Risky Biz News: Trump campaign points finger at Iranian hackers for documents leak
In other news: Another DPRK laptop farmer detained in the US; Trend Micro explores sale; soccer club gets BECed for transfer fee.

This newsletter is brought to you by Corelight. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

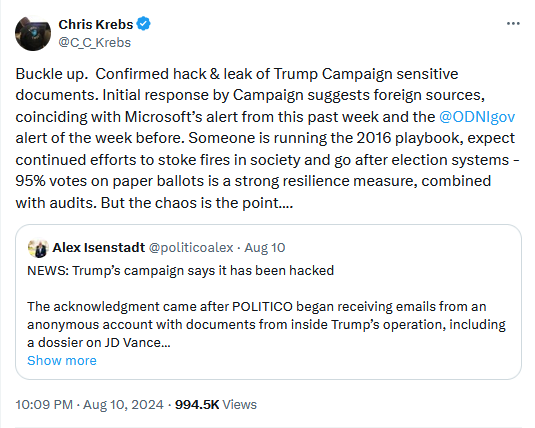
The Trump campaign claims it was hacked by Iran after a trove of sensitive documents were leaked to Politico at the end of July.
The news outlet says it received the documents from an individual using the name Robert and an AOL email address.
The documents allegedly contained vetting materials pertaining to J.D. Vance and Marco Rubio, which were compiled by the Trump team as part of the Vice President nomination process. The documents are allegedly part of a larger collection of files stolen from the campaign.
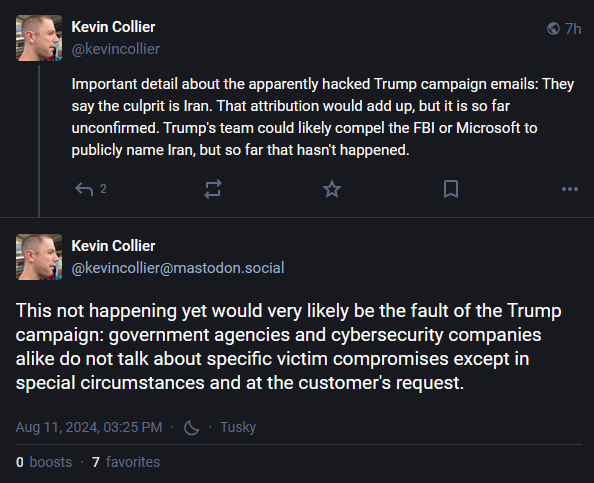
When contacted by Politico, Trump campaign spokesperson Steven Cheung confirmed the hack and the authenticity of the documents, and pointed the finger at a Microsoft report published last week about Iran's attempts to influence the upcoming 2024 US Presidential Election.
Cheung claims this is a hack-and-leak operation carried out by Iran in the hopes of influence the upcoming election, similar to how Russian hackers leaked Clinton campaign documents to the media in the 2016 election.
"These documents were obtained illegally from foreign sources hostile to the United States, intended to interfere with the 2024 election and sow chaos throughout our Democratic process. On Friday, a new report from Microsoft found that Iranian hackers broke into the account of a ‘high ranking official’ on the U.S. presidential campaign in June 2024, which coincides with the close timing of President Trump's selection of a vice presidential nominee."
Based on Cheung's above-statement and the Microsoft report (quote below), the Trump team seems to imply that an Iranian cyber-espionage group named Mint Sandstorm (aka APT35, Charming Kitten, Newscaster Team) was behind the hack.
"In June 2024, Mint Sandstorm—a group run by the Islamic Revolutionary Guard Corps (IRGC) intelligence unit—sent a spear-phishing email to a high-ranking official of a presidential campaign from a compromised email account of a former senior advisor. The phishing email contained a fake forward with a hyperlink that directs traffic through an actor-controlled domain before redirecting to the listed domain. Mint Sandstorm similarly targeted a presidential campaign in May and June 2020 five to six months ahead of the last US presidential election."
While there was pressure over the weekend from multiple major US news outlets, neither Microsoft nor the US government have come out to publicly confirm the Trump campaign's attribution.
According to the same Microsoft report, the same group also attempted and failed to log into an account belonging to a former US presidential candidate.
The incident took place in June, days after the phishing campaign that "allegedly" compromised the Trump campaign.
The Mint Sandstorm group has been previously linked to the Islamic Revolutionary Guard Corps's intelligence and cyber unit, the IRGC-IO.
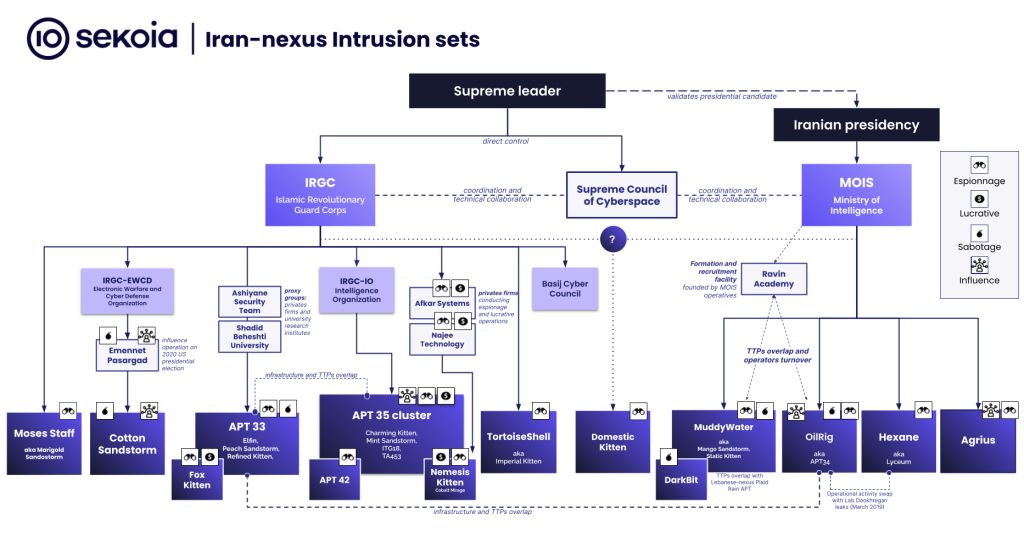
An ODNI report from July warned that Iran was not only seeking to undermine the upcoming US election, but were specifically trying to prevent a second Trump term.
Media reports claim that a Pakistani man arrested in mid-July was also allegedly working with Iran to hire hitmen to assassinate Donald Trump. Ironically, the FBI detained the suspect a day before a Pennsylvania man named Thomas Matthew Crooks attempted to kill Trump at a rally in Butler.
Unlike the 2016 Clinton leaks, both the media and the cybersecurity has been more careful around amplifying unproven claims made by the leaker—although, to be fair, nothing of importance has been leaked so far to amplify in the first place.
As Marcy Wheeler highlights in a blog post, the leaks have their own importance for Iran that may not be viewed in the same light and perspective by the rest of us.
"Trump has not firewalled his campaign from a criminal case involving the most sensitive documents of the US government, meaning a well-executed hack targeted at his campaign may turn into an intelligence bonanza.
If Iran plans to make things difficult for Trump, the problems may extend well beyond what documents get leaked. As they did in 2016, this could mean that Trump wastes resources having to serially defend against hacking attempts via a range of different platforms. It could mean that Iran does what Russia did, hack key strategic models to optimize other kinds of f--kery later in the election. Because — unlike Russia — Iran is actively trying to kill Trump, not just defeat him, hacked documents may also facilitate efforts like those charged against Asif Merchant, manufacturing fake protests to create distractions to facilitate an assassination attempt.
The question of how to approach this news, if it is further confirmed, goes well beyond the question of whether to publish the documents allegedly stolen by Iran. In significant part because Trump refuses to maintain boundaries between his political life and his criminal life, hacks from Iran could create real damage to the United States beyond what they do to Trump’s campaign."
Breaches, hacks, and security incidents
Soccer/football BEC incident: Qatari soccer club Al Gharafa has fallen victim to a BEC scam after it sent a player's transfer fee to the bank account of a Vietnamese scam group. The hack was discovered at the start of the month when Romanian soccer club FCSB didn't receive the final €1 million payment for the transfer of midfielder Florinel Coman. The club had sold Coman to Al Gharafa earlier this year for €6.25 million. Al Gharafa paid most of the sum but was due the last million by July 31. Qatari officials discovered the hack when FCSB asked why they hadn't made the final payment. The Qatari club is investigating the email breach while FCSB lodged a complaint with soccer's governing body FIFA. [Additional coverage in Golazo]
General tech and privacy
Intel CPU patches: Intel has released a firmware patch to address the performance issues and crashes in 13th- and 14th-gen chips caused by elevated power delivery. [Additional coverage in Tom's Hardware]
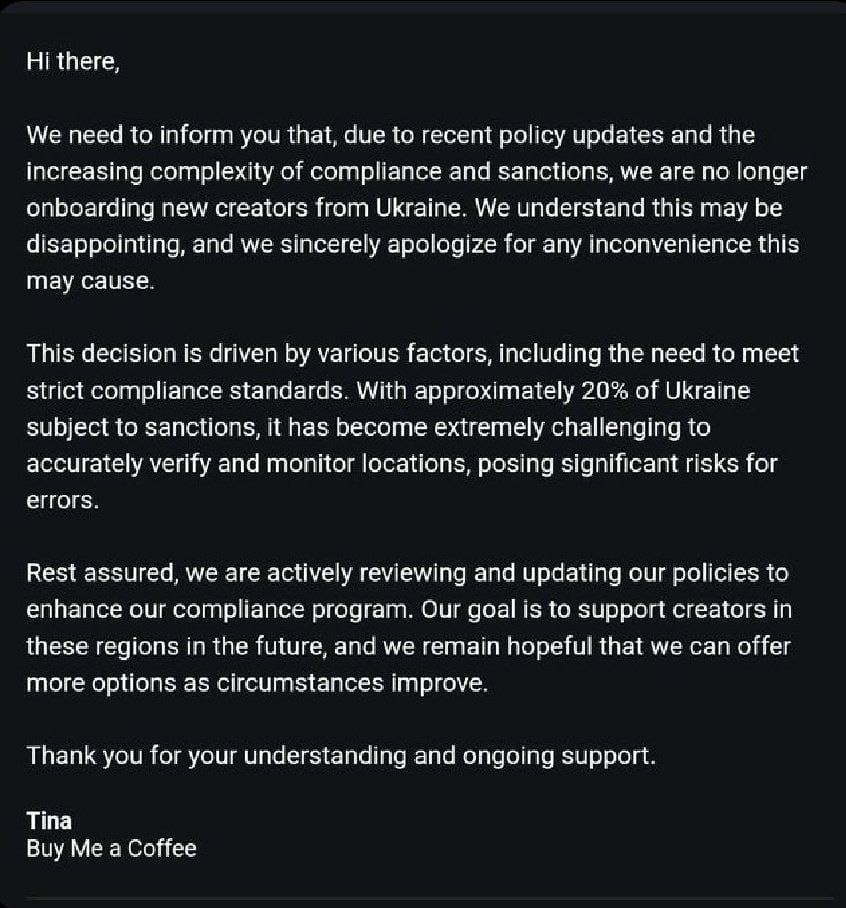
Buy Me a Coffee leaves Ukraine: Donation service Buy Me a Coffee is leaving Ukraine citing problems with following sanctions imposed on some of the Russian-conquered parts of Ukraine. The company says it's getting harder to tell which users in Ukraine are living where and if they are subject to sanctions.
Government, politics, and policy
UN cybercrime treaty moves forward: The United Nations Ad Hoc Committee on Cybercrime has unanimously passed a proposed reform of the UN's cybercrime treaty. The treaty was adopted by consensus after three years of negotiations. It now moves to a vote in the General Assembly later this year, where it is expected to pass. The treaty's draft was proposed by Russia and has been heavily criticized by human rights organizations. [Additional coverage in The Record]
New DARPA CIO: The DOD's Defense Advanced Research Projects Agency (DARPA) has appointed Peiter "Mudge" Zatko as its new Chief Information Officer (CIO). Zatko returns to DARPA after 11 years in the private sector. He previously served as Cyber Program Manager between 2010 and 2013, and as Twitter's Head of Security between 2017 and 2020. [Additional coverage in ExecutiveGov]
OS31 report: The White House has published a yearly summary report for its Open-Source Software Security Initiative (OS3I).
Federal Contractor Cybersecurity Vulnerability Reduction Act: Two US senators have introduced a bill that would require federal contractors for the US government to run vulnerability disclosure programs. US federal agencies are already required to run bug bounty programs, but the new bill extends the same requirement to their contractors. The Federal Contractor Cybersecurity Vulnerability Reduction Act was introduced in the Senate after a similar bill passed in the House in May. It is sponsored by senators Mark Warner (D-VA), Chairman of the Senate Select Committee on Intelligence, and James Lankford (R-OK), a member of the Senate Committee on Homeland Security & Governmental Affairs.
Turkiye internet block shenanigans: After blocking 27 VPN apps and Instagram last week, the Turkish government has now lifted the Instagram ban but is now blocking Roblox.
Russia and Venezuela block Signal: The governments of Russia and Venezuela have blocked access to the Signal secure messaging service. Russia's communications watchdog says it blocked the service because it was being used for terrorist and extremist purposes. The block in Venezuela comes days after the Maduro regime also blocked Twitter. Protests broke out across Venezuela after President Maduro claimed victory in the country's election without providing any evidence that he actually won. Tens of protesters have been killed by the military in the streets and more than 1,000 protesters have been arrested in their homes. Former President Maduro claimed victory in recent elections with what appeared with what appeared to be a bogus votes tally. Signal has asked affected users to enable a feature named "Censorship Circumvention" to get around the block.
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Brian Dye, CEO of Corelight about a string of recent CISA advisories. These advisories address specific technical issues, but when examined together Brian says there is an underlying message about addressing security holistically.

Cybercrime and threat intel
Bug hunters extortionists sentenced to prison: A Finnish court has sentenced three brothers to nearly three years in prison for an extortion scheme that targeted lock manufacturer Assa Abloy. Anssi, Henri, and Pauli Pukari found a vulnerability in Abloy smart locks in 2021. The trio anonymously contacted the vendor and threatened to publish details about the bugs unless they were paid a massive €37 million bounty. Officials say the brother who orchestrated the scheme used to work as a police officer in the city of Tampere, Finland. [Additional coverage in Yle] [h/t Harry Sintonen]
Ransomware affiliate faces 12 years in prison: Ukraine's Cyber Police says it completed the pre-trial investigation into a suspected ransomware affiliate linked to operations such as LockerGoga, MegaCortex, Hive, and Dharma. Officials say the suspect is responsible for damages of almost $73 million. He was detained last November and now faces up to 12 years in prison.

AMOS interview: Threat intelligence analyst g0njxa has published an interview with Ping3r, the creator of the AMOS macOS infostealer.
Head Mare: Kaspersky looks at Head Mare, a pro-Ukrainian hacktivist group that emerged last year and has targeted Russian and Belarus companies with ransomware attacks.
DarkVault missteps: DarkVault, a RaaS platform described as LockBit's spiritual successor, listed back in April a Belarussian transportation company named ATriLine. Attacking a company in Putin's backyard by a Russian-based ransomware operation may not bode well for the group. [h/t Roman Sannikov]
New npm malware: One-hundred-fourteen malicious npm packages were discovered last week. Check out GitHub's security advisory portal for additional details.
Companies avoid ransoms: Security researcher Vangelis Stykas has helped six companies avoid paying hefty ransoms after he found vulnerabilities in the web panels used by two ransomware gangs. Stykas was able to provide decryption keys for two companies and also notify four before the encryption process could get underway. The bugs resided in web panels used by gangs such as Everest and BlackCat. The vulnerabilities included the use of default passwords for backend databases, exposed file directories, and unsecured API endpoints. [Additional coverage in TechCrunch]
Malware technical reports
Ande Loader: eSentire has published a report on an Ande Loader campaign dropping the 0bj3ctivity Stealer.
Sponsor Section
James Pope, Corelight's Director of Technical Marketing Engineering, demonstrates the company's Open NDR Platform and how it combines network detections with a whole host of other data sources.
APTs, cyber-espionage, and info-ops
US disinformation report: A United Nations report has found that the fossil industry is behind a sprawling misinformation and disinformation campaign designed to attack climate change topics and slow down the transition away from carbon-based energy sources. [Additional coverage in The Guardian]
Second DPRK laptop farmer detained: The US has arrested and charged a 38-year-old Tennessee man for allegedly running a "laptop farm" for North Korean IT workers. US officials say Matthew Isaac Knoot was part of a scheme to help North Korean programmers pose as American-based employees. The workers would apply for remote jobs in the US and receive laptops from companies at Knoot's Nashville residence. Knoot would install remote access software on the laptops and then host the devices at his home to help the workers pose as being based in the US. Officials say the suspect has made over $250,000 from hosting the laptop farm. Knoot is the second suspect arrested in the FBI's crackdown on DPRK laptop farms. An Arizona woman was detained on similar charges earlier this year in May.
BfV i-SOON report: Germany's Federal Office for the Protection of the Constitution (BfV) has published a two-part report on the industrialization of cyber-espionage and has used the i-SOON leaks from earlier this year as a case study. Title says "part 2" but both parts are linked in that page.
CloudSorcerer: Kaspersky has published a report on EastWind, a new espionage campaign targeting Russian state organizations and IT companies that the company has linked to the CloudSorcerer APT it discovered last month. New clues shows the group used GrewApacha, a Windows trojan previously linked to APT31.
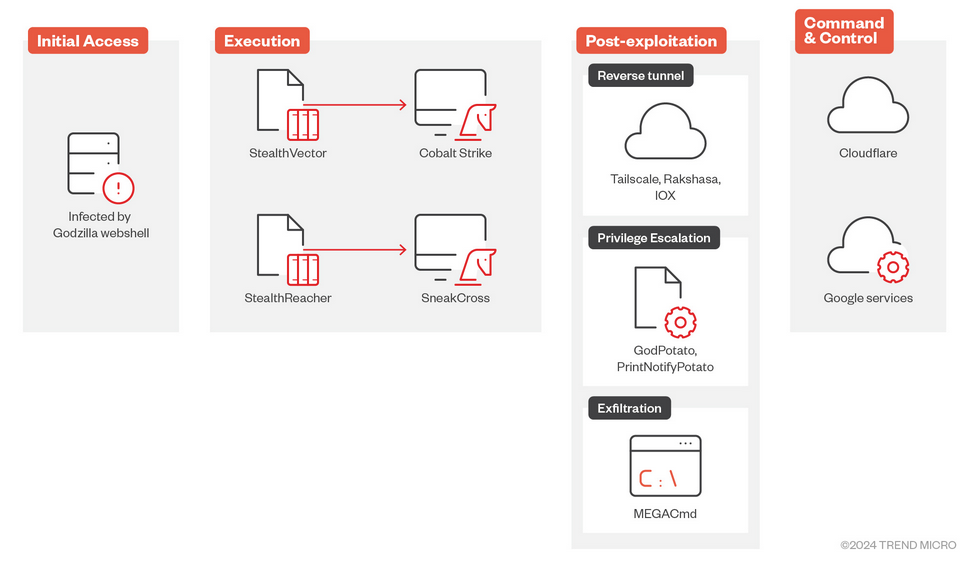
Earth Baku (APT41): Trend Micro looks at how Chinese APT group Earth Baku has recently expanded operations from the Pacific region to Europe, Africa, and the Middle East. The attacks have used public-facing applications such as IIS servers as entry points. The group then deployed advanced malware toolsets such as the Godzilla webshell, StealthVector, StealthReacher, and SneakCross.
Vulnerabilities, security research, and bug bounty
AWS to issue CVEs: AWS says it will now issue CVE identifiers for vulnerabilities reported in its cloud services. To receive a CVE, Amazon says bug reports must have a CVSS severity score of 4 or higher. AWS joins Microsoft as the second cloud vendor to issue CVEs for cloud bugs.
Web timing attacks: PortSwigger researcher James Kettle has published a paper on a novel technique called "web timing attacks." The technique is useful for bypassing firewalls, reverse proxies, and front-end access rules.
"This is not a theoretical threat; every technique will be illustrated with multiple real-world case studies on diverse targets. Unprecedented advances have made these attacks both accurate and efficient; in the space of ten seconds you can now reliably detect a sub-millisecond differential with no prior configuration or 'lab conditions' required. In other words, I'm going to share timing attacks you can actually use."
BYOVDLL technique: Orange's SCRT team looks at the relatively new BYOVDLL (Bring Your Own Vulnerable DLL) technique.
AMD Sinkclose attack: AMD has released firmware updates for some of its CPUs that are impacted by a new vulnerability known as Sinkclose (CVE-2023-31315). The new attack was discovered by security firm IOActive and impacts the System Management Mode, a highly privileged mode inside AMD CPUs that runs during a computer's boot process. The Sinkclose attack allows threat actors to bypass security protections and install low-level rootkits with the help of the SMM. Sinkclose impacts AMD's almost entire CPU line-up.
K8s git-sync bug: Akamai researcher Tomer Peled has found a vulnerability in the Kubernetes feature git-sync that can allow threat actors to inject commands or steal data from Kubernetes pods. A proof-of-concept exploit was also published online.
"Since a CVE has not been assigned to this design flaw, there is no patch for it — it remains exploitable. The Kubernetes team has encouraged us to share this research to raise awareness about these attack vectors."
AWS vulnerabilities: At the Black Hat conference last week, AquaSec researchers presented a talk about vulnerabilities they found in six of AWS' services. The vulnerabilities target services that share AWS S3 buckets between them. AquaSec says that an attack technique they named "Bucket Monopoly" could have allowed a threat actor to claim ownership of the buckets and their data—away from legitimate AWS customers.
"We reported these vulnerabilities to AWS, and they promptly responded and fixed them. Regarding the possibility that an attacker used this vector previously to exploit the vulnerabilities, AWS indicated that they "are confirming the results of each team's investigation and will contact customers directly in the event they are affected by any of the reported issues.""
OpenVPN vulnerabilities: Microsoft has published details on four vulnerabilities it found in the OpenVPN project. The blog post got a little heat over the weekend after Microsoft described the issues as "zero-days," even if they were privately reported and patched, and have never been exploited in the wild.
Ecovacs vulnerabilities: Two security researchers are set to publish details about vulnerabilities in Ecovacs vacuum and lawn mower robots that could be used to hijack the devices and spy on their owners. The main issue is a bug that allows threat actors to connect to any Ecovacs system via Bluetooth up to 130 meters away. From here, attackers can expand access and take control of the devices via the internet. The two researchers say Ecovacs never replied to their emails and that the vulnerabilities are likely still unfixed. [Additional coverage in TechCrunch]
Sonos vulnerabilities: The NCC Group has published details on a remote over-the-air (WiFi) attack on Sonos One devices, which could have been used to enable covert recording of all audio within the physical vicinity of the speaker. Sonos patched the bug before it was presented at this year's Black Hat security conference.
Quick Share vulnerability: Security researchers from SafeBreach Labs have discovered 10 vulnerabilities impacting Google's Quick Share peer-to-peer data-transfer utility. The vulnerabilities can allow threat actors to remotely write files to a user's Android or Windows system without authentication or the user's permission. They can also be used to open persistent WiFi connections to a targeted Windows PC. Google has released patches for all reported issues.
Unpatched Office NTLM relay attack: Two PrivSec researchers will publish details at the DEFCON security conference about a new NTLM relay attack that abuses Microsoft Office. Microsoft has confirmed the issue as CVE-2024-38200, but no patches are out yet. The vulnerability will most likely be patched in next week's Patch Tuesday updates.
The Apache server bugs: Akamai's Ryan Barnett and Sam Tinklenberg and DEVCORE's Orange Tsai have published reports on a suite of nine vulnerabilities Tsai found and reported in the Apache HTTPD web server. The bugs were patched earlier this year, but everyone has been awaiting Tsai's write-up since he has a talent for finding bugs in places and ways that people don't usually find or look. They weren't disappointed as Tsai found ways to bypass authentication and access controls using only a question mark (?) character, found a way to get root access to the server because of unsafe RewriteRules, and a way to elevate an XSS bug to RCE in a piece of code dating back to 1996.
- CVE-2024-38472 - Apache HTTP Server on Windows UNC SSRF
- CVE-2024-39573 - Apache HTTP Server proxy encoding problem
- CVE-2024-38477 - Apache HTTP Server: Crash resulting in Denial of Service in mod_proxy via a malicious request
- CVE-2024-38476 - Apache HTTP Server may use exploitable/malicious backend application output to run local handlers via internal redirect
- CVE-2024-38475 - Apache HTTP Server weakness in mod_rewrite when the first segment of substitution matches the filesystem path
- CVE-2024-38474 - Apache HTTP Server weakness with encoded question marks in backreferences
- CVE-2024-38473 - Apache HTTP Server proxy encoding problem
- CVE-2023-38709 - Apache HTTP Server: HTTP response splitting
- CVE-2024-?????? - [redacted]
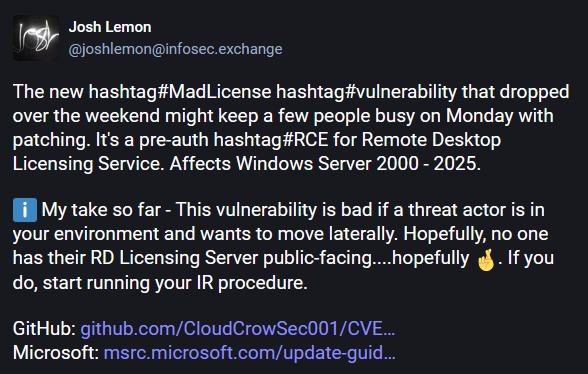
RD Licensing exploit: A public PoC is now available for CVE-2024-38077, an RCE in the Windows Remote Desktop Licensing server that Microsoft patched last month. The bug has been named by its researchers MadLicense and affects all known versions of Windows Server. [h/t ScreamingGoat]
Infosec industry
Threat/trend reports: AhnLab and Palo Alto Networks have recently published reports covering infosec industry threats and trends.
Trend Micro explores sale: Japanese cybersecurity firm Trend Micro is exploring a sale. According to Reuters, the company is valued at around $6.5 billion and is working with investment bankers to search for a buyer. Trend Micro recently reported a 13% year-over-year increase in second-quarter net sales.
Acquisition rumors: CrowdStrike is allegedly trying to purchase patch management company Action1. [Additional coverage in CybersecurityDive]
Congratulations: Congratulations to Ray [REDACTED], whose son, Sam, won the bronze medal at the Paris Olympics in the men's speed climbing event, breaking the world record along the way.
This is what it looks and sounds like when your child breaks the world record at the Olympics. This is shot live from my perspective. pic.twitter.com/M0MwnWFR1r
— Ray [REDACTED] (@RayRedacted) August 6, 2024
Pwnie Awards: The Pwnie Awards were handed out this weekend in Las Vegas. As usual, the Pwnies website was not updated. If I know them, they're probably gonna add the winners to it in March next year. However, it seems like CrowdStrike won the most epic fail award with a "well-deserved" late entry.
CrowdStrike accepting the @PwnieAwards for “most epic fail” at @defcon. Class act. pic.twitter.com/e7IgYosHAE
— Dominic White 👾 (@singe) August 10, 2024
Tool update—BBOT: Black Lantern Security has released v2 of its BBOT OSINT tool.
New tool—BadZure: Microsoft security engineer Mauricio Velazco has released BadZure, a tool to automatically set up misconfigured Azure Active Directory (now Entra ID) tenants.
New tool—TrailShark: AquaSec has open-sourced TrailShark, a plugin that connects Wireshark with AWS CloudTrail logs.
New tool—Grimoire: DataDog has released Grimoire, an open-source project that allows you to build data sets based on audit logs for common AWS attack techniques.
New tool—MaLDAPtive: Permiso's Daniel Bohannon and Solaris security engineer Sabajete Elezaj have released MaLDAPtive, a framework for LDAP SearchFilter parsing, obfuscation, deobfuscation and detection.
New tool—Shwmae: Security researcher Ceri Coburn has released Shwmae, a Windows Hello abuse tool.
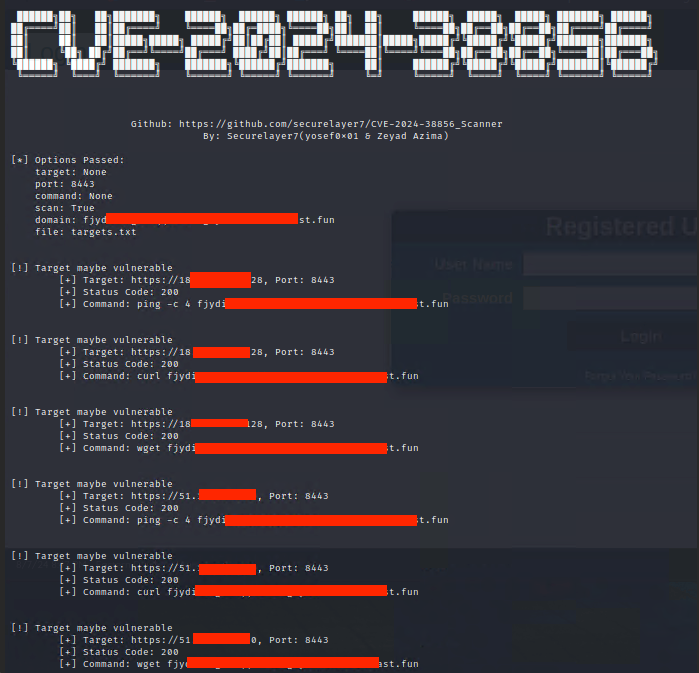
New tool OFBiz scanner: SecureLayer7 has published a scanner to find Apache OFBiz servers vulnerable to CVE-2024-38856.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss recent changes in a Chinese APT's tactics and how cyber security agencies have responded.
In this podcast, Tom Uren and Patrick Gray discuss the US's National Counterintelligence strategy, and that it highlights the risk that foreign intelligence entities will use personal information to target and blackmail individuals.
The Risky Business team has recently started publishing video versions of our podcasts. Below is the main weekly show, with Pat and Adam at the wheel!




