Risky Biz News: The mystery at Mango Park, and the Cambodian government's shady reaction
In other news: Microsoft to charge home users $30 for Windows 10 extended security updates; WhatsApp and NSO prepare to settle; crypto-exchange reimburses users hours after major hack.

This newsletter is brought to you by vulnerability management and analysis platform Nucleus Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Something is rotten in the state of Cambodia, according to an increasing number of reports that cyber scam compound operators are now receiving protection from local police and government officials.
The perfect example of this new reality is the incident surrounding the recent "arrests" at Mango Park, a cyber scam compound in the country's Kampong Speu province.
A report from South Korean national television KBS presented the story of a South Korean who was duped by the promise of a high-paying job to travel to Cambodia, where he was held against and forced to work on online scams at Mango Park. He was freed after his family paid a ransom, and once back home, he shared with reporters how local police had protected the scam compound when he tried to complain.
The story caused waves with South Korean officials, who pressed Cambodian counterparts to rescue the other South Koreans there, and it eventually led to a raid on Mango Park on October 24.
Around 1000 foreign nationals, mainly Chinese and Koreans, were "detained" during the raid.
Following the arrests, Cambodian police went out of their way to say they found no evidence of kidnappings, illegal detentions, or torture.
Cambodia's Ministry of Internal Affairs called the KBS report "defamatory news" and claimed the reporters had "ulterior motives" and had "exaggerated the reality." Officials said the workers who complained had claims related to labor disputes or wanted quick excuses out of their contracts to return home.
The country's Ministry of Tourism echoed the statement, said the KBS report negatively impacted the tourism sector, and even asked for a correction.
Provincial police also denied the reports of human trafficking and torture and said the compound had resumed operations after they found nothing wrong.
The fate of the 1,000 detained (freed) workers is a mystery. It's unclear if they've been sent back to the compound or are being extradited back to their countries.
Pictures from the so-called raid show a building with fences up to the first or second floor, with barbed wire on top, and bars on both the inside and outside windows. Hardly the typical workplace.
Together with Myanmar, Cambodia is believed to be the home of today's most cyber scam compounds. A UN report published last year estimated that roughly 100,000 people are being forced to work in cyber scam call centers in Cambodia—many trafficked from neighboring countries.
A report from Cyber Scam Monitor highlights how many of these Cambodian cyber scam compounds are not only well-known and operate in plain sight but are also expanding. Some centers tripled in size over the past year, according to aerial photos.

Victims are lured to Cambodia, have their passports taken away, and forced to work in the call centers to repay travel expenses, housing, or other of their kidnapper's imaginary fees—often under the threat of violence and not seeing their families again. Many are held captive in the call centers and not allowed to exit the premises, which explains the multi-story high barb-wired fences.
Over the years, there have been suspicions that local corrupt officials, police, and rogue military units were either running or protecting some of these compounds.
What happened last week in Cambodia is a wake-up call that some of the higher forms of government are protecting these operations. Having two Cambodian ministries come out and deny a compound's existence is a telling sign of a higher power being involved.
But this wasn't the first time. In September, the US Treasury sanctioned Ly Yong Phat, a local business tycoon and senator, for his involvement in some of these scams, but it appears the rot is far more widespread. Back then, Cambodian officials called the decision "unjust" and "politically motivated," and instead decided to praise Ly for his "contributions to infrastructure development, job creation and poverty alleviation."
In July, blockchain analysis firm Elliptic described a Cambodian online platform named Huione Guarantee as a major hub for laundering the proceeds from online cyber scams. The report linked the platform to the Huione Group, a large Cambodian financial conglomerate linked to Cambodia's ruling Hun family.
Maybe we should have been paying attention earlier to what was coming out of the Phnom Penh government, because it's starting to become clearer and clearer on what side they stand when it comes to cyber scam compounds.
Breaches, hacks, and security incidents
US Soccer data breach: The US soccer federation has disclosed a data breach after a threat actor gained access to an employee account in May this year.
AEP ransomware attack: A ransomware attack on AEP has the potential to disrupt pharmaceutical supply chains in Germany. The company is working to recover IT systems before pharmacies that rely on its services start experiencing shortages. According to its website, AEP supplies medicine to more than 6,000 pharmacies across the country. [Additional coverage in Heise Online]
MTL cyberattack: France's Ministry of Labour and Employment has suffered a security breach on the night between October 23 and 24. Officials believe hackers stole the personal details of young people looking for employment. This includes the details of jobseekers aged 16 to 25. Exposed data includes names, email and postal addresses, and telephone numbers.
Sunray Finance crypto-heist: A threat actor has stolen $2.85 million worth of crypto-assets from the Sunray Finance platform. Security firm CertiK says the incident took place after the attacker compromised a private key. The key granted the attacker control over the platform's SUN and ARC tokens, which the intruder sold shortly after. Sunray has taken down its platform to secure its infrastructure.
M2 reimburses users after crypto-heist: The M2 cryptocurrency exchange has reimbursed users within hours after getting hacked last Thursday. The company restored almost $13.7 million worth of crypto-assets within 24 hours of the hack. The funds were stolen from M2's hot wallets in an incident that is still being investigated.
DDoS attacks hit major dark web markets: via Dark Web Informer.
General tech and privacy
Windows 10 ESU pricing: Microsoft will charge home users $30 to receive an extra year of security updates for Windows 10 once the operating system reaches end-of-life in October next year. Home users will only be able to buy extended security updates for one year, while enterprises can sign up for three. For enterprises, the price will be $61 for the first year, and then $122 and $244 for the subsequent years.
Microsoft delays Recall again: Microsoft has delayed the launch of Recall—a controversial feature that takes screenshots of the user's screen and uses AI to search through old activity. This marks the third time Microsoft has postponed Recall's launch. It was initially set to launch in June but was delayed to October, and now December. The feature came under fierce criticism for its spyware-like behavior, insecure data storage, and the inability for it to be turned off. Microsoft announced a major overhaul of Recall's security that was supposed to launch last month. [Additional coverage in The Verge]
WhatsApp and NSO prepare to settle: WhatsApp and Israeli spyware vendor NSO Group appear to be heading to a settlement. The two companies have scheduled a meeting in January of next year to discuss a settlement. The move comes after Meta asked the case judge to award a default win after the NSO defied a court order and refused to share internal email communications and its exploit source code. In September this year, Apple filed paperwork to drop its NSO lawsuit after three years of litigation.
Intellexa migration: A report from InsideStory from April highlights how former Intellexa employees appear to have migrated to two new mysterious Greek companies. Intellexa is the surveillance vendor behind the Predator spyware, and this smells like another rebrand after it got in trouble and got itself sanctioned. Unfortunately, the article is paywalled and I can't share the names of the two new companies.
Government, politics, and policy
Russia's influencer registration enters into effect: Russian social media figures and bloggers with more than 10,000 subscribers must register with the Russian government by the end of the year. Influencers must link their channels and blogs to their official account on the Russian Gosuslugi government portal. Russia's internet watchdog will then approve if they're allowed to continue posting 10 working days after registration.
CIRCIA complaints: Twenty-one organizations from various critical sectors have sent a letter to CISA to complain about the strict CIRCIA incident reporting rules. [Additional coverage in CyberScoop]
Sponsor Section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Adam Dudley, Senior Director for Strategic Initiatives & Alliances at Nucleus Security, on how the company works with partners and customers to constantly improve its service. Adam also touches on how executives are now inquiring about vulnerability management more than low-level practitioners.
Arrests, cybercrime, and threat intel
Equalize hacker-for-hire scandal: Italian officials have identified the company that breached state security databases as Milan-based private investigative firm Equalize. Four Equalize members are under house arrest, and 60 other suspects are under investigation. The company stands accused of hacking state databases to steal data on politicians, entrepreneurs, athletes, and musicians. The company also conducted investigations overseas, and some of its customers also include the Vatican, Israeli intelligence agents, and Italian energy giant Eni. According to Politico Europe, the Vatican allegedly hired Equalize to spy on Vladimir Putin's right-hand man and find financial trails to the Wagner para-military group.
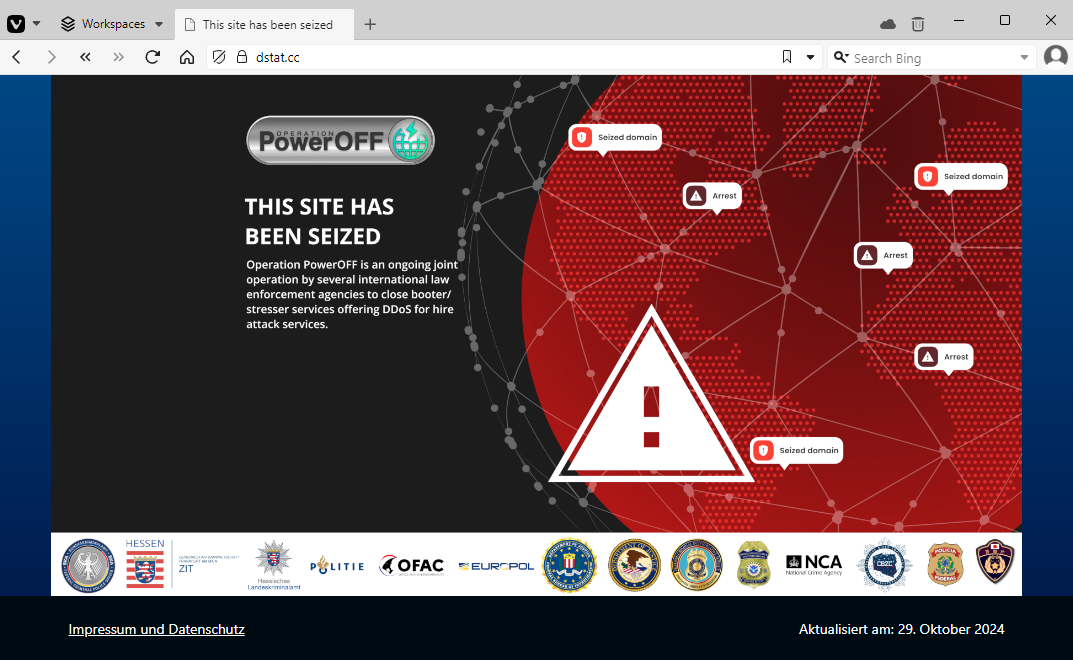
Dstat takedown: German authorities have taken down DDoS-for-hire service Dstat.cc and arrested its two administrators. Two suspects, aged 19 and 28, were detained in West Germany. Officials say the two also managed Flight RCS, an online marketplace that sold synthetic cannabinoid vapes.
Mysterious spoofed Tor traffic: A threat actor is launching SSH brute-force attacks and spoofing packets to make the attack look like it's coming from legitimate Tor relay nodes. Several Tor node operators have now reported receiving multiple abuse reports for traffic they did not carry. Experts warn that the spoofed SSH brute-force attacks may be used to disable Tor relays. Web hosting providers usually take down servers that receive a large number of abuse reports in a short span of time.
Mammoth scheme: Russian security firm FACCT looks at a cybercrime scheme targeting Russian-speaking users with malware designed to gain access to their bank accounts.
Marko Polo rebrand: According to threat intel analyst g0njxa, the Marko Polo group has rebranded to the ZeroDay Team. How very original!
New npm malware: Forty-two malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details. There's also this Phylum report that looks at an npm typosquatting campaign targeting popular libraries.
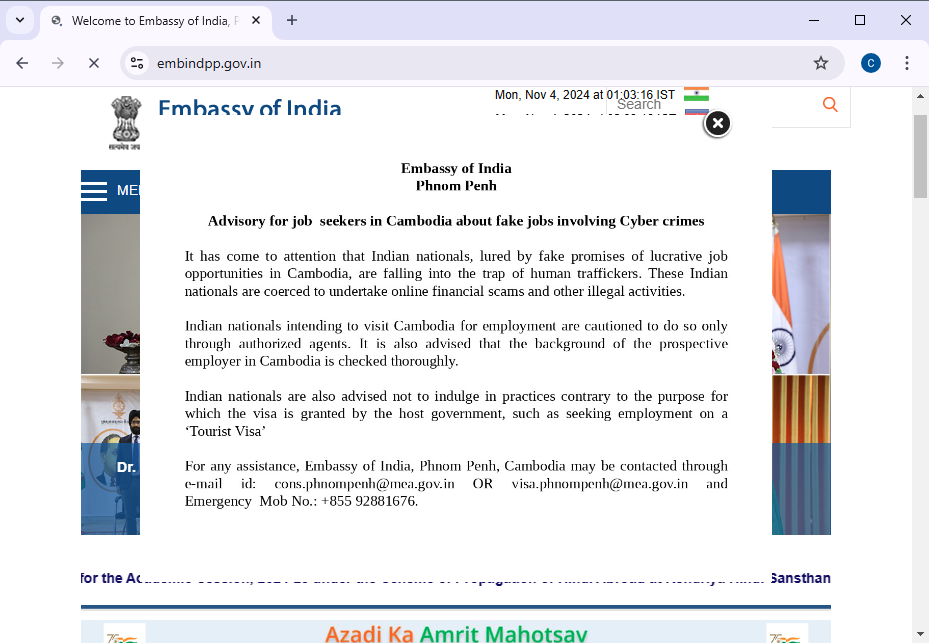
Cyber scam repatriations: The Indian government has repatriated seven individuals who were forced to work in a cyber scam compound in Cambodia. After several such flights, India's embassy in Cambodia also started showing a popup to all visitors about the dangers of being lured with fake jobs to the country and then forced to work in cyber scam call centers. [Additional coverage in The Times of India]
Malware technical reports
SmokeLoader returns: The SmokeLoader malware botnet is still active five months after Europol and the FBI disrupted its operation. The group was one of six botnets that had command and control servers seized at the end of May. Security firm Zscaler says the botnet has returned with new server infrastructure. SmokeLoader is the second botnet after Bumblebee to return to life after this year's takedown. Zscaler has also released a tool named SmokeBuster to help enterprises detect and remove old and new SmokeLoader infections.
GootLoader: Google Cloud's security team has published some basic tips on how to find systems infected with the GootLoader malware.
EDRSandBlast: PAN's Unit42 looks at EDRSandBlast, a new EDR bypass tool they found while investigating a customer breach. The EDR evasion toolkit appears to be a modified version of an open-source project of the same name.
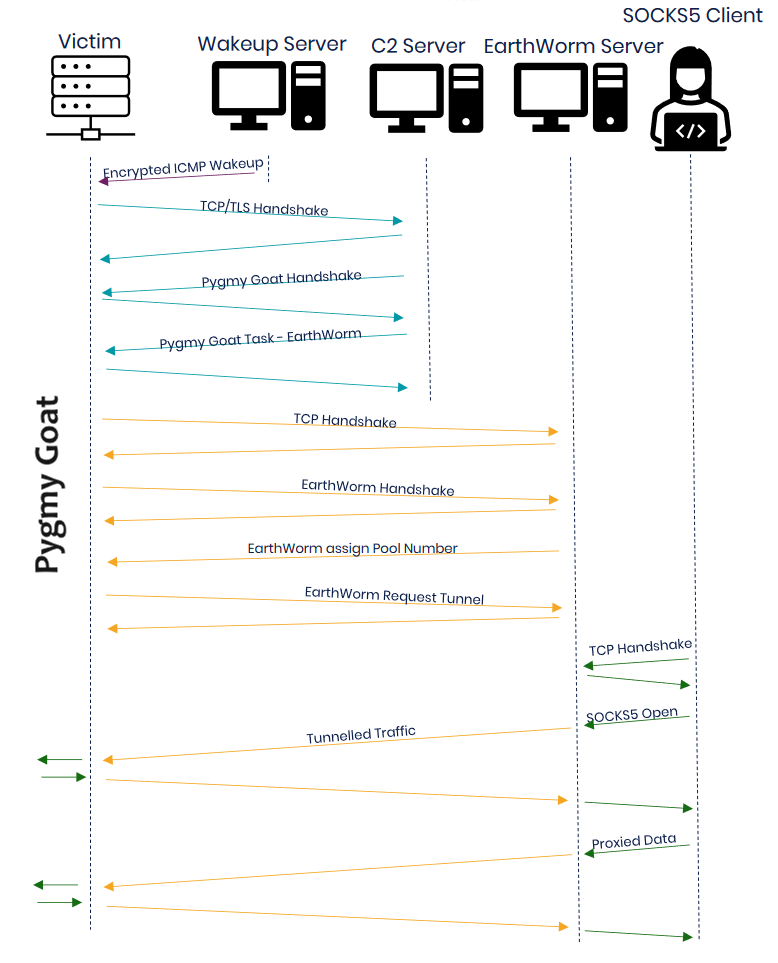
Pygmy Goat: The UK's cybersecurity agency has published details on a backdoor deployed on hacked Sophos XG firewall devices back in 2022. The Pygmy Goat [PDF] backdoor is loaded into the system's native SSH daemon and can be controlled via SSH or ICMP packets. It provides attackers with functionality such as a remote shell, packet capture, cron tasks, and SOCKS proxy servers. Sophos says the malware is the work of Chinese state-sponsored hackers.
Sponsor Section
Nucleus Security's COO Scott Kuffer shows Patrick Gray their vulnerability management platform. It ingests scan outputs from a number of vulnerability identification tools, normalizes that information, and then allows vulnerability management teams to do things like assigning responsibility for certain types of bugs to the correct people.
APTs, cyber-espionage, and info-ops
Pro-UAE info-op: The Daily Kos looks at a pretty obvious pro-UAE covert social media influence operation that's been live for months on Twitter and Reddit. Antibot4Navalny also covers the same campaign in their own thread and how the campaign used AI capabilities for region-specific messaging.
"Excited" intel botnet: OSINT expert Auonsson has published a thread on a weird Twitter bot network posting content on intel, military, and political topics.
"End game is unknown, but a guess is recruitment or information gathering. Maybe just influence."
VoterAlert/True The Vote: OpenMeasures has published a report looking at how the True The Vote organization allows anyone to publish misleading and fake reports of election fraud on its VoterAlert website.
Russia behind voter disinfo video: US intelligence agencies say that a Russian threat actor is behind a misleading video that targeted voters from the state of Georgia. The video went viral last week. It showed a man to be a Haitian migrant who voted multiple times across Georgia for the Harris-Walz campaign. This is the second time US intelligence officials put out a joint statement to debunk election misinformation. The first case was for a video claiming to show a man ripping Trump ballots in Pennsylvania.
UNC3707: StrikeReady has a look at a phishing campaign targeting Ukraine from Russian APT cluster UNC3707.
Konni: ThreatBook looks at Konni's operations this year.
Contagious Interview: The Macnica Security Research Center in Japan has published a report on Contagious Interview, a DPRK operation targeting employees at critical sector companies with fake job interviews that lead to malware infections.
DPRK Naver phishing op: Security firm Hunt.io analyzes a North Korean APT phishing campaign targeting Naver users.
Confucious: Qihoo 360 has published a report that examines how suspected Indian APT group Confucious uses NTFS alternate data streams (ADS) to deploy and hide malware.
SideWinder in Sri Lanka: Threat intel analyst Nimantha Deshappriya has published a report looking at spear-phishing campaigns targeting Sri Lanka, campaigns linked to Indian APT group SideWinder.
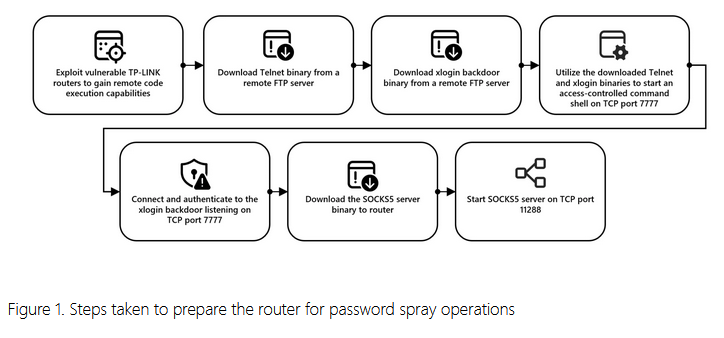
Quad7/CovertNetwork-1658: Chinese state-sponsored hackers have accessed accounts that were previously compromised using Quad7, a brute-force attack botnet. Microsoft has linked some of these intrusions to a group it tracks as Storm-0940. The Quad7 botnet was first spotted last year and is known for its ability to conduct low-and-slow and highly evasive password spray attacks. Microsoft says the botnet is mainly made up of hacked TP-Link routers.
Vulnerabilities, security research, and bug bounty
PTZOptics zero-day: GreyNoise researchers have discovered two actively exploited zero-day vulnerabilities (CVE-2024-8956 and CVE-2024-8957) in PTZOptics live-streaming cameras. The zero-days can allow attackers to take full control of the cameras, manipulate feeds, or enlist the devices into botnets. Both issues have been patched last week. GreyNoise says these are the first zero-days it discovered with the help of its AI system while analyzing honeypot logs.
FortiManager zero-day: BishopFox and Darktrace have published reports on CVE-2024-47575, a recently disclosed zero-day in Fortinet's FortiManager firewall management app that has been exploited in the wild since June.
IBM SSO vulns: Security researcher Pierre Kim has found 36 (32+4) vulnerabilities in IBM Single Sign-On (SSO) products. Kim says it took IBM between 13 and 18 months to fix all the reported issues. For some issues, IBM ignored the reports and closed tickets outright. The researcher called the company's behavior "quite worrying" and not on par with current cybersecurity risks.
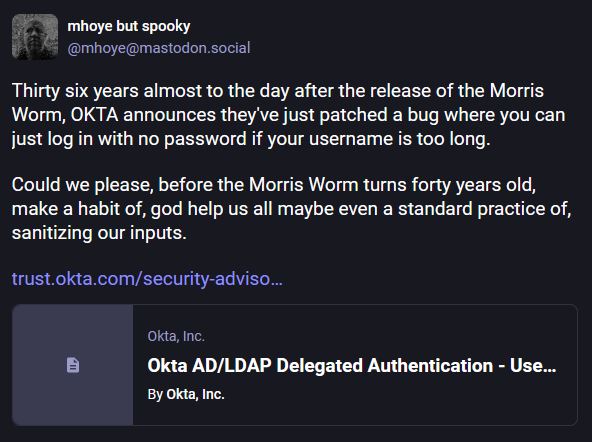
Okta's stupid password bypass bug: Okta has fixed a bug that could have allowed attackers to log into customer accounts without a password if the username was longer than 52 characters. The bug impacted Okta's AD/LDAP DelAuth product. Okta has asked customers to check logs for any unauthorized logins between July 23 and October 30 this year.
Spring WebFlux vulnerability: Kudelski Security's Mouad Kondah has published a write-up on CVE-2024-38821, an authorization bypass in the Spring WebFlux component that was patched last week.
RISK:STATION zero-click vulnerability: Midnight Blue researchers have published details on RISK:STATION, a zero-click vulnerability in Synology DiskStation and BeeStation NAS devices. The vulnerability (CVE-2024-10443) was demoed at the Pwn2Own hacking contest last month and was patched last week.
New Mystique variant: A security researcher known as Flanker looks at CVE-2024-31317, a bug patched in Android this June that allows privilege escalation. The author says the bug is similar to a Pwnie-award-winning bug named Mystique they found in 2021.
ABB Cylon Aspect exposure: Around 265 ABB Cylon Aspect building automation and energy management systems are currently exposed on the internet and are unpatched and vulnerable to two major security exploits that could allow attackers to take over systems. According to VulnCheck, proof-of-concept exploits are publicly available, yet threat intelligence platforms show limited exploitation activity.
IPLS security audit: The NCC Group has released a security audit of WhatsApp's new secure contacts feature, built on the new Identity Proof Linked Storage (IPLS) protocol.
IBM creates XOR team: IBM's X-Force security division has created XOR, a new team dedicated to offensive security research.
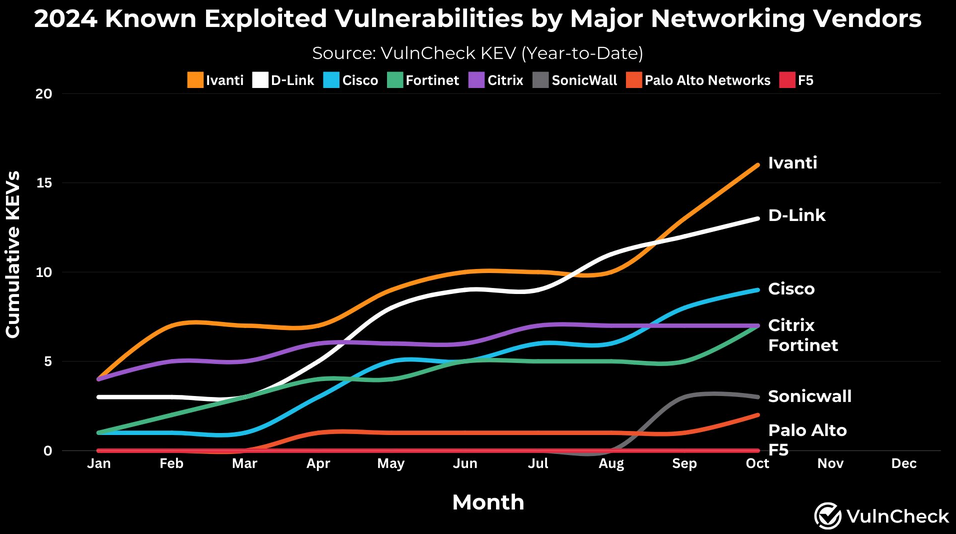
Ivanti takes the top prize: Congratulations to Ivanti for being the most exploited networking equipment vendor so far this year. [h/t Patrick Garrity]
Infosec industry
New tool—PII Masker: HydroX AI has open-sourced PII Masker, a tool that uses AI to spot personally identifiable data and automatically mask it.
New tool—Maestro: SpecterOps has released Maestro, a "post-exploitation tool designed to interact with Intune/EntraID from a C2 agent on a user's workstation without requiring knowledge of the user's password or Azure authentication flows, token manipulation, and web-based administration console."
New tool—Malcrow: A security engineer going by Babyhamsta has released v1 of Malcrow, a tool that creates fake processes and registry keys that mock a security sandbox and analysis environment. This, in theory, prevents some malware from running on your system.
Acquisition news: Insider risk solutions provider Everfox has acquired case management software provider Yakabod.
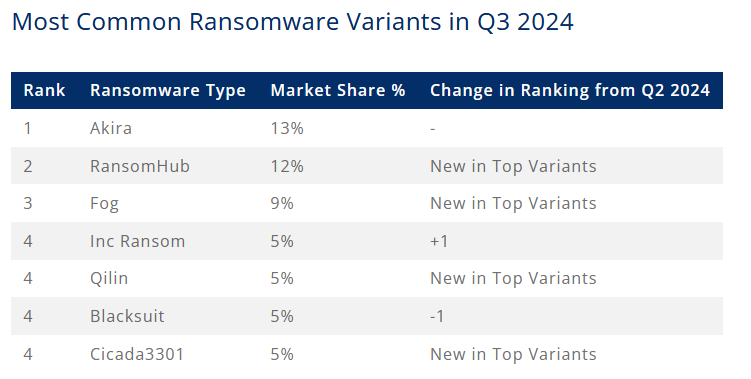
Threat/trend reports: Check Point, Coveware, Kandji, LayerX, Phylum, ThreatMon, and Wordfence have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about a new attempt to measure cyber power, the International Institute for Strategic Studies Cyber Power Matrix.
In this podcast, Tom Uren and Patrick Gray talk about the evolving relationship between Russian intelligence services and the country’' cybercriminals. The GRU's sabotage unit, for example, has been recruiting crooks to build a destructive cyber capability. Tom suspects that GRU thugs are not so good at hands-on-keyboard operations but excellent at coercing weedy cybercriminals to hack for the state.
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!




