Risky Biz News: Twilio cracks down on SMS Traffic Pumping schemes
In other news: Tor to get anti-DoS protection; Martinique gets ransomed; and even more ad-injecting Chrome extensions found on the Web Store.
This newsletter is brought to you by Stairwell. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple podcasts:
Communications platform Twilio will automatically reconfigure customer accounts in a crackdown against SMS traffic pumping schemes.
The company will block customers from sending SMS messages to countries the user has no previous history, and the country is known to be a source of SMS traffic pumping schemes.
The change will occur in three weeks, on June 21, 2023, according to emails Twilio has sent customers.
SMS Traffic Pumping is a scheme where fraudsters abuse a company's Twilio account and trick it into sending SMS messages to premium phone numbers where they generate a profit just by receiving the messages.
These types of schemes can also be carried out without premium phone numbers, where fraudsters work together with mobile operators. In this variation of the scheme, fraudsters abuse a Twilio customer's SMS systems to send a huge number of SMS messages to the mobile operator's numbers, allowing the telco to charge Twilio large sums of money for the traffic they received.
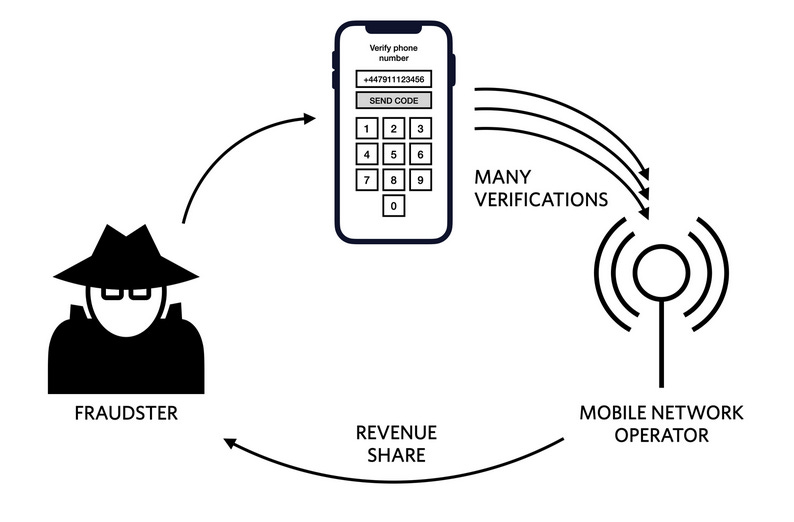
Any Twilio customer's SMS systems can be abused through such schemes, but online services that use SMS messages for two-factor authentication (2FA) are particularly vulnerable.
The perfect example of this is a scheme that targeted Twitter for the past years, where fraudsters working with mobile operators in Belarus, Ukraine, and other countries registered a large number of Twitter bots, which they'd then used to trigger 2FA one-time passcodes sent via SMS.
The more login attempts the groups triggered, the larger the ISP bill would be for Twilio, which the company passed down to its customers. In a Twitter Spaces talk last December, Twitter CEO Elon Musk said such schemes were generating Twillio bills of $60 million per year.
The fact that Twilio knew of these schemes and did nothing for years until one of its largest customers called them out speaks volumes.
The company's crackdown on fraudsters also comes after the FTC also threatened Twilio to have it disconnected from the US telecommunications network if the company did not take proactive steps to block robocalls originating from its systems.
Nothing like some tough love to get Twilio to act.
Breaches and hacks
Aladding hack: The Korean Publishers Association has confirmed that hackers have breached e-book platform Alladin and stole more than one million e-books. The organization says that more than 5,000 Aladdin books have already been shared on Telegram channels. The organization says Aladdin has refused to answer questions about its security and has called on similar platforms to work together to defend their systems.
"These e-books will wander like ghosts over the next few decades and will virtually lose their value as a commodity. Leaking e-book files is a completely different problem from the theft of paper books. This is because it can be reproduced infinitely and is not affected by time and space. If the stolen e-book files are additionally leaked, it will be a disaster that the publishing world cannot even imagine. And this will return to damage not just publishers, but also to the entire e-book distribution industry [machine translated by Google].
Xplain ransomware attack: A cyberattack on Swiss IT company Xplain has put several Swiss government agencies on high alert, including the Swiss Army, multiple cantonal police forces, and the Federal Office of Police. Swiss government agencies impacted by the attack say that while they use Xplain products, they use self-hosted solutions, and the government's data is safe. The Play ransomware group took credit for the Xplain attack, leaked 5GB of data on its dark web leak site, and threatened to publish the entire data if there was "no reaction" from the company. Xplain says it did not contact the ransomware gang and will now pay the ransom demand. [Additional coverage in LeTemps]
Martinique ransomware attack: A new ransomware gang named Rhysida has taken credit for breaching the IT network of the government of the Caribbean island of Martinique. The attack took place on May 16, according to a statement the government posted on Facebook. The Ryhisida ransomware gang was first spotted last month, according to reports from SentinelOne and Secplicity. The Martinique government is the fourth victim listed on the gang's dark web leak site. [Additional coverage in DataBreaches.net]
Augusta ransomware attack: After Augusta officials denied being extorted for $50 million in a ransomware attack, the figure of the actual ransom is now out, and it's only $2 million.
Atomic Wallet thefts: The Atomic cryptocurrency wallet service is currently investigating a series of incidents where some of its customers' wallets were breached and emptied of funds. It's still unclear if the attackers used spear-phishing or if they exploited a vulnerability in the Atomic wallets.
STALKER game leak: Russian hackers have leaked early dev builds of the upcoming STALKER 2 game from Ukrainian gaming studio GSC Game World. The hackers breached the company last year after the studio removed the Russian language pack from the game following Russia's invasion of Ukraine. The hackers threatened to leak the game if the studio didn't add back support for the Russian language. GSC refused and told fans not to look at the leaks if they want to enjoy the upcoming game.

General tech and privacy
Gabon gets back its TLD: The Gabonese government has terminated its contract with Dutch domain registrar Freenom and has taken over the management of the .ga top-level domain (TLD) again. Libreville officials cited the company's failure to properly manage the country's TLD, which has seen "widespread technical abuse" by threat actors. More than 7 million .ga domains have been transferred this weekend to Gabon's ANINF. Officials say they plan to delete any domain that does not have information on its owners. France's national domain registrar AFNIC will also provide technical support. [AFNIC press release/PDF]
Cortana EOL: Microsoft has announced the end-of-support for the Cortana smart assistant. The company says that starting in "late 2023," the service will no longer be supported on both Windows 10 and Windows 11. The announcement comes after the company seemingly gave up on the app four years ago when Microsoft CEO Satya Nadella admitted Cortana would never be able to compete with Amazon Alexa, Apple Siri, or even Google Assistant.
SMB signing in Windows 11: Future versions of Windows 11 will soon require that all SMB requests be signed for all types of connections. Currently, both Windows 10 and 11 require SMB signing only for SYSVOL and NETLOGON connections. Microsoft says this change is part of its plan to "improve the security of Windows and Windows Server for the modern landscape." SMB signing is a security mechanism in the SMB protocol where every SMB message contains a signature generated using the session key. It's been supported since Windows 98 but has never been enabled by default until now because it usually comes with a performance impact in data-transfer operations. From a security perspective, SMB signing can protect against NTLM relay attacks.
Tor gets anti-DoS protection: The Tor Project is testing a new DoS mitigation feature for the Tor network where servers will require connecting clients to solve a "puzzle" to access its resources. The new protection will kick in when the server is overloaded with requests and will disable itself when activity is low. The idea is to allow authentic users to connect to a Tor service while weeding out automated DDoS attacks. The new feature is currently being tested in the Tor alpha software and is expected to roll out to most Tor nodes later this year. Work on the feature started last year after Tor node operators reported DDoS attacks against their infrastructure.
Government, politics, and policy
US sanctions Arvan Cloud: The US Treasury Department has imposed sanctions on Iranian IT company Arvan Cloud for helping the Iranian government censor the internet in Iran. Officials say Arvan Cloud has helped the Tehran regime build the National Information Network, Iran's national firewall system. The company's servers are used to intercept internet traffic, sniff its content, and then censor incoming and outgoing communications. Treasury officials say Arvan Cloud has a close relationship with Iran's intelligence services, and managers of Arvan Cloud are either current or former MOIS affiliates.
Know Your App Act: Three Republican senators have introduced a bill that would require large online app stores to display the country where apps are developed and owned. The Know Your App Act—as it's been named—comes as US officials have repeatedly warned that China may use its national security laws to compel app developers to cooperate or share user data. The bill would also require app stores to provide users with the ability to filter applications by country of origin and warn users when an app has been developed in "adversarial countries."
DHS legacy systems: A US GAO report found that the DHS is still using legacy gear to run some of its critical systems, exposing itself to hacks and other security risks.
Defense contractor cybersecurity certification program: The US and Canada will work on a cybersecurity certification framework for defense contractors. The certification will apply to both countries in order to reduce compliance work and allow contractors to work seamlessly in both countries. The new framework is expected to be in place by the end of next year. [Additional coverage in Reuters]
State of cybersecurity in EdTech: According to a study published by the Consortium for School Networking, a professional association of school systems technology providers, two-thirds of most school districts don't have a full-time employee dedicated to cybersecurity. Twelve percent of districts also don't allocate any funds for cybersecurity defense. [Additional coverage in CybersecurityDive]
Dutch study of solar panels: A study commissioned by the Dutch National Digital Infrastructure Inspectorate has found that the majority of solar panel products available on the market are vulnerable to hacking and don't meet minimum cybersecurity requirements. The panels are usually exposed on the internet and can either be switched off remotely or hijacked to perform DDoS attacks. Officials say none of the nine products they tested met the cybersecurity requirements of the upcoming EU Radio Equipment Directive, set to enter into effect on August 1, 2024.
Russian internet passport: The Russian Duma is working on a law that would require Russian citizens to obtain a unique code before accessing the internet. The new code is being touted in government circles as an "internet passport" that would make it easier to track its citizens' activities.
The role of security cameras in the war in Ukraine: The Ukrainian Security Service has asked citizens to shut off security cameras filming public spaces. The SSU says Russia is exploiting vulnerabilities in modern security cameras to access streams, launch missile attacks, and adjust targeting in real-time. After the SSU sent SMS messages to all citizens with this message last week, several Russian military bloggers thought the agency was trying to mask the movement of its troops for its impeding counter-offensive.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Chris St. Myers, Threat Intelligence Lead at Stairwell, on how the company Inception platform can be used for finding old or new threats that sometimes may go unnoticed.
Cybercrime and threat intel
Comm arrests: The FBI has detained a member of "The Comm," an underground community that has organized a wave of swattings against schools and universities across the US. The group used Discord and Telegram channels to organize and coordinate threats, such as sending fake bombings or mass shootings in the name of other individuals. A subgroup of The Comm named ACG is also involved in SIM swapping and the theft of cryptocurrency from online accounts. A suspect named Braiden Williams was detained in July 2022 for the SIM swapping attacks, released, and then re-arrested this May for the swatting incidents. [Additional coverage in Motherboard]
AvosLocker goes after Veritas backups: Cybersecurity firm At-Bay has spotted the AvosLocker ransomware gang using vulnerabilities in Veritas backup servers to gain access to victim networks.
MOVEit exploitation: HuntressLabs, Mandiant, Rapid7, TrustedSec, and Trustwave have published more details on the attacks targeting MOVEit file-transfer appliances. No words on who's behind the attacks, though. Mandiant assigned all this activity to a new cluster it tracks as UNC4857. Attacks target the CVE-2023-34362 vulnerability and deploy a webshell named LEMURLOOT, through which the threat actors steal data uploaded by users on the MOVEit server. According to Censys and Shodan, there are currently between 2,500 and 3,000 MOVEit servers exposed online.
Operation CMDStealer: BlackBerry has discovered a new financially motivated threat actor that is currently targeting Spanish and Portuguese-speaking countries. Named Operation CMDStealer, the group's primary purpose is to infect victims with malware and then gain access to online banking accounts. According to researchers, the group relies heavily on LOLBnins and CMD scripts for its attacks. For now, the group has been seen targeting users in Portugal, Mexico, and Peru.
Megatraffer: Brian Krebs has a profile on Megatraffer, a Russian individual who's been providing code-signing certificates to malware gangs since 2015.
India's hacker-for-hire industry: The New Yorker has a profile of India's budding cyber mercenary market, which outsources hacker-for-hire services across the globe, with the government's tacit acceptance.
New npm malware: Twenty-six new malicious npm packages were spotted last week. Check out GitHub's security advisory portal for more details.
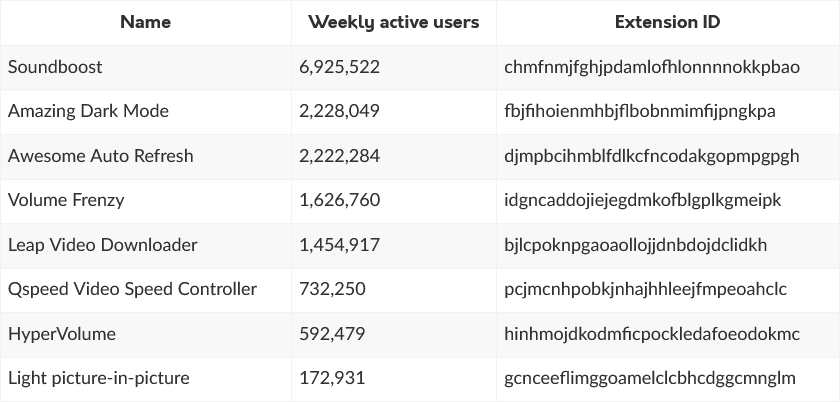
Malicious Chrome extensions: Cybersecurity company Avast has discovered a cluster of 82 Chrome extensions that display adware and hijack search results. Avast says the extensions were available through the official Chrome Web Store and have been downloaded more than 75 million times. The company says it discovered the extensions by pivoting from research published last week by security researcher Wladimir Palant. At the time, Palant discovered 18 Chrome extensions on the Play Store with similar behavior. Since then, Palant discovered another set of 16 extensions with the same behavior. Eight of these are still available for download (see image below). In subsequent research, Palant says the extensions passed under the radar because they moved their code to Google's new Manifest V3 Chrome extensions system and are using "new ways of running arbitrary code that wouldn't attract unnecessary attention."
Malware technical reports
ModiLoader: SANS ISC's Brad Duncan has a breakdown of a recent ModiLoader campaign pushing the Remcos RAT.
Magecart campaign: Akamai takes a look at a recent Magecart e-skimming campaign. This campaign was notable because of hosting their Magecart scripts on their own domains, the attackers hosted the malicious code on compromised legitimate sites as a way to avoid detection by security solutions that use website domain reputation checks.
Bandit Stealer: Zscaler has published a report on Bandit Stealer, a new Go-based infostealer. A similar report is also available from Trend Micro.
Risky Business Demo
Stairwell's Mike Wiacek demonstrates Stairwell's file analysis and threat detection platform to Risky Business host Patrick Gray. Stairwell helps you monitor and analyze every executable file in your organization, automatically collecting crucial intelligence and providing your security team with in-depth visibility and detections.
APTs and cyber-espionage
Kimsuky alert: US and South Korean authorities have issued their first joint cybersecurity advisory warning that the Kimsuky North Korean cyber-espionage group is conducting large-scale social engineering campaigns. Officials say the group poses as journalists, academics, or other individuals with credible links to North Korean policy to reach out to their targets, establish a rapport, and then send malware or lure victims on phishing sites. Typical Kimsuky targets include think tanks, academic institutions, and news outlets. Officials say the purpose of the attacks appears to be intelligence gathering. South Korean officials have also sanctioned the group.
Chinese APT in Taiwan: EclecticIQ has discovered a suspected Chinese threat actor utilizing a modified version of Cobalt Strike (named Cobalt Strike Cat) to target Taiwanese government entities, including critical infrastructure. Cobalt Strike Cat was initially shared on a Chinese-speaking cybersecurity forum called t00ls[.]com.
Vulnerabilities and bug bounty
ReportLab RCE PoC: A proof-of-concept exploit has been published on GitHub for a remote code execution vulnerability in the ReportLab Toolkit, a Python library used to convert HTML files into PDF documents.
Cisco RV PoC: Chinese security researchers have published an analysis and a PoC for CVE-2023-20073, an arbitrary file upload vulnerability impacting Cisco RV VPN routers. The vulnerability was patched back in February 2023.
Gigabyte security updates: Taiwanese hardware vendor Gigabyte has released BIOS updates after Eclypsium researchers found that its motherboards were downloading and running files from its servers in an insecure manner, exposing users to Attacker-in-the-Middle (AitM) threats. Gigabyte says that any file downloaded from its servers during the boot process is now verified for integrity and legitimacy.
Google Security Sheppard: Google has a nice explanation of its Security Sheppard role, the Google security engineer that's tasked with triaging Chrome security bugs each week.
Infosec industry
New tool—triangle_check: Kaspersky has open-sourced a tool named triangle_check that can scan iTunes backups for traces of compromise by Operation Triangulation.
New tool—Binder Trace: UK security firm Foundry Zero has released a tool named Binder Trace that can intercept and parse Android Binder messages, which is Android's IPC mechanism.
Infosec conferences: This GitHub repo from Xavier Santolaria keeps track of all past and upcoming infosec security conferences.
Fox-IT developments: According to reports in Dutch media, NCC Group is dismantling Fox-IT, the Dutch cybersecurity giant it acquired in 2015 for €135 million. [Additional coverage in de Volkskrant/non-paywall]
AWS Blueprint for Ransomware Defense: AWS has published a guide [PDF] on how to defend against ransomware attacks against its customers' AWS infrastructure.
An OWASP for LLMs: The OWASP Foundation is working on an OWASP Top 10 list to showcase the most dangerous security risks involved in working with Large Language Model (LLM) applications. A draft v0.1 document is already live.
- Prompt Injections
- Data Leakage
- Improper Sandboxing
- Unauthorized Code Execution
- SSRF Vulnerabilities
- Overreliance on LLM-generated Content
- Inadequate AI Alignment
- Insufficient Access Controls
- Improper Error Handling
- Training Data Poisoning




