Risky Biz News: The spyware industry has found a cozy home in the EU
In other news: Medibank won't pay the ransom; Hushpuppi sentenced to 11 years; Microsoft patches ProxyNotShell and four other zero-days.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
In a press conference on Tuesday, PEGA, an EU committee set up to investigate the abusive use of spyware across Europe, presented the initial results of an extensive investigation it started back in April this year.
While there have been reports of spyware abuse across several EU member states—which led to PEGA's creation in the first place—in a 159-page draft report shared with Risky Business, the committee said it found that spyware use and the surveillance industry are prevalent across EU member states.
"All member states have spyware at their disposal. All of them, even if they don't admit it. They do!" PEGA Committee rapporteur Sophie In 't Veld said yesterday.
She added that while some countries use it responsibly, others have abused it to spy on political rivals, journalists, and government critics, but all use the cloak of "national security" to create an "area of lawlessness" where they operate without any accountability.
Unmatched in spyware abuse in the UE are Hungary and Poland, according to the PEGA Committee rapporteur.
"[In] Poland and Hungary, [...] spyware is an integral element of a system; a system which is designed to control and even oppress the citizens—that is the critics of the government, the opposition, journalists, whistleblowers—and the whole system is very methodically set up. It's not by accident. It's not a random tool they are using," In 't Veld said.
In other countries like Spain and Greece, In 't Veld said spyware was deployed "with no evident, imminent, immediate threat to national security" and that there are also reports of similar abuses in Cyprus.
But In 't Veld said that while some EU member states are consumers, others are guilty of providing a legal framework for surveillance companies to operate unhindered and sell their software all across the globe. According to the draft report, some vendors advertise themselves as "EU regulated," using the term as a form of "quality label."
"Certain EU countries are attractive as an export hub, as—despite the EU's reputation of being a tough regulator—enforcement of export regulations is weak," the draft report concluded. More below:
"Two Member States, Cyprus and Bulgaria, serve as the export hub for spyware. One Member State, Ireland, offers favourable fiscal arrangements to a large spyware vendor, and one Member State, Luxemburg, is a banking hub for many players in the spyware industry. The home of the annual European fair of the spyware industry, the ISS World' Wiretappers Ball,' is Prague in The Czech Republic. Malta seems to be a popular destination for some protagonists of the trade. A few random examples of the industry making use of Europe without borders: Intellexa has a presence in Greece, Cyprus, Ireland, France and Hungary, and its CEO has a Maltese passport and (letterbox) company. NSO has a presence in Cyprus and Bulgaria and it conducts its financial business via Luxemburg. DSIRF is selling its products from Austria, Tykelab from Italy, FinFisher from Germany (before it closed down)."
PEGA's draft report proposes a series of measures the EU should take to address its spyware problem. The first one that the EU should apply, according to In 't Veld, would be an immediate moratorium on the sale and use of such tools.
The second would be to "enforce the [EU] export rules vigorously because that, frankly, friends, is a joke. We have Dual Use regulation but the enforcement is really not serious"—as In 't Veld eloquently put it yesterday.
Other proposals include states defining what "national security" is, the creation of a dedicated European Export Control Agency, a joint initiative with the US to create common standards and a blacklist of spyware vendors, the involvement of Europol in the investigation of abusive spyware use, and granting PEGA and other EU bodies actual powers to investigate spyware cases.
Breaches and hacks
Medibank update: In an update on its data breach disclosure, Australian private health insurance provider Medibank said the personal information of more than 9.7 million Australians was stolen in a ransomware attack last month. The company said it does not plan to pay the threat actor's ransom demand. A ransomware gang known as BlogXX (believed to be a subgroup of the older REvil gang) took credit for the intrusion and data theft.
Cyber-attack cripples Mexico's transportation system: According to a report, Mexico's transportation ministry has stopped issuing new permits, license plates, and driver's licenses for commercial truck operators until December 31 because of a cyberattack that hit the IT infrastructure of the Secretariat of Infrastructure, Communications and Transport (SICT) in late October. (via DataBreaches.net)
Pando crypto-heist: DeFi platform Pando said it was the target of a hack last Saturday when a threat actor tried to steal more than $70 million worth of cryptocurrency from the platform's wallets. The company said it managed to freeze $50 million of the stolen funds, but the attacker successfully stole more than $21.8 million of its funds. Pando said the hacker used an Oracle attack against one of its protocols and is still hoping to negotiate with the attacker to return some of the stolen funds.
Government, politics, and policy
Greece to ban the sale of spyware: After Greece's spyware scandal exploded to new dimensions over the weekend and after a visit from the EU's PEGA Committee last week, the Athens government announced it was planning to ban the sale of spyware. Unclear how this will prevent the Greek government from continuing to use it in new operations.
Sponsor section
Thinkst is one of this newsletter's four main supporters and this week's featured sponsor. The company launched a new product called Sensitive Command Canarytoken, a simple canary token that sends an alert every time any command you choose as "sensitive" or "malicious" is executed on your host.
Cybercrime and threat intel
Hushpuppi sentenced: A US judge sentenced Ramon Abbas, also known as "Ray Hushpuppi," an infamous BEC scammer, to 11 years in federal prison. The 40-year-old Nigerian national was also ordered to pay more than $1.7 million in restitution back to two victims of his BEC scams, estimated to be in the realm of tens of millions of US dollars.
Silk Road scammer: In a surprising case that nobody saw coming, the US Department of Justice said it seized funds and charged James Zhong, an Atlanta-based real estate mogul, who in 2012 hacked and stole more than 50,000 Bitcoin from Silk Road, a dark web marketplace for illicit products. The DOJ said it seized 50,676 of the 51,680 Bitcoin that were stolen from Silk Road. The funds are now worth $3.3 billion. Zhong has already pleaded guilty.
Former Deloitte employee behind FIFA hacks: Deloitte said it fired an employee named Aditya Jain, who was exposed over the weekend as one of the individuals behind WhiteInt, an India-based hacker-for-hire cyber-mercenary group that allegedly helped the Qatari government hack FIFA officials in the run-up of Qatar receiving hosting rights for the 2022 Soccer World Cup.
Sydney teen pleads guilty to extorting Optus customers: Dennis Su, 19, from Sydney, pleaded guilty this week to extorting Australians who had their data leaked in the Optus breach. Su—who was not involved in the breach itself—admitted to taking some of the leaked Optus data, contacting some users via SMS, and demanding an AUS$2,000 payment or he'd use their personal details to commit "financial crimes." Su was detained in early October, a week after sending out the SMS messages.
Yep. The guy has already been caught and now plead guilty. 🤦. My favourite bit from the court case: 'No one ever transferred money but one person responded with an emoji'. sbs.com.au/news/article/t…
— Joe Tidy (@joetidy) 8:51 AM ∙ Nov 8, 2022
Magento sites extortion: Sansec reports that threat actors are contacting the administrators of Magento-based online stores with classic extortion messages, threatening the release a company's data unless a ransom of $3,000 is paid to them in Bitcoin. Sansec researchers urge Magento admins not to pay any ransom demand until the threat actors prove they have stolen a store's data, as similar campaigns involving fake threats have taken place in the past targeting other platforms.
Yanluowang leak: Darktrace has an in-depth technical analysis of the Yanluowang leak—on which we reported last week.
SocGholish update: The operators of the SocGolish malware delivery platform have ramped up efforts to expand their infrastructure. SentinelOne reports that the group is now deploying 18 new malware-staging servers each month, a 334% rise compared to the first half of 2022. Most of these new servers are located in Europe.
Emotet back from the dead: Cisco Talos has analyzed the recent email malspam campaigns coming out from the Emotet botnet, which recently came back to life after being dormant for months since June this year.
DeimosC2: Trend Micro also has a breakdown of DeimosC2, an open-source command-and-control framework that has been recently gaining adoption with malware gangs.
Microsoft Customer Voice abuse: Dynamics 365 Customer Voice, a Microsoft product used to gain feedback from customers via phone, is being abused for phishing operations. Avanan reports that phishing emails containing voice messages recorded via this service are being used to lure users to phishing sites that capture their credentials for various online services.
Malicious PyPI packages: After discovering last week 29 malicious Python libraries that tried to install the W4SP Stealer malware on developers' systems, DevOps security firm Phylum found another 27 Python libraries uploaded to the PyPI portal that installed a clipboard hijacker. According to Phylum, this malware would wait until the developer copies a cryptocurrency address in the clipboard and immediately replace it with one of the attackers.
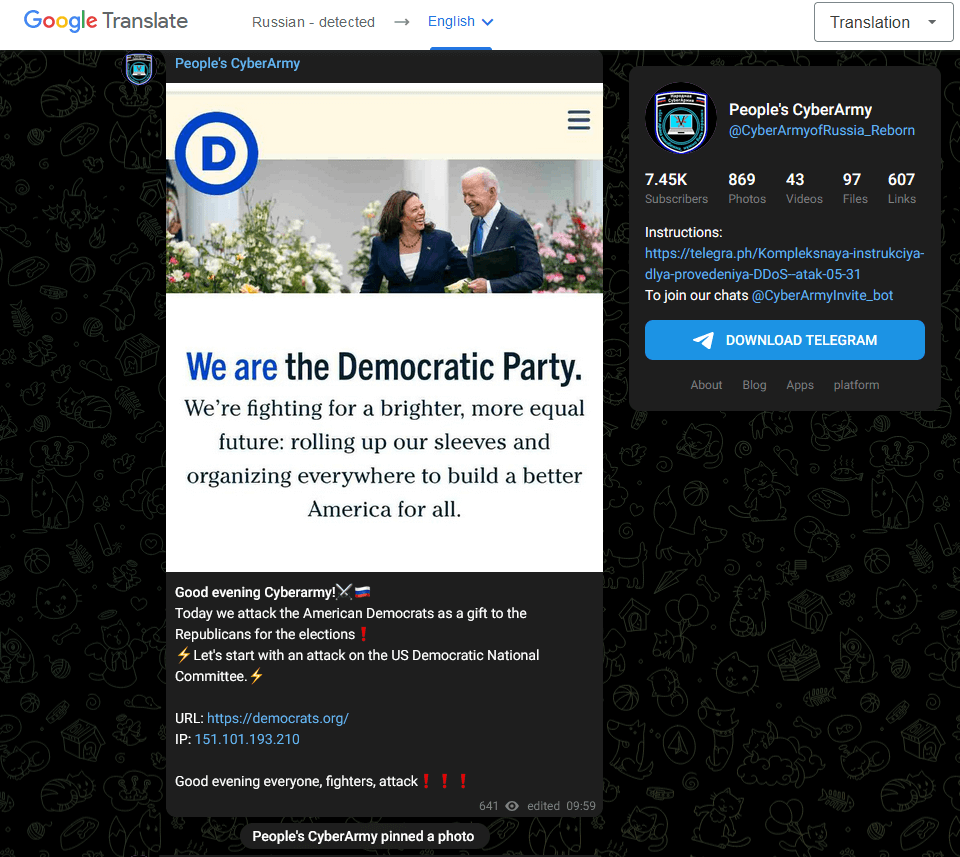
Calls for DDOS attacks on US election day: Wordfence researchers said they'd seen a pro-Russian hacktivist group named "The People's Cyberarmy" call on its members and fellow hacktivist groups to launch DDOS attacks on websites linked to the American Democratic party on November 8, during the US midterm elections.
Malware technical reports
Cloud9: Zimperium researchers took a deep dive into Cloud9, a malicious Chrome extension spread via third-party websites that, once it infects users' browsers, can steal cookie files, keystrokes, and browser session data but can also deploy other malware on the infected system.
StrelaStealer: DCSO researchers have a report out on StrelaStealer, a new info-stealer trojan discovered earlier this month.
Elibomi variants: Trend Micro has analyzed a phishing and malware campaign targeting the customers of Indian banks with mobile malware strains like FakeReward, AxBanker, and Elibomi (including two variants known as IcRAT and IcSpy).
IceXLoader: Researchers from MinervaLabs have analyzed the most recent version of the IxeXLoader (v3.3.3) and found that one particular malware instance was involved in attacks that compromised thousands of users.
APTs and cyber-espionage
APT29: Mandiant has a technical report out on how the Russian state-sponsored group APT29 has abused a feature called Windows Credential Roaming in a recent attack against a European diplomatic entity.
UAC-0010: Ukraine's CERT team said it detected a spear-phishing operation carried out by the UAC-0010 (Armageddon/Gamaredon) group that was posing as Ukraine's SSSCIP agency.
Unknown APT: CYFIRMA researchers have also studied the attacks of an unknown APT that has targeted the personnel of the Indian Defence Force with malicious Android applications.
Black Reward leak: Cluster25 has an analysis of a Black Reward leak of files from the Iranian nuclear agency, and more particularly of sensitive documents showing the close collaboration between Iranian and Russian scientists.
Ukraine Cyber Project: The National Security Archive—a project of the George Washington University in Washington, DC—has launched a new initiative called the Ukraine Cyber Project, in which researchers will document the role of cyber operations in Russia's invasion of Ukraine and how they helped augment traditional kinetic warfare.
"Although Russia's overt resort to cyberattacks has not matched the level of intensity most observers expected – a lesson in itself – the Ukraine war has offered many fascinating insights into topics such as: how smaller states can effectively counter the actions of a larger aggressor; the importance of alliances and cooperative relationships among cyber actors; the key role of the private sector and the dynamics of its interactions with governments; the wide-ranging impact hackers have had and the mix of motivations behind their actions, in addition to the nature of their connections to governments they used to consider bitter adversaries."
Vulnerabilities and bug bounty
Patch Tuesday: Yesterday was also November's Patch Tuesday. We had security updates being released by Adobe, Microsoft, SAP, Android, VMware, Citrix, and others. This month, Microsoft has fixed 67 security flaws, including the ProxyNotShell vulnerabilities, and four actively-exploited zero-days:
- CVE-2022-41128 - an RCE in the JScript9 scripting language, detected in the wild by Google TAG
- CVE-2022-41091 - a MotW bypass also known as ZippyReads
- CVE-2022-41073 - an EoP in the Windows Print Spooler service, discovered by MSTIC
- CVE-2022-41125 - an EoP in the Windows CNG Key Isolation Service, detected by MSTIC and MSRC.
Infosec industry
New tool—Microsoft Section52 ICS Forensics Tools: Microsoft has open-sourced this week a new collection of tools to enable investigators to identify suspicious artifacts on ICS environments and to detect compromised devices during incident response or manual checks.
New tool—Shennina: Cybersecurity engineer Mazin Ahmed has open-sourced a new tool this week named Shennina, a tool for automated host exploitation.
New tool—SpyGuard: Sekoia security researcher Félix Aimé has released a tool called SpyGuard, an enhanced version of TinyCheck, a tool to detect signs of compromise by monitoring network flows transmitted by a device.
Here comes a little GIF that shows the new interface. I didn't want to change it all, just a couple of things. (2/7)
— Félix Aimé (@felixaime) 1:45 PM ∙ Nov 7, 2022




