Risky Biz News: The EU will make vendors liable for bugs
In other news: Wiper attacks hit Israel via ESET partner; Microsoft loses weeks of security logs; DOD looks to buy deepfake tech.

This newsletter is brought to you by Okta. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
The European Union has updated its product liability law to cover software and associated risks, like security flaws and planned obsolescence.
The new EU Directive on Liability for Defective Products [PDF] replaces one of the EU's oldest directives and will provide consumers with the legal tools to hold companies liable in court if they sell defective products.
The biggest change to the old directive is the addition of software products to the list of covered goods.
Companies that sell or want to sell in the EU will have to make significant changes to how they are currently doing business if they have failed to invest in proper software development and cybersecurity practices.
The new directive extends liability to vendors for software that contains security flaws, and those flaws lead to any damage to consumers. This includes both physical damage caused by defective or insecure software but also material damage, such as loss of functionality and features, loss of financial assets, and others.
The directive also classifies the lack of a software update mechanism to be a product defect and makes the vendor liable. Software vendors are also forbidden to withhold information about a software update's negative impact.
The only exemption in liability coverage is when the software update requires the consumer to manually install an update, but generally, the directive sees vendors liable as long as they have control over their product after a sale.
The directive also extends liability to vendors who use any type of planned obsolescence system to artificially reduce the life span of their products. This includes software designed to slow down a device, hardware components engineered to fail after a certain period, or an update that degrades a software's performance in order to entice users to move to a new service, tier, or product.
Companies can also be held liable for misleading consumers about a product's durability, repairability, or expected life span.
The directive requires victims to prove a product's defectiveness, but it also adds a new legal mechanism to force vendors to make required evidence available.
The new rules exclude free and open-source software (FOSS) from its requirements.
The new directive was approved earlier this year by the EU Parliament and earlier this month by the EU Council. It is set to go into effect in 24 months, in the fall of 2026.
Breaches, hacks, and security incidents
Radiant Capital crypto-heist: A threat actor stole over $50 million worth of crypto assets from DeFi platform Radiant Capital. In a post-mortem, the company says the attacker compromised the hardware wallets of three geographically distributed core developers. The attackers showed a fake user interface for the wallet that tricked the developers into signing malicious transactions that approved the Radiant thefts.
Nidec ransomware attack: Japanese tech giant Nidec says it suffered a ransomware attack at the start of August. Nidec was previously known as the Nippon Densan Corporation.
Cisco breach: Cisco has identified the source of a recent security breach as its DevHub portal—now taken down.
Ambient Fiance domain hijack: The Ambient Finance crypto-project has reported a DNS hijack of its main website.
Pravosodye attack: The Pravosodye IT system at Russian courts is still down after a Ukrainian data wiper attack earlier this month. [Additional coverage in Teleport]
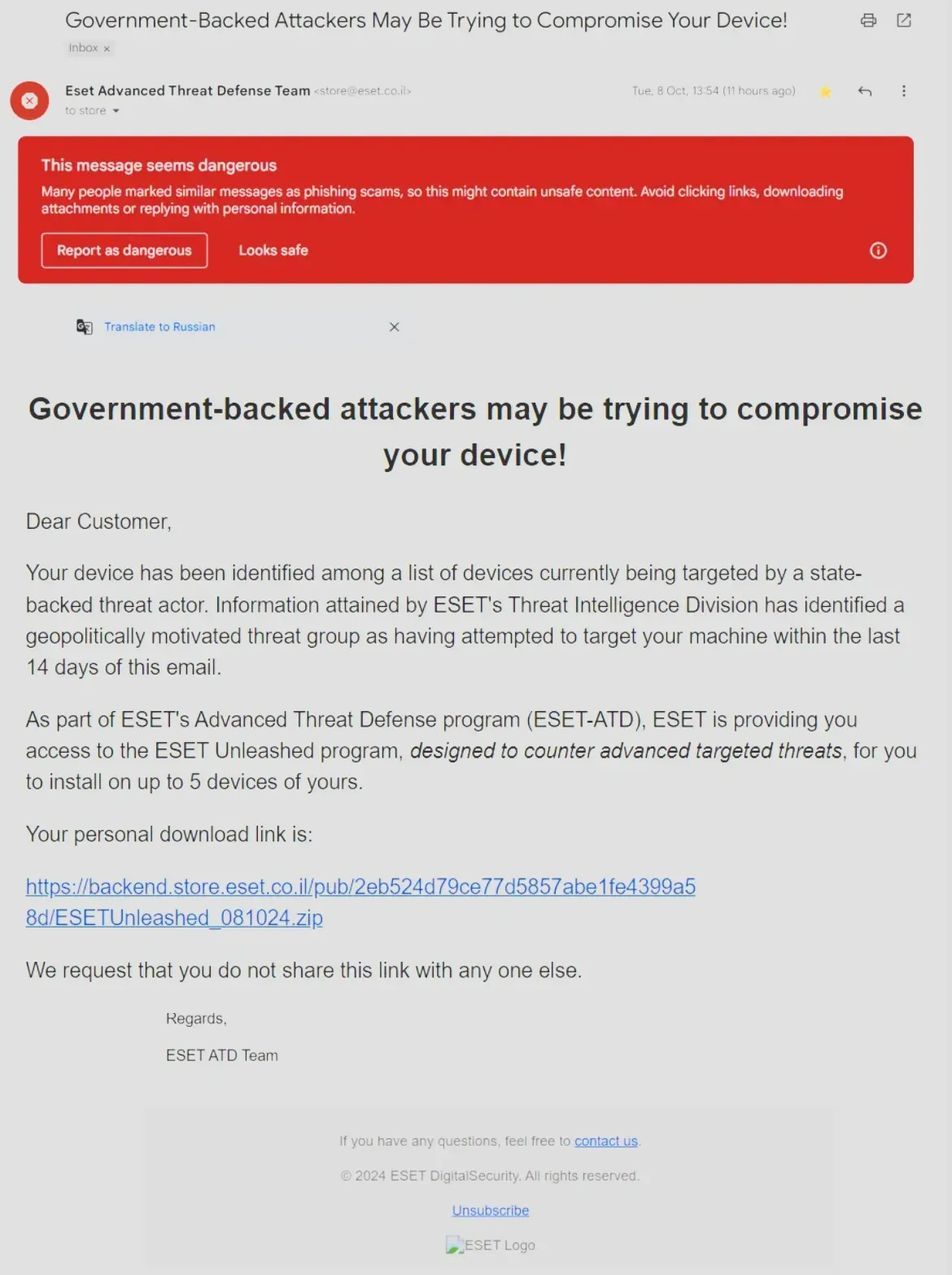
Wiper attacks in Israel: A threat actor has breached the servers of ESET's partner in Israel and has sent phishing emails to Israeli companies containing a data wiper. The emails pretended to be from an ESET team that deals with government-backed threats and offered a new security tool for customers. The emails were sent on October 8, a day after the one-year anniversary of the October 7 Hamas attack on Israel. No threat actor has publicly taken credit for the operation. ESET confirmed the incident but has not said how many companies were affected. [Additional coverage in DoublePulsar]
General tech and privacy
Microsoft loses weeks of security logs: Microsoft has notified customers that it lost almost a month of security logs for multiple cloud products. The company blamed the issue on a bug in its monitoring agent that uploaded incomplete log data. Affected services include Microsoft Entra, Microsoft Sentinel, Azure Virtual Desktop, and others.
Android security changes: The Android FIDO2 API is moving to hardware-based key attestation. Web apps using the API will need Chrome 130+ to support the change.
WordPress drama: WordPress creator Matt Mullenweg has forced an update to the WordPress.org code of conduct to "protect" private direct messages and the "community" after he was caught harassing staff in private messages.
BattleEye false bans: The BattlEye anti-cheat system says it patched an exploit that allowed threat actors to ban other players' accounts. The exploit affected multiple games, including PvP titles such as PUBG, Rainbow Six Siege, and Escape from Tarkov. The project says it's working with game makers to reverse the bans based on its logs. BattlEye disclosed the bug a day after Activision fixed a similar exploit in the Call of Duty anti-cheat.
Government, politics, and policy
EU to run gait recognition pilot: EU countries will test a gait recognition pilot program as a way to identify and profile people crossing EU borders. [Additional coverage in The Record]
DJI sues the Pentagon: Chinese drone maker DJI has sued the Pentagon over listing the company as a Chinese military contractor. [Additional coverage in Reuters]
DOD looking for AI deepfake tech: The US Defense Department is looking to acquire AI deepfake technology capable of creating believable internet personas. According to procurement documents, the deepfake technology must be capable of generating images, videos, and audio. The online personas must also be advanced enough to pass identity checks online and must not be detectable by social media algorithms. The new technology will be made available to the Joint Special Operations Command, or JSOC, a special operations unit inside the DOD. [Additional coverage in The Intercept]
New FTC click-to-cancel rule: The Federal Trade Commission is introducing a new click-to-cancel rule to help consumers easily cancel online subscriptions. The agency says it passed the rule because of the large number of complaints it was receiving on a daily basis about the complicated steps required to cancel a subscription. The new rule will go into effect 180 days after it's published in the Federal Register.

Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Brett Winterford, Okta’s APAC Chief Security Officer. Brett has mined Okta’s data and finds strong evidence that organisations invest in phishing-resistant authentication methods once they know they’ve been targeted by groups that excel at social engineering (such as Scattered Spider).
Brett discussed this research at Okta’s conference, Oktane, which was held in Las Vegas on 15 to 17 October 2024.
Cybercrime and threat intel
CEO charged for fake security audits: US authorities have charged the CEO of a data center company for lying about his company's security requirements in order to win an SEC contract. Prosecutors claim Deepak Jain created a fake auditing company to falsify security certifications for his main data center business. The SEC paid Jain over ten million dollars for data centre services over six years. Jain's LinkedIn page lists him as the founder of AiNET. He now faces up to 10 years in prison.
New npm malware: One hundred sixteen malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
BraveTalk scam campaign: The Brave browser has sent out an alert about a malicious campaign that tricks users into downloading and running malware on their system disguised as an app for Brave Talk—an online service similar to Google Meet.
Crypt Ghouls group: Russian security firm Kaspersky has published a profile on Crypt Ghouls, a new threat actor that appeared at the end of last year and is attacking Russian businesses and government agencies with ransomware.
"The group under review has a toolkit that includes utilities such as Mimikatz, XenAllPasswordPro, PingCastle, Localtonet, resocks, AnyDesk, PsExec, and others. As the final payload, the group used the well-known ransomware LockBit 3.0 and Babuk."
Microsoft runs fake tenants, floods phishing sites: Microsoft is running a massive deception campaign that is flooding phishing sites with fake credentials. The credentials lead to Azure tenants for fake companies. Microsoft says that threat actors use the credentials to log into the Azure honeypots in 5% of cases. The company uses the data collected from the honeypots to document new techniques. It takes around 20 days for threat actors to catch on to the deception and stop logging into the accounts. [h/t Jeremy Kirk]
Malware technical reports
Necro trojan: Zimperium says it has more info on the Necro Android trojan, spotted by Kaspersky on the Play Store this year.
Divulge, DedSec, and Duck Stealer: CyFirma has published a report on Divulge, DedSec, and Duck Stealer, three new infostealers found on the underground market.
X-ZIGZAG RAT: ThreatMon looks at X-ZIGZAG RAT, a new remote access trojan targeting Windows systems that the company spotted this month.
Latrodectus: Forcepoint looks at IcedID's supposed replacement, the Latrodectus malware.
GHOSTPULSE: Elastic's security team has published the second part of an analysis of GHOSTPULSE, a new loader currently used in campaigns leveraging compromised websites, SEO techniques, and malvertising. Part one is here.
Bumblebee returns: The Bumblebee malware botnet has resurfaced almost five months after Europol and the FBI disrupted its operation. The group was one of six botnets that had command and control servers seized at the end of May. Security firm Netskope says it has seen the first campaign carrying new Bumblebee samples since the takedown.
Beast ransomware: Cybereason has published a profile on the Beast ransomware, a group active since 2022.
Fog ransomware: Dark Atlas has published an analysis of the Fog ransomware's inner workings.
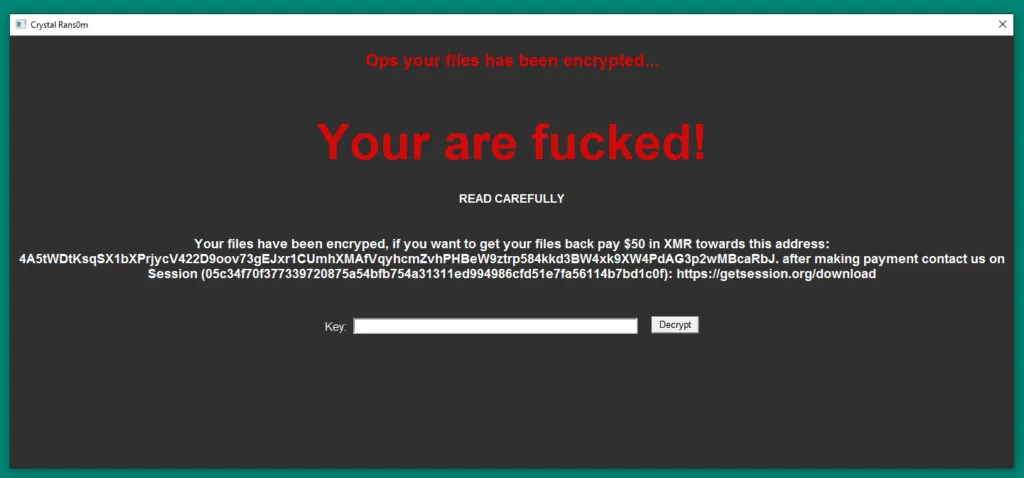
Crystal Rans0m: Security researchers have discovered a new ransomware strain that combines the features of infostealers with classic file-encrypting ransomware. The new Crystal Rans0m strain was first spotted in September. It infected a victim, stole browser, Steam, and Discord data, and then encrypted files to demand a ransom. The malware seems to be the work of amateurs as it only demands the equivalent of $50 in Monero.
Sponsor Section
In this sponsored product demo Okta's Harish Chakravarthy and Brett Winterford walk through four new features Okta introduced in the wake of the emergence of modern attacker techniques targeting identity providers. These features will help you to prevent or limit the damage to your environment if an attacker manages to compromise a session token.
APTs, cyber-espionage, and info-ops
Lazarus' InvisibleFerret: South Korean security firm Hauri has published a report on InvisibleFerret, a new Python-based backdoor hidden in malicious files hosted inside GitHub repositories.
Russian disinfo is easy money in the US: The AP has discovered a new US right-wing influencer producing anti-Ukraine content—this time a 12-part documentary—with Russian funding.
Prigozhin disinfo empire: Yevgeniy Prigozhin's Patriot Media Group, the holding company for many of his disinfo operations, has formally dissolved.
Rybar reward: The US State Department is offering a $10 million reward for information on a Russian company named Rybar and its employees. Officials say the company is behind an influence operation targeting the US election and the Texas secession movement. It is also involved in praising Russia's war in Ukraine and advancing anti-Western narratives. The State Department says Rybar was part of Yevgeniy Prigozhin's fake news media empire but is now financed by Russian state company Rostec. So far, the US says it identified nine Rybar employees—some of which are connected to Russia's military.

Vulnerabilities, security research, and bug bounty
New Google Cloud VRP: Google Cloud has re-launched its vulnerability rewards program (VRP).
"The Google Cloud VRP will continue to focus on coordinating new vulnerabilities and compensating security researchers for helping us in our mission, and offers a top award of $101,010."
China's hacking contest ecosystem: The Atlantic Council has published a deep dive into China's local hacking contests. It also released the China CTF Competition Tracker, a website that keeps track of all recurring competitions.
HM Surf vulnerability: Microsoft has found a new macOS vulnerability nicknamed HM Surf that can allow attackers to bypass the Transparency, Consent, and Control (TCC) security feature and gain unauthorized access to a user's protected data.
New WhatsApp leak: Security researcher Tal Be'ery has discovered a new WhatsApp bug that leaks a user's OS information.
Remote Registry PoC: Akamai has published details and a PoC for CVE-2024-43532, an elevation of privilege (EoP) vulnerability in the Microsoft Remote Registry client.
Realtek SD card reader vulns: Dell, HP, Lenovo, and MSI laptops can be hacked via new vulnerabilities impacting their SD card reader. The bugs reside in a Realtek driver that interfaces the SD card reader the laptop's OS. Realtek has released security updates, but the issues have gone undiscovered for years and impact a wide range of products. According to security researcher zwClose, the security bugs allow read-write access to both kernel and physical memory.
Trend Micro RCE: Trend Micro has released a security update to fix a remote code execution vulnerability in its Cloud Edge security appliance. Tracked as CVE-2024-48904, the vulnerability can be exploited by un-authenticated attackers to inject and run commands on the device. The issue has a severity rating of 9.8/10, and the company has asked customers to patch it as soon as possible.
Synology RCEs: Taiwanese hardware vendor released five security updates last week, including for two RCEs in the Synology Camera and the Synology BeeStation NAS.
SharePoint RCE: BI.ZONE researchers have published an analysis of CVE-2024–38227, a remote code execution in SharePoint that Microsoft patched last month.
Atlassian security updates: Atlassian has released six security updates last week, part of the company's October Patch Tuesday.
New Roundcube exploitation: A threat actor is exploiting an old vulnerability in the Roundcube open-source webmail software. According to Russian security firm Positive Technologies, the attacks targeted a government organization of an unnamed former Soviet state. The attacks took place in June, a month after the vulnerability (CVE-2024-37383) was patched. The vulnerability is a cross-site scripting issue that can be exploited via animated SVG images.
Samsung zero-day: Samsung has released patches for a zero-day (CVE-2024-44068) exploited in the wild. The vulnerability is a use-after-free vulnerability in a driver for the Samsung Exynos processor. The attacks were detected by Google researchers. Google says the zero-day was part of a larger exploit chain.
New side-channel attack: Researchers have published details about a new side-channel attack on AMD and Intel CPUs.
Infosec industry
Threat/trend reports: Check Point, EAST [PDF], GuidePoint, and Wordfence have recently published reports and summaries covering various infosec trends and industry threats.
New tool—VulnHuntr: Protect AI has released VulnHuntr, a LLM-based tool for analyzing code and finding security flaws. The tool has allegedly found 14 zero-days.
New tool—VulnCov: One eSecurity's Miguel Llamazares has released VulnCov, a tool that correlates Semgrep scans with Python test code coverage to identify which vulnerable code has been executed by unit tests.
New tool—Ghostport: Security researcher vxFemboy has released Ghostport, a port spoofing tool designed to confuse and mislead port scanners.
New tool—OpenVMM: Microsoft has open-sourced OpenVMM, a modular, cross-platform Virtual Machine Monitor (VMM) written in Rust.
Bsides Exeter 2024 videos: Talks from the Bsides Exeter 2024 security conference, which took place in July, are now available on YouTube.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about how criminals are using deepfakes… but it is not the end of the world.
In this podcast, Tom Uren and Patrick Gray talk about the evolving relationship between Russian intelligence services and the country’' cybercriminals. The GRU's sabotage unit, for example, has been recruiting crooks to build a destructive cyber capability. Tom suspects that GRU thugs are not so good at hands-on-keyboard operations but excellent at coercing weedy cybercriminals to hack for the state.
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!




