Risky Biz News: Tor launches new WebTunnel anti-censorship protocol
In other news: Crypto-phishing losses go over $100 million in the first two months of the year; 74 countries are now using commercial spyware; Airbnb bans all indoor security cameras.

This newsletter is brought to you by Yubico. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

The Tor Project has launched this week a new anti-censorship tool named WebTunnel.
WebTunnel is a new type of Tor bridge, a type of secret server that are not listed in Tor's public directory.
Because they are not public, Tor bridges are typically used in oppressive countries to allow users to connect to the Tor network.
For the past two decades, Tor bridges have run the obfs3 and obfs4 protocol to encrypt traffic and hide it from firewalls and censors. While such an approach has worked, it was only a matter of time until censors would have caught up.
Developments in anti-Tor censorship technology have allowed some countries and private companies in recent years to achieve better results when scanning, detecting, and then blocking Tor bridges.
Tor's new WebTunnel technology takes a different approach, and instead of using its own distinct encryption pattern, it works by taking regular Tor traffic and attempting to disguise it as regular HTTPS traffic.
Tor developers say WebTunnel will make it harder for censors to detect users connecting to a Tor node because the connection will look like any other WebSocket-like HTTPS connection out there (and there's a bunch of those).
Developers are positive WebTunnel will work out in practice because of recent approaches to internet censorship across the globe, where countries are moving to a deny-all type of model.
Instead of trying to fingerprint suspicious traffic, countries like China are moving to a model where they block anything that does not look like regular internet traffic. Since Tor's obfs4 and other anti-censorship protocols are using their own schemes, the way forward is with projects like WebTunnel that go for hiding in plain sight.
"Right now, there are 60 WebTunnel bridges hosted all over the world, and more than 700 daily active users using WebTunnel on different platforms. However, while WebTunnel works in regions like China and Russia, it does not currently work in some regions in Iran."
Breaches, hacks, and security incidents
France DDoS attacks: French officials say DDoS attacks of an "unprecedented intensity" have targeted government websites over the past weekend. A pro-Kremlin hacktivist group named Anonymous Sudan took credit for the attacks in posts on Telegram. The same group also targeted government sites last week in Sweden, Denmark, and Israel. [Additional coverage in France 24]
Roku hacked accounts: Streaming device maker Roku says that hackers gained access to more than 15,000 user accounts. The company says hackers broke into accounts where users had re-used passwords across multiple online profiles. Roku says that in some cases, the hackers attempted to purchase streaming hardware and streaming subscriptions from the compromised accounts.
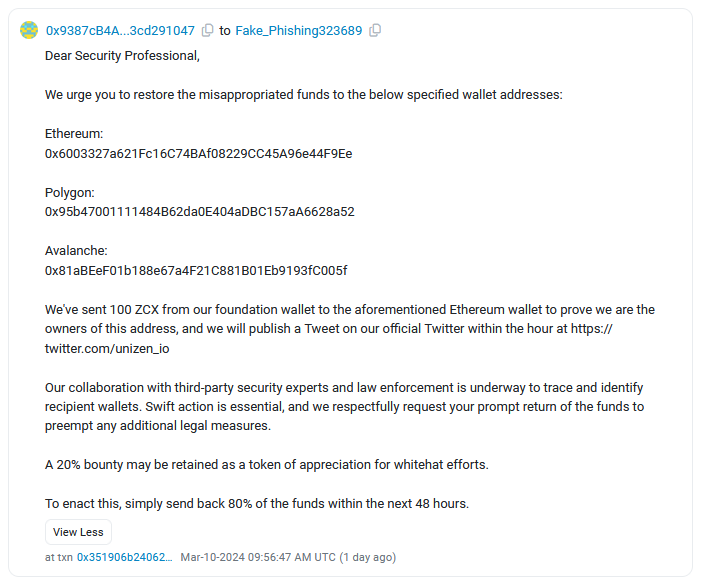
Unizen crypto-heist: Hackers have stolen $2.1 million worth of assets from cryptocurrency trading platform Unizen. The attackers are believed to have exploited a vulnerability in the company's smart contract. Unizen has sent a blockchain message to the hackers and offered a 20% white-hat bounty to the hackers. The company is willing to forget about the hack if the attackers return 80% of the stolen funds.
General tech and privacy
EU's use of M365: The European Commission violated data protection rules in its use of Microsoft 365. The EU's data protection watchdog says EU bodies did not take protective measures to prevent the transfer of personal data outside the EU. The Data Protection Supervisor (EDPS) has ordered the European Commission to take corrective measures and become compliant by December 9 this year. EU officials must configure their Microsoft 365 systems to stop sending personal data to Microsoft and its affiliates in non-EU countries.
Microsoft CISPE complaint: A trade group of cloud providers from Europe has accused Microsoft of unfair market practices. CISPE says Microsoft charges companies an extra 28% fee if they use Microsoft software on third-party cloud products. The group has threatened to file a complaint with the EU for anti-competitive practices.
Cloudflare Log Explorer: Internet infrastructure company CloudFlare has released its Log Explorer service in beta. It is one of the many services and features announced during the company's Security Week last week.
Airbnb bans indoor security cameras: Airbnb has banned the use of indoor security cameras in listings globally. The ban applies to all rooms in an Airbnb rental. Previously, the platform allowed homeowners to have security cameras in common areas only. The ban also applies to cameras that are turned off but are located inside a property.
US car privacy: Automakers are secretly collecting large quantities of data directly from customer cars as vehicle owners are avoiding installing car-related apps on their devices. According to a New York Times investigation, carmakers are selling this data to car insurers, which are then using it to calculate risk scores. Sold data includes all sorts of information except precise location data. This includes details such as trip lengths, hard braking, speeding habits, and other driving-related analytics.
PIGEON AI: Something we missed last year was this new academic paper on PIGEON, an AI model that can pinpoint geo-locations based on images. The AI model was inspired by the popular GeoGuessr game.
Meta sues former exec: Social media giant Meta has filed a lawsuit against a former executive for allegedly stealing private documents before leaving the company. Meta claims former vice-president T.S. Khuran moved employee pay docs and private contracts from Meta systems to his private email account before leaving the company. Khuran served as VP of Infrastructure at Meta for 12 years before moving to an unnamed AI cloud computing company. [Additional coverage in Bloomberg]
Quantum-safe email: Tuta has enabled quantum-safe encryption by default on all new Tuta Mail accounts.
Twitter losing bot fight: Twitter's bot account problem is getting out of control.
Speedometer 3: Mozilla, Google, and Apple have announced the release fo Speedometer 3, a universal browser benchmark tool.
Government, politics, and policy
Spyware proliferation: US intelligence agencies have confirmed that 74 countries across the world have purchased and are using commercial spyware. In a Senate hearing, US spy chiefs say spyware is increasingly being used to target dissidents and journalists. Officials also warned the US is struggling to counter ransomware attacks and the growing use of AI in influence operations. [Additional coverage in TechCrunch]
AI crime prosecution: The US Department of Justice says it will seek harsher sentences for individuals who use artificial intelligence to commit white-collar crimes. This includes using AI to commit fraud, price-fixing, and market manipulation. The sentencing guidelines will apply to both individual and corporate defendants alike.
US 2025 budget proposal: A proposed US federal budget for fiscal year 2025 would see more than $13 billion allocated to cybersecurity projects, up from the $12.7 billion allocated in 2024. [Additional coverage in CyberScoop]
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Derek Hanson, Yubico’s VP of Solutions Architecture and Alliances. Derek covers the different reasons organisations are investing in Passkeys, what organisations need to know to deploy them successfully, and warns that too often current deployments are too focused on authorisation rather than looking at the end user holistically.

Cybercrime and threat intel
Threat/trend reports: Some infosec reports covering industry threats and trends came out from GitGuardian, Sophos, Symantec, IRONSCALES, Kaspersky, and the ATOS Group.
2023's leaked secrets: Developers have leaked more than 12 million secret tokens via GitHub commits last year. Almost one million of these secrets were Google API keys, according to DevSecOps company GitGuardian. The company says that only 1.8% of the repo owners they contacted last year took steps to plug the leaks.
Muddled Libra: Palo Alto Network has published an in-depth profile on Muddled Libra, a threat actor that has been active since mid-2022 and joined the AlphV RaaS in 2023.
Meson attacker: Cloud security firm Sysdig has detected a coordinated attack against the Meson blockchain. The company says a threat actor has flooded the blockchain with more than 6,000 nodes in an attempt to mint new Meson tokens. The Meson token is set to officially launch later this week, on March 15. Sysdig says the attacker has used compromised cloud accounts to deploy the nodes. At the current rate, the hacked accounts are set to rack up a bill of around $22,000/month for their legitimate owners.
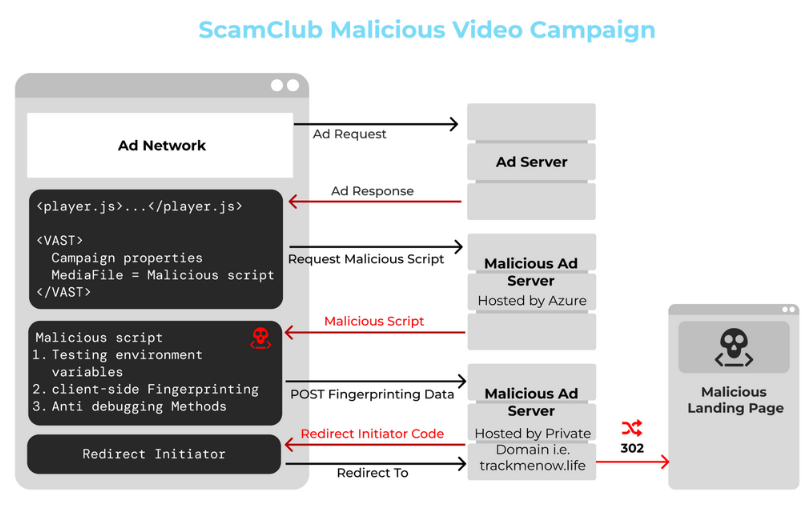
ScamClub: The ScamClub malvertising group shifted operations in February this year from using classic web ads to malicious video ads. The video ads work as the group's past web ads and redirect users to sophisticated financial scams. Ad security firm GeoEdge says that almost 90% of the group's malicious ads targeted mobile devices. The rest targeted desktops, consoles, and smart TVs.
Crypto-phishing losses: Cryptocurrency users have lost more than $100 million to phishing in the first two months of the year. Users lost $58 million in January and another $46 million in February. Attacks involved a new form of phishing kit named crypto-drainers that can hijack and automatically empty cryptocurrency wallets.
PyPI crypto-thefts: ReversingLabs researchers have found seven Python packages on the official PyPI repository containing code to steal mnemonic phrases for cryptocurrency wallets. The campaign (named BIPClip) has been active for more than a year, with the oldest package dating back to December 2022. The packages posed as open-source libraries for working with mnemonic phrase formats.
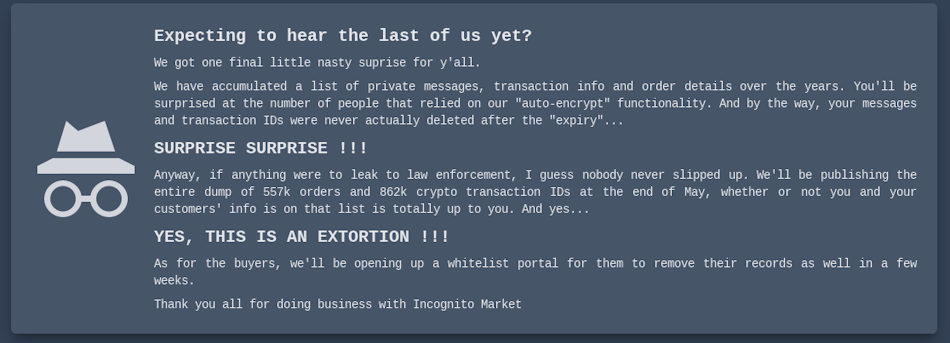
Dark web market extorts its own users: The administrator of the Incognito dark web marketplace is extorting the site's past users. Site admin Pharoah is demanding payments from $100 to $20,000 from the site's vendors and buyers. In a message posted on its frontpage, Pharoah mocked users for trusting the platform and threatened to publish chat logs and cryptocurrency transaction IDs. Such data would allow law enforcement to track down some of the site's vendors and buyers. The Incognito market was known for the sale of drugs, forged documents, and stolen data. The extortion comes after Pharoah exit-scammed last week and stole all user funds deposited on the platform. [Additional coverage in KrebsOnSecurity]
Malware technical reports
PurpleFox: Threat detection engineer Doomdesire has published a blog post on how to detect installations of the PurpleFox exploit kit.
Sponsor Section
YubiKeys slashes exposure to security breaches from phishing and credential thefts by 99.9% and reduces administrative overhead. Create your own customized Forrester Consulting Total Economic Impact™ study tailored for your organization here: Yubi.co/TEI
APTs, cyber-espionage, and info-ops
i-SOON leak: Hunt & Hackett looks at the leak from Chinese hacker-for-hire contractor i-SOON and its possible ties to at least three Chinese APTs—Poison Carp (also known as Evil Eye, Earth Empusa, EvilBamboo), Jackpot Panda, and APT41 (also known as Double Dragon, Wicked Panda, Bronze Atlas).
Dr.Web report: Russian antivirus maker Dr.Web has published a report on a suspected APT report and its tooling in an attack that targeted a Russian mechanical engineering enterprise.
Vulnerabilities, security research, and bug bounty
Patch Tuesday: Yesterday was the March 2024 Patch Tuesday. We had security updates from Adobe, Microsoft, Cisco, SAP, QNAP, Zoom, AMD, Intel, Siemens, and Schneider Electric. The Android Project, Apple, Kubernetes, Drupal, VMWare, JetBrains, HikVision, Fortinet, and Unbound released security updates last week as well. This month, Microsoft patched 64 vulnerabilities, no zero-days.
TeamCity drama: Software company JetBrains has blamed security firm Rapid7 for the recent wave of attacks on TeamCity servers. JetBrains says Rapid7's insistence on publishing details and a PoC for two TeamCity vulnerabilities has led to attacks on customer servers hours after a patch was out. JetBrains's accusation is the latest chapter in the drama between the two companies. Rapid7 accused JetBrains last week of trying to bury news about the two security flaws by not telling customers the latest firmware update contained security fixes.
"We firmly believe that releasing the full technical details of a vulnerability and the exploit steps simultaneously with its fix is entirely unethical and harmful to our customers, provided that enough details are made publicly available to allow customers to fully understand the risks and protect themselves against the vulnerability."
iwd vulnerability: SPR researcher Alex Radocea has published details on CVE-2024-28084, a memory corruption vulnerability in the iNet Wireless Daemon (iwd) WiFi firmware.
MS Outlook RCE: NetSPI researchers have published details on CVE-2024-21378, an RCE they found in the Microsoft Outlook client. The issue was fixed in February.
NextChat unpatched bug: Horizon3 has published details about an unpatched SSRF vulnerability in NextChat, a generative AI chatbot widget. Researchers say they disclosed the vulnerability after the vendor failed to release a patch in almost three months. Tracked as CVE-2023-49785, the vulnerability can allow threat actors to read files on servers that run the NextChat widget. Horizon3 says the NextChat app is currently installed on more than 7,500 internet-connected servers.
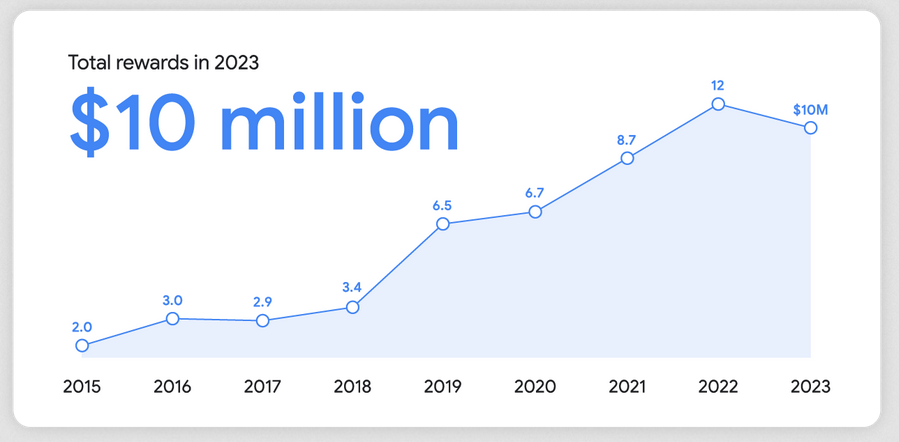
Google bug bounty: Google paid more than $10 million to security researchers last year for vulnerability reports across its products. The sum is down from the $12 million the company paid to researchers in 2022. The money went to 632 researchers, with the highest bounty last year being $113,337. More than $3.4 million was awarded for Android bugs and another $2.1 million for Chrome vulnerabilities.
Infosec industry
Symantec+Carbon Black: Broadcom has merged Carbon Black into its Symantec cybersecurity division. The two brands will continue to operate separately. Broadcom acquired the Carbon Black Black last year as part of its $69 billion acquisition of VMware. The company initially planned to sell off Carbon Black. Broadcom previously acquired Symantec for $10.7 billion in August 2019.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at recent efforts to disrupt ransomware gangs and discuss what could make these efforts more effective.




