Risky Biz News: UK NCA "on its knees," bleeding staff, seriously underpaid
In other news: Poland's Pegasus inquiry reaches a roadblock; Americans lost $5.6 billion to crypto-fraud last year; US arrests Terrorgram admins.

This newsletter is brought to you by Sublime Security, an email security platform that's not a black box. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

A UK anti-corruption organization has published a report this week warning that the UK's top police investigative body—the UK National Crime Agency (NCA)—is close to a critical collapse, describing it's current state as "on its knees."
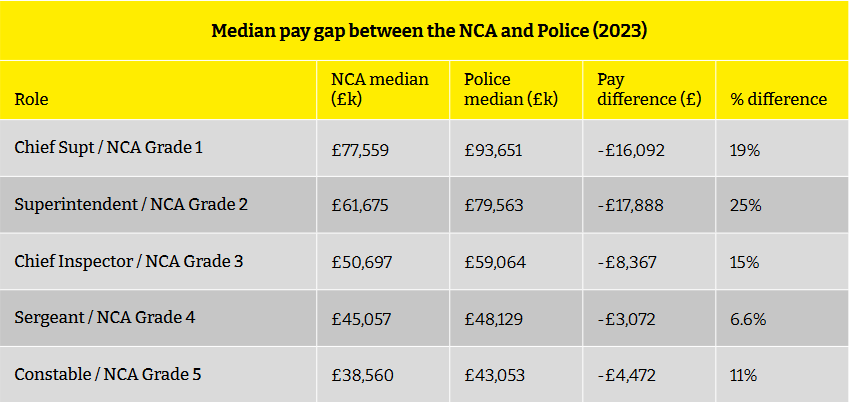
According to the Spotlight on Corruption, the NCA is dealing with huge staff turnover, recruitment issues, and chronically low pay. The study's results are below:
- NCA spend on temporary staff and consultants has risen by an alarming 369% since 2015/16 and by 58% in the last three years alone.
- 9% of NCA roles are unfilled due to recruitment issues – more than double the average of 3.9% for the public sector and higher than the 4.8% in the voluntary sector.
- Despite a 7% pay award last year, NCA officers' median pay has dropped by 16.3% in real terms since 2013/14, when the agency was established. The proposed 5% pay award for this year still leaves officers with a 13.9% real terms pay cut compared to over a decade ago.
- The NCA faces a major brain drain with a quarter of senior managers leaving annually, and the agency loses a third of its legal expertise annually.
- The NCA faces potential equal pay claims of around £200 million due to its unequal pay structures.
- 59% of NCA officers are stuck at the bottom of their pay range with no chance of pay or career progression.
Eleven years after its creation, the study highlights the agency's stagnation and the lack of attention and reform from the British government.
Salaries aren't just below what the median UK police officer or government employee makes, but the NCA's top officers barely earn over what an FBI starting agent makes.
Spotlight on Corruption says the NCA is at a pivotal moment, and the government needs to step in with an "urgent pay reform."
The government also needs to reform the NCA's legal organizational status to insulate it from budget freezes and cuts, which it currently risks as a civil service department under the Home Office.
And last, the NCA also needs a tech capability uplift to keep track with its cyber-related responsibilities. This includes an increasing number of responsibilities and cases dealing with CSAM, cyber attacks, and online fraud.
While the NCA has had a few successes in the form of disrupting cyber operations like Lockbit, OTP Agency, DDoS services, and several malware botnets, the report warns the NCA may soon fall behind to Europol and FBI capabilities in the near future.
Breaches, hacks, and security incidents
Highline cyberattack: One of Seattle's largest school districts closed all schools this week after it fell victim to a cyberattack over the weekend. The shutdown impacted the first day of kindergarten and the second week of school at all Highline Public Schools. The school district said it couldn't dispatch school transportation, hold athletic activities, and school meetings. The incident is suspected of being a ransomware attack and the school is investigating if any student or staff data was stolen. [h/t James Sanders]
SIDN leak: The Netherlands' national registry, SIDN, says it exposed the identity of domain name holders via WHOIS queries. The leak took place on Monday and was fixed in a few hours.
SlimCD breach: Payments processor SlimCD has disclosed a security breach that exposed the personal data of almost 1.7 million users. The breach took place in August of last year and went undetected until June this year. SlimCD says the hackers managed to gain access to a system from where they intercepted customer names, credit card numbers, card expiration dates, and home addresses.
General tech and privacy
Wix leaves Russia: Website hosting platform Wix is leaving the Russian market and will block all Russian accounts on September 12, this week. All website owners have been instructed to move their domains to a new web host. The ban does not apply to non-resident Russians living overseas. The company cited new Western sanctions imposed in response to Russia's invasion of Ukraine. Wix joins other major tech companies that have pulled this year from Russia, such as Microsoft, Google, HP, and Slack.
Firefox extends Windows 7 support: Mozilla has extended support for Firefox on older versions of Windows and macOS until March 2025. Support for Windows 7, Windows 8, and macOS 12 through 14 was supposed to end this month. Mozilla developers say they're considering extending support for these older operating systems indefinitely.
Unicode update: Unicode 16.0 is out with more than 5,100 characters, including almost 4,000 Egyptian Hieroglyphs.
Ford seeks new car-spying patent: Ford Motors has applied for a new patent for technology designed to serve ads based on conversations taking place inside a car. [Additional coverage in The Record]
Government, politics, and policy
Poland dismantles hacker group: In a press conference this week, the Polish government says it dismantled a group of "cyber saboteurs" working for Russian and Belarusian services. Officials say the group engaged in hacks and extortion campaigns targeting Polish individuals and government agencies. The group was allegedly responsible for hacking and leaking data from Poland's anti-doping agency last month. No arrests were announced, and it's unclear what "disruptions" the Polish government took. Officials said that Poland saw more cyberattacks in the first half of the year than all of 2023 combined. [English coverage in Notes from Poland]
Poland's Pegasus inquiry meets a roadblock: The Polish Supreme Court has ruled that a parliamentary commission established to investigate the previous regime's abuse of the Pegasus spyware is unconstitutional. The Supreme Court ruled on the matter after a petition from the Law and Justice (PiS), which led the previous government. It is also the party that named most of the judges on the Supreme Court. The head of the Pegasus commission told reporters they already knew what the Supreme Court's ruling would be even before it was published. Since PiS lost its re-election last year, the Supreme Court constantly ruled against the current government's reforms. Courts in Poland and the EU found that three of the Supreme Court judges have been appointed illegally, including one judge who served as a PiS member. [Additional coverage in Gazeta.pl/English coverage in Notes from Poland]
Australia to introduce minimum age for social media: The ruling Australian party says it will introduce legislation later this year to enforce a minimum age for access to social media apps. The minimum age was not announced.
Russian firewall costs: Russia's communications watchdog Roskomnadzor plans to spend close to $650 million over the next five years to upgrade its internet traffic censorship systems. The agency hopes the new investments will help block 96% of all VPN traffic by 2030. The improved system will also be designed to protect against DDoS attacks. [Additional coverage in Forbes Russia/ English coverage in Bloomberg]
Billington Cybersecurity Summit: Anne Neuberger and Harry Coker's talk from the Billington Cybersecurity Summit last week is now live.
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Josh Kamdjou, founder and CEO of Sublime Security, about the spectrum of attacks that are taking advantage of generative AI. These range from taking basic attacks with a pinch of AI pixie dust to more complex attacks where AI is used to construct message threads with multiple personas. Josh also talks about how different AI models can be used to identify these attacks, even when they are novel.

Cybercrime and threat intel
Sextortion gang charged: The US has charged four Delaware residents for their role in an international sextortion scheme that targeted young men and minors across Canada, the US, and the UK. The group's members posted as women and lured victims to send sexually explicit images or videos. They then extorted victims for money by threatening the share the photos with family, co-workers, and friends. Officials say the group made almost $2 million from CashApp and Apple Pay payments alone. Two members of the gang were detained in April this year, one in the US and a second in the Ivory Coast.
Terrorgram leaders arrested: The US has arrested and charged two suspects for running a Telegram channel named Terrorgram. The channel served as a meeting spot where violent white supremacist groups ordered murders, physical attacks and hate crimes. US officials say Terrorgram was used to organize a shooting at an LGBTQ bar in Slovakia and the stabbing of five people near a mosque in Turkey. The channel was also allegedly used to solicit the murder of US federal officials and plan attacks against energy facilities in New Jersey. If convicted of all charges, the two suspects face maximum penalties of up to 220 years in prison each. Terrorgram is the second online harassment community disrupted this month after German officials took down NWO last week.
CosmicBeetle gang: A threat actor known as CosmicBeetle has splintered off from the RansomHub operation and has now launched its own ransomware service named ScRansom (also known as NoName). Security firm ESET says the group has been active since 2020 and has previously worked as an affiliate for multiple ransomware operations. Its new ScRansom platform is built on previously leaked ransomware code and primarily focuses on SMBs in Europe and Asia. ESET says that although CosmicBeetle has launched its own RaaS platform, it still observed the group deploy the RansomHub encrypter together with its own ransomware.
Scattered Spider: EcleticIQ looks at recent Scattered Spider operations targeting cloud services and then pivoting to local networks to deploy ransomware.
Threats to think tanks: France's cybersecurity agency has published a report on the threats French think tanks can expect in the current cyber landscape.
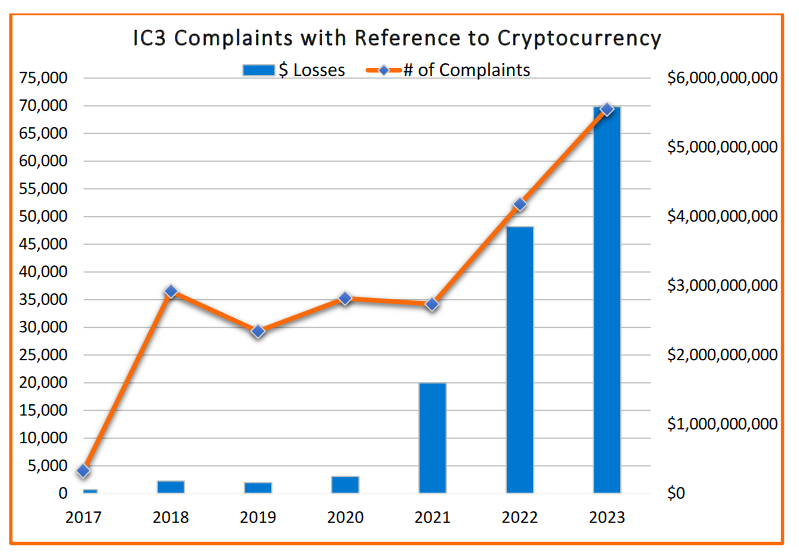
2023 crypto fraud numbers: The FBI says Americans lost over $5.6 billion to cryptocurrency-related fraud last year. Most of the funds were lost to cryptocurrency investment scams, which accounted for half the complaints and almost $4 billion in losses. The FBI says that while crypto-related complaints represent only 10% of the total number of financial fraud complaints, losses account for 50% of total fraud losses.
Malware technical reports
Rust rootkit: Trustwave researchers look at the possibility of developing a rootkit in Rust.
Loki backdoor: Kaspersky has published a report on Loki, a new backdoor the company discovered in July that appears to be a modified version of the Mythic agent, an open-source red team framework.
Quad7 botnet: Sekoia has published a report on the ever-evolving and ever-growing Quad7 (7777) botnet.
"The Quad7 botnet operators seem to be compromising several brands of SOHO routers and VPN appliances, including TP-LINK, Zyxel, Asus, Axentra, D-Link, and Netgear, using multiple vulnerabilities—some of which are previously unknown. The Quad7 botnet operators appear to be evolving their toolset, introducing a new backdoor and exploring new protocols, with the aim of enhancing stealth and evading the tracking capabilities of their operational relay boxes (ORBs). Given these developments, it is possible that without interception capabilities, tracking the evolution of Quad7 botnets could become nearly impossible in the near future."
CryptBot: Intezer researchers have published an analysis of CryptBot, and more specifically, a variant they're calling Yet Another Silly Stealer (YASS)—itself delivered through a novel multi-stage downloader that we are calling MustardSandwich.
BLX Stealer: CyFirma researchers published this week a report on BLX Stealer, a new infostealer also known as XLABB Stealer. These things are like mushrooms after a rain these days.
Ailurophile Stealer: ThreatMon has published a report on the new Ailurophile Stealer.
Cicada3301 RaaS: Security firms Palo Alto Networks, Morphisec, and Truesec are warning that a new threat actor named Cicada3301 has set up a Ransomware-as-a-Service platform and is now actively and aggressively recruiting new affiliates in the cybercrime underground. The group launched in late May this year and appears to reuse code from the AlphV and Nokoyawa ransomware gangs. Cicada3301 has already listed over 20 victims, but security researchers expect the gang's activity to increase in the coming months.
Hazard ransomware bug: GuidePoint security researchers have identified a bug in the Hazard ransomware that blocks files from being decrypted in the event of a victim's payment. Researchers say the flaw corrupts files when encryption operations run too closely to each other within a second. GuidePoint says it found a way to fix the bug but warns victims not to pay the attackers.
RansomHub abuses Kaspersky tool: The RansomHub ransomware group is abusing a legitimate Kaspersky anti-malware tool to disable security products as part of its recent attacks. Malwarebytes says the group is now deploying TDSSKiller, a tool Kaspersky released in the early 2010s to remove rootkits from infected PCs. The tool has the ability to remove almost any process and has been used against EDR products in the past. This marks the first time it's been abused by a ransomware gang.
Sponsor Section
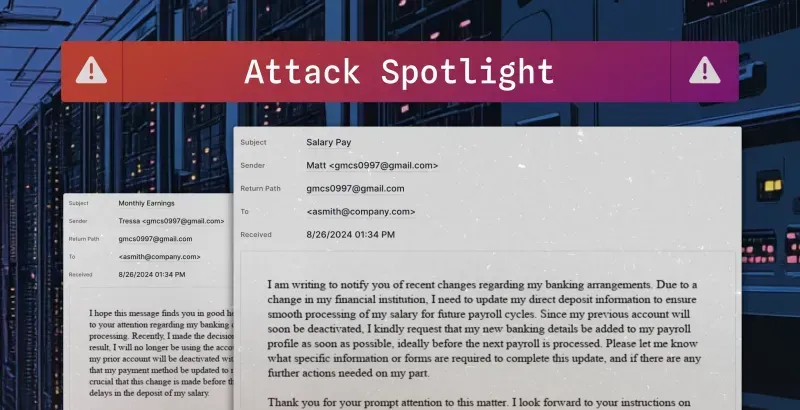
Sublime Security shares a recent payroll fraud campaign, likely produced using generative AI.
APTs, cyber-espionage, and info-ops
US election misinformation: A WaPo report looks at how Musk is behind a plethora of misleading election claims that are being used to harass and pressure US local election officials.
Iranian info-op: The Foundation for the Defense of Democracies has discovered 19 websites that are part of an Iranian influence operation. The websites criticized Israel, the US, and Saudi Arabia while praising Iranian terrorist proxies Hamas, Hezbollah, and the Houthi rebels. Of the 19, one focused solely on glorifying Persian history.
Crimson Palace: Sophos looks at a new Crimson Palace campaign that hit "a prominent agency within the government of a Southeast Asian nation." This is a suspected Chinese APT the company discovered back in June.
Earth Preta: Trend Micro reports seeing an increase in sophistication and the malware arsenal of Chinese APT group Earth Preta (aka Mustang Panda). Most of these new tools are being deployed in campaigns targeting government entities, the military, police, foreign affairs agencies, welfare, the executive branch, and education in the APAC region.
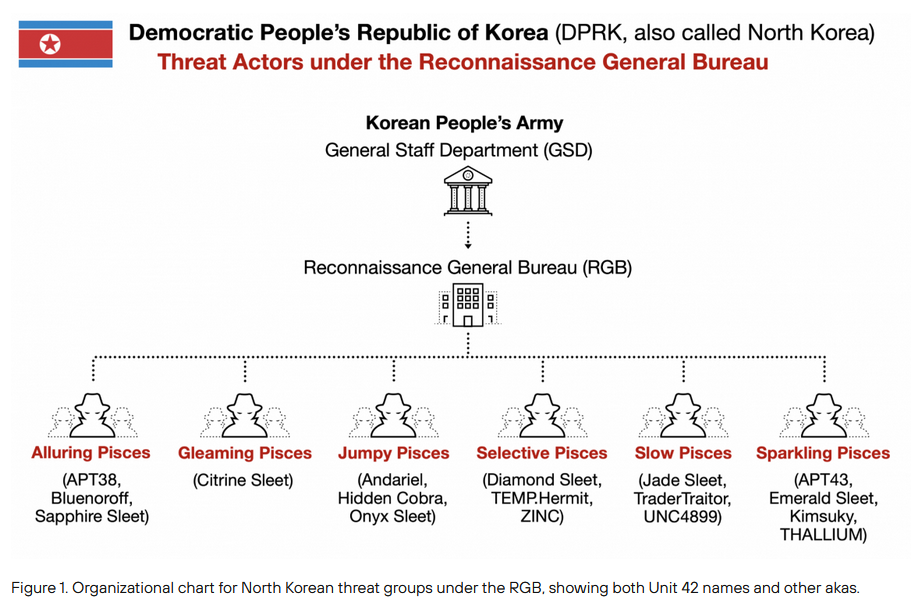
DPRK APTs: Palo Alto Networks looks at the links and connections between all the North Korean APTs and their malware arsenal.
Vulnerabilities, security research, and bug bounty
SonicWall attacks linked to Akira ransomware: In our last edition, we featured an item about attacks in the wild on SonicWall firewalls using a recently patched vulnerability (CVE-2024-40766). According to ArcticWolf, it's the Akira ransomware gang.
KEV update: CISA has updated its KEV database with three vulnerabilities that are currently exploited in the wild. One of them is the SonicWall from above, while the other two are a 2017 Linux bug and a 2016 ImageMagick one.
Patch Tuesday: Yesterday was the September 2024 Patch Tuesday. We had security updates from Adobe, Microsoft, Ivanti, Fortinet, Intel, SAP, Citrix, Kubernetes, Schneider Electric, Siemens, Zyxel, and Zoom. The Android Project, Chrome, Firefox, VMware, Cisco, Kemp, QNAP, Veeam, and Elastic released security updates last week as well.
Microsoft Patch Tuesday: This month, Microsoft patched 79 vulnerabilities, including four actively exploited zero-days.
- CVE-2024-38014 - Windows Installer Elevation of Privilege (via SEC Consult).
- CVE-2024-38217 - Windows Mark of the Web Security Feature Bypass (via Elastic)
- CVE-2024-38226 - Microsoft Publisher Security Feature Bypass
- CVE-2024-43491 - Microsoft Windows Update Remote Code Execution (via an anonymous reporter)
Past Windows zero-day: Core Security has published an analysis of CVE-2024-30051, a zero-day in the Windows Desktop Windows Manager that was exploited by the Qakbot botnet earlier this year. This was patched back in May.
Veeam analysis: watchTowr Labs has published an analysis of CVE-2024-40711, an unauth RCE in Veeam that was patched last week. This was initially discovered by Code White. This seems bad, and everyone is bracing for active exploitation.
Kakadu vulnerabilities: Google Cloud's security team published a technical analysis of two vulnerabilities they found in Kakadu, a third-party software to support the JPEG 2000 image format.
Gallup XSS: Checkmarks has discovered an XSS vulnerability in the website of the Gallup survey company. Researchers say the bug could have been exploited to disseminate false information and compromise user personal data.
WhatsApp view-once bug: Security researcher Tal Be'ery has discovered a bug in the WhatsApp "View Once" feature. The bug can allow recipients to save or view the message more than once or view it in the WhatsApp web app where the feature is not supported. Be'ery says the bug is already exploited in the wild by some browser extensions. Meta initially declined to patch the bug but has recently told TechCrunch it is now working on a patch.
Infosec industry
Threat/trend reports: Check Point, Databarracks, Google Mandiant, the FBI, NCC Group, Rostelecom, Trustwave, and Zscaler have recently published reports covering infosec industry threats and trends.
New tool—HexForge: Elastic's security team has open-sourced HexForge, an IDA plugin that extends the functionality of the app's assembly and hex view.
New tool—Impacket ZSH Integration: SVA's Daniel has released a version of Impacket that integrates well with the ZSH Unix shell.
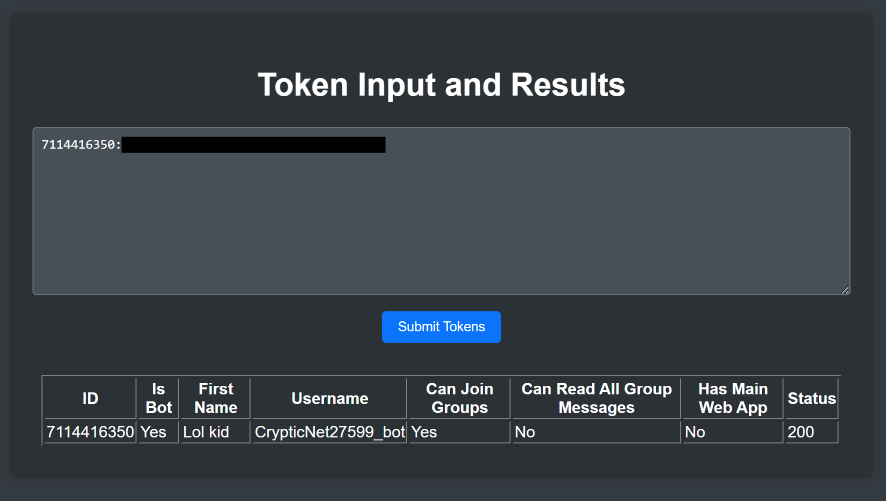
New tool—Teletoken: Threat intel analyst Gi7w0rm has released Teletoken, a tool that returns API info for Telegram bot tokens.
OrangeCon 2024 videos: Videos from the OrangeCon 2024 security conference, which took place last week in Amsterdam, are available on YouTube [Track 1 and Track 2].
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq dissect an FBI advisory about North Korean groups targeting cryptocurrency firms with social engineering.
In this podcast, Tom Uren and Patrick Gray discuss Russia's use of exploits from commercial spyware vendors. Bought through a front or stolen with other bugs? They also discuss Iran's counter-intelligence innovations—if you apply for a job that's very clearly an Israeli front, then perhaps you're not that trustworthy after all?
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!





