spyware vendors "with varying levels of sophistication and public exposure, selling exploits and surveillance capabilities to government customers."
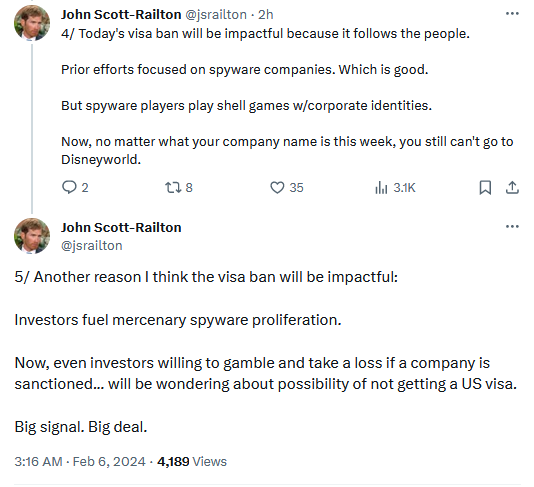
"Investors fuel mercenary spyware proliferation," CitizenLab's John Scott-Railton explained in a series of posts on social media. "Now, even investors willing to gamble and take a loss if a company is sanctioned... will be wondering about [the] possibility of not getting a US visa. Big signal. Big deal."
In addition, a visa entry ban list has other benefits. The biggest is that it can be managed and expanded much easier and faster than an international sanctions list that needs to be coordinated with different US government agencies and maybe some foreign countries.
It remains unclear how the visa restriction will work with citizens of countries with a visa waiver.
Breaches, hacks, and security incidents
Deepfake theft incident: An employee at a multinational company in Hong Kong sent $25 million to scammers. The employee transferred the funds after the scammers invited him to a meeting with deepfake versions of his colleagues and chief financial officer. Hong Kong police said the theft is one of many similar incidents where deepfake technology was used. [Additional coverage in CNN]
Google+ breach settlement: Google has agreed to pay $350 million to settle a class action lawsuit over a security lapse at its defunct Google+ social network. The incident took place in 2018 when Google discovered that the Google+ API exposed the data of 52.5 million users. Google initially agreed to pay $7.5 million to affected users in a separate lawsuit. The new $350 million settlement is for individuals who bought Google stock between April 2018 and April 2019 and were impacted by Google's security blunder. [Additional coverage in WaPo]
Philippines govt cyberattacks: Hackers operating out of China tried to break into websites and email systems of the Philippine government. Philippine officials say the attacks came from Chinese IPs but didn't attribute the attacks to the Chinese government. The attackers DDoSed government sites and attempted to break into Google Workspace admin accounts. [Additional coverage in PhilStar]
Japan MFA hack: Chinese state-sponsored hackers have allegedly breached a system used by the Japanese Ministry of Foreign Affairs to exchange diplomatic cables. The hack took place in 2020 and was initially detected by US authorities. The same hacking campaign also breached a network used by the Japanese Defense Ministry to handle classified military information. In light of the hacks, the Japanese government committed to hiring 20,000 cybersecurity professionals in the coming years. [Additional coverage in Yomiuri, Piyolog, and MofA/PDF]
Netherlands MoD hack: The Dutch government says that Chinese cyber spies breached one of its military defense networks. The incident took place last year and the network was described as an "unclassified peripheral system." According to a technical report published by the Dutch military intelligence agency, the hackers gained access after exploiting an old vulnerability (CVE-2022-42475) in an unpatched FortiGate firewall. The threat actor deployed an advanced backdoor named COATHANGER that was designed to survive both reboots and firmware upgrades.
General tech and privacy
Apple warning: Apple Fellow Phil Schiller—who heads the company's App Store—warns that EU users will be more vulnerable to attacks and intrusive tracking after the EU forced the company to open its platform for third-party app stores. [Additional coverage in Fast Company]
Google Rust grant: Google has announced a $1 million grant for the Rust Foundation to improve the programming language's interoperability with C++.
Copilot lowers code quality: A new GitClear study has found that GitHub's new AI-powered Copilot tool lowers code quality and maintainability. [Additional coverage in Visual Studio Magazine]
Android Virtualization Framework: Here's a list of Android smartphones that support the new Android Virtualization Framework that shipped with Android 14.
Pkl: Apple has open-sourced a new programming language named Pkl (pronounced Pickle), an embeddable configuration-as-code language designed for runtime configuration. Pkl can work with apps written in Go, Swift, Java, and Kotlin.
Mozilla Monitor Plus: Mozilla has launched a paid version of its Monitor service that will allow users to remove subscribers' data from data broker services. The new service is named Mozilla Monitor Plus and will cost users $8.99 per month.
Government, politics, and policy
Russia formally bans VPNs: The Russian government has formally banned the use of VPN services starting on March 1 this year. The ban was announced by Ekaterina Mizulina, Chairwoman of the Safe Internet League, a para-government organization that works with the Kremlin to censor the Russian internet. Mizulina described the ban as a measure needed to stop VPNs from siphoning information from Russian devices. The Russian official was sanctioned by the EU at the end of January for her work on restricting freedom of opinion and expression in Russia. She is often described as Russia's main censor. The official ban comes as Russian officials repeatedly claimed they would not ban VPN services. Russian telecommunications watchdog Roskomnadzor has been silently banning VPN services and protocols since Russia's invasion of Ukraine. [Additional coverage in TASS]
Russian internet censorship visibility: Russian officials are planning to limit access to the list of websites blocked by Russian telecommunications watchdog Roskomnadzor. [Additional coverage in Kommersant]
US industry group pushback: Cybersecurity and tech trade groups are urging the US government to rethink its new cybersecurity requirements for federal contractors. The new requirements include stricter breach reporting and the use of software bills of materials (SBOMs). [Additional coverage in NextGov]
Pall Mall Process: Thirty-six countries have signed a new international agreement to tackle the hacker-for-hire and commercial spyware industry. Named the Pall Mall Process, the agreement will encourage governments to tackle the growing number of companies providing such services. Israel, the home of many of these companies, did not attend. Representatives from Apple, Google, Microsoft, and other private-sector companies were also at the event.
Sponsor section
In this Risky Business News sponsor interview, Tom Uren talks to Haroon Meer of Thinkst Canary. They discuss how network attackers win, how their tactics have changed over time, and what this means for network defenders.

Cybercrime and threat intel
Grandoreiro money mules: Spain's National Police has detained 133 suspected money mules for allegedly helping the Grandoreiro malware gang launder stolen funds. The suspects were detained over the course of the past two years. Brazilian police detained five individuals last month believed to be the leaders of the Grandoreiro malware gang. The Grandoreiro gang has targeted and stolen funds from customers of banks in Brazil, Spain, Portugal, and Mexico since 2019.
Google's view of the commercial spyware industry: Google says it is tracking around 40 entities that are currently active on the commercial z`surveillance market. The companies have varying degrees of sophistication and are involved in the sale of exploits and turn-key surveillance capabilities to government customers. Google says that 20 of the 25 zero-days discovered last year were linked to spyware vendors. In addition, 35 of 72 zero-days in Google products discovered since 2014 have also been linked to these companies.
ResumeLooters: A cybercrime group named ResumeLooters has breached and stolen sensitive data from at least 63 websites across Southeast Asia. The group's attacks leveraged SQL injection and XSS vulnerabilities to gain access to its victims' backend databases. Security firm Group-IB says the group has stolen more than 2 million records, many of which were later sold on Telegram channels for Chinese-speaking cybercriminals. Over a quarter of the stolen data was taken from job search portals.
RedCurl: FACCT has published a new report on RedCurl, a financially motivated hacking group. According to the new report, RedCurl has now expanded operations to Southeast Asia and Australia. The Russian security firm described the group as "Russian-speaking."
C2 infrastructure report: Cobalt Strike has remained the top choice for adversary command and control (C2) infrastructure last year, according to a recent Sekoia report. It's honestly no surprise. Cobalt Strike has been the top choice for APTs and cybercrime operators for more than half a decade now.
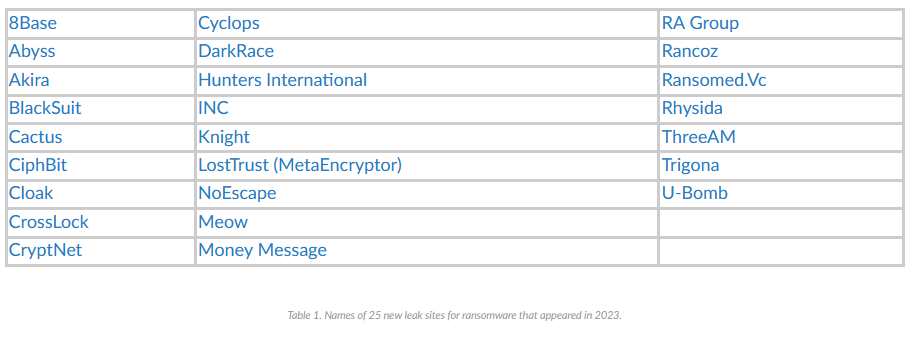
Ransomware in 2023: Palo Alto Networks has published a yearly overview of the 2023 ransomware landscape. Last year, activity hit an all-time high, with 3,998 victims listed on leak sites and 25 new ransomware leak sites launched on the dark web. Malwarebytes also published a report on the same topic.
Malware technical reports
BlackHunt ransomware: Rapid7 has published a technical write-up on BlackHunt, the ransomware gang that recently hit a major Paraguayan ISP. Researchers say BlackHunt uses some of the leaked LockBit source code and has been heavily inspired by REvil operations.
Mispadu Stealer: Palo Alto Networks has published a report on Mispadu Stealer, an infostealer that is commonly used to target LATAM organizations.
Ov3r_Stealer: Trustwave looks at Ov3r_Stealer, a new infostealer spread online using phishing and Facebook ads.
PikaBot: Logpoint has published a report on the PikaBot loader, which has been offered as a MaaS since early 2023.
Sponsor Section
Most companies discover they've been breached way too late. Thinkst Canary fixes this: just 3 minutes of setup, no ongoing overhead, nearly 0 false positives, and you can detect attackers long before they dig in. Check out why our Hardware, VM, and Cloud-based Canaries are deployed and loved on all 7 continents.

APTs, cyber-espionage, and info-ops
Midnight Blizzard Microsoft hack: SpecterOps researchers have published an analysis of how the Midnight Blizzard Russian APT breached Microsoft's infrastructure.
Vulnerabilities, security research, and bug bounty
Android security updates: The monthly security updates for Android smartphones are out.
Canon security updates: Printer maker Canon has published a security update to patch seven issues in its printer firmware. The vulnerabilities were used at last year's Pwn2Own hacking contest.
Ivanti zero-day write-up: Assetnote has published a technical write-up on CVE-2024-21893, the latest of the three recent zero-days in Ivanti Connect Secure VPN appliances. This has now entered mass exploitation after two PoCs were published online.
Ivanti Avalanche write-up: Trend Micro's ZDI has published a write-up on CVE-2023-46263, an arbitrary file upload vulnerability in the Ivanti Avalanche MDM product.
MikroTik unpatchable jailbreak: Agile Information Security's Pedro Ribeiro has published a jailbreak for MikroTik Cloud Hosted Router (CHR).
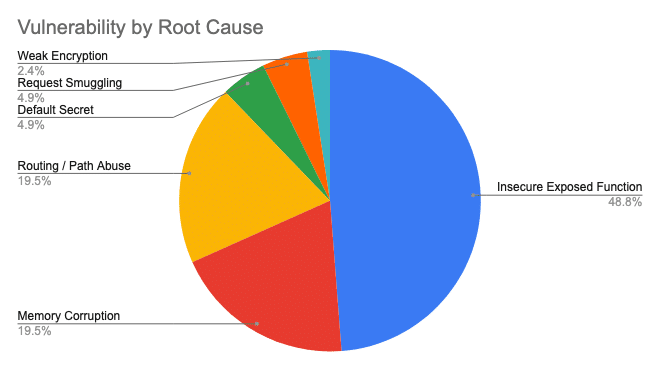
CISA KEV 2023 analysis: Security firm Horizon3 has analyzed all the entries published in 2023 in CISA KEV, a database of actively exploited vulnerabilities. Almost half of actively exploited bugs discovered last year targeted insecure exposed functions rather than memory corruption issues, leading researchers to believe that a transition to Rust coding won't put a dent in actively exploited bugs as it was initially believed.
Infosec industry
Employee trust in security teams: A CybSafe survey found that 97% of employees across the UK and US trust their cybersecurity teams despite having trust and visibility fears.
VT Livehunt Cheat Sheet: Google has published a cheat sheet for its VirusTotal Livehunt service.
New tool—Root User Alarm: Software engineer Ben from KC has published a Terraform library named Root User Alarm that will automatically configure AWS root user usage alarms.
DEF CON conference canceled and uncanceled: The DEF CON cybersecurity conference was forced to relocate to a new venue after Caesars Hotels abruptly terminated its contract. This year's event was canceled for a day before organizers found an empty venue during the busy Las Vegas August period. DEF CON 32 will now be hosted at the Las Vegas Convention Center from August 8 to 11. The DEF CON conference was canceled for the first time in its history and went to virtual format in 2020 due to the COVID-19 pandemic.
BSides London videos: Talks from the BSides London 2023 security conference, which took place in December, are now available on YouTube.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about what up-and-coming countries should expect from a Cyber Command and whether they should invest in it.





