Risky Biz News: US charges swatters who terrorized government officials
In other news: City of Columbus sues security researcher; Brazil bans Twitter; Poland charges official in Pegasus spyware scandal.

This newsletter is brought to you by GreyNoise. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

The US Department of Justice has charged a Romanian and a Serbian man for a years-long swatting campaign that terrorized US citizens, including multiple senior government officials.
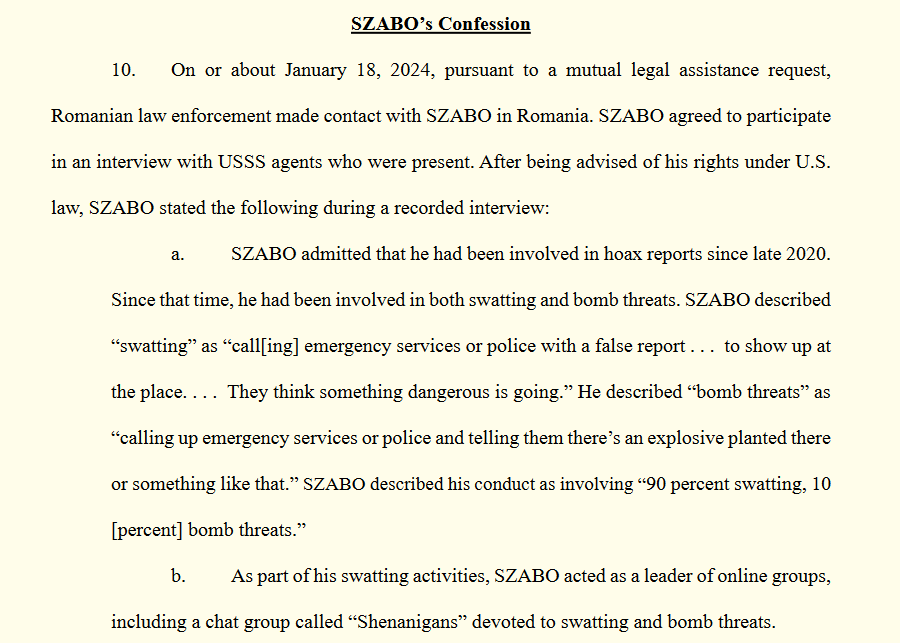
Officials say a 26-year-old Romanian named Thomasz Szabo was the moderator of an online chatroom called "Shenanigans," where he planned swatting and fake bomb threats since December 2020.
Szabo allegedly worked closely with a 21-year-old from Serbia named Nemanja Radovanovic.
According to court documents [PDF], the two collected the personal information on well-known figures and then called authorities to report shootings, kidnappings, or bombs at their homes, hoping for an armed police response that would scare or even harm the victims.
Throughout the years, and especially in late 2023, Szabo and Radovanovic organized swatting events against a former US president, members of Congress, state governors, federal officials, and members of US law enforcement agencies.
The court documents did not share the name of the ex-President but it does mention that in the aftermath of the Capitol riots, Szabo called in a bomb threat at the Capitol, claiming he planted a bomb designed to kill then-President-elect Joe Biden.
The two also called in fake bomb threats at US universities, synagogues, and other religious institutions.
The DOJ indictment lists more than 50 unnamed victims, although some dates align with public reports, such as a swatting event that targeted the home of CISA Director Jen Easterly earlier this year.
According to a supporting affidavit, Szabo confessed to his crimes and is currently in the custody of the US Marshals.
He and Radovanovic were identified after using Google Voice to place the swatting calls.
Breaches, hacks, and security incidents
Lookier data breach: Hackers have leaked data from UK online shopping service Lookier. The data is from a March security breach and includes the details of almost five million users. This includes names, email addresses, phone numbers, and physical addresses.
JAS ransomware attack: Transport logistics company JAS Worldwide says a ransomware attack has crippled its ability to operate for over four days. The company is a freight forwarder, a firm specializing in the arrangement of cargo on behalf of shippers. JAS says the attack impacted its ability to prepare and transport cargo containers for some customers. The company restored its central operations system last Friday, four days after the initial attack.
Columbus sues security researcher: The city of Columbus has sued a security researcher who exposed the local government for lying about the impact of a recent ransomware attack. The city attorney has obtained a temporary restraining order against David L. Ross Jr., a security researcher publicly known as "Connor Goodwolf." The order bans Ross from speaking about a ransomware attack that hit the city of Columbus at the end of June. Ross had previously corrected city officials when they claimed no personal data was stolen in the attack. The researcher retrieved sensitive city data from the dark web, which led local police and firefighters to file lawsuits against the city. Ross says he's going to fight the restraining order. [Additional coverage in The Columbus Dispatch]
Maduro's false DDoS attack statements: The Maduro regime has made misleading statements about a DDoS attack that hit Venezuela's electoral system on election day. Security firm Team Cymru says the attack took place but was short-lived and that its origin was not from North Macedonia, as officials claimed. The attack appears to have targeted the login portal for Venezuela's electoral oversight system.
DFS cyberattack: Russian government hackers have breached the IT network of the DFS, the German air traffic control agency. The incident has not impacted air traffic across Germany. According to government sources, German news outlet BR24 has linked the attack to ATP28, a cyber unit in Russia's military intelligence service.
Guatemala MoE cyberattack: Guatemala's Ministry of Education says it was the victim of a cyberattack on some of its IT systems. Officials are still investigating last week's attack and if any data was stolen or compromised.

General tech and privacy
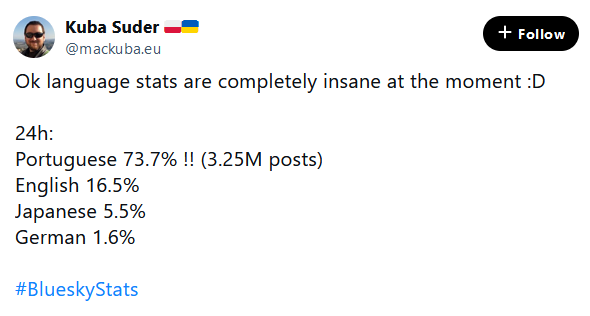
Brazil bans Twitter: Brazil's Supreme Court has banned social media app Twitter after the company refused to name a legal representative in the country. The Court banned Twitter after the company failed to suspend accounts that were spreading disinformation about the 2023 attempted coup and attack on the Brazilian Congress. The ban also comes with a $9,000/day fine for users who use a VPN to access the platform. Following the ban, Bluesky reported a huge influx of new users, with Portuguese-speaking users now accounting for 75% of the site's accounts. [Additional coverage in the BBC]
FTC fines Verkada: The FTC has fined security camera firm Verkada $2.95 million for failing to implement cybersecurity measures to protect its systems. The fine is related to a March 2021 security breach when a hacker accessed customer data and video footage from over 150,000 Verkada cameras. The hacker used the cameras to access and leak footage from psychiatric hospitals, women's health clinics, police stations, and prisons. The FTC fine is also related to violations of the CAN-SPAM Act after Verkada was also caught flooding prospective customers with spam emails.
Algorithms not protected by Section 230: A US judge has ruled that TikTok curation algorithms are not protected by Section 230 of the Communications Decency Act. [Additional coverage in BIG]
Text Fragment URLs: Apple and Mozilla are adding support for Text Fragment URLs in Firefox. The feature has been available in Chromium browsers and allows users to link to specific pieces of text within a web page.
AnandTech shuts down: Hardware review news site AnandTech announced last week it was shutting down after 27 years.
Proton launches new VPN protocol: VPN maker Proton has launched Stealth, a new VPN protocol to bypass internet censorship by making VPN traffic appear as common HTTPS.
Telegram disables geo-chat feature: Telegram has disabled the "People Nearby" and geoChat features for most of its users. The two features are used by users to discover each other and start chats when they are in physical proximity to each other. According to law enforcement, the two features were often used to arrange drug deals and prostitution. Only users who are friends on Telegram can still use the two features.
Microsoft launches Windows App: Microsoft has launched a new app to manage remote desktop connections across a variety of MSFT services, such as Windows 365, Azure Virtual Desktop, Remote PC, Remote Desktop Services, Microsoft Dev Box, and more. Available on the Microsoft Store as the Windows App.
Threads-Mastodon integration: Threads is now letting its users see and interact with replies made on Mastodon instances.
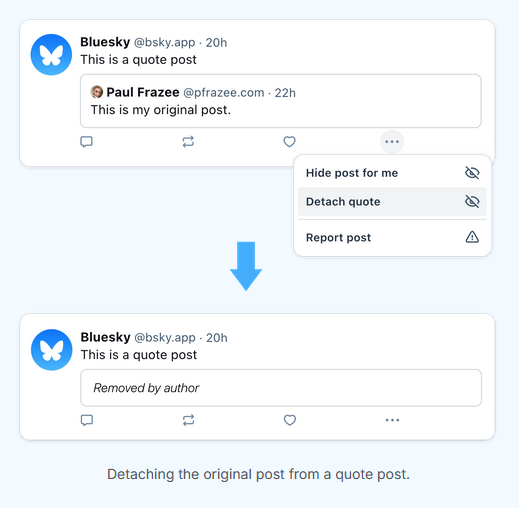
Bluesky adds anti-toxicity features: Social network Bluesky has added what the company calls new "anti-toxicity" features. Bluesky will now let users hide replies they don't like and detach quote posts from the original posting. The company has added the new features to reduce harassment on the platform. It also added the ability to mute notifications from people the account owner doesn't follow.
Government, politics, and policy
CISA launches new reporting portal: CISA has launched a new secure platform where companies can report cybersecurity incidents to the agency's staff. The new CISA Services Portal includes support for Login.gov credentials and the ability to start a conversation with a CISA representative. It also includes the ability to save and update reports and the ability to share the report with other parties in the case of other third-party reporting requirements.
US Healthcare Cybersecurity Act: Three congressmen have introduced a bill in the US House to improve cybersecurity in the healthcare sector. The Healthcare Cybersecurity Act will task CISA to collaborate with the HHS on improving cybersecurity for non-federal healthcare entities. The two agencies will have to prepare threat indicators and defensive measures and coordinate during cybersecurity incidents. A similar bill was introduced in the US Senate in July and is the government's response to the Change Healthcare cyberattack from earlier this year. [Additional coverage in CyberScoop]
Green Berets hacking capabilities: US Green Berets are now utilizing cyber capabilities in their operations.
"During the exercise, the aforementioned ODA team identified a target building and used a remote access device (RAD) to identify the networks coming from the facility. They were able to crack the WiFi password, enumerate the network, and run exploits on the target computer inside the building. This enabled the team to manipulate security cameras, door locks, and other security systems in the building."
EU Chat Control comes back from the dead: EU officials have resurrected the Chat Control legislation for the umpteenth time. [h/t Jurre van Bergen]
Germany's cybercrime losses: Cybercrime and other acts of sabotage have cost German companies around $298 billion in the past year. [Additional coverage in Reuters]
Poland charges official in spyware scandal: Polish prosecutors have charged a former government official with abuse of power related to the purchase of Pegasus spyware using ministry funds in 2017. Charges were levied against Michał Woś, a member of the Law and Order party who served as undersecretary in the Ministry at the time of the purchase. Officials say Woś diverted money from legitimate government funds to finance the Pegasus acquisition. Woś denied any wrongdoing and argued the charges are illegal because they were brought by illegitimately appointed prosecutors. If found guilty he faces up to ten years in prison.
Russia tells telcos to stop speeding up YouTube: Russia's internet watchdog has told local telcos to stop trying to speed up YouTube traffic. Some Russian telecom operators started speeding up or disguising YouTube traffic in their networks as a way to get around a national block on the site imposed by authorities. [Additional coverage in Kommersant]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Andrew Morris, founder of security firm GreyNoise. Andrew introduces Plasma, a new GreyNoise product that can allow customers to deploy custom GreyNoise sensors anywhere they want—on perimeters, on internal networks, on DMZs, or anywhere else.

Cybercrime and threat intel
BEC scammer extradited to US: US authorities have extradited a Nigerian national from Ghana to face charges in a BEC-related case. Officials say Olusegun Samson Adejorin was part of a scheme designed to steal $7.5 million from two US charitable organizations in 2020. If found guilty, Adejorin faces up to 20 years in prison.
OTP Agency admins plead guilty: Three British men have pleaded guilty to running OTP Agency, a web service that allowed cybercriminals to intercept one-time passcodes. The three were arrested in March 2021, a month after the site was featured in a Brian Krebs article about the rising market of OTP token thefts. The OTP Agency service allowed threat actors to enter a victim's phone number, initiate a call posing as a bank, and request victims to share an OTP token from their banking app.

New npm malware: Seventy-seven malicious npm packages were discovered last week. Check out GitHub's security advisory portal for additional details.
gTLDs study: Palo Alto Networks has looked at the 19 newly released gTLDs and found that many of them have already been adopted for malware campaigns.
Deepfake scam campaigns: Palo Alto Networks has published a report on dozens of scam campaigns using deepfake videos featuring the likeness of various public figures, including CEOs, news anchors, and top government officials.
#FreeDurov campaign: CyberKnow looks at the response from the hacktivist community to Pavel Durov's arrest. While some were happy of Durov's arrest, most hacktivist groups participated in #FreeDurov, a DDoS campaign that targeted French websites. Most of the groups were the same pro-Kremlin groups that have been harassing Western countries since Russia's invasion of Ukraine.
Black Basta goes to SEO poisoning: In its threat intel podcast, the Microsoft security team says it spotted the Black Basta ransomware make a significant shift in its operational tactics. The company says Black Basta operators have moved away from malspam phishing campaigns and are now using SEO-poisoned results and voice phishing techniques to lure victims into installing malware on their networks.
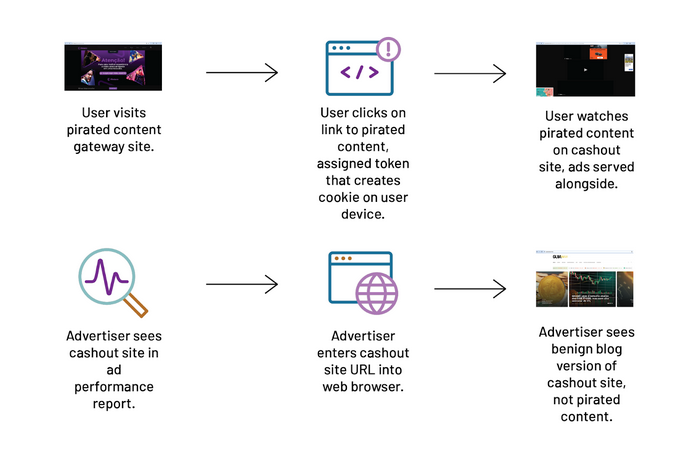
Camu network: A threat actor has used a sprawling network of Brazilian piracy sites to serve billions of ads and defraud online advertisers. The Camu network has been operating since December of last year and was generating at its peak the daily ad traffic for the city of Atlanta. Security firm HUMAN says Camu went undetected for months because it would load the piracy sites through intermediary links and show benign blogs when accessing the domain names directly.
Malware technical reports
Godzilla webshell: Trend Micro looks at a malicious campaign targeting Atlassian Confluence servers with exploits for CVE-2023-22527. The end goal is to install a version of the Godzilla webshell on the unpatched servers. The vulnerability has a long history of being exploited for crypto-mining.
AsyncRAT: eSentire looks at a malspam campaign spreading AsyncRAT.
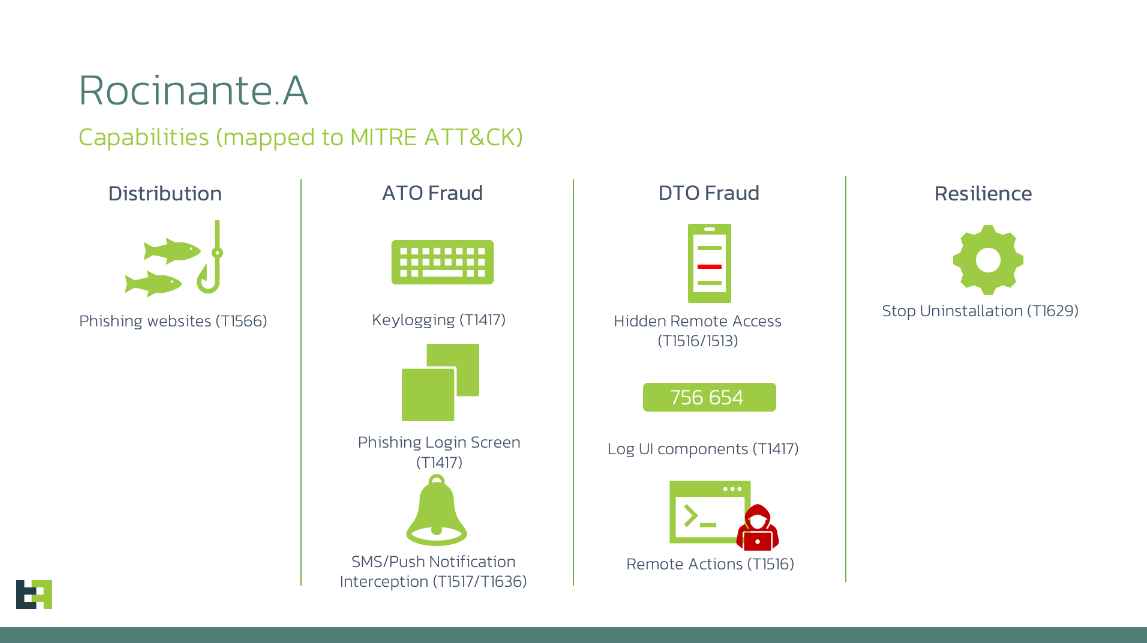
Rocinante: Mobile security firm ThreatFabric has discovered a new Android banking trojan targeting financial institutions in Brazil. Named Rocinante, the trojan can phish for e-banking login credentials, can perform keylogging, and provide attackers with remote access to infected devices. ThreatFabric says the trojan is still under development, and its authors appear to be influenced by malware in other regions.
Underground ransomware: Fortinet looks at one of the smaller ransomware strains recently spotted in the wild, a strain named Underground, currently spread via malspam.
Cicada3301 RaaS: TrueSec has published a report on Cicada3301, a new Ransomware-as-a-Service that launched in June this year.
Sponsor Section
GreyNoise founder Andrew Morris demonstrates how people use the GreyNoise sensor network to find threats and detect attacks.
APTs, cyber-espionage, and info-ops
Voldemort espionage malware: Proofpoint researchers have discovered a mysterious new APT group using a novel backdoor named Voldemort as part of an intelligence collection campaign targeting organizations across the world. The group has used phishing emails impersonating tax authorities from governments in Europe, Asia, and the US. The campaign used LNK and ZIP files to infect victims with the Voldemort backdoor, which was later used to drop additional payloads. Proofpoint researchers say that even if the campaign's technical modus operandi aligns with cybercrime activity, they assess it's likely a cyber-espionage operation.
APTs and LLMs: In the same Microsoft threat intel podcast, the company goes over all the major advanced threat actors abusing LLMs for their operations. The list includes Crimson Sandstorm, Forest Blizzard, and Emerald Sleet.
Citrine Sleet zero-days: North Korean hackers have used a combination of Chrome and Windows zero-days to target individuals in the cryptocurrency industry. The attacks were detected by Microsoft and linked to a North Korean government-backed group the company is tracking as Citrine Sleet. Both zero-days were patched in early August. Microsoft says the attackers used the Chrome zero-day to run malicious code and escape the browser and then used the Windows zero-day to elevate privileges and deploy the FudModule rootkit.
Vulnerabilities, security research, and bug bounty
KerberosSmartcardPaddingOracleAttack: Two researchers from Tel Aviv University have published details about a new attack that exploits legacy cryptographic algorithms to go after the Windows Kerberos protocol. A PoC is here.
VMWare vulnerability: ZDI has published a write-up on CVE-2024-37079, a critical bug in VMWare vCenter that was patched in June.
"A remote, unauthenticated attacker could exploit this vulnerability by sending a crafted DCERPC packet to the target server. Successfully exploiting this vulnerability could lead to a heap buffer overflow, which could result in the execution of arbitrary code in the context of the vulnerable service."
SQLi to bypass TSA checks: Two security researchers have found a vulnerability in a TSA system that allowed them to skip airport security screenings. The vulnerability is an SQL injection in FlyCASS, a program used by the TSA to allow pilots and flight attendants to pre-flight boarding checks. Researchers Ian Carroll and Sam Curry exploited the vulnerability to gain access and add their names to the system. The DHS and TSA fixed the issue in May and have since tried to downplay the vulnerability's impact.
SQLi in wishlist plugins: Patchstack has found an SQL injection vulnerability in a wishlist plugin for WooCommerce. The plugin is used by more than 100,000 sites.
MediaTek exploitation: A security researcher known as Hypr has published a blog post looking at four different ways to exploit CVE-2024-20017, an RCE in the MediaTek WLAN service—originally patched back in March.
Microsoft Streaming Service bug: Security researcher Divyanshu has published an analysis of CVE-2023-29360, an EoP in the Windows Streaming Service exploited in the wild and patched last June.
MSI file vulnerability research: CICADA8's Michael Zhmailo has published research looking at various vulnerabilities in the Microsoft MSI file format.
Aiir account takeover bug: Security researchers at Quorom have found a CSRF bug that can be exploited to hijack accounts on Aiir, a website for creating and hosting online radio streams.
Infosec industry
Threat/trend reports: CriticalStart, Gartner [1, 2], GRF, and Sucuri have recently published reports covering infosec industry threats and trends.
Potential Secureworks sale: Dell is exploring selling Secureworks and has hired a pair of investment bankers to look for buyers. [Additional coverage in Reuters]
DEF CON 32 talks: Slides from the DEF CON 32 security conference, which took place in August, are available on the conference's site.
Black Hat Asia 2024 videos: Videos from the Black Hat Asia 2024 security conference, which took place in April, are available on YouTube.
New tool—ghmlwr: Cyllective security engineer Dave Miller has released ghmlwr, a portal that keeps track of malicious or suspicious GitHub repositories.
New tool—RACE: DARPA has open-sourced the first test version of RACE (Resilient Anonymous Communication for Everyone), a distributed messaging system.
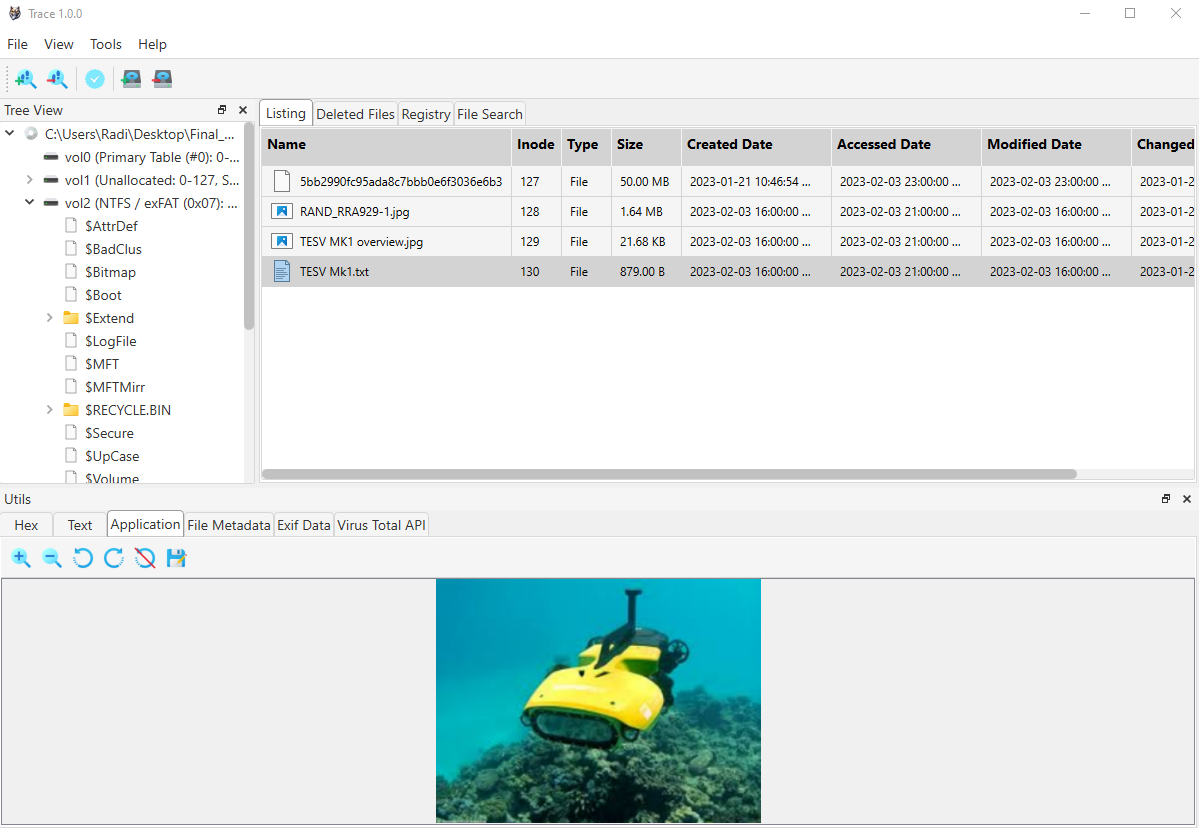
New tool—TRACE: Security researcher Radoslav Gadzhovski has released TRACE, a toolkit for the retrieval and forensic analysis of cyber evidence. It provides an intuitive interface for analyzing disk images and includes a range of functionalities to assist forensic examiners in extracting and viewing the contents of various image file formats.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss the opportunities in phishing and why it is both easy and difficult.
In this podcast, Tom Uren and Patrick Gray discuss an Australian government effort to bridge the gap between online and real identity across the whole economy. It addresses a real need, but Tom doesn't think it will go smoothly.
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!





