Risky Biz News: Twitch limits browser logins as it deals with massive bot attack
In other news: New Chaos botnet spotted in the wild; vulnerability in Stacked VLAN implementations; and new Exchange zero-day.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Live streaming service Twitch dealt with a major bot attack this week and was forced to block logins from exotic browsers to prevent a threat actor from mass-creating new accounts to be used in future hate raids.
According to a developer who creates Twitch-centered software, more than 4 million new accounts were created over the course of roughly 30 hours between late Sunday and early Tuesday this week.
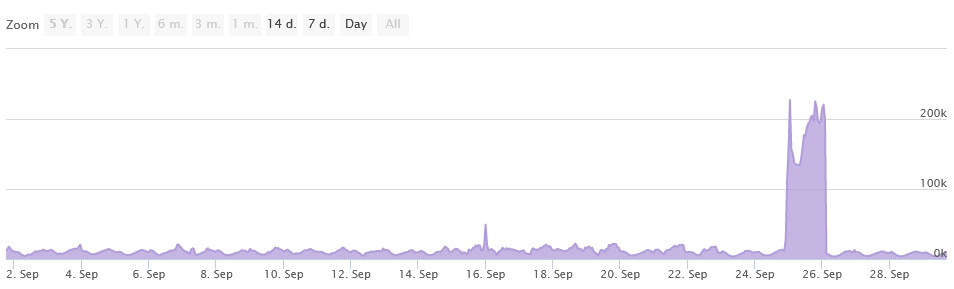
Since such operations are usually carried out with automated tools like headless browsers, Twitch's security team initially responded to the attack by blocking all user logins from all browsers except the very most recent versions of Chrome, Firefox, and Edge, on which most of its "legitimate" userbase would likely be using.
🔧 Seeing an error when logging in? Be sure you are using a supported web browser (Chrome, Firefox, or Edge), and your browser is fully updated!
— Twitch Support (@TwitchSupport) 11:32 PM ∙ Sep 28, 2022
We have a help article to help troubleshoot this coming soon!
"There are organized groups trying to create botnets—bots that end up getting used for hate raids. There was one such mob very active recently," said Twitch chief product officer Tom Verrilli said in a Twitter thread yesterday, trying to explain to users what was happening and why some of them couldn't log in.
"When that happens, we (1) close whatever hole they found, (2) clean up the bot accounts made. Because (1) takes time, we're temporarily restricting log-in to certain browsers," he added.
"I totally appreciate it's a PITA. [...] Unfortunately, this is what the work of making Twitch safe entails. Folks need to use a browser not of their preference today to stop tomorrow's hate raid."
In the meantime, the list of supported browsers has been expanded with both Apple Safari and Opera GX, as Twitch's staff has continued to investigate the root cause of the mass sign-ups and has whitelisted other browsers.
CommanderRoot, the developer who first spotted the bot attack, said that while Twitch failed to detect the attack when it started, the company was quick to intervene and stop it two hours after they first tweeted about it. However, CommanderRoot said that four days after the attack took place, most of the accounts are still not suspended.
You have to give Twitch some credit for stopping the massive bot account creation around 2 hours after I tweeted about it. That makes me wonder. When did Twitch notice it? Did it take a 3rd party like me and community outcry or did they have alerts setup?
— CommanderRoot (@CommanderRoot) 8:24 PM ∙ Sep 29, 2022
Breaches and hacks
Kazakhtelecom DDOS: Kazakhtelecom, Kazakhstan's national telecom provider, said it suffered a massive DDoS attack from "abroad" locations at the end of last week.
BXH hacked twice: DeFi cryptocurrency platform BXH was hacked twice over the past week, according to blockchain security firm SlowMist. The first incident took place on September 23, and the company lost $2.5 million worth of BXH tokens after one of the developers' private keys was stolen. The second incident took place on September 27, and the company lost $40,085 during a flash loan attack.
FastCompany hacked: News media outlet FastCompany said that a threat actor hacked its CMS on Tuesday and sent out obscene and racist push notifications to its customers through its Apple News account, which was connected to the CMS backend.
An incredibly offensive alert was sent by Fast Company, which has been hacked. Apple News has disabled their channel.
— Apple News (@AppleNews) 1:32 AM ∙ Sep 28, 2022
General tech and privacy
Chrome drops OCSP: Starting Chrome v106, released earlier this week, Chrome has stopped doing Online Certificate Status Protocol (OCSP) revocation checks for Extended Validation (EV) certificates, providing an immediate performance improvement for any sites still using an EV certification.
Brave ships cookie consent blocker: The Brave team has released a new version of its browser that now comes with a built-in system to block those annoying cookie consent popups.
Results about you: Google launched this week a new tool called "Results about you" that will notify users when Google indexes new web pages that contain a user's personal data. Users then have the option to request that Google removes these pages from future search listings. Google announced the tool earlier this year.
The tool is available from the Google app and the web beginning today, in the US for English to start (we’re looking to expand the tool globally in the future). Click the three dots next to any result to open the “About this results” panel, then use the “Remove result” option...
— Google SearchLiaison (@searchliaison) 6:54 PM ∙ Sep 28, 2022
Government, politics, and policy
Taiwan invests in cybersecurity defense: In the aftermath of Russia's invasion of Ukraine and after seeing the role cyber operations played in the conflict, a Taiwanese semiconductor magnate is funding a new cyber defense training course for Taiwanese citizens. According to Axios, Taiwanese tech tycoon Robert Tsao has invested $20 million in Kuma Academy; a company founded last year that promised to train more than 3 million Taiwanese citizens for a potential Chinese invasion and the online disinformation and hybrid warfare that could accompany it.
Polish investigation into use of Pegasus spyware: A Polish court ordered this week a criminal investigation into the use of the Pegasus spyware against prosecutor Ewa Wrzosek. Wrzosek had her phone infected with the spyware last year after she legally challenged an attempt by the Polish ruling populist right-wing government to purge the judiciary branch. Investigators and the EU believe the compromise of her device was ordered by the Polish government itself, which has been quiet about the incident and refused to cooperate with EU's PEGA anti-spyware commission.
Hungary buys social media-tracking services: The Hungarian government has acquired the services of Avnon Group, an Israeli company that sells software for mapping and tracking social media activities. Avnon Group representatives told Israeli media this week that the contract has been approved by the Israeli Defense Ministry, but the sale is controversial nevertheless; as Hungary is one of the three EU member states that have been caught using spyware against journalists and political rivals, and the EU Parliament recently updated the country's designation from a democracy to an autocracy.
Germany launches IT security labels: The German government has expanded its IT Security Label program to new categories of products this week. The BSI launched the program last year for routers and email services, and then it expanded it to cameras, speakers, cleaning and gardening robots, smart toys, and smart TVs. From this week, almost all smart home consumer products are eligible to apply a security label on their products sold in Germany to show that they meet basic security standards.
US federal cyber insurance program: CISA and the US Treasury are asking for feedback on the possibility and feasibility of establishing a federal cyber insurance program. In particular, the agencies would want to know if the program should require policyholders to implement basic cybersecurity measures. Forcing agencies and local governments to implement basic security measures would avoid moral hazards where organizations would intentionally avoid investing in cybersecurity, knowing the federal insurance program would cover the costs of an incident. [More coverage in NextGov]
Former NSA employee detained: The DOJ announced criminal charges against a former NSA employee who worked at the agency for less than a month but had enough time to steal and then attempt to sell top secret documents to a foreign agent—actually, an undercover FBI agent. The DOJ said the suspect, identified as Jareh Sebastian Dalke, 30, stole and attempted to sell documents on foreign targeting of US systems and information on US cyber operations.
UK NCSC CEO keynote speech: Here's the full keynote speech given by Lindy Cameron, the CEO of the UK National Cyber Security Centre, given at the Chatham House security and defense conference 2022 where she discussed, among other things, Russia's cyber operations in Ukraine.
Sponsor section
RunZero (formerly Rumble Network Discovery) is one of this newsletter's four main supporters and this week's featured sponsor. The company's main product is its network discovery and asset inventory platform, which can be used to find any managed and unmanaged assets inside a customer's network. To learn more, please check out this runZero product demo below:
Cybercrime and threat intel
Botnet creator pleads not guilty: A Northern Ireland teen pleaded not guilty to creating a DDoS botnet back in 2018 that was used to attack a large number of targets, including the servers of British and Czech police.
Abdilo to be extradited to the US: An Aussie court has approved that David Kee Crees, known as Abdilo, to be extradited to the US, where he will face 22 counts of hacking and fraud-related charges. Crees was first raided in 2015 in connection to various incidents, and the US has pressed charges against him in 2021 for other more recent hacks.
eBay security execs get prison sentences: Two former execs that were part of eBay's security team were sentenced to 57 and 24 months in prison, respectively, for a coordinated harassment campaign against two of the site's users.
Fake CISO profiles: As infosec reporter Brian Krebs found this week, an unknown threat actor has been creating fake LinkedIn profiles claiming to be CISOs for various large enterprises.
IRS warning: The US Internal Revenue Service issued an alert this week warning about a "significant increase" in IRS-themed texting scams aimed at stealing personal and financial information.
So far in 2022, the IRS has identified and reported thousands of fraudulent domains tied to multiple MMS/SMS/text scams (known as smishing) targeting taxpayers. In recent months, and especially in the last few weeks, IRS-themed smishing has increased exponentially.
New ransomware operation: Several security researchers have been tracking a new private ransomware affiliate program called Royal / Zeon which launched earlier this year in January and has focused solely on large corporate network attacks.
LockBit leak yielding results: Security researchers have spotted a new version of the Bloody ransomware that has been built on the recently-leaked LockBit ransomware builder. More here.
REvil insider worked with infosec firm: Security firm Trellix said in a report on Thursday that back in 2019, after they published an initial article on the REvil ransomware strain, a "disgruntled internal source" who worked with the gang provided them with valuable insight into how the group operates, including taking a Trellix researcher for a tour around the REvil RaaS backend.
The source shared multiple screenshots of the actual REvil backend panel. The Left side of the panel showed an overview of the infected victims including country and ransom price. The middle column showed the details of a single infection that was transmitted back via the config file. The right screen shows snippets of the multiple negotiation chats that were ongoing. One of the most important findings from the screenshots was that it confirmed our affiliate ID hypothesis. As visible in figure 8 it clearly shows the affiliate moniker name and their affiliate ID number in brackets, the other value was the campaign ID for the specific campaign. Essentially this means this backend system had the complete affiliate roster and would make attribution a lot easier.
Hacktivist activity in Iran: Israeli security firm Check Point said it's seeing an increased number of hacking groups using Telegram, Signal, and the dark web to aid anti-government protestors in Iran bypass regime restrictions.
Key activities are data leaking and selling, including officials' phone numbers and emails, and maps of sensitive locations. [Check Point Research] sees the sharing of open VPN servers to bypass censorship and reports on the internet status in Iran, as well as the hacking of conversations and guides.
Brute Ratel leak: Security researcher William Thomas said that cracked versions of the Brute Ratel red-team framework have been leaked and are widely shared on underground hacking forums. The leak occurred after an unknown entity uploaded the Brute Ratel tool on VirusTotal earlier this month, which eventually allowed threat actors to get hold of it and crack its installer. Brute Ratel's author blamed security firm MDSec for the leak, but the tool was already being used in attacks since July already, in ALPHV/BlackCat ransomware attacks. In the meantime, defenders might want to get acquainted with detecting Brute Ratel beacons before it's too late.
TP-Link credentials for sale: Security firm CyFirma said it spotted threat actors selling credentials for compromised TP-Link devices to serve as initial access inside organizations' networks for other cybercrime groups. In addition, CyFirma said it also saw threat actors looking to collaborate with other gangs on exploiting older TP-Link vulnerabilities.

Malware technical reports
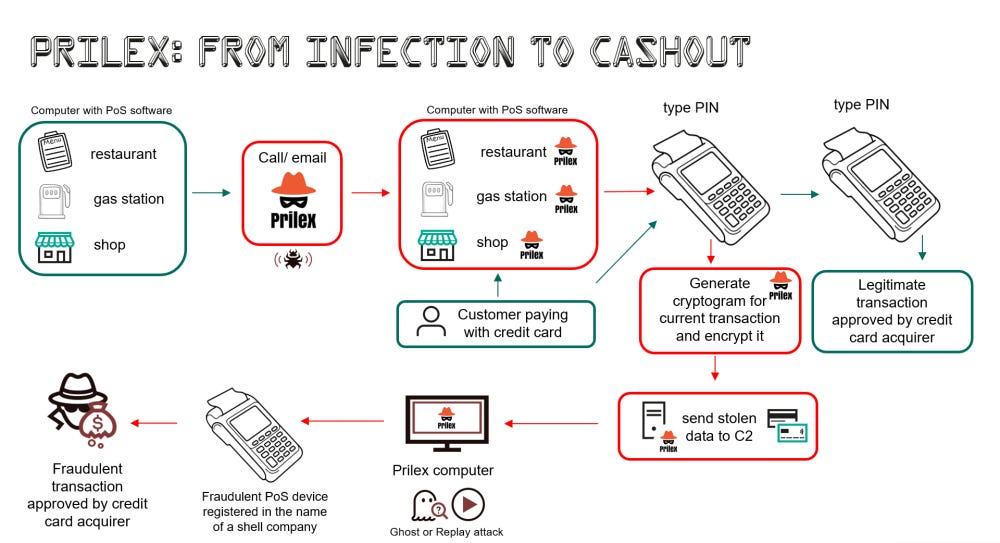
Prilex PoS malware: Kaspersky researchers have published a report on the evolution of Prilex, a Brazilian cybercrime group active since 2014. The report details how the group evolved from performing ATM jackpotting attacks to creating and deploying their own strain of Point-of-Sale malware.
CredoMap: Security researcher Vlad Pasca has a breakdown of the CredoMap infostealer, linked to past APT28 operations in Ukraine.
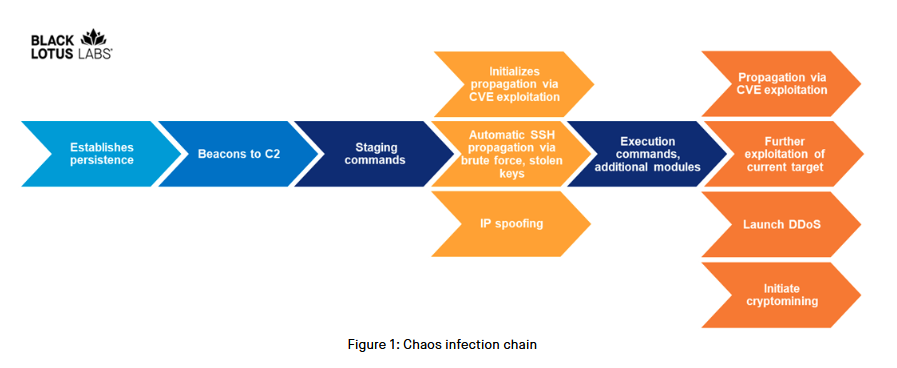
Chaos botnet: Lumen's Black Lotus Labs said they identified a new Go-based malware strain named Chaos that has spent the past few months infecting Windows and Linux servers worldwide, including many SOHO routers. According to current evidence, the main purpose of this new malware appears to mine cryptocurrency for its operator(s) and launch DDoS attacks.
APTs and cyber-espionage
New ESXi persistence technique: Mandiant discovered a new persistence technique used against VMWare ESXi systems where threat actors gained access to the servers and then installed malicious vSphere Installation Bundles (VIBs). These VIBs deployed the VIRTUALPITA and VIRTUALPIE backdoors at the hypervisor level, allowing the threat actor to run commands on all hosted guest operating systems.
Mandiant has begun tracking this activity as UNC3886. Given the highly targeted and evasive nature of this intrusion, we suspect UNC3886 motivation to be cyber espionage related. Additionally, we assess with low confidence that UNC3886 has a China-nexus.
🔥 VMWare has released guidance addressing malware known as VirtualPITA, VirtualPIE, and VirtualGATE, used to gain persistent access to instances of ESXi. Apply recommended mitigations and threat hunting guidance: core.vmware.com/vsphere-esxi-m…
— US-CERT (@USCERT_gov) 9:37 PM ∙ Sep 29, 2022
ZINC APT: Microsoft said in a report on Thursday that it's been tracking a series of social engineering campaigns carried out by the ZINC North Korean cyber-espionage group. These attacks consist of ZINC operators reaching out to targets via LinkedIn, engaging in WhatsApp conversations, all in order to get them to download and install backdoored versions of various open source software. The Microsoft report seems to cover the same campaign detailed by Mandiant earlier this month, but besides PuTTY, Microsoft said it saw ZINC operators also leverage apps like KiTTY, TightVNC, the Sumatra PDF Reader, muPDF, and Subliminal Recording software.
Witchetty: Broadcom's Symantec team has a report out on Witchetty, a sub-group of the Chinese-linked APT10 cyber-espionage group that has "targeted the governments of two Middle Eastern countries and the stock exchange of an African nation." According to Symantec, the attacks took place between February and September 2022, and the group heavily relied on the ProxyShell and ProxyLogon vulnerabilities for these intrusions.
CloudMensis=Scarcruft: In a series of tweets on Wednesday, ESET said it was able to finally attribute an APT operation targeting macOS users that they spotted in July (which they named CloudMensis) to the ScarCruft North Korean cyber-espionage group.
In July, #ESETresearch reported on macOS spyware we dubbed CloudMensis. In the blogpost, we left the malware unattributed. However, further analysis showed similarities with a Windows malware called #RokRAT, a #ScarCruft tool. @marc_etienne_, @pkalnai 1/9
— ESET research (@ESETresearch) 12:43 PM ∙ Sep 28, 2022
Vulnerabilities and bug bounty
Microsoft Exchange zero-day: Vietnamese security firm GTSC said it identified attacks using a new Microsoft Exchange email server zero-day in ongoing attacks. GTSC said they reported the issue to Microsoft via the ZDI program. Details about the zero-day are available in the company's blog post. RBN understands that this zero-day has been abused by an APT actor against local companies.
Stacked VLAN vulnerability: Security researcher Etienne Champetier has discovered a suite of vulnerabilities in the implementations of the VLAN Stacking (or QinQ) feature of modern routers and networking equipment. Champetier said in a write-up on Wednesday that these bugs can be exploited to crash devices or carry out MitM attacks on the encapsulated VLANs. Several major companies like Cisco, Arista, Juniper, and Microsoft [1, 2] have confirmed that their devices are vulnerable and have released patches.
Matrix protocol vulnerabilities: Security researchers disclosed this week "several practically-exploitable cryptographic vulnerabilities" in the Matrix end-to-end encryption protocol. The research team said the vulnerabilities could be exploited to break the confidentiality of Matrix-based apps and even run MitM attacks on participants. The Matrix team released security updates this week to address all issues. You can learn more about this research from this Twitter thread from Latacora founder Thomas Ptacek.
Matrix is not the first group chat system to have this basic flaw, which is apparently non-obvious: if you can’t securely control group membership, the cryptography doesn’t much matter.
— Thomas H. Ptacek (@tqbf) 11:02 PM ∙ Sep 28, 2022
SolarWinds security updates: SolarWinds has released three security updates this week. Memba them?
Medical device vulnerabilities: Trustwave researchers have published a write-up on two vulnerabilities in Canon Medical's Vitrea View toolkit for viewing medical images. Researchers say that exploiting these vulnerabilities could allow an attacker access to patient information.
Infosec industry
CISO AMA: Lightspin CISO Jonathan Rau held an AMA session on Reddit this week on his journey of becoming a CISO without having a college degree or cybersecurity certifications.
Infosec F1 news: In recent years, cybersecurity firms have been rushing to sponsor F1 cars, and most of the sponsor slots have been filled for a couple of seasons now. Nevertheless, Bitdefender is now Ferrari's sponsor, replacing Kaspersky, which is probably not having one of its best financial years right now. Because... reasons.
HITCON videos: Talks from the HITCON PEACE 2022 security conference, which took place earlier this month, are now available on YouTube.
New red team tool—VirusTotalC2: Red team developer D1rkMtr has open-sourced a new tool named VirusTotalC2 that abuses the fact that the VirusTotal API URL might be whitelisted in some corporate networks to host command-and-control traffic inside VirusTotal comments.
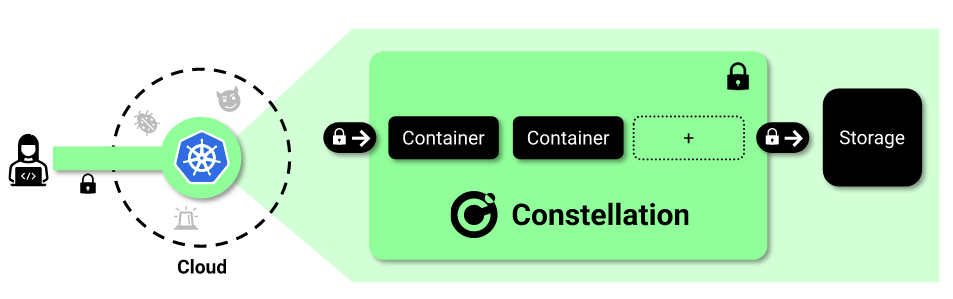
New tool—Constellation: Edgeless Systems has open-sourced a new tool named Constellation, a Kubernetes engine that wraps K8s clusters in a confidential wrapper that encrypts all data and separates it from the underlying cloud infrastructure.