Risky Biz News: Unauth RCE in OpenSSH—a scary combination of words
In other news: Chinese APT exploits Cisco zero-day; cyber insurance rates go down; malware found in multiple WordPress plugins.

This newsletter is brought to you by Rad Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

There's an unauthenticated remote code execution vulnerability in OpenSSH. We're all gonna d... Nah, I'm kidding! It's actually not as bad as that combination of words makes it seem.
The vulnerability was discovered and disclosed on Monday by security firm Qualys. It is tracked as CVE-2024-6387 and is also known under the name of regreSSHion.
It impacts all OpenSSH versions released since October 2020.
Qualys says the bug is a new version of an older 2006 vulnerability (CVE-2006-5051) after OpenSSH devs accidentally removed an older protection. Technically, all OpenSSH versions before 4.4p1 are also vulnerable to regreSSHion—but if you're using an OpenSSH version from 2006 and earlier, there's a special place in IT hell for you, and you deserve everything bad that's coming.
The bug impacts only OpenSSH running on Linux systems, so that's what? 50 to 75% of the world's servers and IoT devices? Cool, cool!
Qualys says it developed an exploit for 32-bit systems, but one for 64-bit platforms is also theoretically possible.
If successfully exploited, the vulnerability allows attackers to run code on remote systems with root privileges.
However, according to Qualys, exploitation is not trivial. The reason is that regreSSHion is a race condition at its core, which means an attacker's request must "race" an internal function for execution. Triggering (winning a race) usually takes at least 10,000 requests and about four hours—if you're lucky. It may also take days to win a race and exploit a system.
This exploitation complexity makes the bug manageable from a defender's perspective since you can detect attacks as they tend to look like any other brute force. This means stuff like fail2ban, SSHGuard, and other brute-force protections will protect systems until defenders can install a patch.
While Qualys has abstained from releasing a proof-of-concept, some PoCs are already making their way on GitHub and other places, and it's only a matter of time until they're confirmed and refined.
So, get to patchin'!
Breaches, hacks, and security incidents
Guernsey cyberattack: The government of the island of Guernsey has been hit by a cyberattack that locked officials out of their email and Microsoft Teams accounts. The incident took place last week, and officials claim they stopped it before it spread further. The government's IT team has reset passwords for all government employees. Despite the quick response, some government officials have described the IT team's response as "staggeringly incompetent" and "an utter fiasco." [Additional coverage in the BBC]
Patelco breach: The Patelco credit union has shut down operations over the weekend in the aftermath of a security breach. The company suspended transactions and payments while it investigates the cause of the attack. Its ATM network has remained functional. Patelco is the 28th-largest credit union in the US by asset size.
Prudential Financial: Financial service provider Prudential says that hackers stole the personal information of more than 2.5 million customers. The breach took place in February this year and was claimed by the now-defunct AlphV ransomware gang. Prudential is one of the world's largest financial companies and part of the Fortune 500.
Shoe Zone breach: UK footwear retail store Shoe Zone has disclosed a security breach.
TeamViewer breach update: TeamViewer has updated its recent data breach notification to add that hackers stole a "copy employee directory data, i.e. names, corporate contact information, and encrypted employee passwords for our internal corporate IT environment." The company previously attributed the hack to Russian cyber-espionage group APT29.
General tech and privacy
EU Temu&Shein investigation: The EU has launched a formal investigation into Chinese shopping apps Temu and Shein. The EU is looking to see if the platforms are tracking children and if they implemented ways for users to report illegal products. [Additional coverage in Yahoo News]
Grindr fine: A Norwegian court has ordered dating app Grindr to pay €5.6 million for sharing its users' dating data with advertisers.
Pixel PSA: There's a bug in Google Pixel 6 phones that will brick the device after a factory reset. [Additional coverage in Tech-Issues Today]
Government, politics, and policy
Supreme Court Chevron ruling: CybersecurityDive takes a look at how the US Supreme Court's recent overturn of the Chevron doctrine may impact cybersecurity regulations.
Poland investigates PAP hacks: Polish prosecutors are investigating a suspected Russian cyberattack on the country’s state news agency. Russian hackers breached the Polish Press Agency (PAP) in late May and published two fake stories claiming the Polish government was calling up 200,000 men for military service in Ukraine. Polish prosecutors are looking to identify the attackers and press charges. The offense is punishable by eight years in prison. [Additional coverage in Polskie Radio]
Russia launches YouTube clone: The Russian government launched this week Платформа (Platforma), a clone of the YouTube video-hosting platform but without all the "Western censorship" and "anti-Russian rhetoric." According to Meduza, the platform also lacks any content and viewers.
China introduces border device checks: Chinese border authorities have received the authority to search the electronic devices of foreigners entering the country. The new rules were approved last year on the grounds of national security and have entered into effect this week. Border authorities can now search smartphones, laptops, and other devices and collect emails, pictures, and videos. The searches can be carried out in cases of emergency and without warrants. The new rules have triggered a wave of warnings among China's neighbors, which are advising travelers not to take their devices when traveling to the country. [Additional coverage in Kyodo News]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Jimmy Mesta, CTO and Co-Founder of Rad Security (formerly KSOC). Jimmy explains how Rad Security has replaced signature-based detections with a new concept the company calls "behavioral fingerprints" or "verified runtime fingerprints," which can detect malicious activity in cloud environments using a wider set of indicators.

Cybercrime and threat intel
Dutch phisher case: Dutch officials are seeking a one-year prison sentence for a man who developed and sold phishing panels.
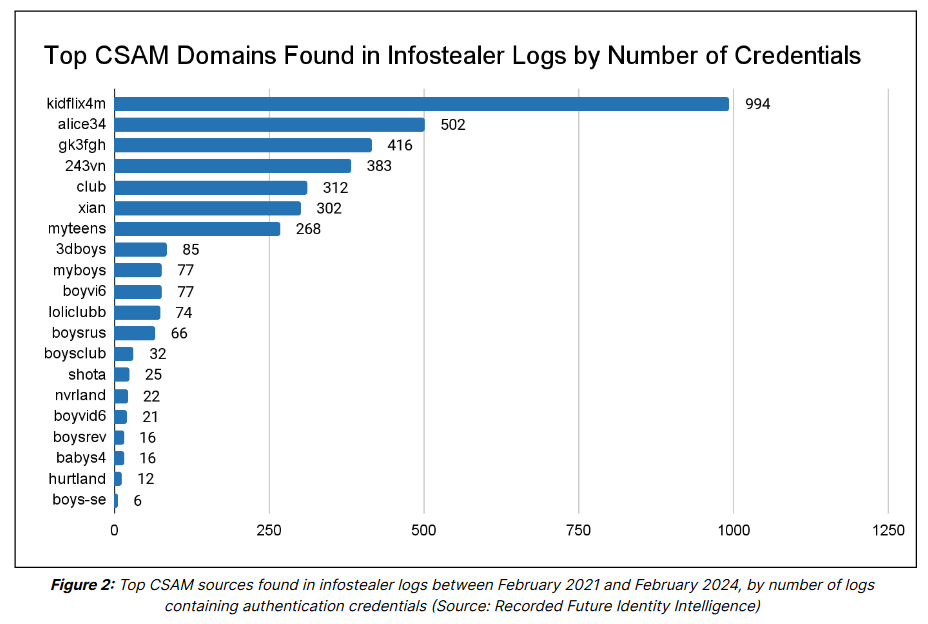
CSAM indetification technique: Security firm Recorded Future has identified thousands of credentials for CSAM websites in infostealer logs sold on the dark web. The company says that most of the credentials are for users based in Brazil. Recorded Future argues that the data can be used to identify and detain visitors of CSAM portals and other abusive sites. The company says it already forwarded its current material to law enforcement for further action.
WP repo supply chain attack: A threat actor has gained access and added malicious code to at least eight plugins on the official WordPress repository. The hijacked plugins create new admin users and insert SEO spam and cryptominers into infected sites. The plugins are installed on more than 100,000 sites. Security firm Wordfence says the attacker gained access to the plugins by guessing the developer's password on the WordPress portal.
ReaverBits: Russia security firm FACCT has discovered a new threat actor named ReaverBits that is currently attacking Russian companies. The group has been active since December 2023 and has relied on spear-phishing operations.
RafelRAT: Zimperium warns of a new Android remote access trojan named RafelRAT being advertised on underground cybercrime forums. No other technical details.
Election spam: Proofpoint reports a three-times jump in US election-related email spam this year compared to the 2022 Midterms.
Threat/trend reports: Arete IR, Dr.Web [desktop], Dr.Web [mobile], Dragos, OVH, Positive Technologies, Sophos, Trend Micro, and Uptycs have recently published reports covering infosec industry threats and trends.

Malware technical reports
Orcinius: Sonicwall has published a report on the Orcinius trojan.
Volcano Demon: Halcyon researchers have discovered a new ransomware operator named Volcano Demon that is currently distributing versions of the LukaLocker ransomware. Halcyon says the group engages in targeted ransomware attacks but does not operate a dedicated dark web leak site. The group is also known for calling a company's executives to extort and negotiate payments.
FakeBat: Sekoia has published a report on FakeBat, a popular malware loader used this year by multiple cybercrime crews for their drive-by download operations. The malware is also known as BatLoader and has been sold as a Loader-as-a-Service on the Exploit forum since late 2022.
Xeno RAT: Hunt.io has taken a look at Xeno RAT, a remote access trojan often linked to DPRK APT ops.
Poseidon: Malwarebytes has discovered Poseidon, a new macOS infostealer distributed via malicious Google ads.
"The macOS stealer being dropped in this latest campaign is actively being developed as an Atomic Stealer competitor, with a large part of its code base being the same as its predecessor. Malwarebytes was previously tracking this payload as OSX.RodStealer, in reference to its author, Rodrigo4. The threat actor rebranded the new project ‘Poseidon’ and added a few new features such as looting VPN configurations."

Sponsor Section
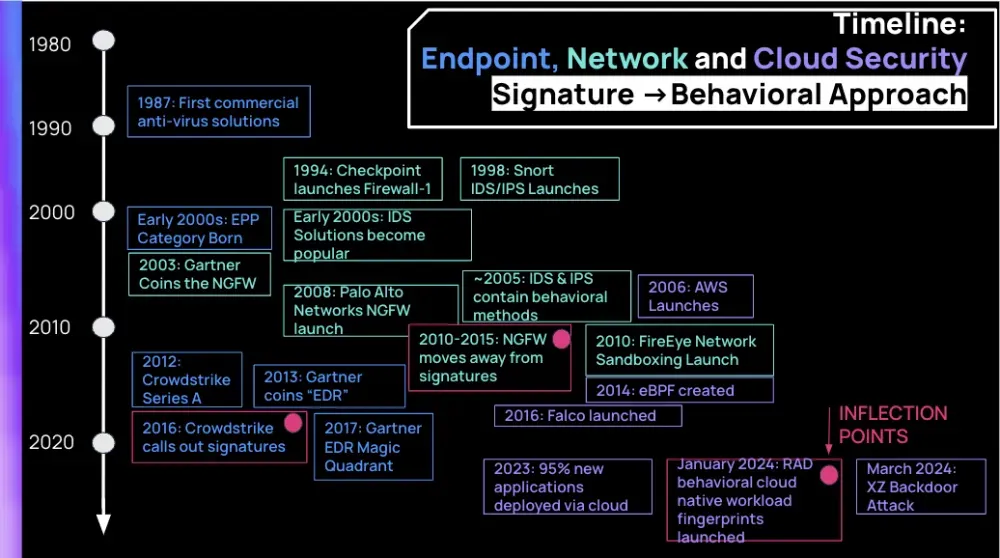
This week's sponsor, Rad Security, takes a look at how security products have evolved from older signature-based detection technologies to a more modern behavioral-based approach over the past decade.
APTs, cyber-espionage, and info-ops
Andariel's Xctdoor: AhnLab has published a breakdown of Xctdoor, a new backdoor used by the Andariel North Korean APT group.
Transparent Tribe: SentinelOne looks at Transparent Tribe's recent operations, which involved planting the CapraRAT in Android apps mimicking popular video browsing applications—with a focus on mobile gamers, weapons enthusiasts, and TikTok fans.
Velvet Ant's Cisco zero-day: A Chinese APT group named Velvet Ant has exploited a zero-day in Cisco Nexus switches in attacks that took place this year. Cisco released patches for the zero-day (CVE-2024-20399) this week after being notified of the attacks by security firm Sygnia. The company described the attacks as very targeted since the zero-day required knowledge of the device's admin password to exploit. Sygnia says the same group also abused F5 BIG-IP appliances as part of a campaign that started at the end of last year.
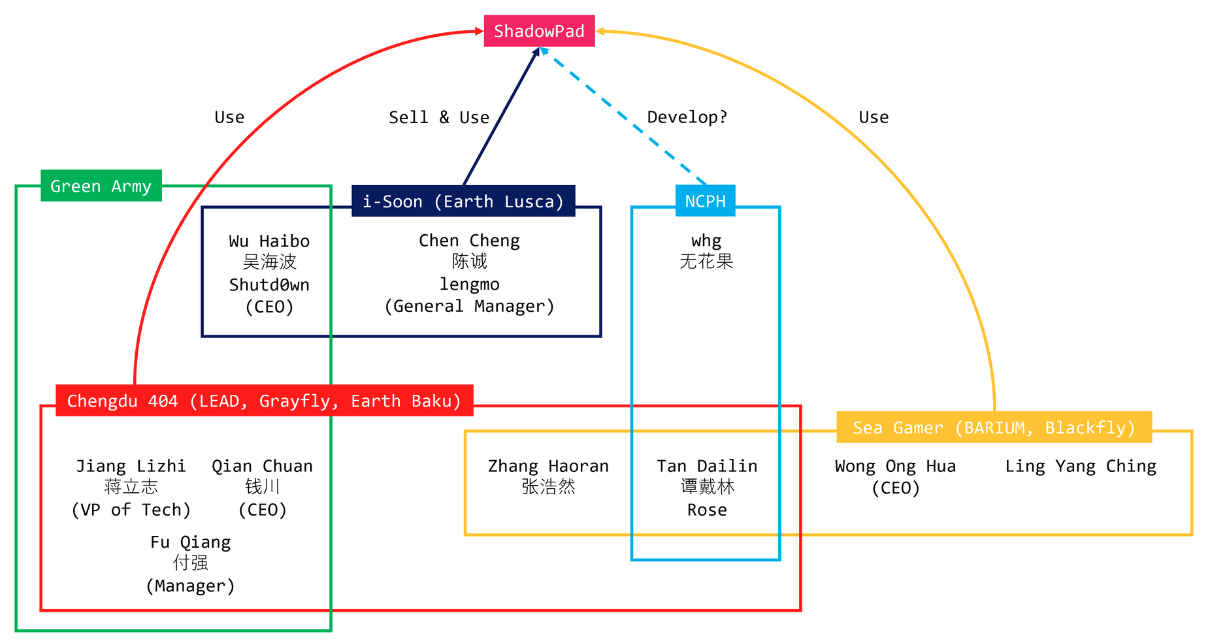
ShadowPad: NaoSec has published a detailed write-up on a leaked ShadowPad builder that has offered some insights into who developed the malware, to whom they're selling, and who is using it.
Vulnerabilities, security research, and bug bounty
Windows EoP PoC: An infosec researcher has published a PoC for CVE-2024-30088, an EoP vulnerability in the Windows kernel that was patched last month.
Docassemble vulnerability: Tanto researchers have found an unauth path traversal vulnerability (CVE-2024-27292) in the Docassemble, an open-source document assembly.
Mailcow vulnerabilities: SecureLayer7 researchers have found two vulnerabilities in the Mailcow open-source email server. The issues include an XSS in the admin panel and a path traversal vulnerability. [h/t ScreamingGoat]
PanelView vulnerabilities: Microsoft researchers have found two vulnerabilities in Rockwell's PanelView Plus HMI graphic terminals. The two are unauth RCE and DoS issues.
CocoaPods vulnerabilities: Security firm EVA has discovered vulnerabilities in the CocoaPods package repository used in the iOS and macOS ecosystems. The vulnerabilities could have allowed threat actors to hijack developer accounts with no interaction, claim ownership over orphaned pods, and even take over the central CocoaPods "trunk" server. EVA says the issues could have been used to orchestrate supply chain attacks on more than three million iOS and macOS apps that rely on CocoaPods libraries. The vulnerabilities affected CocoaPods for over 10 years and were fixed last October.
Indirector attack: A team of academics from the University of California, San Diego, have discovered a new speculative attack impacting high-end Intel CPUs. Named Indirector, the attack can be used to leak sensitive data from Intel Raptor Lake and Alder Lake CPUs. Intel says previous mitigations for attacks like Spectre and Meltdown also apply for Indirector, but with a considerable performance hit.
PgC attack: Security researcher Can Bölük has developed PgC, a new technique for disabling the Windows Kernel Patch Protection (KPP), aka PatchGuard.
Monzo vulnerabilities: Security firm FortBridge has published details about several issues in Monzo's mobile banking app.
Android Security Bulletin: Android security updates for July 2024 are out. The Pixel security bulletin was late and wasn't up when we wrote this. It will go live at this URL.
Splunk security updates: Cisco has patched 18 security flaws in its Splunk SIEM product.
Apache HTTPD security updates: The Apache Web Server Project has published a security update to fix eight new vulnerabilities. Seven of the issues were found by security researcher Orange Tsai. He will cover five in an upcoming Black Hat USA talk.
Infosec industry
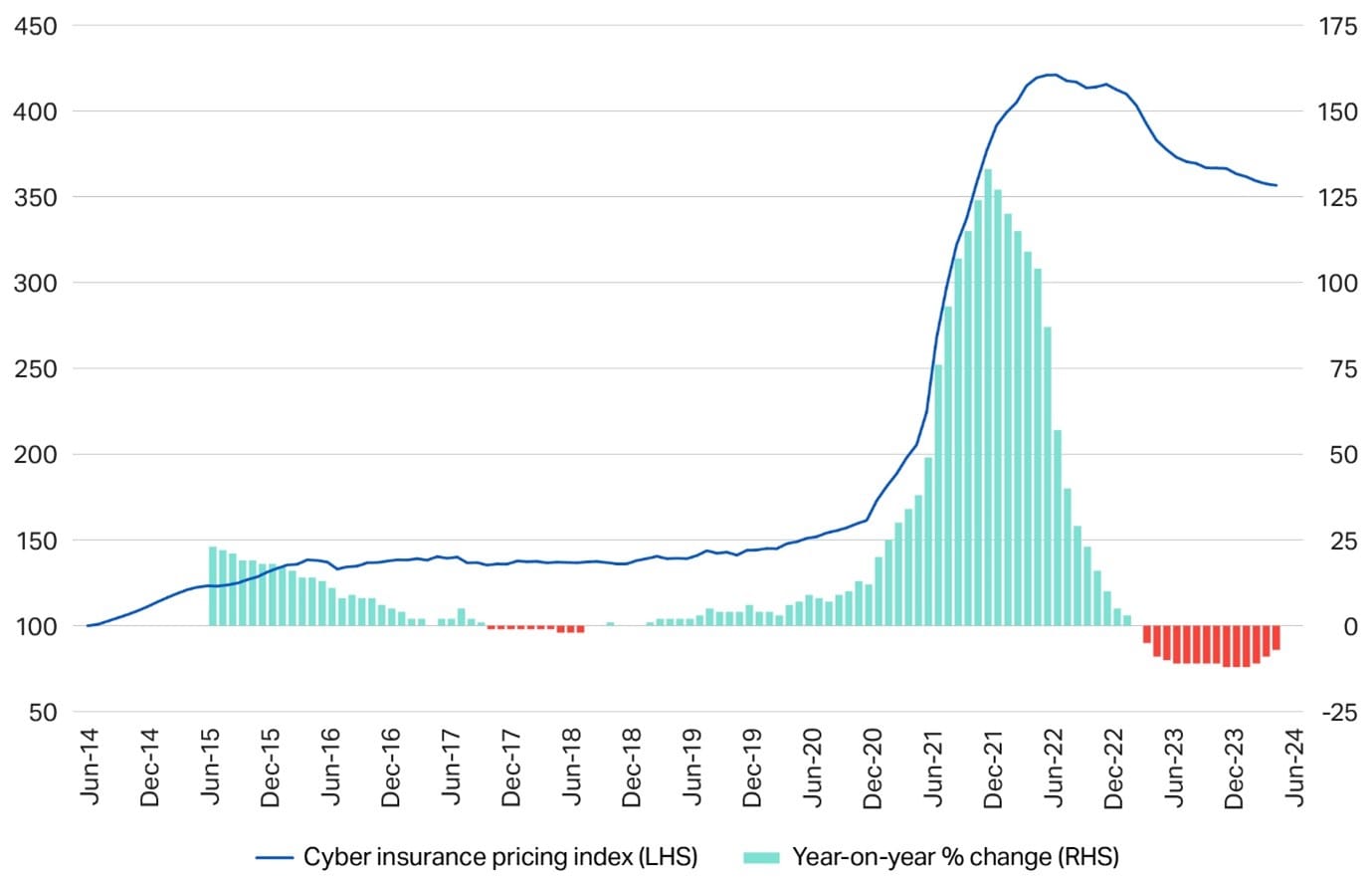
Cyber insurance rates go down: Cyber insurance rates have fallen over the past year as companies have gotten better at securing their networks. Cyber insurance broker Howden says cyber insurance prices are down 15% from their 2022 peak. Howden says companies are flocking to get cyber insurance due to a rise in ransomware attacks. Prices have also gone down as more carriers and brokers have entered the market and are now willing to offer cyber insurance coverage. Howden predicts the market will reach $43 billion by 2030 as cyber insurance coverage grows outside the US. Currently, the US accounts for two-thirds of the global market. [Additional coverage in Insurance Business Mag and Reuters]
New CEO: Deepwatch has appointed John DiLullo as its new CEO. He replaces retiring Charlie Thomas.
New tool—RemoteKrbRelay: Russian security firm CICADA8 has published RemoteKrbRelay, a tool to execute KrbRelay and KrbRelayUp attacks remotely.
IRISSCON 2023 videos: Talks from the IRISSCON 2023 cybercrime conference, which took place earlier last November, are available on YouTube.
PancakesCon 5 videos: Talks from the PancakesCon 5 security conference, which took place in March, are now available on YouTube.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about why governments have failed to protect the private sector from state-backed cyber espionage.
In this podcast, Tom Uren and Patrick Gray talk about a new report [PDF] that explores how China's vulnerability discovery and research ecosystem is linked to state-sponsored espionage. This research finds that a relatively small number of people are responsible for an outsized contribution to vulnerability discovery. They also talk about difficulties at CISA's Joint Cyber Defence Collaborative initiative and why it should be retired.
Abhishek Agrawal is the CEO and co-founder of Material Security, an email security company that locks down cloud email archives. Attackers have been raiding mailspools since hacking has existed, and with those mailspools now in the cloud with services like o365 and Google Workspace, guess where the attackers are going?




