Risky Biz News: URSNIF goes from banking trojan to backdoor, dreaming of ransomware profits
In other news: Microsoft discloses another data breach; Canada's Parliament got hacked; Brazilian police detain Lapsus$ member.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Researchers from security firm Mandiant have reported this week that URSNIF (aka Gozi, or Gozi/IFSB), one of the oldest and last few remaining banking trojan operations that were still active this year, has completely ditched its banking fraud-related features and now appears to operate as a basic backdoor trojan, the type of barebones malware typically used in Access-as-a-Service (AaaS) schemes that rent access to compromised devices.
According to Mandiant, the change took place earlier this year, in June, when URSNIF developers started distributing a new URSNIF version tracked under a codename of LDR4.
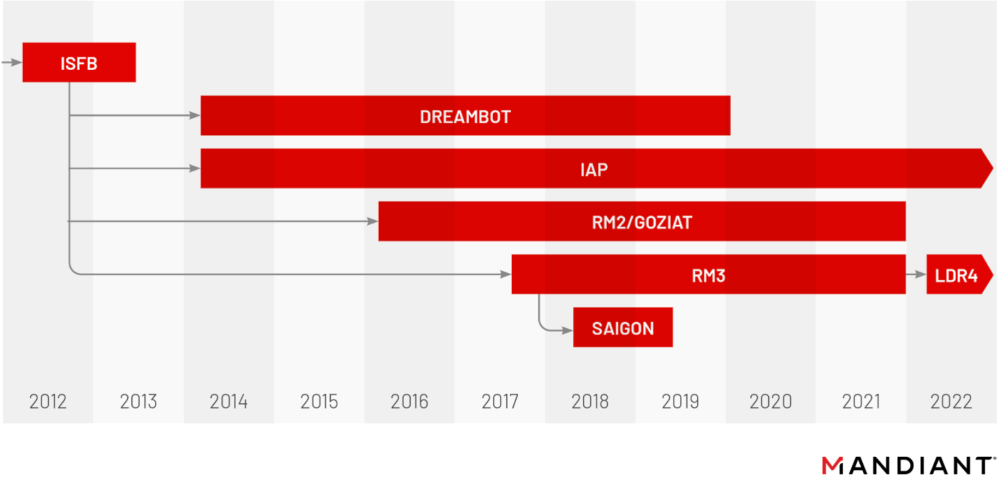
Mandiant cites several reasons for URSNIF's new radical redesign. At least two leaks of its codebase, multiple branches of the same codebase that had slowly diverged and were making it harder to support features across different botnets, but also an ancient codebase that had finally reached the end of the road when IE was removed from Windows.
"In June 2022, with Internet Explorer finally being fully removed from Microsoft Windows, the RM3 variant was officially seen as a "dead" malware from a technical point of view, as RM3 was reliant on this browser for some of its critical network communication."
Honestly, it's a surprise that URSNIF lasted this long still operating on a banking trojan model. It had become obvious in the mid-2010s that the banking malware scene was dying, at least on the desktop.
Banks, tired of a decade of heists from customer accounts, had rolled out advanced multi-factor authentication and transaction verification systems. While not foolproof, these systems did their job and made it more time-consuming for banking malware operators to steal money from compromised accounts.
Today, it's very hard to list a banking trojan off the top of my head and without googling it first.
Emotet and TrickBot converted their codebases from banking trojans to generic modular backdoors back in 2016, being some of the first to do so. Even if they kept their banking modules around, Dridex and Qbot also followed suit in subsequent years.
The driving force behind this shift in malware economics was the rise of ransomware and enterprise network big-game hunting. As ransomware operators realized they could extort an obscene amount of money from companies and government networks, they started to look for ways into these networks.
This initially led to the rise of a market for initial access brokers, smaller threat actors that typically exploited corporate networking and server gear, where they planted backdoors and then sold access to these systems to ransomware gangs and their affiliates.
EvilCorp was the first major botnet operator to realize they could use their banking trojan to drop ransomware inside the thousands of corporate networks they had at their disposal through the Dridex botnet and even launched internal teams to write and deploy their own internal forms of ransomware.
Because Dridex operated on a closed model, providing limited access to their botnet to only a handful of very carefully vetted operators, Emotet, and later TrickBot, cornered the market in MaaS services working with ransomware gangs.
Once law enforcement cracked down on the two, IcedID and Qbot stepped in as handy replacements after years of slowly growing in their shadows.
The world of underground malware is not that hard to understand if we dispel all the CTI mumbo-jumbo and we are really honest. It's all about the minimum amount of work you can perform for the largest profit. Banking/carding is now hard, thanks to banks, and ransomware is easy, thanks to a bazillion reasons.
There are literally no good reasons to run a banking botnet these days, especially one as old and complicated as URSNIF, when you can just manage a simple backdoor, spam bored corporate employees until they infect themselves, and then sell access to ransomware or cryptomining gangs for a cut of the profits.
But enough explaining basic cybercrime economics. What this means going forward for the readers of this newsletter, many of which are most likely tasked with defending networks, is that URSNIF infections now need to be treated with the same urgency as we once used to treat Emotet and Trickbot. Once it's in your network, you need to get it out ASAP, as you never know when that infected system might end up deploying ransomware to your network. If we take stats from previous IR reports, this might be somewhere from 30 minutes and up to an hour. Sure, Mandiant hasn't linked any URSNIF incident with a confirmed ransomware attack, but the writing's on the wall as clear as day.
Breaches and hacks
Microsoft breach: Microsoft confirmed on Wednesday a report from security firm SOCRadar that the OS maker misconfigured one of its cloud servers that eventually leaked the details of some of its business transactions and prospective customers. SOCRadar claimed the data of more than 65,000 customers was exposed as a result of the leaky server, but Microsoft said that "greatly exaggerated the scope of this issue" and that the number was far smaller, including many duplicates. Microsoft also said it was disappointed that SOCRadar released BlueBleed, a tool for users to search and see if their data was exposed in the incident.
Defense Health Agency: The US Defense Health Agency, the agency that provides healthcare services to the US Army, Navy, and Air Force during peace and wartime, has disclosed a security breach that exposed the details of more than 1,200 individuals.
Canada Parliament hack: Canadian Parliament members have been asked to change their email passwords following what officials have described as a "cyber incident." RiskyBizNews understands this is a ransomware attack, although government officials have not yet confirmed the incident as such.
Technoserv hack: The Russian National Republican Army of Russia, an anti-Russian government hacktivist group, took credit for hacking Technoserv, one of the country's largest IT companies and a major government contractor.
Moola Market crypto-heist: A threat actor stole $9 million worth of cryptocurrency from DeFi platform Moola Market, only to return 93% of the funds within hours of the hack as part of a shady deal to "rebrand" the hack as vulnerability research and the 7% of the stolen funds as a bug bounty payment. These types of deals have been widespread in the cryptocurrency ecosystem and are not only bordering on criminality but also making a sham of actual white-hat hacking.
Following today's incident, 93.1% of funds have been returned to the Moola governance multi-sig. We have continued to pause all activity on Moola, and will follow up with the community about next steps, and to safely restart operations of the Moola protocol. (1/2)
— Moola Market 🐮 (@Moola_Market) 11:08 PM ∙ Oct 18, 2022
General tech and privacy
Another TikTok scandal: Forbes reported on Thursday that they obtained documents showing how a Beijing-based team inside Bytedance was planning to use TikTok to monitor the location of some US citizens. The team was created to keep track of TikTok's US employees, but Forbes claims it had also planned to monitor non-employees as well.
Minecraft drama: The developer of the PolyMC launcher app for Minecraft servers has kicked out all his fellow collaborators, citing their "leftist queer ideology." Never a good sign, so if you're a Minecraft gamer, you might want to remove a single-developer-controlled closed app from your system as soon as possible.
LibreOffice, not OpenOffice: Take note, IT departments. OpenOffice has been dead for eight years now.
@WIRED Hi Wired! 👋 Your article mentions OpenOffice, but note that since 2014, virtually all development moved to LibreOffice instead. It's way more up-to-date, with huge compatibility improvements and timely security fixes. And still free and open source: libreoffice.org/discover/libre…
— LibreOffice (@LibreOffice) 6:41 PM ∙ Oct 19, 2022
Government, politics, and policy
Another NSO target: Mexican opposition congressman Agustin Basave Alanis revealed this week that his iPhone was infected with a version of the Pegasus spyware. The official said he was notified by Apple about the incident last November and confirmed the infection with experts from CitizenLab, according to a report from Latin America privacy watchdog R3D.
FBI warning on Emennet Pasargad: The FBI issued a security alert [PDF] on Thursday warning that an Iranian threat actor named Emennet Pasargad might try to sway the upcoming US midterm elections using hack-and-leak techniques the group has been using during operations targeting Israeli organizations over the past two years. The FBI has been keeping an eye on this group after they also tried to meddle in the US 2020 Presidential Election as well.
Russian MP calls for cyberattacks on Ukraine: Alexander Khinshtein, a member of the Russian Parliament, publicly advocated this week for the Russian government to carry out cyberattacks against Ukraine as a preemptive measure to stop theoretical Ukrainian cyberattacks. Someone should tell him this clueless MP about HermeticWiper and all the other wipers that hit Ukraine this year. He might not be aware of what's going on in his own country.
Ukraine dismantles another bot farm: Ukraine's Security Service said it dismantled another Russian bot farm operating inside its borders, inside the city of Dnipro, where a threat actor was running 10,000 fake accounts dispensing Kremlin propaganda across the EU. The operation marks the sixth time Ukrainian officials have gone after Russian bot farms operating inside Ukraine, after similar operations in February (18,000 bots), March (100,000 bots across five bot farms), August (1,000,000 bots), September (7,000 bots), and October (50,000 bots).
Germany fines Telegram: The German government has fined Telegram €5.125 million for failing to create and maintain a system through which users can report illegal content on the platform. The fine applies to fiscal years 2021 and 2022.
No: Just no! This is dumb. Just have a video call, like everyone else.
Erm, Interpol has created a metaverse for police to meet up and get training on hacking/forensics
— Thomas Brewster (@iblametom) 11:37 AM ∙ Oct 20, 2022
Sponsor section
Proofpoint is one of this newsletter's main sponsors. Below is a product demo Patrick Gray, the host of the main Risky Business podcast, recorded with them last year, where they show off Nexus People Risk Explorer, the company's product for mitigating insider threats:
Cybercrime and threat intel
Lapsus$ member detained: The Brazilian Federal Police detained this week a 19-year-old suspect on suspicion of being part of the Lapsus$ cybercrime group. Authorities did not release the teenager's name, but the arrest comes after BFP officials raided eight locations back in August looking for evidence linked to several Lapsus$ attacks against various government agencies and local companies. The teen is also the second Lapsus$ member detained by authorities after another teen was also detained in the UK at the end of September.
SIM swappers sentenced: Two Massachusetts men were sentenced this week to prison for a scheme to steal "OG" social media and cryptocurrency accounts using SIM-swapping attacks. Eric Meiggs, 24, of Brockton, was sentenced to two years and one day in prison, and Declan Harrington, 22, of Beverly, was sentenced to two years and seven days in prison.
Car thieves detained in France: Two car thieves were detained in France last week for stealing Lexus and Toyota cars using a "quick start electronic key" device disguised inside a portable JBL speaker.
WatchDog: After AquaSec researchers reported last month that they'd seen new malware linked to the TeamTNT gang and their infrastructure—a notable event because the TeamTNT gang formally announced their retirement last year—Trend Micro researchers said they believe this new malware might be the work of a threat actor known as WatchDog.
Bjorka profile: DarkOwl researchers have a profile on Bjorka, the threat actor who has been hacking and leaking documents from the network of the Indonesian government, including details related to sensitive cases, like the murder of human rights activists by government officials.
Nested self-extracting RAR: Trustwave researchers have documented a recent malspam technique where spam groups use nested archive files to hide payloads from security solutions, and sometimes, with some exploit chains involving up to three nested files and even the use of password-protected files and self-extracting file formats.
KEV update: CISA has updated its KEV database with two new vulnerabilities that are currently being actively exploited. The two are a recently patched Zimbra zero-day and a 2021 vulnerability patched last year in the Linux kernel.
Supple chain attack figures: DevOps security firm Sonatype said it discovered 97,334 malicious libraries across several programming ecosystems in 2022. The number is up from roughly 12,000 last year, representing nearly 633% in incidents over the course of a calendar year. More in the company's State of the Software Supply Chain report.
Malware technical reports
OldGremlin: Group-IB published a report on OldGremlin, a rare Russian-speaking ransomware gang that has been carrying out attacks within Russia. Group-IB said it linked the gang to at least 16 incidents so far.
"For the second year in a row, OldGremlin demanded the highest ransom from Russian organizations: in 2021 their largest ransom demand amounted to $4.2 million, while in 2022 it soared to $16.9 million. [...] Although OldGremlin mainly targets corporate Windows-based networks, the group's most recent attacks show that their arsenal includes dedicated ransomware for Linux."
Deadbolt ransomware: The same Group-IB team also has a report out on Deadbolt, the ransomware that has been targeting QNAP NAS devices over the past few months.
FUD PS backdoor: SafeBreach researchers published a report on a new undetected PowerShell backdoor.
"The covert self-developed tool and the associated C2 commands seem to be the work of a sophisticated, unknown threat actor who has targeted approximately 100 victims."
Clicker: McAfee researchers have a report out on the Clicker adware, which they said they found in 16 applications hosted on the official Google Play Store, all of which had more than 20 million downloads.
Cuba ransomware: Microsoft's security team said it recently spotted the operators of the Cuba ransomware installing an Avast anti-rootkit driver on compromised networks to elevate privileges and disable local security solutions. BYOVD, to the moooooon!
APTs and cyber-espionage
Domestic Kitten: ESET said it detected a new cyber-espionage campaign carried out by APT-C-50, an Iran-based threat actor. The campaign, which the company named Domestic Kitten, targets Iranian citizens with a new version of the FurBall malware hidden inside an Android translation app.
DiceyF: Kaspersky's GReAT team has published a report this week on DiceyF, an advanced persistent threat actor that has been targeting online casinos and their dev environments across Southeast Asia.
"Our research shows overlap with LuckyStar PlugX, a supply chain incident privately reported. TTPs, secure messaging client abuse, malware, and targeting demonstrate that this set of activity and resources align with Earth Berberoka/GamblingPuppet activity discussed at Botconf 2022 by Trend Micro researchers, also discussed as an unknown or developing cluster by other vendors. Prior to "Operation Earth Berberoka," Trend Micro reported on "Operation DRBControl," which also aligns with this activity and resource set."
Vulnerabilities and bug bounty
FabriXss: Orca Security published a report on CVE-2022-35829, an XSS vulnerability in Microsoft Azure Service Fabric that can allow an attacker to gain full Administrator permissions on the Service Fabric cluster.
"Specifically, the attacker can use a single permission to create a new malicious application and abuse the Administrator permissions to perform various calls and actions. This includes performing a Cluster Node reset, which erases all customized settings such as passwords and security configurations, allowing an attacker to create new passwords and gain full Administrator permissions."
"Won't fix" bug: MDSec researchers have found an unauthenticated SSRF to RCE vulnerability in the Microsoft Office Online Server, which the Redmond-based company said it would not fix as it doesn't meet their regular definition of a security flaw.
Something from my side 😋
— Manish Kishan Tanwar (@IndiShell1046) 2:41 PM ∙ Oct 19, 2022
I found an un-authenticated SSRF bug in "Microsoft Office Online Server" and chained it with ADCS/Shadow credential attack trick to gain Remote code execution on the machine which was hosting "Office Online Server".
PHP filter chains: New research into ways to attack PHP applications.
Hello everyone, I worked on PHP filters chain to understand better how they work and written this article to synthesize what I learned. Hope you enjoy reading it as much as I enjoyed studying this kind of payloads :)
— Remsio (@_remsio_) 6:27 PM ∙ Oct 18, 2022
Infosec industry
New DigiCert CEO: Amit Sinha, the former Zscaler President, has been appointed as the chief executive officer at DigiCert.
HexRays acquisition: A consortium of investors led by Belgium venture capital firm Smartfin has acquired HexRays, the company behind the IDA Pro malware reverse engineering toolkit.
New tool—GUAC: Google open-sourced this week a new tool called GUAC to aggregate software security metadata into a graph database for easier querying.
New tool—SCuBA: The US Cybersecurity and Infrastructure Agency open-sourced a new tool named SCuBa, an assessment tool that verifies if an M365 tenant's configuration conforms to a set of baseline security rules.
New tool—Paranoia: Venafi's Jetstack team has open-sourced a new tool named Paranoia that can analyze and export trust bundles from container images.
Text4Shell scanner: Security firm SilentSignal has created a tool that scans Java applications for Text4Shell, a vulnerability (CVE-2022-42889) in the Apache Commons Text library.




