Risky Biz News: Two security enhancements coming to Windows (ActiveX, CLFS)
In other news: ColdRiver hacks Russian pro-democracy foundation; backdoor found in EV charger model; sextortionist brothers get long prison time after victim's suicide.

This newsletter is brought to you by Sublime Security, an email security platform that's not a black box. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

Microsoft announced last week two changes to its products designed to boost the company's security posture.
Redmond plans to disable ActiveX in Office apps in October and then harden the Windows CFLS logging service against logic bugs in future versions of Windows 11.
Both are important steps that address some of today's biggest attack surfaces in Windows.
ActiveX, which was added to Windows in the 90s to support interactive content, has often been the target of zero-days from both espionage and cybercrime groups. On top of that, ActiveX controls embedded in Office documents (typically delivered through phishing) have been used to deploy all sorts of malware over the past decades.
This is about to change, though. In a note posted in the Microsoft 365 admin section, Microsoft says that with the launch of Office 2024, ActiveX controls will be disabled by default in Word, Excel, PowerPoint, and Visio.
This new change will take effect for the four Office apps in October, while the Microsoft 365 versions will receive the staggered rollout in April next year.
After those dates, Office users won't be able to create new ActiveX objects, while the old ones will appear as static images. In case you need to keep the feature active or mess with various group policies, CloudScout has a copy of MC884011, the Microsoft Admin Center note that announced the change.
On top of that, Microsoft also announced a change in how the Common Log File System (CLFS) will work in Windows 11.
All logs created on a Windows system will now have a hash added at the end—also known as Hash-based Message Authentication Code (HMAC).
This hash will be computed from the log file's Merkle tree (hash representation of its content) and a secret cryptographic key that can only be accessed by the CLFS service and admin accounts.
The idea behind this change is to prevent threat actors from replacing or editing existing logs to trigger logic bugs in the Windows CLFS log parser.
This has been a big issue for Microsoft, which says that 19 of the 25 CFLS-related vulnerabilities from the past five years have been log parsing logic bugs.
The company hopes this new HMAC feature on CFLS files will help "address a class of vulnerabilities all at once."
This is now being tested in the Windows Insiders Canary release channel and will later be shipped with main Windows 11 installs.
All new installs will have the CLFS driver put into "enforcement mode" and refuse to open files without the HMAC hash.
On existing installs, Microsoft says the CLFS driver will first be put into "learning mode" for 90 days, during which time it hopes the driver will have time to add HMACs to logs before the driver switches to "enforcement mode" as well.
Breaches, hacks, and security incidents
Confidant Health leak: Virtual healthcare provider Confidant Health has exposed a trove of sensitive patient data through a misconfigured database server. The leaked data included patient records, copies of their IDs, as well as audio and video therapy sessions. The data leaked after Confidant failed to set a password for the database. The company secured the server at the end of August after being notified by security researcher Jeremiah Fowler.
Avis data breach: US car rental company Avis has disclosed a data breach stemming from a security breach at the start of August. The company says the attacker gained access to one of its business applications for four days. Avis is the third-largest car rental company in the US by revenue.
Free Russia Foundation hack: One of Russia's largest pro-democracy foundations was hacked and had its email inboxes leaked online. The Free Russia Foundation attributed the attack to ColdRiver, a cyber-espionage group linked to Russia's FSB intelligence service. The foundation says it's one of several entities hacked by the group as part of a recent hack-and-leak operation. The foundation's data was leaked on an anonymous Telegram channel. The leaker encouraged authorities to investigate employees and individuals who donated to the organization. The leaker claimed the files also contained the names of employees working in a pro-Navalny internet troll factory operating in Tbilisi, Georgia—also known as the "elf factory." [Additional coverage in Novaya Gazeta Europe]
General tech and privacy
Durov promises to tackle crime on Telegram: Telegram founder and CEO Pavel Durov has promised to step up efforts to fight crime on the platform after his arrest last month by French authorities. In a post on Telegram following his release, Durov called his arrest "a misguided approach" from law enforcement. He blamed the rise in criminal content on Telegram's sudden growth to 950 million monthly active users. Durov says he made it his "personal goal" to improve Telegram's moderation and collaboration with law enforcement agencies. [Additional coverage in the BBC]
Microsoft removes revenge porn from Bing: Microsoft says it partnered with StopNCII for a pilot program that will use the organization's toolkits to detect and remove non-consensual revenge porn from Bing search results.
YouTube removes TENET channel: Google has removed the TENET Media YouTube channel after the DOJ indictment revealed the organization took money from Russia to publish Kremlin propaganda. [Additional coverage in The Record]
AWS AI opt-out: Amazon has added a one-click option so customers can easily opt-out from all of the company's AI features and services.
Meta inter-app calls: Meta says it's building new tools to let the users of third-party apps join groups or place calls to WhatsApp and Messenger users. The inter-app calling feature is expected in 2027, while support for mixed groups will arrive next year. Meta is building the tools for compliance with the EU's Digital Markets Act, which mandates fair competition in the digital market.
Government, politics, and policy
Cybercrime in Russia: Russians have lost more than $1 billion (91 billion rubles) to cybercrime in the first seven months of the year, according to Russia's Ministry of Internal Affairs. [Additional coverage in Vedomosti]
Malta security research law: The government of Malta plans to update its laws to add protection for white-hat security researchers. The new development comes after four students are still being prosecuted by police just for reporting vulnerabilities in a school app. [Additional coverage in LovinMalta] [h/t DataBreaches.net]
Malaysia backtracks on national DNS plan: Malaysian officials have backtracked on a plan to force local ISPs to redirect all DNS traffic to a government-run DNS system. Officials backtracked a day after announcing the plan after ISPs asked the government to hold a consultation meeting to discuss the topic. The government-run DNS system acts as a simplistic firewall that blocks access to websites the government deems illegal. According to reports, almost 70% of sites on the blocklist are gambling and pornography-related.
White House asks tech companies for help: The White House held a meeting with US tech companies last week to help facilitate access to censorship evasion tools in authoritarian countries. Officials have asked Amazon, Google, Microsoft, and Cloudflare to provide discounted server bandwidth to VPN technologies developed by the US Open Technology Fund. The OTF says that demand for its VPN services has quadrupled in recent years in countries such as Russia, Iran, and Myanmar. [Additional coverage in Reuters]
US drops degree requirements for cyber jobs: Back in May, the White House announced a plan to drop degree requirements for cybersecurity jobs. This program is now live since last week as the Service for America platform.
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Josh Kamdjou, founder and CEO of Sublime Security, about the spectrum of attacks that are taking advantage of generative AI. These range from taking basic attacks with a pinch of AI pixie dust to more complex attacks where AI is used to construct message threads with multiple personas. Josh also talks about how different AI models can be used to identify these attacks even when they are novel.

Cybercrime and threat intel
Sextortionist brothers get long prison sentences: US authorities have sentenced two Nigerian brothers to 210 months in prison each for a sextortion scheme that led to the suicide of a 17-year-old from Michigan. Samuel and Samson Ogoshi bought hacked social media accounts, pretended to be women, and lured victims to send sexually explicit images. The brothers used the images to extort the victims for money by threatening the share the photos with family and friends. The campaign targeted more than 100 victims, 11 of which were minors. Officials tracked down and charged the brothers eight months after one of their victims took his own life in March 2022.
Carder pleads guilty: A New York man pleaded guilty to hacking, money laundering, and trafficking in stolen payment card numbers. Authorities arrested Vitalii Antonenko back in 2019 after finding stolen card data on his computer and media storage devices. Officials say Antonenko was part of a group that used SQL injection attacks to steal card data from online sites and then sell it on underground marketplaces. He'll be sentenced in December and can face up to 20 years in prison.
WWH Club charges: The DOJ has (finally) published the news on the arrest and indictment of the two admins of carding forum WWH Club. We covered this a month ago, so we're not gonna go over it again.
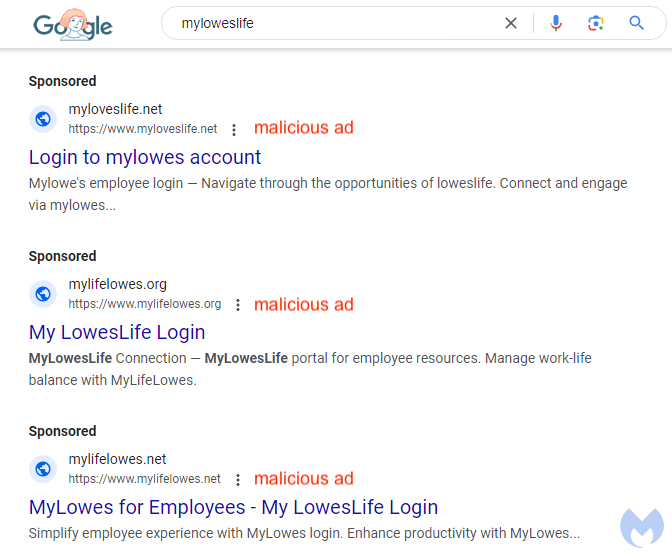
Lowe's malvertising campaign: Malwarebytes has detected a malvertising campaign targeting Lowes employees via Google ads. The campaign showed malicious ads for a search term employees use to find the company's backend portal. The ads were shown at the top of search results and took users to phishing portals.
New sextortion scheme: Users are reporting a new sextortion scheme where they are receiving emails sent to them "by accident." The email is from a fake security firm writing to the user's partner about finding evidence the user has cheated. [Additional coverage in BleepingComputer]
Funeral stream scams: Scammers are creating Facebook groups dedicated to letting users watch a video stream of a friend or family member's funeral service. Users who fall for the trick are sent to a fake video streaming service that tries to collect payment card details. According to cybersecurity reporter Brian Krebs, the scam group operates out of Bangladesh, and this is one of the several types of scams they are currently running.
Operation Uncle Scam: Perception Point researchers look at a phishing campaign using AI tools to target US government contractors.
New npm malware: Seventy-hundred-twelve malicious npm packages were discovered last week. Check out GitHub's security advisory portal for additional details.
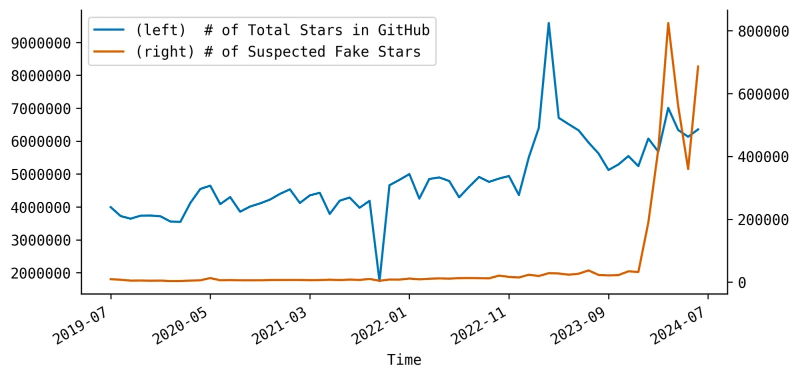
GitHub fake stars: Socket Security has found that more than 10,000 GitHub projects received over 3.7 million fake stars over the past five years. The fake stars were used to boost projects linked to scams and malicious code. GitHub has removed around 89% of projects that received fake stars. Socket says the number of suspected fake stars has rapidly grown over the past six months.
Malware technical reports
Ailurophile Stealer: CyFirma researchers have published a report on Ailurophile Stealer, a new open-source infostealer spotted in the wild.
LummaC2: eSentire has published details about a recent LummaC2 distribution campaign.
AMOS: Sophos researchers look at AMOS (Atomic macOS stealer), today's most popular infostealer used to target Mac users.

Sponsor Section
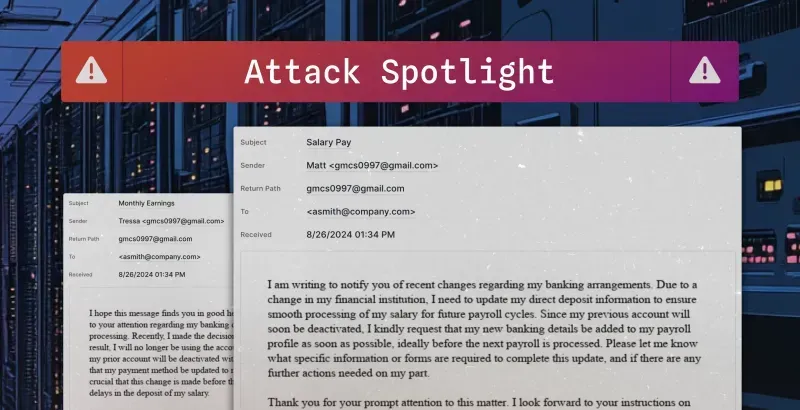
Sublime Security shares a recent payroll fraud campaign, likely produced using generative AI.
APTs, cyber-espionage, and info-ops
US expects info-ops explosion: US intel officials told reporters last week on Friday that they expect China, Iran, and Russia to increase the cadence of their influence operations as the US election gets near. [Additional coverage in CyberScoop/ODNI]
Russian info-ops numbers: Last week, the US charged two RT employees for using an intermediary to pay US influencers to publish pro-Kremlin propaganda. One small detail from that indictment that lots of people missed—including me—was that the FBI said Russia was paying more than 2,800 influencers to publish propaganda, 600 of which are based in the US. That's quite the impressive apparatus. No wonder some Kremlin garbage is trending on Twitter every day. In the meantime, RT has promised to evade sanctions and continue working in the West. RT Editor-in-Chief argued that Western outlets and social media networks should be banned in Russia as a response. [Additional coverage in The Atlantic]

PhantomCore: Russian security firm FACCT has published a report on recent changes in PhantomCore campaigns—an APT the company previously linked to Ukraine.
Librarian Ghouls: Kaspersky says that a new APT group named Librarian Ghouls has been targeting Russia's industrial sector in campaigns this year. The attacks have targeted research institutes, space and rocket companies, and manufacturers of equipment for gas processing, petrochemicals, nuclear power, and the defense industry. Once the group breaches targets, it steals CAD and other technical files, most likely for espionage and IP theft. Kaspersky researchers did not attribute the group to any state.
BlindEagle: Zscaler looks at a June campaign of the BlindEagle APT, which targeted the Colombian insurance sector with a new version of the BlotchyQuasar RAT.
Stately Taurus abuses VSCode: Chinese cyber-spies are abusing a Visual Studio Code feature as an undetectable backdoor on compromised systems. The attackers are abusing a reverse shell feature found in the binary of the official VS Code app. The technique was first discovered and documented by security researcher Truvis Thornton in September of last year. The attacker can abuse a locally installed VS Code app, or they can download and use the VS Code binary without getting detected. Palo Alto Networks has linked the recent attacks to a suspected Chinese APT group named Stately Taurus (aka Mustang Panda, BRONZE PRESIDENT, RedDelta, Luminous Moth, Earth Preta and Camaro Dragon). The security firm says this is the first time they've seen the technique abused in the wild.
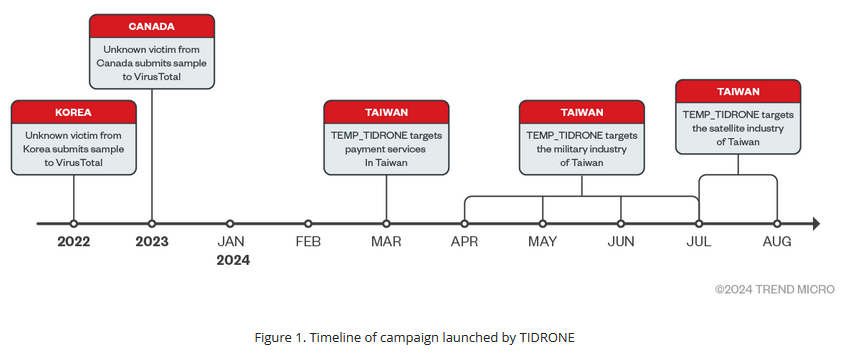
TIDRONE: A Chinese cyber-espionage group is targeting Taiwanese military-related industry chains, and specifically local drone manufacturers. According to Trend Micro, the TIDRONE group has been active since 2022 but refocused operations on Taiwan this year. The group uses ERP software and remote desktops for initial access and its main tools are a downloader named CXCLNT and a remote access trojan named CLNTEND.
Vulnerabilities, security research, and bug bounty
SonicWall firewall exploitation: SonicWall has detected active attacks against its firewalls and VPN systems using a recently patched vulnerability (CVE-2024-40766). The security flaw allows attackers to bypass authentication and access firewall management resources. SonicWall released a patch at the end of August. Organizations that can't install the patch were told to restrict access from the internet to the firewall's management panel.
GeoServer exploitation: Fortinet looks at all the malware payloads dropped through attacks on GeoServer instances. CISA warned of ongoing attacks (via CVE-2024-36401) back in July. Observed malware includes a bunch of coinminers, Condi, Mirai, SideWalk, and GoReverse.
Backdoor feature found in EV charger: Security firm Sector7 says it discovered a backdoor feature in Autel MaxiCharger EV chargers that can grant attackers control over the device. The backdoor is a hard-coded authentication token in the Bluetooth pairing process. Sector7 researchers believe the backdoor token was intentional. The backdoor was one of three security flaws Sector7 researchers found in the device during a hacking contest earlier this year.
Kemp gets a perfect 10: Kemp Technologies has fixed a major vulnerability in its LoadMaster load balancer appliances that can allow threat actors to run malicious code on the device. Tracked as CVE-2024-7591, the vulnerability is an input validation bug in the device's management panel and can allow threat actors to run OS commands. Kemp released a security update last week and encouraged customers to update before the bug gets exploited in the wild. The vulnerability received a perfect severity score of 10/10 due to its ease of exploitation. [h/t ScreamingGoat]
C-MOR vulnerabilities: German security firm SySS has discovered 11 vulnerabilities affecting the C-MOR video surveillance software platform. The security flaws include SQL injection, cross-site scripting, and OS command injection bugs that can be exploited to gain admin access over the platform and disable IP camera video feeds. C-MOR released a patch at the end of July that only fixes six of the reported bugs.
Bing XSS: Security researcher Supakiad S. has discovered an XSS vulnerability on Bing.com by poisoning Bingbot from external websites via Microsoft Bing's Video Indexing System. The researcher received a $3,000 reward for finding the bug.
Linux kernel race condition: Theori researchers have published details about a race condition vulnerability (CVE-2024–27394) they found and helped patch in the Linux kernel in April this year.
QNAP security updates: QNAP has released seven security updates over the weekend to address issues in a bunch of its software.
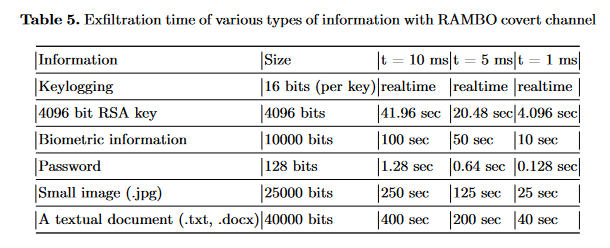
RAMBO attack: A team of academics from Israel has devised a new side-channel attack named RAMBO that uses malicious code running on a machine to make RAM chips emanate electromagnetic radiation that can leak data from air-gapped systems.
Infosec industry
Acquisition news #1: Cybersecurity company Pango is acquiring Kaspersky's US antivirus business. All Kaspersky US users will be moved to Pango's UltraAV. The US Department of Commerce banned Kaspersky from operating in the US in June. The Russian company must exit the US market by September 29. [Additional coverage in Axios]
Acquisition news #2: Absolute Security has acquired Syxsense, an automated endpoint and vulnerability management platform.
New tool—Node.js Security: If you're looking for a new infosec newsletter, check out Liran Tal's Node.js Security.
New tool—PassPort: A German security reporter has released PassPort, a tool to bypass TCP traffic through passkey servers as a way to bypass internet censorship.
Threat/trend reports: Cybernari, CyberCube, Perception Point, and ScamSniffer have recently published reports covering infosec industry threats and trends. Highlights from the CyberCube report:
"The US cyber insurance market could reach up to $45 billion in premiums by 2034, a five-fold increase from today's $8 billion value. In the next 10 years, carriers are also expected to need $121 billion of capital to manage risks. Insurance analytics company CyberCube expects that in the next 10 years cybersecurity to become a primary risk for many insurance categories, such as casualty and property. The company joins Marsh and the Zurich Insurance Group to warn of a looming catastrophic cyber incident. Marsh and Zurich called on governments to help cover some of the risk protection gap."
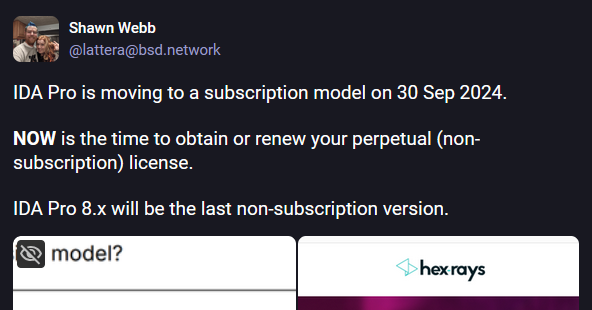
IDA Pro changes licensing model: Hex-Rays is discontinuing its perpetual IDA Pro license and replacing it with a yearly subscription model. The new licensing model will enter into effect on September 30 this year with the release of version 9.0 of IDA Pro.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk to Alex Joske, author of a book about how the Chinese Ministry of State Security (MSS) has shaped Western perceptions of China. They discuss the MSS's position in the Chinese bureaucracy, its increasing role in cyber espionage, its use of contractors, and the PRC's vulnerability disclosure laws.
In this podcast, Tom Uren and Patrick Gray discuss Russia's use of exploits from commercial spyware vendors. Bought through a front or stolen with other bugs? They also discuss Iran's counter-intelligence innovations—if you apply for a job that's very clearly an Israeli front, then perhaps you're not that trustworthy after all?
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!





