Risky Biz News: US critical infrastructure needs better cyber insurance coverage
In other news: Pro-abortion hacktivism; another mega ultra crypto hack; and a ransomware gang launches a "bug bounty program."
This newsletter is brought to you by Airlock Digital, Rumble Network Discovery, Proofpoint, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
A report published last week by the US Government Accountability Office (GAO) has found that critical infrastructure organizations may not receive full cyber insurance coverage, especially if incidents result in "catastrophic financial losses."
GAO looked at cyber insurance provided by both the US private sector and the US government itself—through its Terrorism Risk Insurance Program (TRIP).
Officials said that while, in general, the cyber insurance sector provides good coverage for incidents like data breaches and ransomware attacks against most companies, critical infrastructure entities are in a sensitive spot.
First, the US government's TRIP coverage may not kick in unless a cybersecurity incident is formally linked to an act of "terrorism," which most likely is not going to happen since cyber-related outages must be violent or coercive in nature, to be certified as "acts of terrorism."
Second, GAO notes that private cyber insurance providers may be able to weasel their way out of covering a particularly damaging (and expensive) attack if the incident is formally linked to an act of war, such as the acts of a state-backed threat actor.
The findings of the GAO report aren't particularly "new" and, at this point, are common knowledge for most cybersecurity experts today. However, the report is an important step in the sometimes overly complex procedure of the US government.
In the report's conclusion, GAO officials recommended that both Treasury and DHS officials update the US government's response to incidents impacting critical infrastructure. This revamped response should provide better support for cybersecurity-related events and their typical fallout, such as expanding the government's insurance coverage beyond just acts of "classic" terrorism.
Breaches and hacks
Harmony mega-hack: Cryptocurrency bridge project Harmony said it was hacked for more than $100 million worth of cryptocurrency. The hack took place on Thursday and targeted the Harmony Protocol, a system used to interchange cryptocurrencies between different blockchains. The company is currently keeping an incident response blog post on Medium.
The @wormholecrypto, @Ronin_Network, and #Horizon bridge exploits lost $1.1B funds in user funds.
— Uno Re (@unoreinsure) 4:41 PM ∙ Jun 24, 2022
That's more than what @Meta paid for @instagram's acquisition.
Unless #DeFi manages to create safer bridges, it may be impossible to achieve a truly #crosschain ecosystem.
CafePress fine: The US FTC fined last week the CafePress t-shirt merchandise site $500,000 for trying to cover up the severity of its 2020 data breach. The FTC said CafePress had weak security measures in place, which eventually allowed a threat actor to break in and steal the personal data of 23 million customers.
Ransomware attacks in Japan: Two large Japanese companies—automotive component manufacturer TB Kawashima and automotive hose giant Nichirin—were hit by ransomware attacks last week.
XCarnival hack: XCarnival, a company that claims to be the first NFT assets management platform for the Metaverse, was hacked on Saturday by an unidentified threat actor who exploited its smart contracts to steal 3,087 ETH, estimated at roughly $3.8 million at the time of the heist. The company confirmed the incident in a statement on Twitter when it also paused its smart contracts. Additional details are available in this Twitter thread from blockchain security firm PeckShield, which was the one to stop the suspicious transactions:
1/ @XCarnival_Lab was exploited in a flurry of txs (one hack tx: etherscan.io/tx/0x51cbfd46f…),
— PeckShield Inc. (@peckshield) 1:14 PM ∙ Jun 26, 2022
leading to the gain of 3,087 ETH (~$3.8M) for the hacker (The protocol loss may be larger).
Abortion hacktivism: In the aftermath of the US Supreme Court's overturning of the Roe v Wade abortion protections, a hacktivist group known as SiegedSec has leaked data claiming to be from government employees from states that support or have already enacted abortion bans. According to early reports of users who sifted through the data, the leaked files appear to contain info from Arkansas and Kentucky, although it's unclear if it's newly obtained information or just recycled old leaks.
Unsurprisingly, we are seeing some cyberattacks against those who support abortion bans. One group has already targeted/hacked two state govs and dumped files. Partial screencap (redacted):
— Dissent Doe, PhD (@PogoWasRight) 2:33 PM ∙ Jun 26, 2022
General tech and privacy
Google Analytics banned in Italy: The Italian data protection agency has banned the use of Google Analytics on Italian websites. Italy has now become the third country to ban the use of Google Analytics after Austria and France.
Opera launches no-log VPN: Following in Mozilla's footsteps, Opera Software has launched a VPN service for its users. Opera says the new VPN Pro service is complementary to its Free VPN offering, which the company has been providing to its browser users for half a decade. However, unlike its Free VPN service, which works more like a proxy, Opera says this new service is actually a "no-log" VPN with "3000+ private network servers in over 30 locations around the world." Furthermore, VPN Pro will also be provided as a separate app and provide device-wide VPN connections and not only for the Opera browser's traffic.
Government, politics, and policy
Supreme Court ruling bot activity: The US Supreme Court's controversial ruling that rolled back Roe v Wade abortion rights protections for US women has spurred a spike in bot and inauthentic activity on Twitter. According to Christopher Bouzy of BotSentinel, inauthentic accounts are trying to convince people angry about the decision not to vote in the upcoming US midterm elections.
Foreign influence actors are very likely to use todays abortion decision to amplify the emotions we all feel on both sides of this issue. Russia is more likely to covertly further the divide between Americans on this issue. China is more likely to amplify how F’d the US govt is.
— Charity Wright @FIRSTCon Dublin (@CharityW4CTI) 7:20 PM ∙ Jun 24, 2022
More cash for CISA: US officials voted on Friday in favor of a $2.9 billion budget for the Cybersecurity and Infrastructure Security Agency (CISA). The amount allocated for CISA is $417 million more than the Biden administration requested for the DHS cyber wing, The Record reported.
New Air Force cyber chief: The Senate on Thursday confirmed Air Force Maj. Gen. Kevin Kennedy, the current US Cyber Command director of operations, as the new head of the US Air Force's information warfare branch, the 16th Air Force (Air Forces Cyber).
Russia's IT balkanization continues: Russian government agencies are ditching foreign video conferencing software, such as Zoom, Webex, and WhatsApp, in favor of Russian-made video conferencing tools from VK and TrueConf, Kommersant reported last week. The move comes after Russian government agencies also abandoned foreign IM apps earlier this month as well, also in favor of local alternatives.
Cybercrime and threat intel
Mitel zero-day: Crowdstrike said in a report on Friday that it observed threat actors using a zero-day in Mitel MiVoice VOIP appliances as a way to gain initial access inside corporate networks for supposed ransomware attacks. The company said it reported the vulnerability (CVE-2022-29499) to Mitel, which released patches here.
Shodan search to find Mitel boxes:
— Kevin Beaumont (@GossiTheDog) 3:22 PM ∙ Jun 24, 2022
http.html_hash:-1971546278
Presentation online has roughly doubled in 5 years.
Malicious Python packages: Sonatype said it discovered five malicious Python packages that contained functionality to steal AWS credentials and environment variables.
Cobalt Strike update: The Cobalt Strike adversary emulation framework received an update last week with the addition of "thread stack spoofing capabilities." This new feature allows CS tools to bypass some AVs and EDRs that rely on thread stack inspection to determine the legitimacy of a process that is calling a function or an API.
Social engineering report: Proofpoint has an interesting report out on the most common techniques that threat actors used in social engineering attacks throughout 2021. This includes holding extended conversations with victims to build trust, using existing conversation threads between colleagues, and the use of telephone calls, since victims generally tend to believe that cyber scams usually take place via web-based communication channels only.
LockBit 3.0: The operators of the LockBit ransomware have apparently launched the 3.0 version of their malware over the weekend. In addition, the group also launched a "bug bounty program" where they plan to pay for information on bugs in their encryption code, vulnerabilities in their public infrastructure, or PII data on the members of other ransomware groups.
Lockbit ransomware group announced today Lockbit 3.0 is officially released with the message: "Make Ransomware Great Again!"
— vx-underground (@vxunderground) 8:30 PM ∙ Jun 26, 2022
Additionally, Lockbit has launched their own Bug Bounty program paying for PII on high-profile individuals, web security exploits, and more...
Malware technical reports
Snake Keylogger: Malware researcher Mohamed Ashraf has published a deep analysis of the Snake Keylogger, a malware strain developed in .NET. The malware includes functions to steal sensitive information from an infected device, including browser credentials, keystrokes, screenshots of a victim's screen, and clipboard data.
API hammering: Palo Alto Networks detailed on Friday the use of "API hammering" as a sandbox evasion technique. API hammering is currently used by malware strains such as Zloader and BazarLoader.
Black Basta: Security firm Cybereason has published a report on the Black Basta ransomware. The report echoes previous findings from IBM X-Force, Trend Micro, and NCC Group, including that Black Basta members are connected to the now-defunct Conti gang, something the Conti group tried to "formally deny" a few weeks back.
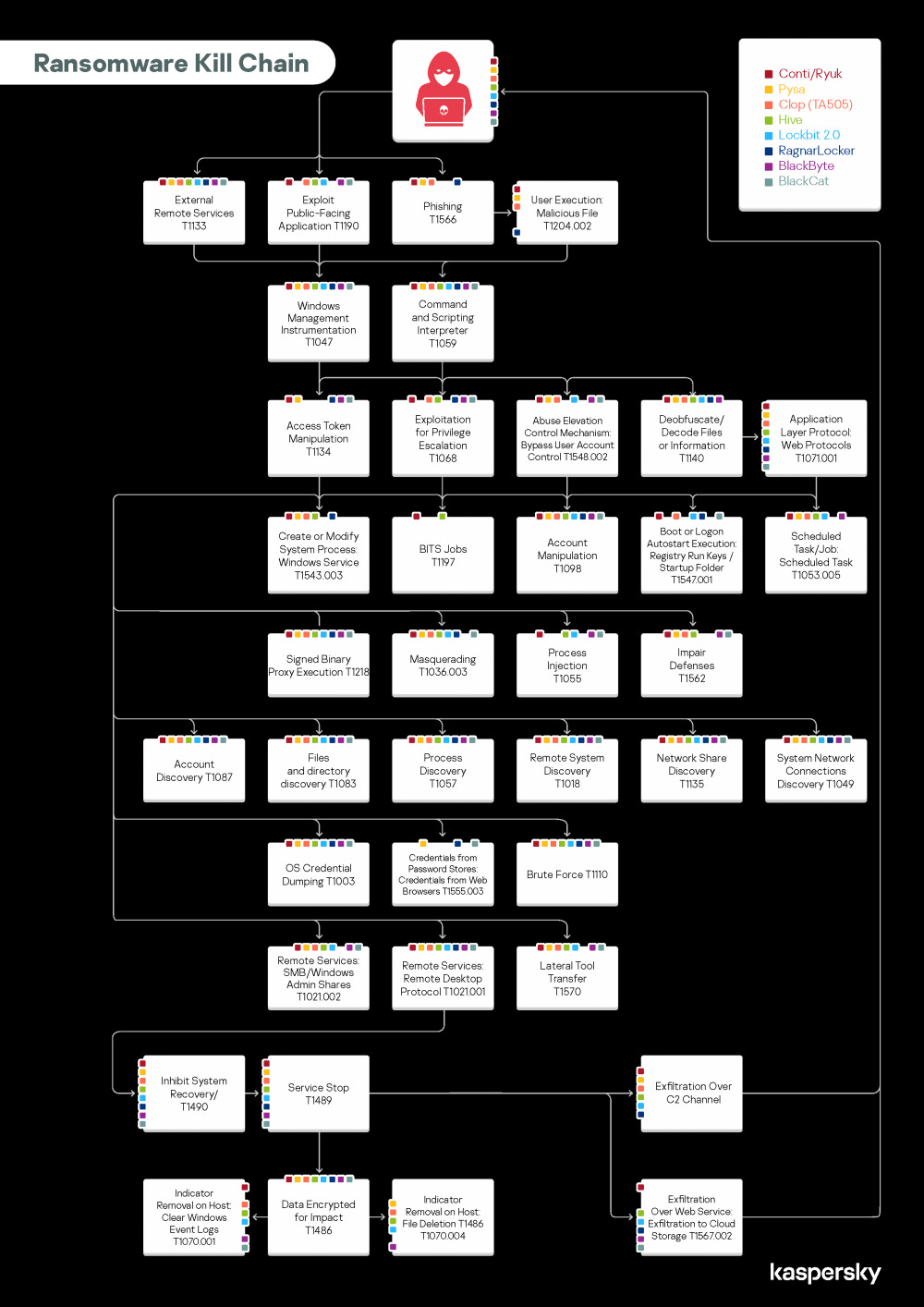
Ransomware TTPs: Kaspersky has published a report on the TTPs of the most common eight ransomware families, including Conti/Ryuk, Pysa, Clop (TA505), Hive, Lockbit2.0, RagnarLocker, BlackByte, and BlackCat.
APTs and cyber-espionage
Agent Saitama: Malware researcher Mohamed Ashraf has published an analysis of APT34's Saitama Agent, a backdoor trojan that uses DNS tunneling and a finite state machine.
Vulnerabilities and bug bounty
FOSS bugs get patched slower and slower: DevSecOps firm Snyk has published its yearly State of Open Source Security report, and one of the company's main findings this year was that the time it took companies to fix vulnerabilities in FOSS projects has more than doubled from 49 days in 2018 to 110 days in 2021.

Miracle exploit: Two security researchers have published a technical write-up on a vulnerability in the Oracle Fusion middleware tracked as CVE-2022–21445 but also known as the Miracle exploit. The vulnerability allows pre-auth RCE, and the researchers said that it took Oracle roughly six months to patch the issue.
Codesys bugs: A security researcher from NSFocus has published details about 11 vulnerabilities in CODESYS v2 runtime, used in many industrial products.
Zena RCE: Phoenix Security has published a technical write-up about an XSS-to-RCE vulnerability in the Zena IT orchestration toolkit. A PoC has also been published on GitHub.




