Risky Biz News: US charges five Scattered Spider members
In other news: Apple fixes macOS zero-days; T-Mobile finally stops a breach; US takes down PopeyeTools carding portal.

You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
The US Department of Justice has unsealed charges against five suspected members of the Scattered Spider hacking group.
The five include four Americans and one British citizen.
- Ahmed Hossam Eldin Elbadawy, 23, aka "AD," of College Station, Texas;
- Noah Michael Urban, 20, aka "Sosa" and "Elijah," of Palm Coast, Florida;
- Evans Onyeaka Osiebo, 20, of Dallas, Texas; and
- Joel Martin Evans, 25, aka "joeleoli," of Jacksonville, North Carolina.
- Tyler Robert Buchanan, 22, aka "tylerb," from the United Kingdom
Three of the five are confirmed to be in custody. Evans was arrested this week, Buchanan in June, and Urban in January.
Another suspected Scattered Spider member, a 17-year-old from Walsall, the UK, who was detained in May, was not included in the DOJ indictment.
Officials say that since September 2021, the group has conducted phishing and smishing campaigns that targeted the employees of major companies.
Once inside, they allegedly stole confidential information, intellectual property, and personal identifying information. They used the stolen data to gain access to the online accounts of other individuals and then steal cryptocurrency. Officials have confirmed thefts of almost $11 million from at least 29 victims.
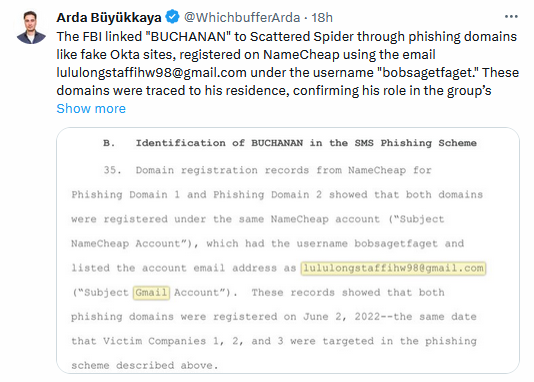
The five are only a small portion of what security firms call the Scattered Spider group—also known as 0ktapus (Group-IB), Scatter Swine (Okta), UNC3944 (Mandiant), Octo Tempest (previously Storm-0875, Microsoft), Star Fraud (SentinelOne), and Muddled Libra (Unit42).
Scattered Spider is not a "hacking group" in the classic meaning of the word, but more of a loosely connected community of individuals who collaborate on hacks for their own financial profit.
Reports from threat intel firms claim that most Scattered Spider members are teens or young men who started inside a Discord server named The Comm.
The Comm served as the meeting ground for some of the internet's "nicest" people, who had some of the "nicest" hobbies, such as organizing swattings, SIM swaps, hacker-for-hire, and even violent attacks, beatings, and physical intimidation.
Scattered Spider evolved from The Comm as the subgroup that was into hacking, but not the educational kind of one. According to the FBI, there are over 1,000 individuals who are connected to Scattered Spider in one way or another.
Ever since its appearance in cybersecurity reports, the group and its tactics stood out instantly, mainly due to the combination of modern and extremely efficient exploitation and social engineering techniques. The DOJ indictment doesn't do them justice to how advanced their hacks have often been.
They didn't just use phishing and smishing, as the indictment says. They also allegedly used SIM-swapping and adversary-in-the-middle (AiTM) phishing kits to breach large corporations, and once inside, they relied on some pretty clever and well-executed social engineering to navigate complicated corporate environments to broaden their access to Slack, Teams, and other internal applications and cloud environments.
They relied on an arsenal of open-source toolkits, anonymizing proxy services, and they monitored hacked networks for early signs of detection.
Some Scattered Spider members also monetized hacked networks either through data extortion or by deploying ransomware.
Some of their victims included Okta, MGM Resorts, Caesar's, Mailchimp, Twilio, and Riot Games, just to name a few.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
T-Mobile stops breach early on: US wireless carrier T-Mobile has detected and stopped a security breach before hackers could get their hands on customer data. According to Bloomberg, hackers breached the company's edge-routing infrastructure and then moved to gain access to some other nearby devices. T-Mobile's security team booted the hackers out after detecting reconnaissance activity from the compromised devices. T-Mobile has suffered nine security breaches since 2019.
Finastra breach: A threat actor has breached and stolen a large batch of internal files from UK fintech company Finastra. The breach took place earlier this month, according to infosec reporter Brian Krebs. The company claims the attacker did not deploy malware or tamper with customer files. The company's data was put up for sale on a known hacking forum a day after the breach.
FlipaClip: The data of almost 900,000 users who registered on the FlipaClip animation app has leaked online. More on the leak can be found in this thread.
Hackers steal MLB star's Lamborghini: A BEC group has hacked into a car dealership and has re-routed expensive cars to new addresses. According to Carscoops, one of the victims who had their cars stolen is Kris Bryant, a third baseman for the MLB's Colorado Rockies. Many of the re-routed cars have now been recovered.
Upbit 2019 crypto-heist linked to NK: South Korean officials have formally linked the $50 million 2019 hack of cryptocurrency exchange Upbit to North Korean hackers.
General tech and privacy
Google cracks down on SEO parasites: Google has apparently remembered that it runs a—checks notes—search engine and has apparently rolled out new updates to websites that abuse their reputation to publish unrelated or paid content.
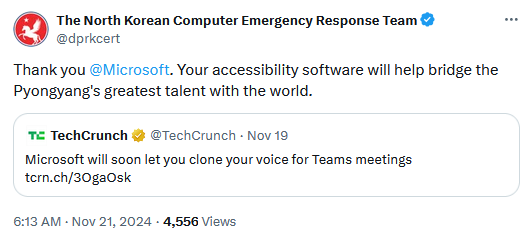
Microsoft develops something dumb, part 9,136: Microsoft engineers had the "great" idea to develop a tool that lets Teams users clone their voices. While Microsoft claims the tool can be used by its AI-based translation tool to speak a user's words in another language with their natural voice, this sounds like one of the most useful phishing tools ever developed.
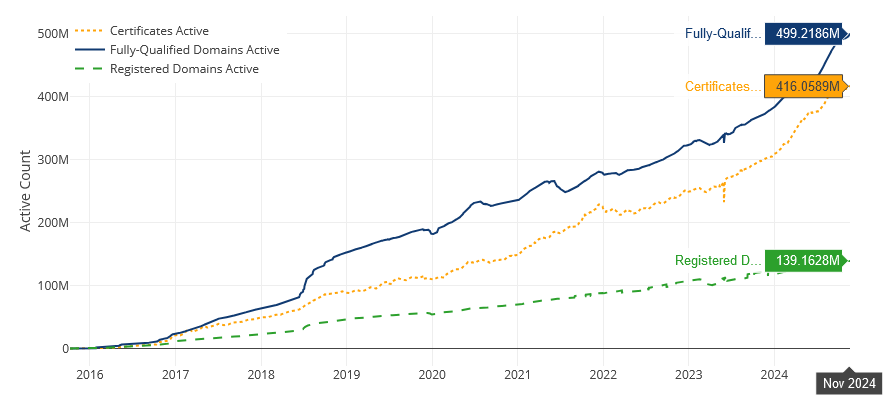
Let's Encrypt 10-year anniversary: The Let's Encrypt project has celebrated its 10-year anniversary on November 18. According to its stats page, its certificates are now used on almost 500 million domains.
Government, politics, and policy
TSA cybersecurity woes: While a GAO report was criticizing the TSA for failing to implement basic cybersecurity guidelines, the agency was also getting blasted on the same day in the US House for being too pushy with its new proposed cybersecurity rules by GOP members, pipeline, and railway operators. US politics in a nutshell, ladies and gentlemen!
Coast Guard issues STS warning: The US Coast Guard has ordered port operators to secure Chinese-made ship-to-shore (STS) cranes. In a security directive this week, officials say the cranes come with "built-in vulnerabilities" that can allow remote access to the equipment's software. Chinese-made ship-to-shore cranes account for nearly 80% of all STS cranes at US ports. The US Coast Guard received the ability to issue maritime cybersecurity directives earlier this year, but it's unclear what its recommendations to secure STS clones actually include. [Additional coverage in GovInfoSecurity]
CISA critical sector RTA: CISA has published the results and recommendations of a red team assessment (RTA) against a US critical infrastructure organization.
"Within this assessment, the red team (also referred to as 'the team') gained initial access through a web shell left from a third party's previous security assessment. The red team proceeded to move through the demilitarized zone (DMZ) and into the network to fully compromise the organization's domain and several sensitive business system (SBS) targets. The assessed organization discovered evidence of the red team's initial activity but failed to act promptly regarding the malicious network traffic through its DMZ or challenge much of the red team's presence in the organization's Windows environment."
Trump's cyber team emerges: The Record looks at early signs of who may end up being on Trump's cyber team next year.
China's secret data trade: Underground data traders are recruiting insiders at Chinese state surveillance agencies and using their access to sell all kinds of personal information. Security firm SpyCloud says it found ads from at least three data traders that are recruiting Chinese government workers. The ads promise to pay from $1,500 to $10,000/day for access to their government accounts. SpyCloud researchers say they were able to retrieve troves of information on Chinese nationals charged in the US for cyber crimes. [Additional coverage in WIRED]
Latvia against spyware: The Latvian government plans to issue a formal statement against the use and proliferation of spyware. [Coverage in Baltic Times]
Africa's technology reliance: The African Center for Strategic Studies warns in a new report that the continent's overreliance on Chinese and US technology is putting governments at risk of hacks and supply chain risks. The report encourages states to cultivate a local tech sector to prevent overreliance on possible future adversary states.
Japan's digital end-of-life planning: Japan's national consumer affairs agency has advised citizens to create end-of-life plans for their digital assets. The agency has urged citizens to look at ways of leaving usernames and passwords to family and friends after they pass on. Citizens are also advised to write down lists of online subscriptions so that family members can cancel them and avoid incurring further costs.
Pakistan is first to block BlueSky: After a phenomenal surge in new users, BlueSky has received its first country-level block, and the winner is Pakistan.
Thailand throws out NSO lawsuit: A Thai court has dismissed an activist's lawsuit against Israeli spyware vendor NSO Group. Jatupat Boonpattararaksa sued NSO in September claiming that the company's Pegasus spyware was used to infect his smartphone in June and July 2021. The court dismissed the case claiming that Jatupat failed to provide sufficient evidence to support his case, even if Amnesty International filed an amicus brief in support.
Risky Business Podcasts
In this podcast, Tom Uren and Patrick Gray talk about what the People's Liberation Army cyber operators have been up to. They used to be China's most visible cyber operators but have since disappeared.
Arrests, cybercrime, and threat intel
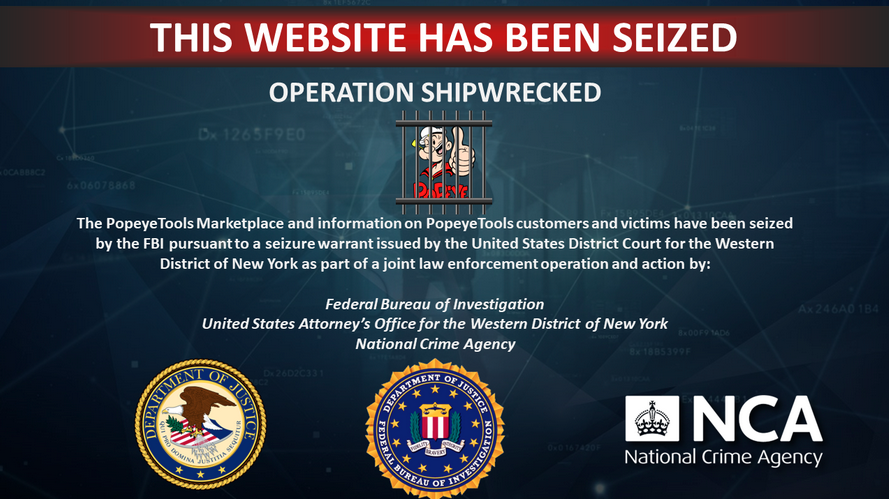
PopeyeTools takedown: US authorities have seized PopeyeTools, a notorious marketplace that sold access to stolen credit card information and hacking tools. Officials have seized PopeyeTools domains, seized cryptocurrency accounts, and indicted the site's administrators. Charges were unsealed against two Pakistani citizens and an Afghan national. The DOJ says the site made at least $1.7 million in revenue since launching in 2016.
US charges 247TVStream admins: The DOJ has unsealed charges against two brothers for operating the 247TVStream illegal streaming portal.
Scam compounds reach the UAE: Social media giant Meta says it has taken down over two million Facebook and Instagram accounts this year that were used in online cyber scams known as pig butchering. The company has been tracking pig-butchering scams since 2022. It initially started following a scam compound in Cambodia and later expanded to track scam centers in Laos and Myanmar. Meta says it also discovered this year what appears to be scam compounds operated out of the United Arab Emirates.
Microsoft seizes ONNX domains: Microsoft's legal team has seized 240 domains used by the ONNX Phishing-as-a-Service operation. The domains were allegedly registered by an Egyptian man named Abanoub Nady. Microsoft says Nady went online as MRxC0DER and was the ONNX main administrator. Microsoft took down the domains with help from the Linux Foundation, which holds the trademark for ONNX, which stands for Open Neural Network Exchange.
NoName057: Threat intel analyst Luc4M has published a report with IOCs and TTPs from the NoName057 pro-Kremlin faketivist group.
"As we noticed tracking the NoName057(16), they evolved their presence in the underground collecting support for thousands of hacktivists actively supporting the Russian regime, and mixing both ideology with economic incentives and reward programs."
Ignoble Scorpius: Palo Alto Networks says they are tracking the BlackSuit ransomware as Ignoble Scorpius, the same name they used for the Royal ransomware gang—because the new ransomware is "a direct continuation" of the old one.
DPRK IT workers use Chinese front companies: A SentinelOne investigation has found that North Korean IT workers are using front companies based in China as part of their attempts to get jobs at Western companies.
Russian bulletproof hosting providers: French security firm Intrinsec has found connections between Russian company PROSPERO (AS200593) and Proton66 (AS198953), another Russian AS believed to be connected to bulletproof services named SecureHost and BEARHOST. These two services are known to host malware operations such as SocGolish, SpyNote, Octo, and GootLoader, along with a hell lot of phishing and C&C servers.
Repo swatting attack hit GitHub and GitLab: Threat actors can abuse a hidden feature to take down GitHub and GitLab accounts in what security researchers call a "repo swatting attack." The technique abuses a feature that allows users to open issues on a targeted repo, upload a malicious file, and then abandon the issue without publishing. On both GitHub and GitLab, the file remains attached to a victim's account. A threat actor can report the hidden, non-public file for breaking Terms of Service and have the repo removed for hosting malware.
Malware technical reports
BianLian ransomware: The FBI says that despite using a Chinese-sounding name, the BianLian ransomware group and multiple of its affiliates operate out of Russia. The agency says the group is part of a recent trend in the ransomware ecosystem where groups try to mislead investigators about their location and nationality by using foreign-language names. Other groups that use foreign-language names but most likely operate out of Russia include the Nokoyawa, Karakurt, and Cuba operations. The FBI says BianLian has also shifted to exclusively exfiltration-based extortion around January this year, abandoning data encryption attacks. [More in the FBI BianLian advisory/PDF]
ElPaco ransomware: CyFirma has spotted a new ransomware strain named ElPaco. Looks to be a variant of the Mimic ransomware and a small operation targeting home users.
Gabagool phishing kit: The TRAC Labs security team has published a technical breakdown of Gabagool, a phishing kit with AitM capabilities. TRAC Labs says it's tracking attacks with the kit against corporate and government employees.
Lumma Stealer: McAfee researchers have published a report on the Lumma Stealer, a quite popular infostealer advertised via shady Telegram channels.
NodeStealer: Netskope researchers look at a NodeStealer campaign seeking to infect and collect data on Facebook advertising accounts.
JarkaStealer: Kaspersky researchers have discovered a supply chain attack on the official PyPI portal that leveraged malicious Python libraries to deploy a new infostealer strain named JarkaStealer. The company says the malicious packages went undetected for over a year but only had over 1,700 downloads. The packages posed as AI chatbot development-related tools.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about how ungoverned spaces on Telegram result in increasingly toxic and antisocial communities.
APTs, cyber-espionage, and info-ops
TAG-110: A Recorded Future report looks at TAG-110's attacks on Asian and European organizations with malware such as CherrySpy and HatVibe.
"The campaign's tactics align with the historical activities of UAC-0063, attributed to Russian APT group BlueDelta (APT28)."
MuddyWater: Sophos says its EDR detected new MuddyWater-linked phishing activity.
Gelsemium's WolfsBane: ESET has uncovered a previously unknown Linux backdoor named WolfsBane the company has linked to the operations of a Chinese APT group it tracks as Gelsemium. ESET says WolfsBane is the Linux counterpart of Gelsevirine, the group's Windows backdoor it has been using for years. The company also discovered a second Linux backdoor named FireWood but has yet to link it to Gelsemium so far.
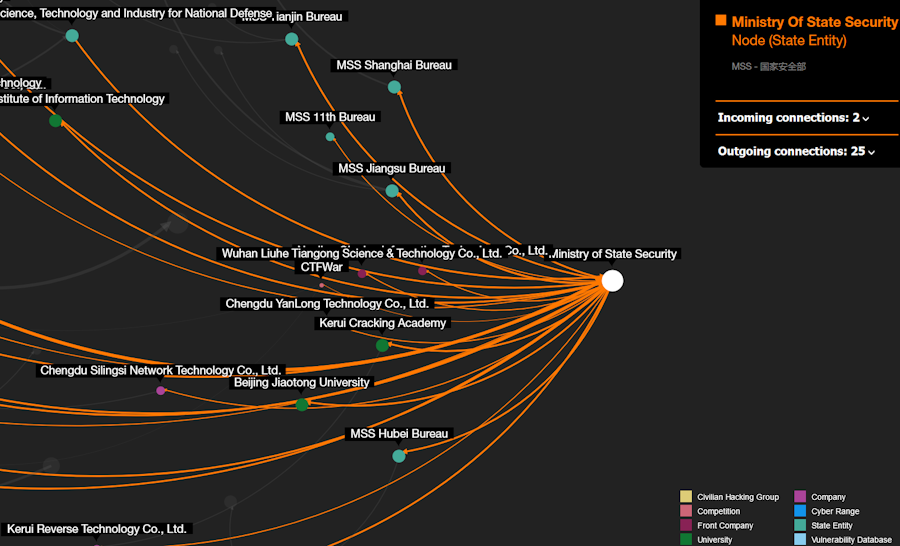
China's cyber landscape: Orange's cybersecurity team has published a report with a top-down look at China's cyber landscape, which covers everything from state agencies to private contractors and local universities. The report also comes with an interactive map.
Vulnerabilities, security research, and bug bounty
Apple fixes macOS zero-days: Apple released security updates this week to fix two zero-days (CVE-2024-44308, CVE-2024-44309) used in attacks against Intel-based macOS systems. The zero-days targeted users through the WebKit browser engine using malicious web content. The attacks were discovered and reported to Apple by Google's TAG security team, which specializes in hunting APT and surveillance vendor operations. Even if the attacks targeted macOS users, Apple has released patches for all its operating systems.
PAN zero-day exploitation: The Shadowserver Foundation has found evidence that at least 2,000 Palo Alto Networks firewalls have been compromised using two recently disclosed zero-days. Compromised firewalls contain a PHP webshell used by attackers for initial access. The number is a conservative estimate since it relies on a limited set of IOCs released by the company last week. Palo Alto warned of a possible zero-day earlier this month. It confirmed attacks last week and released patches this Monday.
Needrestart LPEs: Security firm Qualys has discovered five local privilege escalation (LPE) vulnerabilities in needrestart, a component installed by default on Ubuntu Linux servers. The component works by scanning local services and determining when they need to be restarted. The vulnerabilities can be exploited by unprivileged users to gain full root access without requiring user interaction. The vulnerabilities impact all needrestart versions dating back to April 2014.
7-Zip RCE: The 7-Zip project has released security updates to patch a remote code execution vulnerability discovered in its popular file archiving utility.
"Interaction with this library is required to exploit this vulnerability but attack vectors may vary depending on the implementation. The specific flaw exists within the implementation of Zstandard decompression. The issue results from the lack of proper validation of user-supplied data, which can result in an integer underflow before writing to memory. An attacker can leverage this vulnerability to execute code in the context of the current process."
Bing wormable XSS bug: Security researcher Pedro Jorge Baptista has published a write-up on a now-fixed wormable XSS bug on the main Bing domain.
Wowza vulnerabilities: Rapid7 researchers have identified five security flaws in the Wowza Streaming Engine. The vulnerabilities, all of which are now fixed, could be combined for RCE attacks.
Adobe out-of-band security update: Adobe has released a rare out-of-band security update to patch a memory corruption vulnerability in its Adobe InDesign software. Adobe said it was not aware of any exploits in the wild for the bug.
New OSS-Fuzz discoveries: Google says its AI system discovered 26 new vulnerabilities across open-source projects.
"The reports themselves aren't unusual—we've reported and helped maintainers fix over 11,000 vulnerabilities in the 8 years of the project. But these particular vulnerabilities represent a milestone for automated vulnerability finding: each was found with AI, using AI-generated and enhanced fuzz targets."
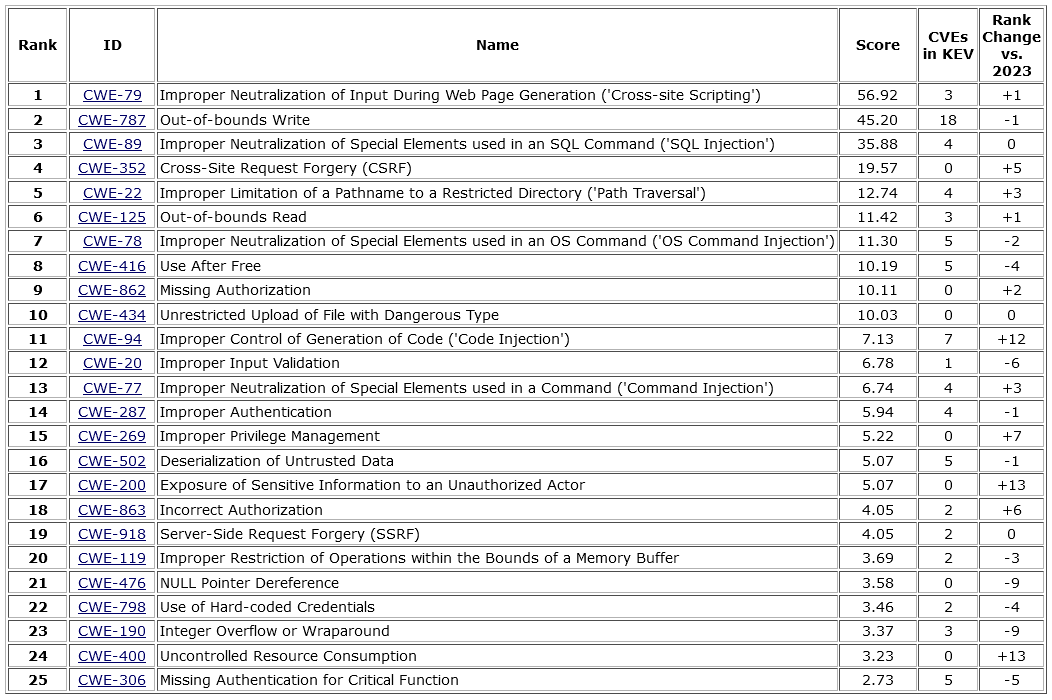
2024's top security weaknesses: MITRE has published its annual list of the top 25 most dangerous software weaknesses (CWEs). Number one was cross-site scripting (XSS), which has returned to the number one spot for the first time since 2020. Last year's number one, use-after-free vulnerabilities, fell to number eight. The Top 25 list was compiled by analyzing over 31,000 vulnerabilities reported over the past year.
Infosec industry
CISO insurance is here: Insurance company Crum & Forster has unveiled a new policy specifically designed to shield CISOs from professional liability. The new coverage is meant to protect executives against claims of negligence or inadequate work linked to their jobs. Such policies have existed but typically have only covered high-ranking executives, such as CEOs, CFOs, and others. The new Crum & Forster policy extends the protections to executives working cyber, fintech, and multimedia roles. [Additional coverage in CyberScoop]
Acquisition news: Israeli cloud security startup Wiz has acquired risk management and remediation company Dazz.
New tool—PanGPA_Extractor: ShellSystems has released PanGPA_Extractor, a tool to extract usernames and passwords in plaintext from Palo Alto Global Protect logs on Windows.
Threat/trend reports: The ASD, Censys, Cloudflare, Corvus, CUJO, Escape, and Trellix have recently published reports and summaries covering various infosec trends and industry threats.