Risky Biz News: Top websites have sucky password policies
In other news: Feds seize RSocks proxy network; US funds VPNs in Russia; and Patch Tuesday is not "ending."
This newsletter is brought to you by Airlock Digital, Rumble Network Discovery, Proofpoint, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
A team of academics from Princeton University analyzed the password policies of today's top 120 of the most popular English-speaking websites and found that even after years of "recommendations" from security experts, the vast majority of these sites still had ridiculously bad rules for when users had to create an account password.
The team—led by the notorious privacy advocate and Princeton professor Arvind Narayanan—focused their research on three of the most basic industry best practices for when setting up a new password:
- Check user passwords against lists of leaked and easily-guessed passwords;
- Provide real-time password strength meters;
- Do not require specific character classes in the password's make-up.
But while these sound like very simple requirements, they are not widely implemented. The research team said that only 15 of the 120 websites they analyzed followed these recommendations.
In fact, their findings are absolutely astounding(ly bad):
- More than half (71/120) of websites do not check passwords at all, allowing 40 of the most common passwords (e.g., "12345678", "rockyou") to be used as account credentials, with no warning to the user that they may be at risk of account hijacking.
- Only 23 of the 120 websites used password strength meters, and ten of these sites misused meters in the sense of nudging users toward specific types of characters.
- In addition, 54 out of the 120 websites still require specific character classes such as digits or special characters to be included in the password, a practice that has been shown to be dangerous, as users tend to select simpler and easier to-remember passwords as a result.
The research team gives Facebook as a good example of how many of these policies appear to be cobbled together with no actual thinking behind the process and how websites are stimulating users toward using weaker passwords.
We facepalmed a lot while researching the password policies of 120 websites, but this took the cake. Facebook tells users 20-char random pw's are weak, but "Passw0rd" is strong, because hackers could never guess that pw's might have uppercase or digits. passwordpolicies.cs.princeton.edu
— Arvind Narayanan (@random_walker) 4:23 PM ∙ Jun 15, 2022
The researchers also looked at some of the reasons why, in 2022, so many popular websites still haven't learned anything from the hacks from the last decade.
One of the reasons they put forward was that companies are shifting their attention to multi-factor authentication, and many websites may not care to strengthen their password policies. Another was related to auditors.
"Websites need to pass security audits, and the firms who do these audits, such as Deloitte, recommend or mandate outdated practices," researchers said.
Breaches and hacks
BeanVPN leak: Romanian-based VPN provider BeanVPN appears to have leaked 25 million records. According to CyberNews, the leaked data included details such as user device IDs, Play Service IDs, internet protocol addresses (IPs), and connection timestamps, among other diagnostic information.
StoreHub leak: Elsewhere, an Elasticsearch server owned by PoS software vendor StoreHub also leaked the personal data of thousands of customers (companies) and more than one million of their staff, according to SafetyDetectives.
General tech and privacy
Rust Foundation grants: The Rust Foundation has announced its first-ever grants; funds the Foundation will be providing to open-source developers and programs for improving the Rust programming language and its integration with other projects. In total, $650,000 were dispensed to 41 recipients, including for projects for improving Rust's documentation, the Crates package repository, its Windows library, and others.
Problematic bill: A bill proposed by Sen. Blumenthal (D-CT) meant to force companies like Apple and Google to open their in-store payment systems to other payment options is considered too broad, as it requires the tech companies to open all their APIs, including those used for sensitive operations, like encryption and backups. Even worse, as spotted by John Hopkins Prof. Matthew Green, the bill also contains a clause that can allow US law enforcement to close certain APIs to companies or entities that may be considered a "national security threat," which Green argues could be used to go after apps of encrypted IM solutions.
While that part is fine, there is an amendment to the bill that may allow manufacturers to close their APIs to people who are “national security, intelligence or law enforcement risks”. I’m very worried this could be used to block out encryption app developers.
— Matthew Green (@matthew_d_green) 10:12 PM ∙ Jun 15, 2022
Instagram sabotage: Around 25 Iranian Instagram accounts that shared stories of sexual violence and posted about the Iranian MeToo movement this spring were flooded with subscriptions from bot profiles. The Qurium Foundation, which investigated this harassment campaign, believes the attackers were trying to get the accounts banned for boosting.
Privacy legislation: Senator Elizabeth Warren (D-Mass.) introduced a bill on Wednesday to regulate the sale of Americans' sensitive information. The bill—named the Health and Location Data Protection Act—would prohibit the sale or transfer of information about location and health data without valid authorization. [More in The Record]
Alexa data used for ads: A new lawsuit filed this week claims that Amazon used audio recorded through the Alexa personal assistant to target users with personalized ads, a practice Amazon has long denied.
Google fined in Russia: A Russian court has fined Google 15 million rubles (~$260,000) after the company has refused to store the data of Russian citizens on servers within the Russian Federation.
Government, politics, and policy
Ukraine accuses Russian hackers: Yurii Shchyhol, head of Ukraine's State Service of Special Communications and Information Protection, has accused Russia's state hackers of intentionally targeting non-military targets and critical infrastructure:
Just as the Russian army routinely disregards the rules of war, Russian hackers also appear to have no boundaries regarding legitimate targets for cyber-attacks. Popular targets have included vital non-military infrastructure such as energy and utilities providers. Hospitals and first responders have been subjected to cyber-attacks designed to disrupt the provision of emergency services in the immediate aftermath of airstrikes.
ICO funding: The UK government will allow the country's privacy watchdog, the Information Commissioner's Office, to keep a small portion of the fines they levy against companies that break data protection laws. The sum they can keep will be capped at £7.5 million/year, and the agency will be audited by the government to make sure the mechanism is not abused.
RT loses lawsuit in France: The French division of the RT Russian news agency lost a lawsuit it filed in France against a security researcher and Atlantic Council senior fellow Jean-Baptiste Jeangène Vilmer. RT France sued Vilmer after the researcher published a 214-page report [PDF] in 2018 exposing RT's role in Russia's international disinformation, misinformation, and propaganda machine.
Russia prepares to ban foreign software: Russian officials have put forward a bill on Thursday that would ban the purchase and use of any foreign-made software inside Russia's critical infrastructure following January 1, 2025, TASS reported. Since March this year, the use of foreign software inside critical sectors is only allowed with specific permission from the Russian government.
US government funding: After Russia's invasion of Ukraine, the US government has pushed new and increased funding to three companies that build VPN software, Reuters reported on Wednesday. Between 2015 and 2021, the three companies—nthLink, Psiphon, and Lantern—had received around $4.8 million in funding, but since February this year, that sum has increased by almost half to make sure the three cope with the rise in Russian users utilizing their services. Reuters said that after the start of the war, QR codes linking to the three VPNs are being spread around Moscow.
Cybercrime and threat intel
Racoon Stealer is back: A new version of the Racoon Stealer malware, dubbed V2, is being traded on underground cybercrime forums, per S2W Talon. The malware's creator suspended operations in late March this year, claiming that a key developer died during Russia's invasion of Ukraine.
RSocks seized: US authorities seized the website and infrastructure of RSocks, an online service selling access to proxy servers all over the world. Authorities said RSocks had been built on top of a botnet of hacked computers, smartphones, and IoT devices. The botnet, supposedly operated by Russian cybercriminals, had allegedly grown from 325,000 hacked devices in 2017 to millions of devices this year, the DOJ said in a press release on Thursday. [See Wayback Machine page of the old RSocks website here.]
Call center and BEC arrests: Interpol said it detained more than 2,000 suspects as part of an international crackdown against BEC scammers, online fraudsters, romance scammers, money launderers, and scammy call center operators. The arrests were part of Operation First Light 2022, and authorities said they also froze more than 4,000 bank accounts and seized more than $50 million worth of stolen funds.
Netherlands arrest: Dutch police have detained a 22-year-old from the city of IJmuiden on suspicion of being part of an online cybercrime group specialized in phishing and money laundering. The suspect had been detained at the request of Belgian authorities.
icloudripper4you sentenced: A Florida judge sentenced a 41-year-old man to nine years in federal prison for hacking into iCloud accounts of more than 4,700 users, stealing sensitive images, and then sharing and trading the data on Anon-IB, a now-defunct website famous for hosting "revenge porn." The man, Hao Kuo Chi, 41, of California, went on the forum as "icloudripper4you" and authorities said he obtained and shared sensitive images for more than 500 of his hacked victims.
Russian hacker arrested: Russian officials have detained a man named Oleg Rusakovich on accusations of hacking into the systems of the Russian Federal Customs Services and modifying entries in the system to make sure certain goods cleared customs procedures.
Telerik attacks: Sophos has a report out on a series of attacks against Telerik UI-based apps. The final payload in these attacks has been Cobalt Strike beacons and crypto-miners.
Houdini returns: ISC SANS is reporting on new campaigns distributing Houdini, a very old remote access trojan.
Magecart attacks: Sucuri said it found a web skimming operation attacking WooCommerce-based shops that exfiltrates payment card data to Telegram channels.
Initial access prices: Kaspersky's threat intel team has a good report on the current prices on the initial access market for access to hacked corporate and government networks.
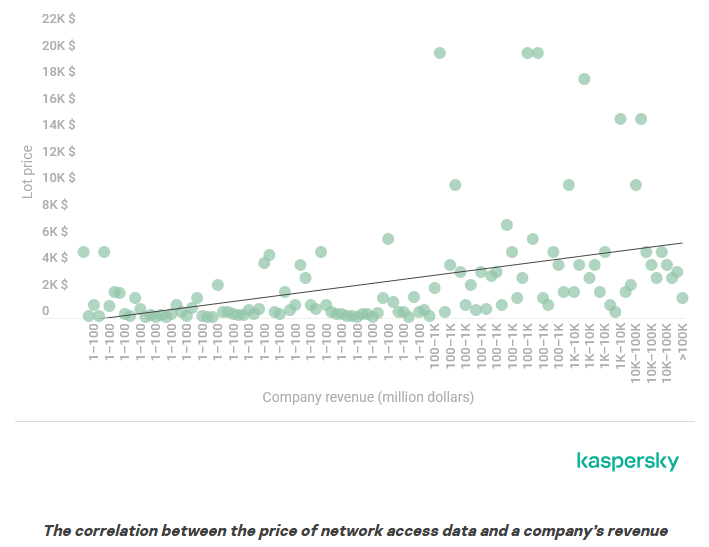
Malware technical reports
Panchan: In a report on Wednesday, Akamai detailed Panchan, a new peer-to-peer botnet and SSH worm that emerged in March 2022 and has been actively compromising Linux servers since. The botnet is written in Go, and its main purpose appears to be cryptocurrency mining.
MaliBot: F5 says that while it was tracking FluBot, they found a new Android banking trojan named MaliBot. Current versions of the malware can carry out web injection and overlay attacks, steal MFA codes, steal authentication cookies, steal wallet data, steal SMS messages, and provide VNC access to infected devices for remote access, among many other features.
Redline Stealer: Qualys has a report out on the Redline Stealer and a recent campaign where threat actors used ZIP archives with fake cracked software to distribute the malware.
APTs and cyber-espionage
Hermit: Security firm Lookout has published a report on Hermit, a piece of "enterprise-grade Android surveillanceware" that was used to spy on Kazakh government officials. The company said the malware was developed by Italian spyware vendor RCS Lab SpA and telecommunications company Tykelab Srl, and that previous instances where Hermit was also deployed included Italy (by law enforcement) and Syria.
Indian police framed reporters: Researchers at security firm SentinelOne and nonprofits Citizen Lab and Amnesty International told Wired that they found evidence to formally link the Pune Police Department to a case where fake evidence was planted on the laptops of two Indian activists (Rona Wilson and Varvara Rao) the same department detained in 2018 on terrorism-related charges. Previous reporting on their case had found that the evidence that led to their arrest was planted on their devices, but investigators could not identify who planted the evidence. The two activists, along with 16 other suspects, are still on trial in India.
DriftingCloud: Volexity said in a report on Wednesday that it spotted a new Chinese APT using zero-day in the Sophos XG firewall earlier this year in March. Named DriftingCloud, this threat actor used the Sophos XG zero-day (CVE-2022-1040) to install web shells on the firewall, create VPN accounts for future access, and then proceeded to intercept and tamper with DNS traffic in order to redirect the victim organization's employees to malicious servers. These servers performed MitM attacks and collected credentials and authentication cookies for other internal apps, helping the attackers escalate their access to other internal company resources.
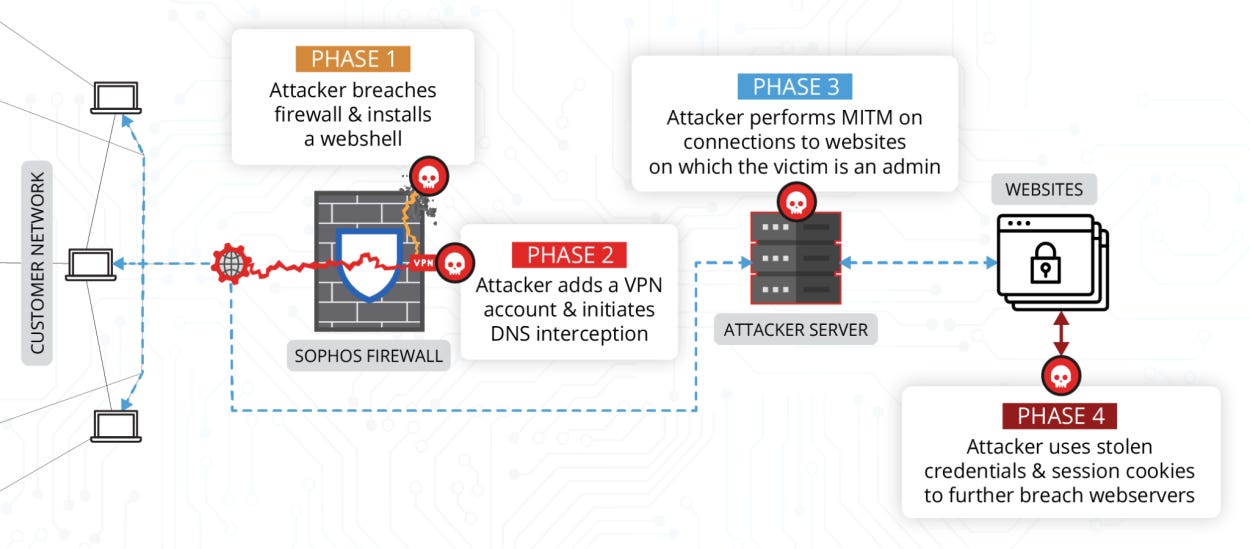
Vulnerabilities and bug bounty
Legal threats: A Polish security researcher said they received a legal threat from Powertek after disclosing vulnerabilities in the company's power distribution units. The company backed down on the threat a few hours later, calling it a miscommunication around the first-ever bug report they received.
Just an update: had a phone chat with their Swiss reseller. In general it's the same old story: Reasonable people mishandling the 1st ever vulnerability disclosure due to not knowing the industry accepted standard. They are interested in upping their security game, which is great
— Gynvael Coldwind (@gynvael) 3:38 PM ∙ Jun 13, 2022
Demonic vulnerability: Security researchers from Halborn discovered a vulnerability affecting many major cryptocurrency wallets. Named Demonic, the vulnerability takes place in situations where certain cryptocurrency wallet browser extensions accidentally store the wallet owner's secret recovery phrase on disk, in plaintext, allowing attackers to recover it in situations where they have access to the victim's device. Impacted wallets include MetaMask, Brave, Phantom, and xDefi. The vulnerability is tracked as CVE-2022-32969, and all the wallet makers have released fixes, according to the researchers.
Ninja Forms vulnerability: WAF provider Wordfence disclosed a major vulnerability in Ninja Forms, one of the most popular WordPress plugins today. The vulnerability allows unauthenticated remote code injection, has a CVSS score of 9.8/10, and patches are already out.
SharePoint and OneDrive ransomware: Proofpoint published new research this week detailing a possible scenario where a threat actor who gained access to a customer's SharePoint or OneDrive accounts could modify the file auto-saving versioning limit to "1" and then encrypt files with ransomware twice, and by doing so ensuring that the victim organization doesn't have access to previous versions of the locked files. The good news is that while the attack is plausible, in the case of a ransomware attack, Microsoft support staff can restore a customer's files to any previous point from the previous 14 days, according to this support page and Matt Swann, Chief Security Architect for OneDrive and SharePoint at Microsoft.
More Hertzbleed: After earlier this week, academics published details about the Hertzbleed attack a team of Intel researchers has published their own paper on the topic, along with more extensive and detailed mitigations to prevent possible attacks.
One might even argue it's disingenuous and an abuse of trust that will discourage cooperation with a group Intel desperately needs to work more closely with.
— Dan Goodin (@dangoodin001) 6:25 PM ∙ Jun 15, 2022
RDP vulnerability finally patched: CyberArk has a write-up on the backstory of a vulnerability in the Windows Remote Desktop feature that was initially disclosed in January and needed a second patch in April to plug all the attack holes.
Patch Tuesday is not ending: Someone started some dumb rumor that Microsoft will stop providing security updates during Patch Tuesdays. That's obviously false, Microsoft told SecurityWeek.
Infosec industry
GitHub updates: GitHub said on Wednesday that every time it would detect a threat actor's attempt to insert malware into open-source projects, it would also add an entry in its GitHub Advisory Database, a place the company previously logged only vulnerability-related issues.
BlackHat Arsenal: The schedule for this year's Black Hat Arsenal edition has been made public. Black Hat Arsenal is the conference tracklist where security researchers present new infosec-related tooling.
Eclypsium: Firmware security firm Eclypsium has expanded its leadership team.
Follina tooling: Security researcher Marcus "MalwareTech" Hutchins has released a tool that can extract payloads from Office files weaponized with the Follina zero-day.




