Risky Biz News: Ukraine jams Russian satellite TV stations in occupied territories
In other news: AWS now encrypts S3 data by default; FCC working on new data breach disclosure rules; Turla hijacks old Andromeda botnet to go after Ukrainian targets.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
The Ukrainian government has jammed Russian satellite TV signals to occupied Ukrainian territories since December 2022, according to Chris Greenway, a monitor for BBC Monitoring, a division of the British Broadcasting Corporation that monitors and reports on mass-media activities across the globe.
"Ukraine is uplinking its own multiplex (a "mux") to various Russian satellites, mimicking the mux being uplinked by Russia," Greenway said last week.
"The Ukrainian uplink is much stronger than the Russian one, fooling the Russian satellite into relaying the Ukrainian uplink instead," he added.
Greenway says Ukraine assigned its TV channels on the "fake" mux the same IDs as the Russian ones, which means that terrestrial transmitters in Russian-occupied regions of Ukraine had been tricked into relaying its channels instead of the Russian ones.
The BBC expert says this trick has allowed Ukrainian officials to broadcast messages inside occupied territories, such as President Zelenskyi's recent New Year address, often on the frequency of Rossiya 1 (Russia 1), Russia's main state-owned TV and radio network.

In a Telegram post, Alexander Malkevich, the General Director of the St Petersburg TV Channel, blamed the incident on... and I kid you not... "Anglo-Saxon IT terrorists from Ukraine... whatever that means.
Greenway says that since the disruptions, Russian TV stations have constantly been changing their satellite signal configurations in an effort to outrun Ukraine's jamming.
The incident marks the most successful jamming and hijacking of Russian TV broadcasts inside occupied territories after Ukrainian IT specialists also hijacked Russian TV stations in September and August last year as well.
Breaches and hacks
Chick-fil-A security incident: Fast-food restaurant chain Chick-fil-A says it's investigating suspicious activity on a number of customer accounts. The incident appears to be a generic credential stuffing attack that typically targets companies that run loyalty and reward-points programs. These accounts are often hacked and then sold on underground forums. Buyers purchase these accounts and then use the loyalty points to place orders in their name. Several Chick-fil-A users reported on social media having their accounts hacked and emptied of loyalty points in recent weeks, which most likely triggered the company's investigation.
AirFrance-KLM incident: French-Dutch airline company Air France–KLM notified customers last week of a security breach that impacted the account owners of its FlyingBlue loyalty program. In an email sent to affected customers, the company says details such as names, phone numbers, email addresses, and latest transactions were exposed in the incident.
Ray-Ban lawsuit: A US judge has ruled that JPMorgan Chase must face a lawsuit from EssilorLuxottica, the company behind Ray-Ban glasses, after the bank failed to detect and stop suspicious transactions that originated from the eyewear company's New York bank account. EssilorLuxottica lost $272 million in 2019 after hackers recruited one of the company's Thai employees, which then made several rogue transactions to a third-party account. In its lawsuit, EssilorLuxottica claimed that JPMorgan should have detected the sudden spike in its regular monthly transfers jumping from $15 million to $100 million.
General tech and privacy
New AWS defaults: Amazon says that starting January 5 this year, all data stored in AWS S3 servers is now encrypted by default. Server-side data encryption has been available to S3 customers since 2011, but the feature has only been optional until now. Amazon also plans to change another AWS default in April, when all new S3 servers will block access to stored data by default. Until now, all AWS S3 servers were open to public access unless administrators took intentional steps to set the servers private.
WhatsApp gets proxy support: Meta has announced support for proxy connections in its WhatsApp service. The company says the new feature will prove useful for users who want to bypass censorship in oppressive regimes. Besides that, it can also be used to bypass firewalls in corporate environments too. (wink-wink)
Apple fined in France: CNIL, France's privacy watchdog, has fined Apple €8 million for showing targeted ads to French users. The agency says that Apple did not obtain explicit consent from users to have their data harvested and used for targeted ads, a clear violation of the EU's GDPR rules.
Louisiana porn law: A new law has entered into effect in the US state of Louisiana where any website where more than a third of its content is adult-related must perform age verification of its visitors. This has led to some websites, such as PornHub, requiring Louisiana residents to verify themselves using a government-issued ID, such as a driver's license.
Government, politics, and policy
FCC working on new data breach rules: The US Federal Communications Commission is updating the data breach reporting rules for US telecommunications providers. According to the proposed rules, carriers that suffer a security breach will be mandated to immediately notify federal agencies of any intrusion. This includes notifying the FBI, Secret Service, and the FCC itself. The new rules also mandate that carriers immediately notify customers; unless otherwise advised by authorities. The FCC's current data breach notification rules allow carriers to sit on a breach between seven and 30 days before disclosing the incident. This is generally considered harmful as it can allow intruders to weaponize and sell the stolen information. [Additional coverage in TeleCompetitor]
DDoS attack on Danish Army: Pro-Russian hacktivists carried out DDoS attacks on the websites of the Danish Army last month. Exemplifying just how unimportant and unimpactful these attacks really are, it took Danish officials four hours to spot the attacks (because nobody actually cares if you DDoS a generic website) and another 11 hours to block them.
Cyber-attacks on Moldova: STISC, Moldova's cybersecurity agency, has put out a warning about a massive phishing campaign that is currently targeting owners of Moldovan .md web domains with an "expired domain" lure. The campaign got the agency's attention after the attackers spammed more than 1,300 government email inboxes that were being used to manage official government websites.
Wikipedia's Saudi Arabia scandal: Reports from two human rights organizations and The Guardian claim that the Saudi Arabian government infiltrated the Wikipedia editorial staff as part of a concerted effort to control the site's content. These admins supposedly promoted positive content about the government and deleted critical items, such as information about human rights abuses and political prisoners. The Saudi agents also allegedly helped identify at least two Saudi citizens who edited the site with critical content, individuals who were later detained and sentenced to heavy prison sentences. The reports come after Wikipedia banned 16 users in its MENA region last month. The two NGOs criticized Wikipedia for its generic announcement and for not revealing any kind of details about the incident, which contrasts with the high level of transparency the organization showcased in past cases. In a statement last week, after the case got media attention, Wikipedia again refused to disclose details about the ban, said the reports contained "many material inaccuracies," and played dumb by claiming they don't know "where these volunteers actually reside."
Sponsor section
RunZero is one of this newsletter's four main supporters and this week's featured sponsor. The company's main product is its network discovery and asset inventory platform, which can be used to find any managed and unmanaged assets inside a customer's network. To learn more, please check out this runZero product demo below:
Cybercrime and threat intel
Rogue Dutch govt employee: Dutch prosecutors are seeking a three-year prison sentence for a former employee of the Dutch Tax and Administration service. Investigators say the suspect used his access to government systems to search sensitive information for cash. Officials say the suspect searched and shared information for license plate numbers, social security numbers, home addresses, if an individual had kids, or where the individual's parents lived. The suspect allegedly charged €10,000 per search, and authorities seized €920,000 from their Amsterdam home following their arrest.
Ransomware investigation: Florida prosecutors are investigating if a former school superintendent and two other former IT administrators broke the law when they used undisclosed details from a March 2021 ransomware attack against the Broward school district, their former employer, as part of their business sales pitches.
MegaCortex decrypter: Romanian antivirus maker Bitdefender has published a decrypter for the MegaCortex ransomware that will allow past victims to recover their encrypted files without paying the ransom.
NSO update: The management of five companies linked to NSO activities has recently moved from Luxembourg to London, UK.
C&C server list: Security researcher Rohit Bansal has published a list of 82 command and control servers for the Rhadamanthys infostealer.
eBPF malware usage: Security firm Red Canary has a breakdown of how the eBPF (extended Berkeley Packet Filter) networking utility is being used by Linux malware strains.
Mac ransomware: Microsoft (out of all people) has a breakdown of the most common techniques used by Mac ransomware.
Mac malware of 2022: More than half of the 13 new macOS malware strains discovered last year are believed to be the work of Chinese state-sponsored hacking crews. According to macOS malware researchers Patrick Wardle, this includes strains such as the Rshell backdoor, the Alchimist malware framework, the DazzleSpy spyware, the oRAT trojan, and the SysJoker backdoor.
New ransomware: Fortinet has a report on new ransomware families that have been spotted in the wild over the past few weeks. This includes the like of Monti, BlackHunt, and Putin (not that Putin).
Automated Libra's PurpleUrchin: Palo Alto Networks says they've spotted a threat actor named Automated Libra engage in freejacking, a type of attack against cloud hosting companies where threat actors sign up for accounts in order to host cryptomining apps on high-power cloud servers. Palo Alto Networks says the group employed a "play and run" tactic where they registered accounts using stolen identities and then disappeared when the cloud vendor's bills came due. Researchers say this campaign, which they named PurpleUrchin, began in November 2022 and involved more than 130,000 automatically-registered accounts on services such as Heroku, Togglebox, GitHub, and others.
Malware technical reports
Dridex update: Trend Micro researchers say they spotted a version of the Dridex malware that was designed to target macOS systems. The sample was first spotted in the wild in 2019 but was never effective, as its final payload was a Windows executable that would crash on macOS systems. Trend Micro warns that despite this, the malware is one update away from being fully macOS-compatible.
poweRAT: DevSecOps security firm has published a report on poweRAT, a new remote access trojan that was distributed via malicious Python libraries uploaded on the official PyPI portal at the end of last year. Six malicious libraries were found to contain the malware, and what stood out about this threat was its use of the Cloudflare Tunnel tunneling service to bypass local firewalls and exfiltrate stolen information (such as browser data and stored secret tokens/keys).
BlueBottle: Broadcom's Symantec security team has a technical report on the techniques used by the BlueBottle threat actor. This is the same threat actor known as OPERA1ER, responsible for the theft of more than $11 million from banks in French-speaking countries across Africa.
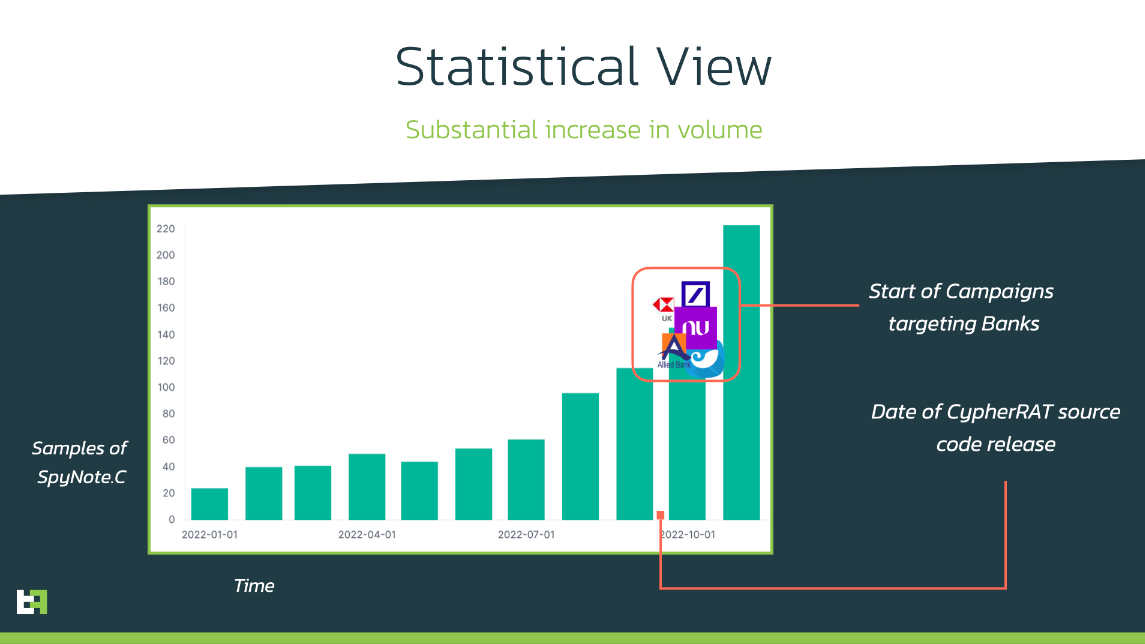
SpyNote leak: ThreatFabric researchers say they've recorded a spike in detections for the SpyNote (SpyMax) Android trojan in the last quarter of 2022. Researchers linked the sudden spike in detections to CypherRAT, a custom-made version of SpyNote that had been sold via a Telegram channel since the summer of 2021. ThreatFabric says CypherRAT's author decided to abandon the project to work on a new Android remote access trojan named CraxsRat, and uploaded the CypherRAT source code on GitHub in October last year before making the switch.
APTs and cyber-espionage
BlindEagle APT: CheckPoint has a report out on Blind Eagle (APT-C-36), a dual financial and cyber-espionage APT group that has targeted various countries across South America since 2018. The report covers the group's most recent operations that have targeted organizations in Ecuador.
Rattlesnake APT: Chinese security researchers have put out a report on Rattlesnake, an Indian APT also known as SideWinder, and a recent operation that took place in November 2022 and targeted Chinese universities.
Saaiwc Group: Researchers with the Anheng Information Hunting Lab have published a report detailing the activities of a new APT they named Saaiwc Group. This campaign targeted military and financial departments in the Philippines, Cambodia, and Vietnam.
Kimsuky APT: Antiy's security team has a report out on attacks carried out by the Kimsuky North Korean APT group against South Korean organizations. The report focuses on the group's Android malware arsenal, specifically on malware known as FastFire, FastViewer, and FastSpy—previously covered in an S2W Talon report.
Cold River APT: Reuters reports that Russian cyber-espionage group Cold River (aka Callisto) has targeted three nuclear research laboratories in the United States between August and September last year, just as Russian officials were escalating their nuclear threats. Targeted entities included the Brookhaven, Argonne, and Lawrence Livermore National Laboratories. Reuters also says the group made multiple OpSec mistakes in recent years, which allowed security researchers to identify one of its members as Andrey Korinets, a 35-year-old IT worker and bodybuilder from the Russian city of Syktyvkar.
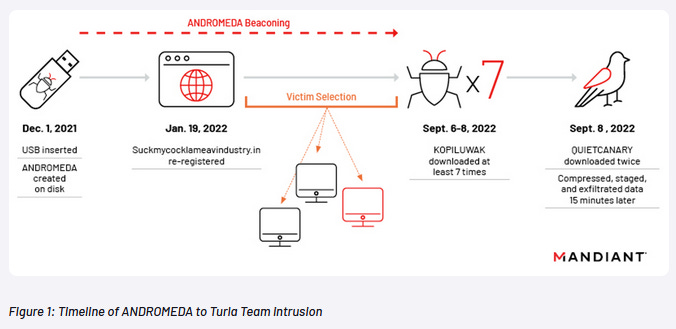
Turla APT: In a report published last week, Mandiant says that Russian cyber-espionage group Turla has hijacked the command and control (C&C) servers of an old Andromeda botnet in order to sift through its compromised hosts and cherry-pick systems of an intelligence and espionage value. Mandiant says that while the botnet had been live since 2013 and had infected systems all over the world, they only observed Turla deploying their custom malware to systems based in Ukraine. Previous reporting has linked Turla with Russia's FSB intelligence agency. The targeting of Ukrainian-only systems through the Andromeda botnet hijack fits into the FSB's supporting role in Russia's invasion of Ukraine. Mandiant says Turla hijacked the botnet by registering a C&C domain that had expired in previous years.
Vulnerabilities and bug bounty
ReDoS beg bounties: Trail of Bits researcher William Woodruff argues in a blog post last year that companies would be better off if they ban reports for ReDoS (regular expression denial of service) vulnerabilities in their bug bounty programs as "signal-to-noise ratio on ReDoS reports is unacceptable."
AWS keys on PyPI: Security researcher Tom Forbes says he scanned every package on the PyPI portal and found 57 AWS access keys that were still valid. Some of these keys belonged to entities such as Amazon itself, the Australian government, Intel, and analytics company Terradata.
OWASSRF, TabShell: Viettel Cybersecurity researchers have published details about two vulnerabilities they discovered in Microsoft Exchange servers. The vulnerabilities are publicly known as OWASSRF (CVE-2022-41080) and TabShell (CVE-2022-41076), and the former has already been exploited in the wild.
CVE-2022-43931: Patch your Synology VPN servers. This one is a 10/10 RCE, just the stuff threat actors like.
CVE-2022-47523: Also, patch your Zoho ManageEngine gear for this SQLi bug.
CVE-2022-39947: Also-also, patch your Fortinet ADCs while you're at it too. There's a nasty OS command injection vulnerability, but, probably not that bad as it's a post-auth issue only.
Infosec industry
New tool—Hardeneks: Amazon's AWS division has open-sourced a tool named Hardeneks that can scan AWS Elastic Kubernetes Service (EKS) instances and see if servers follow recommended best practices.
Risky Business podcast host Patrick Gray recorded this video with Okta, which shows users how to enable phishing-resistant authentication. It also goes into how enabling phishing-resistant auth for some users can benefit the whole org, even if it's not turned on everywhere.




