Risky Biz News: Three years later, US charges Joker's Stash carding forum admin
In other news: WiFi defacements at UK rail stations; new US bill introduces minimum cybersecurity standards for healthcare entities; Kia patches major car hacking loophole.

This newsletter is brought to you by Resourcely, the company that can help you manage Terraform securely. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

The US Department of Justice has charged a Russian national for operating the now-defunct Joker's Stash carding forum.
Officials say Timur Shakhmametov went online under the aliases of JokerStash and Vega. He launched Joker's Stash in October 2014 and shut down operations in February 2021, two months after Interpol and the FBI seized some of its front-facing server infrastructure.
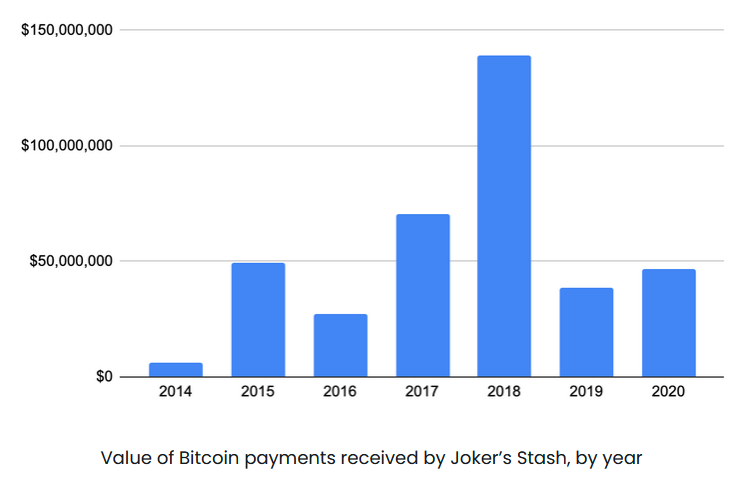
Threat intel companies have estimated the forum made between $280 million to $1 billion by selling more than 40 million payment card details.
For many years, Shakhmametov and Joker's Stash played a crucial role in the cybercrime underground. The site was the de-facto epicenter of the carding world from 2017 to 2020—which was also the reason why it attracted the FBI's gaze at the end of 2020.
But US authorities don't look like they're willing to give Shakhmametov a chance to retire in peace just because he shut down the forum on his own.
In fact, a serious grudge has been brewing, and through its Rewards for Justice Program, the US State Department is not only offering a $10 million reward for information on Shakhmametov but also offering another $1 million for info on the rest of his admin staff.
US sanctions (more) Russian crypto exchanges helping ransomware gangs
Shakhmametov's charges didn't come in their own separate case, but they were bundled in a bigger indictment that charged another Russian national named Sergey Ivanov.
US officials say Ivanov is one of the Russian cybercrime ecosystem's biggest money laundering tycoons. He allegedly ran Cryptex, PM2BTC, UAPS, and PinPays—services that laundered cybercrime proceeds for carding, fraud, and ransomware groups.
Officials say Ivanov specifically advertised the sites in cybercrime circles. The sites allowed users to register without providing their real identities, move cryptocurrency funds through its network, and then provided crypto-to-ruble exchange services.
Ivanov was allegedly involved in laundering $1.15 billion, with almost a third of the funds being linked to criminal activity and $115 million to ransomware alone.
Ivanov's indictment comes a day after Dutch police seized server infrastructure associated with Cryptex and PM2BTC.
Ivanov, Cryptex, and PM2BTC were also sanctioned by the US Treasury.
The US has now sanctioned five Russian-based cryptocurrency exchanges involved in laundering ransomware profits:
Breaches, hacks, and security incidents
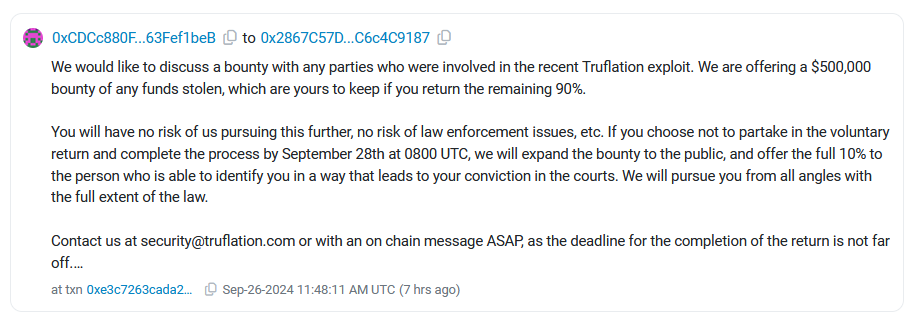
Trueflation crypto-heist: A threat actor has stolen almost $5 million worth of assets from cryptocurrency platform Trueflation. The company has offered a $500,000 to the hacker as a "reward" for returning the stolen funds. It has given the hacker three days to comply or make the reward available to security researchers to track them down.
Ether.fi DNS hijack: DeFi platform Ether.fi says it was the target of a DNS hijack after threat actors took control of its Gandi account.
French citizens data breach: Cybernews and SecurityDiscovery have found an unsecured Elasticsearch server where an unidentified entity was assembling a database with details on over 95 million French citizens. The database was secured after another security researcher notified the hosting provider. There appears to be some drama surrounding Cybernews' way of reporting on data breaches, with the news org not bothering to notify affected entities.
WiFi network defacements in the UK: The WiFi networks of 19 UK train stations were hacked on Wednesday to redirect travelers to a page with Islamophobic messages and a list of terrorist attacks that had taken place across the UK and Europe. WiFi networks were hacked across the UK's largest cities, such as London, Manchester, Leeds, and Birmingham. The incident appears to originate at Telent, a third party contractor that provides WiFi access for Network Rail. [Additional coverage in the BBC]

General tech and privacy
DOJ sues Visa over market monopoly: The US Department of Justice has filed an antitrust lawsuit against payments processor Visa for monopolizing the debit networks market.
Cloudflare adds Zstandard support: Cloudflare is adding support for Meta's Zstandard (zstd) compression algorithm.
Tor merges with Tails: The Tor and Tails projects have merged.
Privacy complaint against Mozilla in the EU: European privacy group noyb has filed a complaint against Mozilla with Austria's data privacy regulator. The complaint is over Mozilla enabling the Privacy Preserving Attribution by default for its users. This is a feature that measures the effectiveness of ads inside users' browsers.
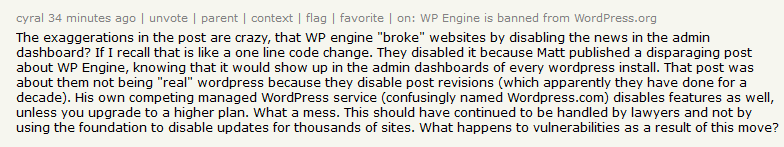
WordPress.org-vs-WP Engine drama: WordPress.org, the maintainer of the WordPress open-source CMS, has sent a cease-and-desist letter to WordPress-hosting service WP Engine for unauthorized usage of the WordPress trademark. The team also banned WP Engine from using any of the WordPress.org resources going forward. The team took the drastic option after WP Engine removed the news widget from WordPress sites hosted on its platform. It removed the widget after WordPress creator Matt Mullenweg published a blog post attacking WP Engine that got pushed to all WP Engine customers via the dashboard news widget. Mullenweg called out WP Engine for removing the "post revisions" feature from the version of WordPress it was hosting on its servers. All of this looks like Mullenweg is using the WordPress.org brand to attack WP Engine, a rival of his WordPress.com commercial service—also known to disable and charge for core WordPress features.
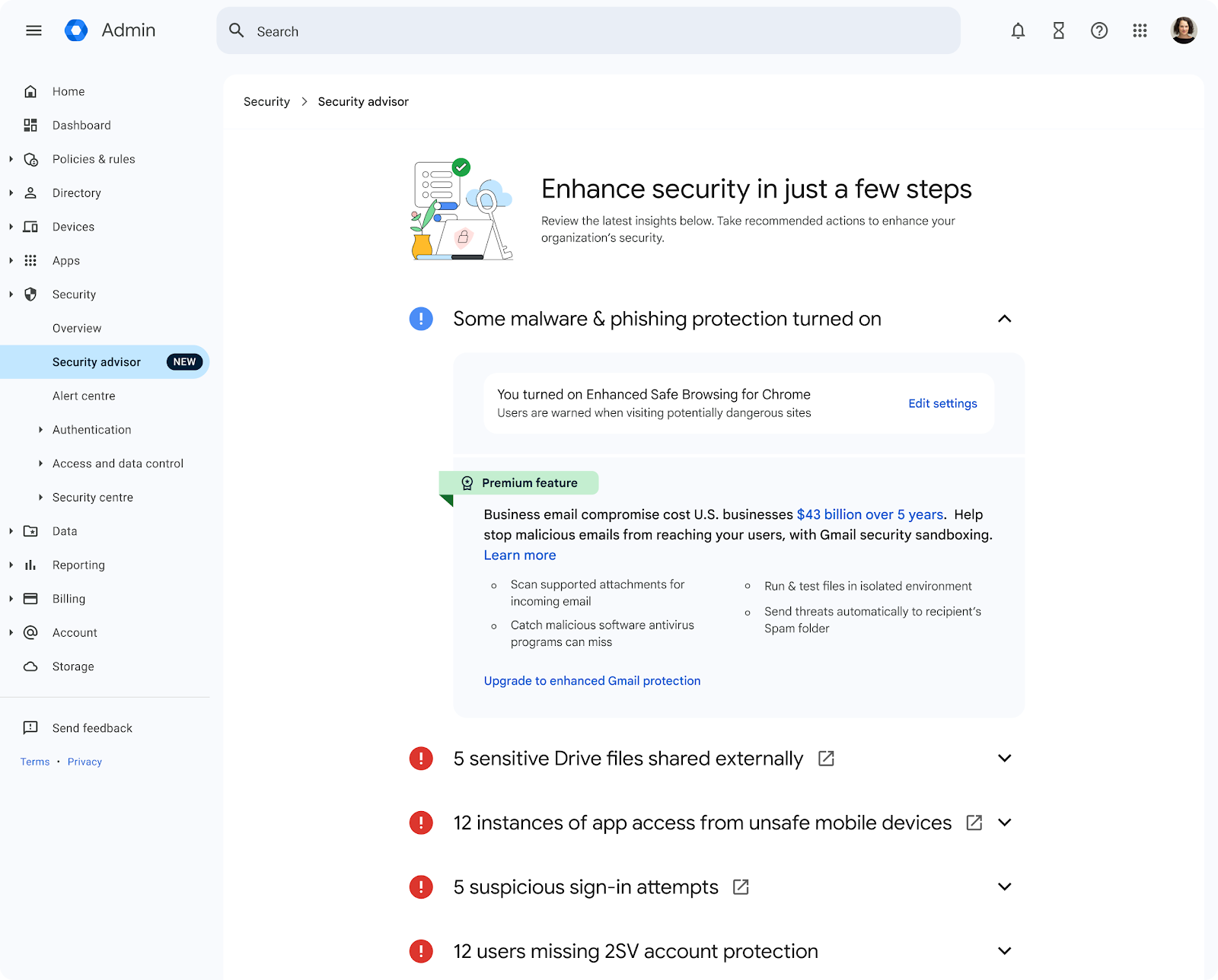
Google Workspace Security Advisor: Google launched a new security feature for its Workspace platform named Security Advisor. The feature works by scanning an organization's setup and providing recommended settings that improve its security posture. Google developed the feature to allow admins to easily determine when security features were accidentally changed or were never enabled.
Government, politics, and policy
EU AI Pact: Over 100 tech companies have signed a voluntary pledge for the safe development of AI systems in the European Union. Signatories have agreed to follow principles from the EU's AI Act before the new regulation is scheduled to go into effect. This includes the trustworthy and safe development of AI systems that don't harm human rights, transparent labeling, and human oversight. Some of the biggest names who signed the pledge include OpenAI, Microsoft, Google, and Amazon. Social media giant Meta did not sign the pact.
G7 cyber group warning: The G7 cyber group has called on the financial sector to prepare for the impending threat of store-now-decrypt later attacks that will be brought in by the development of better quantum computing tools. [Additional coverage in The Record]
US Health Infrastructure Security and Accountability Act: US lawmakers have introduced a new bill that would set mandatory minimum cybersecurity requirements for healthcare and connected entities. The new Health Infrastructure Security and Accountability Act also introduces jail time for CEOs who lie to the government about their company's cybersecurity practices. The bill was introduced by Senate Finance Committee Chair Ron Wyden (D-Ore.) and Senator Mark Warner (D-Va.) and is a direct result of the ransomware attack against Change Healthcare that crippled large parts of the US healthcare system for months.
US looking at Temu: US lawmakers are exploring a possible investigation of Chinese online marketplace Temu and how the company handles the data of American citizens. Officials have asked the FBI and the SEC to evaluate if the shopping app represents a national security risk for the US. The investigation follows the same pattern as what happened to TikTok, with US officials looking at the Chinese government's control over the app and where Temu stores US consumer data. [Additional coverage in The Record]
CrowdStrike outage House hearing: CrowdStrike senior vice president Adam Meyers testified before the House Homeland Security Committee's cybersecurity subcommittee on Tuesday about the company's IT outage from late July. Besides Meyers apologizing for the outage, the meeting was kind of a nothinburger. [Additional coverage in The Guardian]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Resourcely co-founder and CEO Travis McPeak about some of the hard and uncomfortable truths about the role of security teams inside a company.

Cybercrime and threat intel
Twelve and BlackJack connections: Russian security firm Kaspersky says that two hacktivist groups named Twelve and BlackJack appear to originate from the same entity. The company says the two groups "use similar malware, distributing and executing it using the same methods." Both groups appeared in late 2023 when they started attacking Russian companies. Kaspersky says Twelve and BlackJack pose as financially motivated threat actors but are actually focused on stealing data and destroying IT environments.
Sniper Dz: A phishing service named Sniper Dz is behind more than 140,000 phishing websites deployed in the wild this year. Palo Alto Networks says the service grew its userbase after allowing customers free phishing templates. The catch—Sniper Dz admins also get a copy of the phished data.
LOL phishing campaign: Bitdefender says a threat actor is targeting League of Legends players with malicious emails designed to infect them with the Lumma infostealer.
WalletConnect scam: Check Point looks at a malicious crypto-wallet app found on the official Play Store that stole users' crypto passwords and then emptied their accounts.
SMTP abuse: Cisco Talos has published a report on all the tricks threat actors use to abuse third-party infrastructure to send email spam from "clean" email servers. This includes calendar and quiz apps, unsecured contact forms, online account registration forms, event sign-ups, and unsecured SMTP servers themselves.
CISA warns of common attacks on ICS: CISA says that threat actors are continuing to hack into OT and ICS networks using unsophisticated techniques such as default credentials and brute-force attacks. The agency has asked critical sector operators to secure systems and follow basic cybersecurity recommendations. CISA's statement comes days after a ransomware group crippled and forced a Kansas water utility to switch to manual mode.
Joint AD hack mitigation guide: Cybersecurity agencies from Australia and the US have published joint guidance on how companies can recover from having their Active Directory server compromised.
Threat actors are leaving Telegram: After Telegram announced its plan to share data with law enforcement, multiple threat actors have announced their intention to leave the platform. [Additional coverage in KELA]
Malware technical reports
LummaC2: Google Cloud's security team has published a report looking at the control flow obfuscation techniques used by the LummaC2 infostealer.
Rhadamanthys: The Rhadamanthys infostealer has introduced AI-driven capabilities to extract cryptocurrency seed phrases from images.
DCRat: Netskope has published a report on a recent DCRat campaign abusing HTML smuggling. DCRat (Dark Crystal RAT) is a remote access trojan offered through a MaaS platform since 2018.
Pandora hVNC: French security firm Intrinsec has published a report on the infrastructure of the Pandora hVNC remote access toolkit.
BBTok: G DATA researchers look at BBTok, a banking trojan active on the Brazilian market.
DragonForce launches RaaS: The DragonForce ransomware group launched a fully-fledged Ransomware-as-a-Service platform in June this year. The new RaaS promises to allow affiliates to keep 80% of ransoms if they use the group's ransomware in attacks. The group started out as a small ransomware operation in August of last year and got notoriety after successful attacks on the government of Palau and the Ohio Lottery earlier this year. It uses a ransomware strain based on leaked versions of the Conti and LockBit families. It also steals data for double-extortion schemes and manages a dark web leak portal. [Additional coverage in Group-IB]
Sponsor Section
Resourcely co-founder and CEO Travis McPeak held an off-the-record conversation at this year's Blackhat Campfire Stories, talking about some of the hard truths CISOs don't usually talk about.

APTs, cyber-espionage, and info-ops
SloppyLemming: Cloudflare's threat intel team has published a report on a suspected Indian APT that has abused its Workers service for the past two years in an espionage campaign targeting Pakistan, Nepal, Sri Lanka, Bangladesh, and China. The company calls the group Sloppy Lemming but says it's the same thing as CrowdStrike's Outrider Tiger.
Iran info-ops: CyFirma and Radware have published reports looking at Iran's election meddling activities, including the use of residential proxy services to make their activity look like it originates from the US.
Flax Typhoon: The Natto Thoughts team has published a profile on the Integrity Technology Group, a company US officials claim is behind the Raptor Train IoT botnet. US officials track the botnet's activity as the Flax Typhoon APT.
Salt Typhoon: The Wall Street Journal cites sources claiming that Chinese hackers have breached new US internet service providers. This is apparently different from the previous Volt Typhoon intrusions and are the work of a different cluster tracked as Salt Typhoon. The intrusions took place via Cisco networking gear and Microsoft is involved in the investigation.
MimiStick: Russian security firm FACCT has published a report on MimiStick, a threat actor launching malspam campaigns against Russian orgs.
Gamaredon: ESET Research has published a comprehensive technical analysis of Gamaredon's toolset used to conduct its cyberespionage activities focused in Ukraine through 2022 and 2023. According to the company, the group is Russia's most active APT in the region.
Turla fileless backdoor: Malware analyst Vlad Pasca has published an analysis on a fileless backdoor used in recent Turla operations.
Sparkling Pisces' new tools: Palo Alto Networks has published a technical report on KLogEXE and FPSpy, a keylogger and backdoor used by the Sparkling Pisces (Kimsuky) North Korean APT.
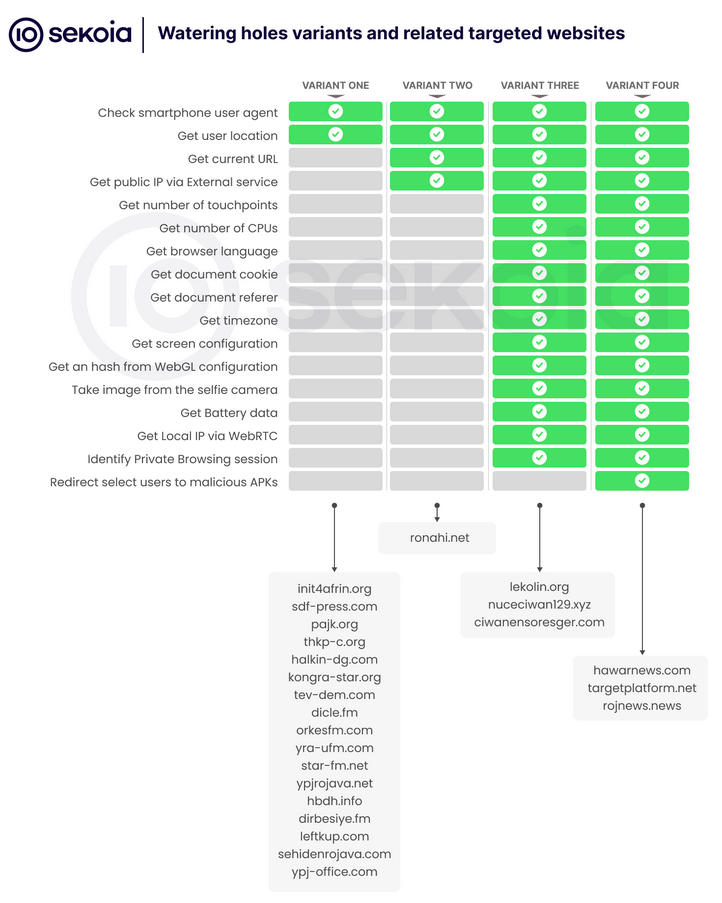
SilentSelfie: French security firm Sekoia has discovered watering hole attacks deployed on 25 Kurdish websites. The websites were compromised with malicious code that harvested a site visitor's device details, prompted users to share their location, and even install a malicious Android app. Sekoia named the campaign SilentSelfie because it went undetected for over a year and also prompted users to activate their phone's front camera and take a selfie. The company said it did not have enough details to link the campaign to any previously known APT group.
Vulnerabilities, security research, and bug bounty
Cisco security updates: Cisco has released 15 security advisories for multiple products.
GitLab security updates: GitLab has released security updates to patch three vulnerabilities.
Citrix security updates: Citrix has released three security updates for its XenServer and Citrix hypervisor.
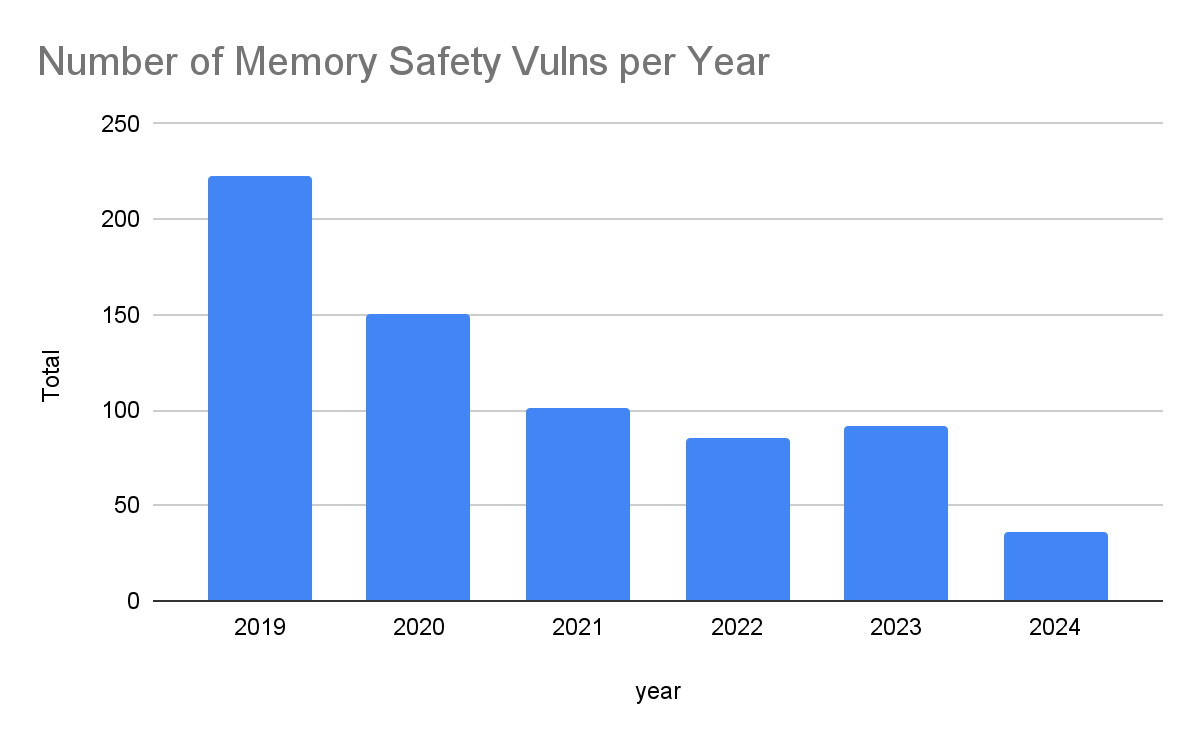
Android memory safety vulnerabilities fall: The percentage of memory safety vulnerabilities in the Android mobile operating system has dropped from 76% to 24% over the past six years. This is well below the 70% industry norm and continuing to drop. Google credits this reduction to the increased usage of memory-safe languages for Android's code.
NVIDIA vulnerability: Cloud security firm Wiz has discovered a vulnerability in the NVIDIA Container Toolkit, a tool for building GPU-accelerated cloud containers. Tracked as CVE-2024-0132, the vulnerability allows a threat actor to use malicious container images to escape and gain full access to the host OS via the NVIDIA toolkit. NVIDIA has patched the bug in an update released this week. Wiz says that roughly a third of all cloud environments may be impacted by this issue. Most of these containers are located at companies specialized in AI development.
WatchGuard SSO vulnerability: RedTeam Pentesting has discovered a vulnerability (CVE-2024-6592) in the WatchGuard Single Sign-On agent, which apparently is neither encrypted nor authenticated.
Unpatched Nortek Linear vulnerability: Nortek has failed to fix a vulnerability in its Nortek Linea smart door and access control platform. The vulnerability allows remote, unauthenticated attackers to cause the device to execute arbitrary commands. The issue was reported to the vendor more than five months ago.
SolarWinds WHD PoC: Horizon3 has published a write-up and PoC on a vulnerability in the SolarWinds Web Help Desk. Tracked as CVE-2024-28987, the issue is a set of hardcoded credentials in one of the app's services. This was patched in August.
"The BasicAuthRouteController allows a hardcoded set of credentials to access any resources that utilize this controller. The credentials are helpdeskIntegrationUser and dev-C4F8025E7."
Gradio exploitation: Threat actors are exploiting two vulnerabilities in attempts to take over Gradio LLM servers. The Shadowserver Foundation says the campaign started in June this year and also targets other AI and LLM systems. Other targeted platforms include NextChat, LiteLLM, and Ollama.
Kia car hacking: A team of security researchers has found a vulnerability in Kia's web portal that allowed them to take over millions of the company's cars. The researchers built a custom tool that took a Kia car's license plate, exploited the bug, and gave them control over key car functions. This included the ability to unlock doors, honk the horn, or start the engine. The research team notified Kia of the bug in June, and the company patched its web portal in August.
Infosec industry
FBI raids Carahsoft: The FBI has raided the Virginia headquarters of IT, software, and cybersecurity services provider Carahsoft. The raid is part of an investigation into the company, SAP, and other unnamed service providers for allegedly conspiring to fix prices and overcharge government agencies. The scheme has allegedly been going on for over a decade. Carahsoft is the US government's second-largest IT service provider after Dell, with $3.5 billion worth of contracts. [Additional coverage in NextGov]
Merger news: Managed service provider TRG has merged with Inversion6 to add cybersecurity services to its line of products. Inversion6 is now a division of TRG.
New tool—Known Physical Bitcoin Attacks: CASA co-founder and CSO Jameson Lopp maintains a list of known physical attacks on Bitcoin and other crypto-assets. The list includes kidnappings, crypto ATM, and crypto wallet physical thefts.
New tool—Jenganizer: Tenable has released Jenganizer, a tool to map hidden services in AWS.
Threat/trend reports: Cloudflare, Kaspersky, the NCC Group, the Ransomware Task Force, Team8, and Zimperium have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about new reports saying that Russia is creating new cyber groups made up of cyber criminals.
In this podcast, Tom Uren and Patrick Gray talk about the possibility of deterring Volt Typhoon, the Chinese group that is compromising US critical infrastructure to enable future disruption operations in the event of a conflict with the US. Tom thinks it is not possible to deter Volt Typhoon, but things might work the other way. If the US can neuter Volt Typhoon and take away the PRC's magic cyber bullet, it could make conflict less likely.
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!






