Risky Biz News: The Linux CNA mess you didn't know about
In other news: TikTok zero-day used to hack high-profile accounts; mysterious new APT targets China; Hungary's ruling party boycotts Russian hack investigation.

This newsletter is brought to you by vulnerability management and analysis platform Nucleus Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

The Linux Kernel project was made an official CVE Numbering Authority (CNA) with exclusive rights to issue CVE identifiers for the Linux kernal in February this year.
While initially this looked like good news, almost three months later, this has turned into a complete and utter disaster.
Over the past months, the Linux Kernel team has issued thousands of CVE identifiers, with the vast majority being for trivial bug fixes and not just security flaws.
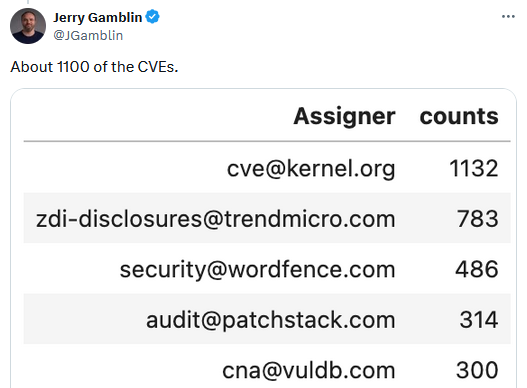
Just in May alone, the Linux team issued over 1,100 CVEs, according to Cisco's Jerry Gamblin—a number that easily beat out professional bug bounty programs/platforms run by the likes of Trend Micro ZDI, Wordfence, and Patchstack.
Ironically, this was a disaster waiting to happen, with the Linux Kernel team laying out some weird rules for issuing CVEs right after the moment it received its CNA status.
We say weird because they are quite unique among all CNAs. The Linux kernel team argues that because of the deep layer where the kernel runs, bugs are hard to understand, and there is always a possibility of them becoming a security issue later down the line. Direct quote below:
"Note, due to the layer at which the Linux kernel is in a system, almost any bug might be exploitable to compromise the security of the kernel, but the possibility of exploitation is often not evident when the bug is fixed. Because of this, the CVE assignment team is overly cautious and assign CVE numbers to any bugfix that they identify. This explains the seemingly large number of CVEs that are issued by the Linux kernel team."
While this looks good on paper, the reality is that other projects also manage similarly sensitive projects, but they don't issue CVEs for literally every bug fix. You don't see Intel and AMD issuing hundreds of CVEs with each firmware update, even if their CPUs are where the Linux kernel runs.
These projects vet reports to confirm that bugs pose a security risk before issuing a CVE and triggering responses with their customers, such as inventory asset scans and emergency patch deployments.
Instead, the Linux Kernel team appears to have adopted a simpler approach where it puts a CVE on everything and lets the software and infosec community at large confirm that an issue is an authentic security flaw. If it's not, it's on the security and vulnerability management firms to file CVE revocation requests with the precise Linux Kernel team that runs the affected component.
The new Linux CNA rules also prohibit the issuance of CVEs for bugs in EOL Linux kernels, which is also another weird take on security. Just because you don't maintain the code anymore, that doesn't mean attackers won't exploit it and that people wouldn't want to track it.
The Linux team will also refuse to assign CVEs until a patch has been deployed, meaning there will be no CVEs for zero-days or vulnerabilities that may require a longer reporting and patching timeline.
The new rules also create a confusing process of validating, contesting, and rejecting CVEs. I'm not going to go into all of that since the venerable Brian Martin did a way better job back in February. Open Source Security's Bradley Spengler shared a real-world example last week of why the entire process of analyzing, validating, and revoking Linux CVEs is now a giant clusterf**k of confusion and frustration. We quote him:
"To say this is a complete disaster is an understatement. This is why CVEs should be for vulnerabilities, should involve actual analysis, and should provide that information in the CVE description, as any other responsible CNA would be doing."
While Linux maintainer Greg Kroah-Hartman tried to justify the team's approach to its new CVE rules, as expected, this has not gone down well with the infosec community.
Criticism has been levied against the Linux Kernel team from everywhere, and there have been some calls for the Linux team to reconsider their approach to issuing CVEs.
The new rules were criticized right from the get-go. The likes of Katie Moussouris, Valentina Palmiotti, Ian Coldwater, Bradley Spengler (again and again), Adam Schaal, Tib3rius, the grsecurity team, the GrapheneOS team, and a whole bunch more, foresaw the disaster that is currently unfolding.
And if this isn't bad enough, the Linux kernel team appears to be backfiling CVEs for fixes to last year's code, generating even more noise for people who use CVEs for legitimate purposes.
Some described the Linux team's approach as "malicious compliance" after the project was criticized for years for downplaying vulnerability reports and contesting CVEs assigned to its code by other CNAs. That may not be the case, as the new approach has some fans who see its merits, such as forcing more people to upgrade their kernels on a more regular basis.
"The Linux CNA intentionally adopts an overly cautious approach and assigns a new CVE when in doubt. While this may surprise many, it is a perfectly legitimate and entirely honest strategy. In contrast, vendors of proprietary software often tend to take the opposite approach, minimizing the assignment of CVEs whenever possible. Effectively managing the substantial number of CVEs involves understanding your kernel configuration, having a clear threat model, and ensuring the ability to update the kernel as needed. I hope that other large projects will eventually adopt Linux’s approach."
Unfortunately, all of this CVE spam also could have not happened at a worse time. Just as the Linux Kernel team was getting its CNA status, NIST was slowing down its management of the NVD database—where all CVEs are compiled and enriched.
NIST cited a staff shortage and a sudden rise in the number of reported vulnerabilities—mainly from the IoT space. Having one of every fifth CVE being a Linux non-security bug isn't helping NIST at all right now.
Breaches, hacks, and security incidents
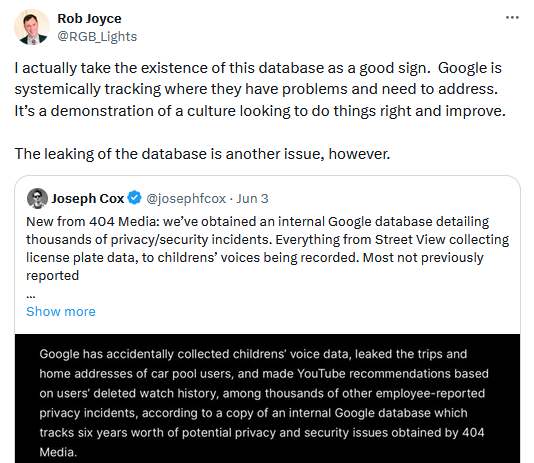
Google internal DB leak: 404 Media has obtained a copy of an internal Google database that contains details on privacy and security incidents that took place inside the company. The database contains details on thousands of incidents reported by Google employees internally between 2013 and 2018. These include issues with Google products, accidental data collections, vulnerabilities in third-party vendors, and mistakes made by single Google staff or contractors. Google confirmed the leak and said all reported issues were resolved internally.
Davis County squad: A group of high school students from Davis County are flooding phishing sites with fake credentials to prevent hackers from spotting the real ones. [Additional coverage in KSL]
Trecente domain hijack: A threat actor pulled out a domain hijack to target a... wait for it... a wedding rings store from Japan. [Additional coverage in Piyolog]
Verny cyberattack: A cyberattack has disrupted the operations of Russian retail store chain Verny. The incident took place over the weekend and impacted more than 1,000 of the company's stores. The attack crippled the store's payment terminals at cash registers and self-checkout counters. No group has taken credit for the incident so far. [Additional coverage in Retail.ru/English coverage in The Record]
Synnovis ransomware attack: A ransomware attack at lab service provider Synnovis has forced at least three London hospitals to cancel surgeries and redirect emergency patients. According to Metro, the incident is impacting the availability of lab results and has delayed transplant surgeries and blood transfusions. One of the affected hospitals is a children's care unit, and the biggest group is London's King's College Hospital.
Northern Minerals ransomware attack: The Bian Lian ransomware gang has taken credit for a ransomware attack on Northern Minerals, one of Australia's rare-earth mining companies. Northern Minerals has confirmed the incident in a filing [PDF] with the Australian Securities Exchange. The incident took place in March but only now came to light after the Bian Lian group started leaking some of the company's files on the dark web. [Additional coverage in CyberDaily]
Telegram scraped data: HIBP has recently indexed more than 361 million email addresses that a security researcher scrapped from Telegram channels. There's no Telegram leak. These are emails shared inside Telegram groups and channels—typically in ones advertising hacked data.
BC hack: The government of Canada's British Columbia region says a recent state-sponsored hack of its IT systems "hit 22 email boxes containing sensitive information about 19 people." The investigation is still ongoing, and no formal attribution has been made. [Additional coverage in the CBC]
Snowflake breach: Security firm HudsonRock has put out a statement on LinkedIn claiming it took down a blog post about the Snowflake breach after receiving a letter from CrowdStrike and Snowflake's legal teams. According to a report, the hackers behind the Snowflake breach claim to have lied and trolled the HudsonRock team about how they gained access to Snowflake accounts, which explains why this incident reached the stage of blog removals and legal letters.

TikTok high-profile hacks: A threat actor appears to be using a zero-day exploit to hack and take over high-profile TikTok accounts. According to Forbes, the malicious code is sent to victims via TikTok DMs and requires no user interaction except opening the message. TikTok says it is aware of the hacks and is investigating the issue. Some of the larger hacked accounts include CNN, Sony, and Paris Hilton.
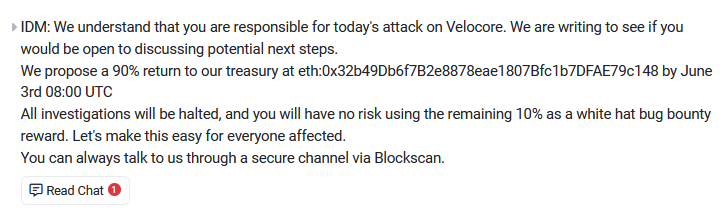
Velocore crypto-heist: A threat actor has exploited a vulnerability in the Velocore DeFi platform to steal $6.8 million worth of Ether tokens. The hack took place on Sunday and targeted one of the company's smart contracts. Velocore staff are willing to forget about the hack if the attacker returns 90% of the stolen funds.
General tech and privacy
GrapheneOS duress password: Mobile operating system GrapheneOS is adding support for a duress password. The feature will allow users to set a special password that deletes all their data when entered. GrapheneOS says the duress-initiated wipe does not require a reboot and cannot be interrupted. Developers say they added the feature to help users who may be forced under threats of violence to reveal their password or users who are having their legal rights violated.
QNAP default password change: QNAP says it will stop using a device's MAC address as its default password. Going forward, the company will use a cloud app named Cloud Key and data from the device's label to provide new users access to their devices.
Major Google Workspace change: Google says it will start logging changes made to Drive accounts via the Drive API. The move comes after threat actors abused the Drive API to interact with Drive accounts without their malicious activity being spotted. Google Drive accounts are commonly used for malware delivery and data exfiltration via Drive API calls. The new change will allow Google Workspace admins to detect abuse of their infrastructure via the Drive API, opening new opportunities for detection and response.
Microsoft "fixes" Win11 install: Microsoft has fixed a workaround that previously allowed users to install Windows 11 without a Microsoft account. The fix removes the option to run the company's latest OS with a local account. The update comes at a bad time when the company is being criticized for adding a spyware-like feature to the OS via its new Recall feature. Windows 11 is set to become the company's main operating system in October of next year, when Windows 10 reaches its end-of-support date. [Additional coverage in PCWorld]
Microsoft Education complaint: European privacy group noyb has filed a complaint against Microsoft with Austria's data privacy regulator. Noyb claims the Microsoft 365 Education service violates the GDPR and children's data protection rights. The privacy group says Microsoft lies when it says that schools can control how their data is stored and that Microsoft secretly tracks children's activities online. Noyb has asked the Austrian data protection authority DSB to investigate the company.
Government, politics, and policy
Hungary's pro-Kremlin party boycotts hack investigation: A series of leaked documents has revealed Hungary's ruling Fidesz party covered up a 2022 hack of the country's Ministry of Foreign Affairs. The Hungarian opposition called an extraordinary Parliamentary meeting to question Fidesz about the leaked documents, but the ruling party boycotted it. The pro-Kremlin party called the meeting an "election stunt" and a "farce" and refused to attend. Under Prime Minister Viktor Orban, Hungary has repeatedly sabotaged the EU's attempts to provide military aid to Ukraine and impose sanctions on Russia. [Additional coverage in 444]
Denmark raises cyber threat level: Denmark's cybersecurity agency has raised the country's cyber threat level for destructive cyber attacks. Officials raised the level from low to middle due to increasing threats from Russian hackers. The middle level is level three on a five-level scale.
White House to harmonize cybersecurity regulations: The White House has promised to work with other government agencies and the private sector to harmonize all the different cybersecurity regulations being passed by lawmakers and agencies. The promise comes a day before the Senate Homeland Security Government Affairs Committee is set to hold a meeting on the topic.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Nucleus Security co-founder and COO Scott Kuffer about recent trends the company has observed among customers when it came to patch management and how service level agreements (SLAs) became a sign of an organization's security health.

Cybercrime and threat intel
Data brokers convicted: Two former executives of a US marketing firm were found guilty at a jury trial for illegally selling the data of millions of Americans. Robert Reger and David Lytle of Epsilon Data Management took data from the company and sold it to fraud groups specializing in mass-mailing schemes. The data contained the names and home addresses of 100 million US households and was used to send scam letters to Americans over a period of 10 years. The Justice Department says the two execs often worked with scam groups to compile lists of consumers more likely to respond to the scams, such as elderly and financially vulnerable groups.
V3B PhaaS: Resecurity has linked a series of attacks on European banks to a new Phishing-as-a-Service platform named V3B. The platform launched in March 2023 and has been advertised on Telegram and the dark web. Resecurity says V3B built a client base by focusing on European banks and the quirks in their login procedures. One of these is support for QR and PhotoTAN code phishing and the ability to chat with victims in real-time.
BoxedApp abuse: Check Point says it's seeing multiple malware gangs abuse the BoxedApp commercial packer service to deploy their payloads.
New npm malware: DevSecOps company Phylum has discovered new malicious packages on the npm repository that target developers working with the Gulp automation toolkit. The campaign targets developers on Windows systems with a remote access trojan.
Work-from-home scams: The FBI has warned consumers not to fall for work-from-home jobs that offer to pay in cryptocurrency for menial tasks such as rating restaurants or "optimizing" services by repeatedly clicking a button.
Threat/trend reports: Abnormal Security, Akamai, AU10TIX, Cato Networks, Google Cloud (Mandiant), Kaspersky, Kaspersky (again), and Veracode [PDF] have recently published reports covering infosec industry threats and trends. The most interesting of these is the Google Cloud (Mandiant) one, summarized below.
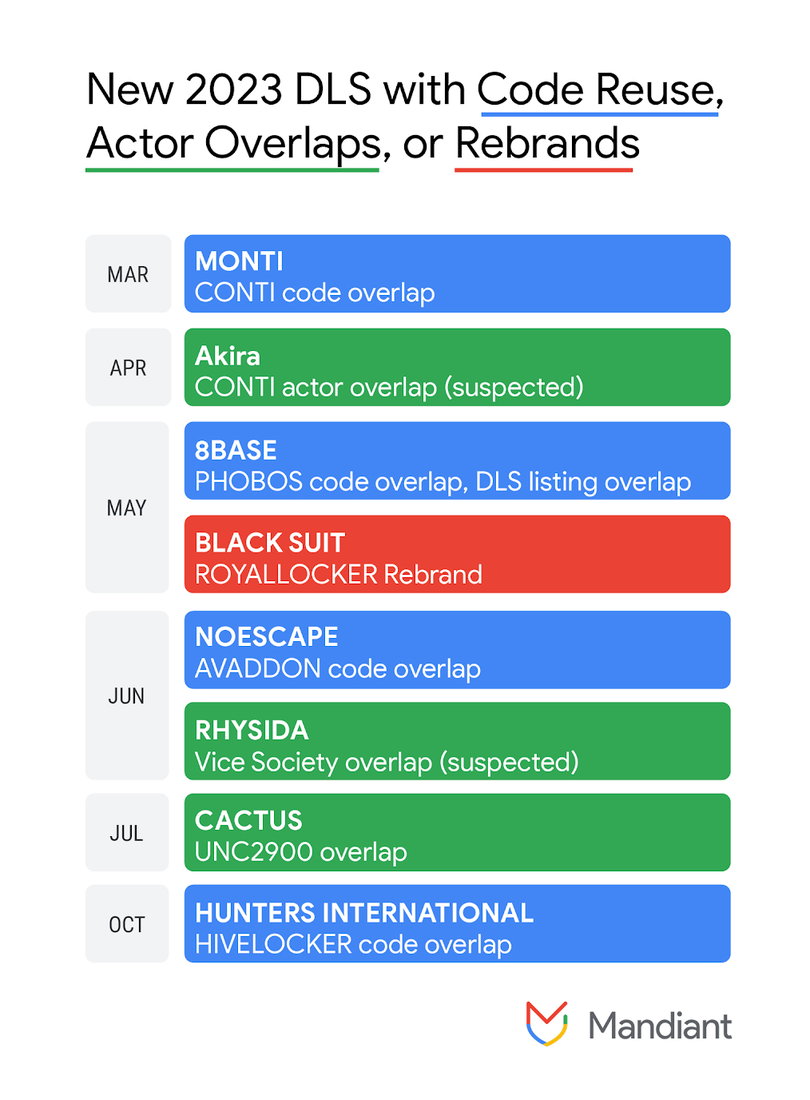
- In 2023, Mandiant observed an increase in ransomware activity as compared to 2022, based on a significant rise in posts on data leak sites and a moderate increase in Mandiant-led ransomware investigations.
- Mandiant observed an increase in the proportion of new ransomware variants compared to new families, with around one-third of new families observed in 2023 being variants of previously identified ransomware families.
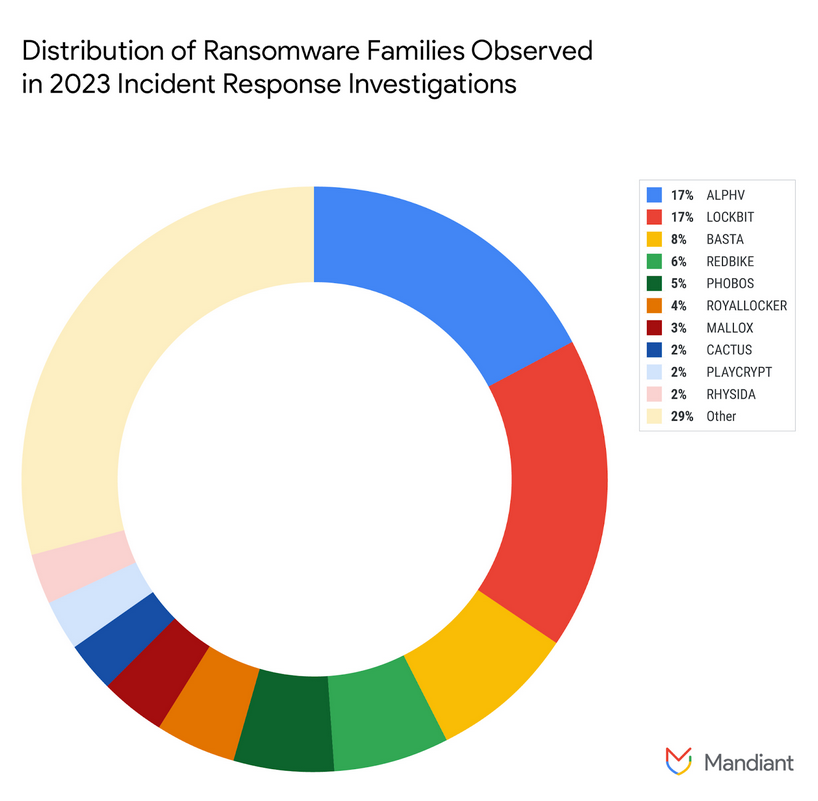
- Actors engaged in the post-compromise deployment of ransomware continue to predominately rely on commercially available and legitimate tools to facilitate their intrusion operations. Notably, we continue to observe a decline in the use of Cobalt Strike BEACON, and a corresponding increase in the use of legitimate remote access tools.
- In almost one-third of incidents, ransomware was deployed within 48 hours of initial attacker access. Seventy-six percent (76%) of ransomware deployments took place outside of work hours, with the majority occurring in the early morning.
Malware technical reports
Vidar Stealer: CyFirma takes a look at Vidar, one of the most widely used infostealers today.
DarkGate: Trellix has published a report on DarkGate v6, a new version of the RAT released at the start of the year.
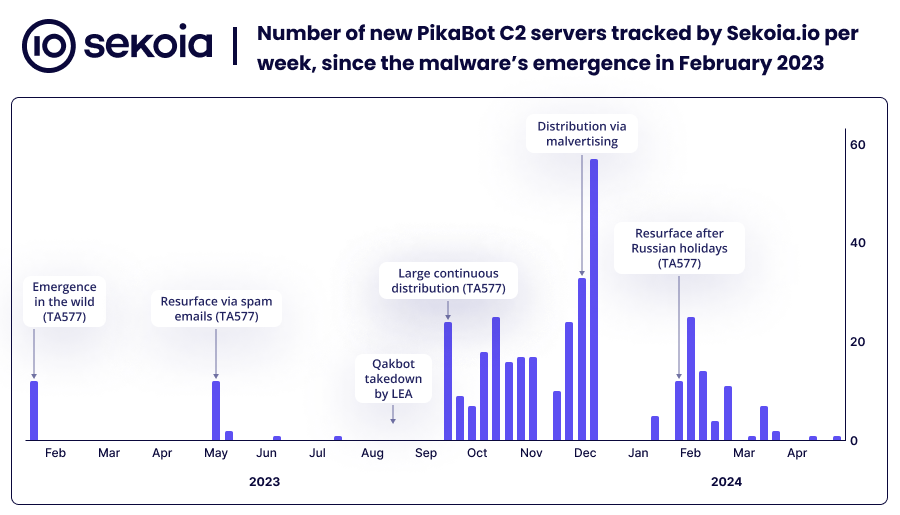
PikaBot: Sekoia has published a report on the now-seized PikaBot malware loader botnet. Sekoia was one of the companies that participated in Europol's Operation Endgame, which took down the botnet last week. The report looks at PikaBot's history since it launched in February 2023.
Sponsor Section
Nucleus Security's COO Scott Kuffer shows Patrick Gray their vulnerability management platform. It ingests scan outputs from a number of vulnerability identification tools, normalizes that information and then allows vulnerability management teams to do things like assigning responsibility for certain types of bugs to the correct people.
APTs, cyber-espionage, and info-ops
Operation Veles: Chinese security firm QiAnXin has discovered a new APT group targeting Chinese research and educational institutes. QiAnXin says the new UTG-Q-008 group uses a botnet to hide its activities. The botnet is exclusively made of Linux systems and has several springboard nodes inside China's internet space. The company has been tracking the group for almost a year but did not make a formal attribution. QiAnXin said the group sometimes deployed a cryptominer on systems with powerful NVIDIA RTX graphics cards.
UAC-0900: A threat actor tracked as UAC-0900 is targeting Ukrainian civil servants, military members, and employees of defense companies with malicious Signal messages. According to Ukraine's CERT team, the messages attempt to lure users into installing Windows apps infected with a remote access trojan (DarkCrystal RAT). Ukrainian officials say the campaign is part of a recent larger trend where threat actors have switched from emails to using instant messengers to go after their targets.
UA campaign: Fortinet has published a report on a mal-spam campaign exclusively targeting Ukrainian organizations, attempting to deploy Cobalt Strike payloads.
APT28: Logpoint researchers have published a report on APT28's newest malware arsenal and post-compromise tools.
APT29's Wineloader: BinaryDefense looks at Wineloader, a modular backdoor linked to APT29 operations.
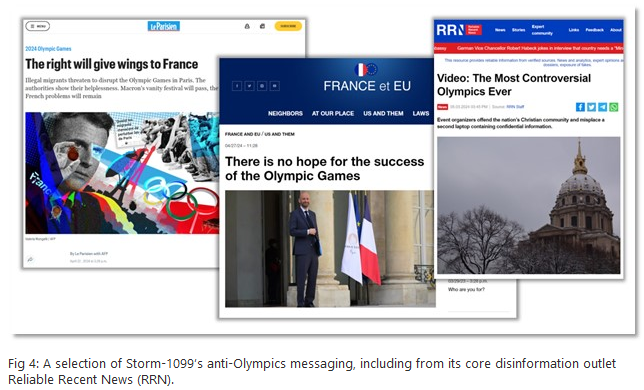
Olympics disinformation: Two Russian influence actors (Storm-1679 and Storm-1099) have pivoted in their operations and are now targeting the upcoming 2024 Olympic Games. The two groups are running social media campaigns defaming the IOC and spreading fear of violence and terrorist attacks during the games. Microsoft says the campaign started in late 2023 and is ramping up ahead of the games. In many cases, the groups use AI-generated content and forgeries of French news outlets. The campaigns attacked the International Olympic Committee, French President Emanuel Macron, and French society, and also promoted right-wing pro-Kremlin parties. On the same note, threat intel company Recorded Future also released a comprehensive report of cyber threats targeting the Olympics this year that goes beyond just Russian disinformation campaigns.
Vulnerabilities, security research, and bug bounty
Crypto whitehat legal defense fund: A cybersecurity non-profit for the cryptocurrency sector (SEAL) has announced the first legal defense fund to help protect security researchers (whitehats) who hack crypto platforms to intercept and secure funds before threat actors can abuse security flaws.
Cox modem takeover vulnerability: Security researcher Sam Curry has discovered a vulnerability in the backend of Cox Communications that could have allowed threat actors to hijack the Canadian ISP's modems. The vulnerability impacted one of the company's backend APIs. If exploited, it could have allowed threat actors to execute commands and modify settings on millions of Cox modems. Curry accidentally discovered the vulnerability while investigating why his own router was hacked.
ClangOver: PQShield cryptography security analyst Antoon Purnal has published a proof-of-concept named ClangOver that exploits a timing leak in the reference implementation of Kyber (ML-KEM), the soon-to-be NIST standard for post-quantum key encapsulation. More details in Purnal's blog post here.
Check Point VPN bug: Security firm Check Point has reminded users to install a recent firmware update to protect themselves against a recent major vulnerability in its security appliance's VPN module. After initially being caught off guard, the company's support thread on the issue has ballooned in size with loads of new information and requirements.
Telerik PoC: Researchers from the Summoning Team have released a PoC for unauth RCE attacks on Progress Telerik Report servers. The PoC chains two older vulnerabilities patched in March and May this year—namely CVE-2024-1800 (post-auth RCE) and CVE-2024-4358 (auth bypass).
Fortinet SQLi vulnerability: Horizon3 has published the second part of its analysis of CVE-2023-48788, an SQL injection vulnerability in the FortiClient EMS. The vulnerability entered active exploitation in March, shortly after a PoC was published online.
KEV update: CISA has updated its KEV database with a new vulnerability currently actively exploited in the wild, a 2017 Oracle WebLogic command injection tracked as CVE-2017-3506. The vulnerability was reported as exploited in the wild by the Water Sigbin group last month by Trend Micro.
OpenSSL security audit: The Open Source Technology Improvement Fund has published a recent security audit of the OpenSSL project. The audit targeted OpenSSL v3, which features a new provider architecture and eight new cryptographic primitives. The audit found 24 security issues, which have been patched.
ZyXEL security update: ZyXEL has published a security update to patch five vulnerabilities in its network-attached storage (NAS) products. Security firm Outpost24 discovered all five vulnerabilities. One of the vulnerabilities is a secret backdoor account named "NsaRescueAngel" and a remote code execution vector. ZyXEL released security updates even if the NAS models reached End-of-Life last year.
Android Security Bulletin: Android security updates for June 2024 are out. No zero-days, and there are three security issues addressed in Google Play system updates (Project Mainline) this month. The Pixel security bulletin was late and wasn't up when we wrote this. Will probably go live at this URL.
Android Binder 2023 vulnerability: Android's own red team has published a write-up on CVE-2023-20938, a use-after-free vulnerability in the Android Binder device driver. Details about the vulnerability were also presented at the OffensiveCon security conference last month in Berlin. Unfortunately, a video of the talk is not yet available. Other talks are, though. See end of this newsletter.
Another Android vulnerability: On the same note, Meta's security team has published a write-up on CVE-2024-31317, a command injection vulnerability in the Zygote process patched in this month's Android security bulletin that can allow malicious apps to read any other app's data, such as per-app secrets and login tokens.
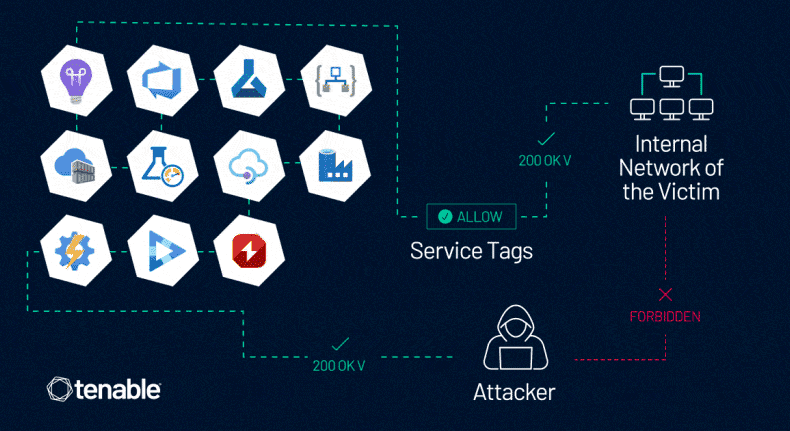
Azure firewall bypass: Security firm Tenable has discovered a vulnerability in the Azure firewall system. The vulnerability allows a malicious attacker to bypass firewall rules that were set up using Azure Service Tags. Tenable says threat actors can forge requests from trusted Service Tags to access a target's resources and private data without additional validation. Instead of fixing the issue, Microsoft has updated its Service Tags documentation. Tenable is recommending that Azure customers use additional authentication and authorization layers.
Infosec industry
New tool—goLAPS: Orange SensePost's Felipe Molina has released goLAPS, a tool to retrieve LAPS passwords from a Windows domain.
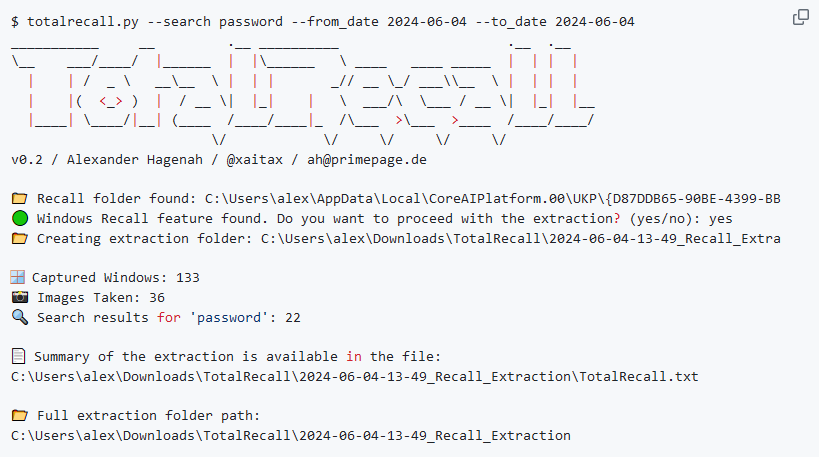
New tool—TotalRecall: Security researcher Alexander Hagenah has released TotalRecall, a tool that extracts and displays data from the Recall feature in Windows 11. A known Windows leaker also released Amperage, a tool to enable the Recall feature on devices that aren't officially supported.
OffensiveCon24: Talks from the OffensiveCon24 security conference, which took place at the start of May in Berlin, are available on YouTube.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about law enforcement agencies trolling cyber criminals when they carry out disruption operations, and why it might be counterproductive.





