Risky Biz News: Thousands of Yubikeys have been deployed in Ukraine, more to come
In other news: PyPI enforces 2FA for top projects; UK recommends against paying ransomware gangs; and Rolling PWN attack can unlock most Honda cars.
This newsletter is brought to you by Airlock Digital, Rumble Network Discovery, Proofpoint, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.

More than 16,000 Yubikeys have been deployed to Ukrainian government executives, workers, and employees of private companies in Ukraine's critical sectors in the aftermath of Russia's invasion.
The initiative is spearheaded by Hideez, a Ukrainian security firm specializing in identity services and FIDO consultancy. Earlier this spring, the company secured a donation of 30,000 Yubikey security keys from hardware authentication device maker Yubico.
Since then, Hideez's staff has been working with Ukrainian government agencies like the Ministry of Digital Transformation, the National Security and Defense Council, and the State Service of Special Communications and Information Protection of Ukraine (SSSCIP) to ensure the devices can be imported into the country, that government infrastructure is prepared for the keys' rollout, and that recipients receive the necessary training.
The idea is that once government and critical sector workers have a security key as an extra layer of protection, their accounts would be safe from the onslaught of spear-phishing attacks constantly hitting their inboxes every day.
"We got Yubikey certified, so they are allowed to be deployed into Ukraine instances," Yuriy Ackermann, VP of War Efforts at Hideez, told Risky Business News in a call last week.
"We have quite a few ministries that have moved a lot of their stuff to G Suite and Azure—with them is quite easy; we just give them a key. We made instructions in Ukrainian, video instructions, and so on. [...] So, it's really fast.
"We had a department that pretty much moved to using FIDO, like 500 people, in less than a week because they just needed to understand their policies, read our documentation, and that's it, they just give the keys and roll them, and voila," Ackermann said.
But efforts are also underway to roll out the keys to individuals in other departments, including those without the proper server-side infrastructure. In these cases, Ackermann says Hideez has been providing the government with the company's solution at minimal costs.
Right now, security keys have been deployed to several government departments and companies in the logistics, energy, and telecommunications sectors. But plans go much further.
"Anything without what the country would fall apart is pretty much on top of our bucket list to work with," Ackermann said.
Ackermann said Hideez's goal is to deploy 100,000 security keys and maybe, in the distant future, reach a milestone of 1 million security keys deployed to government and critical infrastructure sector—making Ukraine the most cyber-secure country in the world.
"My point is that Ukraine should become an example for other countries who cannot afford [...] AI behavioral biometrics anti-phishing system crap, and stuff like this. We cannot afford these things in Ukraine. [...] This should become an example on how to actually and effectively defend yourself because we're dealing with the first cyber war in human history," Ackermann said.
Breaches and hacks
Australian prison suspends visits: The Port Phillip Prison in Melbourne, Australia, has been forced to suspend prisoner visits after its computer systems fell victim to "a sophisticated cyber ransom attack," whatever that means.
La Poste Mobile ransomware attack: French mobile phone network La Poste Mobile is still struggling to recover from a ransomware attack that took place more than a week ago and has crippled its administrative and management services. While service has not been affected, the company noted that customer data might have been accessed, The Record reported.
US Congress DDOS: Russian hacktivist DDoS group Killnet claimed responsibility for an attack on the website of the US Congress, according to Cyberscoop.
Stolen crypto: According to blockchain security and auditing company CertiK, cryptocurrency platforms lost more than $2 billion to hacks in the first half of 2022, a figure that’s more than the entire last year combined. The vast majority of breaches have been linked to “flash loan attacks,” the company said.
General tech and privacy
PyPI enforces 2FA for top projects: The administrators of the Python Package Index (PyPI) are enrolling the top 1% of most popular Python packages (~3,500) into mandatory two-factor authentication (2FA). The PyPI team said it would be working with Google Open Source Security Team to distribute Google Titan security keys to all project maintainers in order to ensure their accounts can't be hijacked for supply chain attacks that could have massive consequences. PyPI's move comes after GitHub moved to do the same with the top npm packages last year. Unfortunately, the rollout didn't go as planned and without some drama, and the owner of one Python library decided they didn't want to maintain a "critical" project and deleted and re-uploaded their package in order to reset the download counter.
Looks like Python just had a left-pad like incident.
— Paulus Schoutsen (@balloob) 8:47 PM ∙ Jul 8, 2022
@pypi today required 2FA for top 1% downloaded projects.
Author of python-atomicwrites hates it. Deletes their package, re-creates it and uploaded a new version and is no longer marked as critical. Now all old versions gone!
Russia to create its own mobile app store: The Russian government approved on Friday the creation of a national mobile app store. The store's app will be mandatory and will have to be pre-installed on all devices sold in the country. The store will operate based on rules "approved by the Ministry of Digital Development," which will also curate its app inventory.
Government, politics, and policy
L3Harris said they had approval for NSO deal: Last month, US media reported that US defense contractor L3Harris was in advanced talks to acquire Israeli spyware vendor NSO Group, in a deal that fell through after the White House showed its disapproval at a DOD contractor seeking to buy a sanctioned entity. However, in a report on Sunday, the New York Times said that several American intelligence officials were in the know and approved of L3Harris' plan, believing NSO' technology could benefit US agencies like the FBI and CIA, but that none of these officials anticipated the Biden's administration stern response to news of the upcoming acquisition.
UK asks law firms not to recommend paying ransomware gangs: In a joint letter signed by the UK ICO and NCSC, the two agencies have asked British law firms to stop advising their customers in paying ransom demands in ransomware attacks.
Paying ransoms to release locked data does not reduce the risk to individuals, is not an obligation under data protection law, and is not considered as a reasonable step to safeguard data.
The ICO has clarified that it will not take this into account as a mitigating factor when considering the type or scale of enforcement action. It will however consider early engagement and co-operation with the NCSC positively when setting its response.
This is quite a significant intervention. Our research on ransomware and cyber insurance suggested that breach lawyers have a significant influence on victim decision-making, particularly when data exfiltration is involved: rusi.org/explore-our-re… (to be published in Autumn)
— Jamie MacColl (@jamiemaccoll) 9:52 AM ∙ Jul 8, 2022
Dutch secret services told to delete citizen database: The MIVD and the AIVD, the Netherlands' secret service agencies, have been told to destroy a database they created to store the personal details of millions of Dutch citizens. The country's data protection supervisor found that the database had been created through an unlawful process and ordered the Dutch Ministries of Defense and the Interior to delete it following a complaint filed by the European Digital Rights (EDRi), a pan-European association of civil and human rights organizations.
Dutch government increases prison sentences for cyber espionage: The Dutch government passed a bill last week that increased the prison sentences for espionage activities. A clause in the document increases the prison sentences by a third for computer offenses if carried out at the behest of a foreign power. [Coverage in RTL Nieuws]
Mauritius Telecom espionage scandal: Sherry Singh resigned at the end of June from the post of CEO of Mauritius Telecom, claiming in a radio interview that the country's Prime Minister, Pravind Jugnauth, ordered him to install traffic-sniffing equipment on the telecom's network. Singh said the equipment was meant to monitor and decrypt internet traffic for the benefit of a foreign state, RFI reported.
Former CEO of the #Mauritius Telecom made a huge revelation regarding his resignation. He stated today in a radio programme that the Prime Minister ordered him to allow a third-party to set up a device within the ISP premises to «sniff» the Internet traffic of users in Mauritius.
— Ish Sookun (@IshSookun) 1:22 PM ∙ Jul 1, 2022
Cybercrime and threat intel
Immigration services for sale: A threat actor going by the name of Royal Bank is advertising immigration services countries like the US and Canada on the Russian-language forum XSS. Flashpoint says the threat actor is selling the service to Russian citizens looking to leave the country, and the service costs $5,000.
Gaming accounts on the dark web: Threat intel firm DarkOwl has an overview of gaming and streaming accounts for sale on the dark web.
AstraLocker and Yashma decrypters: Antivirus maker Emsisoft has released on Friday free decrypters for the AstraLocker and Yashma ransomware strains.
The AstraLocker decryptor is for the Babuk-based one using .Astra or .babyk extension, and they released a total of 8 keys.
— Emsisoft (@emsisoft) 11:08 PM ∙ Jul 7, 2022
The Yashma decryptor is for the Chaos-based one using .AstraLocker or a random .[a-z0-9]{4} extension, and they released a total of 3 keys.
2/4
Malware technical reports
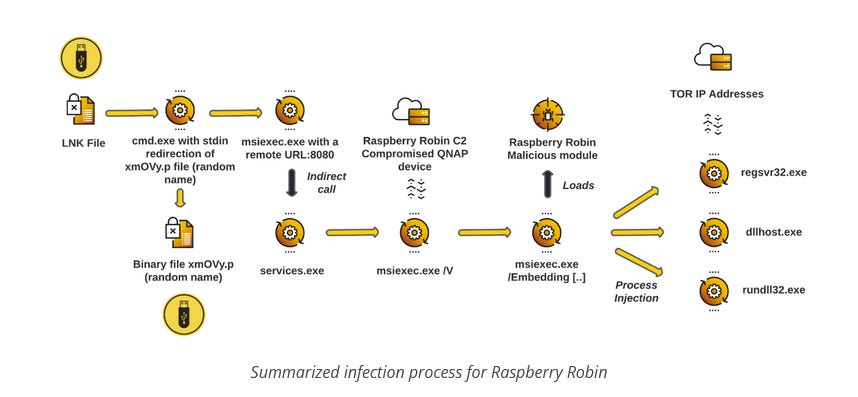
Raspberry Robin: Cybereason researchers have published a technical report on the Raspberry Robin malware, which uses LNK files to infect its victims and is usually delivered through file archives, removable devices (USB), or ISO files. According to Cybereason, the majority of victims are located in Europe. A report on the same malware is also available from Red Canary.
Vulnerabilities and bug bounty
Rolling PWN Attack: A security researcher published details last week on a vulnerability in the key fob technology used by Honda cars. The attack, nicknamed Rolling PWN, can allow threat actors to unlock doors and start engines on all Honda cars sold between 2012 and 2022. The vulnerability is currently tracked as CVE-2021-46145. [Coverage in Motherboard]
Attacks on AI systems: In a whitepaper published last week, NCC Group chief scientist Chris Anley explores the common security problems and real-world practical attacks on AI systems.
Infosec industry
Recorded Future acquires Haching: Threat intelligence giant Recorded Future announced on Friday the acquisition of Hatching, a platform specialized in automated sandbox malware analysis.




