Risky Biz News: Team Synacktiv wins a Tesla and a cool half mil at Pwn2Own 2023
In other news: CISA rolls out pre-ransomware notification system; NCA runs fake DDoS-for-hire websites; GitHub leaks private RSA key.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
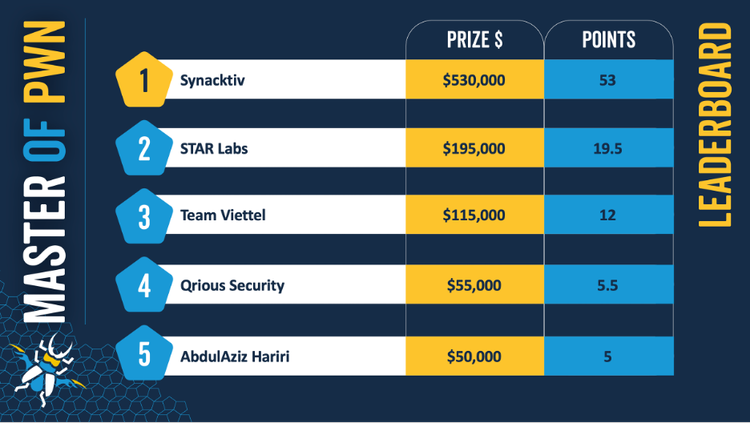
French cybersecurity firm Synacktiv has won this year's Pwn2Own hacking contest after dominating the competition with six successful exploits that brought its researchers a cool half mil ($530,000), the biggest award ever raked in by one contestant in Pwn2Own's history.
There are three Pwn2Own hacking contests that take place during a year: one dedicated to smartphones and IoT devices, one dedicated to industrial equipment, and one dedicated to desktops, servers, and smart cars.
Synacktiv won the latter—considered the most prestigious of all hacking contests today. This year's edition took place during the CanSecWest security conference, which wrapped up on Friday last week.
This marks the second time Synacktiv has won Pwn2Own after it also won the 2021 edition as well.
During this year's three-day contest [1, 2, 3], Synacktiv brought down some notable targets:
- $250,000 - heap overflow and an OOB write to exploit a Tesla Model 3's infotainment system for unconfined root access
- $100,000 - TOCTOU attack against a Tesla Model 3
- $80,000 - three-bug chain against Oracle VirtualBox with a Host EoP
- $40,000 - TOCTOU bug to escalate privileges on Apple macOS
- $30,000 - incorrect pointer scaling leading to privilege escalation on Ubuntu Desktop
- $30,000 - UAF against Microsoft Windows 11
Synacktiv's team members for this year's contest included Eloi Benoist-Vanderbeken, David Berard, Vincent Dehors, Tanguy Dubroca, Thomas Bouzerar, and Thomas Imbert.
Besides the $530,000 and the Master of Pwn trophy, Synacktiv will also receive a Tesla Model 3 car—as part of an agreement between the contest organizers (the Zero-Day Initiative) and Tesla.
All in all, Synacktiv went home with more than half of the prizes awarded at Pwn2Own this year—$1,035,000 and a car.
Breaches and hacks
Euler hacker returns funds: The hacker who stole $197 million worth of cryptocurrency from the Euler Finance platform has returned more than half to the beleaguered company. More than $107 million have been returned so far across three separate transactions. The returns come following negotiations between the two sides. [Press coverage in The Block]
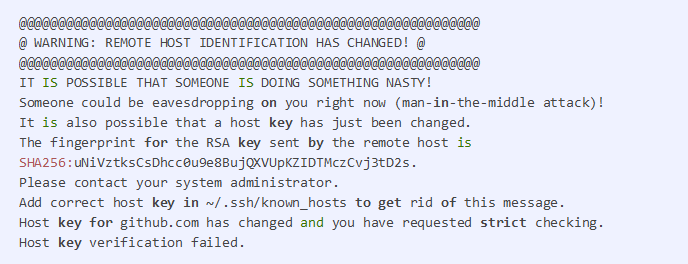
GitHub private key leak: Code-hosting repository GitHub has rotated its RSA private key that the company uses to secure Git operations sent over SSH on the GitHub.com domain. GitHub says it rotated the key after it was accidentally exposed in a public repository earlier in the week. The change does not affect browser traffic to the GitHub website nor Git operations performed on GitHub via HTTPS. Affected users will get a warning in their SSH interface (see below).
General tech and privacy
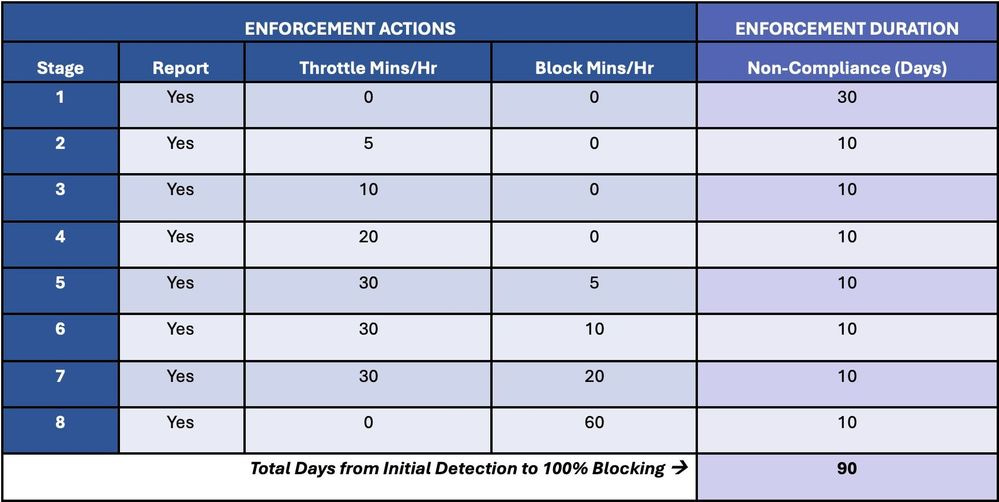
Microsoft to block emails from outdated Exchange servers: Microsoft plans to block emails on its Exchange Online infrastructure that are coming from on-premise Exchange email servers running outdated software. The block will not be enforced right away. Microsoft says it plans to notify Exchange server owners about their insecure server and gradually throttle email traffic from unpatched servers. If servers aren't patched after 90 days, Microsoft says it will block traffic from outdated servers. Microsoft says that once servers are patched, any throttling or block will be lifted immediately. The block is part of a new security feature named Transport-based Enforcement System and will apply to all on-premise Exchange servers that have formally reached end-of-life. The list includes Exchange 2007, Exchange 2010, and soon, Exchange 2013.
Government, politics, and policy
Dutch intelligence overview report: TIB, a committee that supervises the use of telecommunications interception powers by Dutch intelligence services, has published its yearly report for 2022. TIB says that last year, Dutch intelligence services AIVD and MIVD used their hacking capabilities exclusively on "strategic grounds." The report noted that while, in some cases, the intelligence services started operations before the TIB approval—a breach of protocol—the operations themselves were not illegal. TIB officials were annoyed they had to redact some parts of their report, though.
UA mandatory security audits: The Ukrainian government approved a resolution requiring mandatory security audits at critical infrastructure entities once every two or three years. Security audits must also be carried out during a "crisis situation."
Turkmenistan goes nuts trying to block Tor: The Turkmen government has taken extraordinary steps over the past several months to block access to the Tor network. According to volunteers in the Tor Project, the government has blocked entire IP ranges belonging to some of the world's largest hosting providers as part of an attempt to block access to Tor network bridges. Blocked hosting providers include AWS, Hetzner, Digital Ocean, and Linode. The government has also blocked Snowflake, a protocol developed by the Tor Project specifically for situations when their connection is blocked—which marks the first case where a government managed to block it. The Tor Project is now asking volunteers across the world to run Tor bridges over residential connections, which have been reported to still work inside the country.
FBI PSA on BEC supply chain hijack tactic: The FBI has published a public service announcement on how cybercrime gangs use tactics typically seen in BEC attacks to hijack supply chains and steal physical goods. These types of attacks take place when threat actors compromise a company's email accounts to message vendors and request product deliveries to new locations. The FBI says that "victimized vendors assume they are conducting legitimate business transactions" and are fulfilling purchase orders only to discover the fraud when invoicing the hacked company.
CYBERCOM confirms hunt-forward mission: US CYBERCOM confirmed last week it sent a hunt-forward mission to help the Albanian government recover from the cyberattacks conducted by Iranian hackers last summer. In total, CYBERCOM says it has conducted 44 hunt forward missions since 2018. Hunt-forward missions were sent to 22 countries. In addition to Albania, teams have deployed to Ukraine, Estonia, Lithuania, Croatia, Montenegro, North Macedonia, and others.
CISA rolls out pre-ransomware notification system: CISA launched a new program last week named the Pre-Ransomware Notification Initiative. CISA says this new team will work closely with the private industry to detect ongoing intrusions carried out by ransomware gang and notify the affected organizations before the attackers can encrypt files and damage networks. The agency says this initiative will notify US entities via its staff and pass on data about ransomware attacks at foreign entities to their countries' respective CERT teams. CISA says this new program has notified 60 entities about impending ransomware attacks since the start of the year. Officials say the program almost entirely relies on tips it receives from the private industry, such as the cybersecurity research community, infrastructure providers, and cyber threat intelligence companies.
"Without these tips, there are no notifications!"
Two weeks ago, CISA also launched another new program named the Ransomware Vulnerability Warning Pilot. That program works differently, as CISA will scan the networks of critical infrastructure entities and then notify companies that have networks open to common entry vectors used by ransomware gangs, even if a ransomware attack is not ongoing or has not taken place yet.
Risky Business Demo
In this Risky Business demo, Tines CEO and co-founder Eoin Hinchy shows off the Tines no-code automation platform to host Patrick Gray.
Cybercrime and threat intel
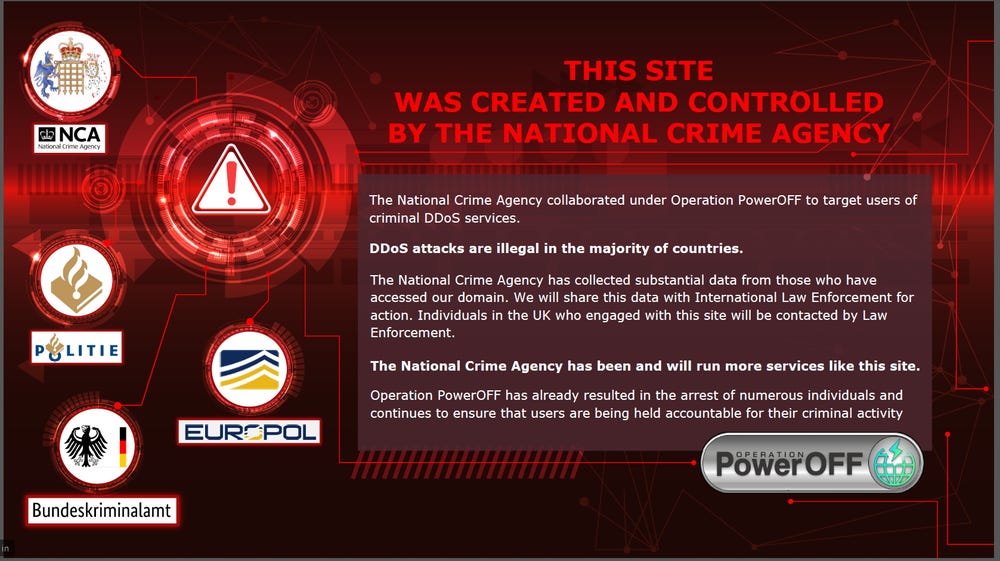
NCA runs fake DDoS website: The UK National Crime Agency says its agents have created several fake DDoS-for-hire services that are currently in operation today. The agency chose to reveal one of the sites last week by replacing its homepage with a splash screen announcing its involvement (see below). The NCA didn't say how many sites it ran but says it collected the data of "several thousand people" who have registered on the sites so far. Officials say they plan to notify and warn UK citizens. They also plan to pass the information of foreign nationals to international law enforcement.
BEC money launderers detained: The Australian Federal Police has detained four members of a cybercrime group on charges of laundering more than AUS$1.7 million stolen via BEC attacks. Officials say the group carried out at least 15 attacks from January 2020 to March 2023. The AFP says the four suspects set up more than 80 bank accounts using stolen identities to help transfer the money out of Australia. Suspects include a 26-year-old man from Wyndham Vale, a 30-year-old man from Adelaide, a 35-year-old woman from Durack, and a 27-year-old woman from Sherwood.
Pompompuring indictment: The US Justice Department made it official on Friday and announced the arrest of Conor Brian Fitzpatrick, 20, of Peekskill, New York. He's known online as Pompompurin, the admin of the now-defunct BreachForums. He was detained the week before, on March 17. The official arrest also means we have the official DOJ complaint. TechCrunch's Lorenzo Franceschi-Bicchierai has a breakdown of the main points from it.
Outlook zero-day attack investigations: Microsoft has released a guide for investigating Outlook accounts and see if they may have been targeted with a recent zero-day tracked as CVE-2023-23397.
6.8k malicious libraries in 2023: DevSecOps company Snyk says it recorded more than 6,800 malicious libraries uploaded on the npm and PyPI portals since the start of the year. Snyk says these recent discoveries bring the grand total to more than 144,000 malicious packages published to open-source software registries over the past several years.
New npm malware: Twelve new malicious npm packages spotted. Check out GitHub's security advisory portal for details.
Malware technical reports
4daLULZ: A write-up from MrBruh, a programmer and aspiring security researcher, goes through the process of dismantling a low-effort malware distribution campaign using an OBS installer as a lure.
ChinaZ: AhnLab researchers are seeing a new DDoS botnet named ChinaZ deploying its payloads on Linux systems with improperly configured SSH.
MacStealer: Uptycs has published a technical report on MacStealer, a macOS infostealer that can exfiltrate data to a remote Telegram channel. The malware is currently being sold via underground hacking forums.
Qakbot: Lab52 researchers have a report on the anti-analysis techniques employed by the Qakbot malware.
IcedID VNC backdoor modules: NVisio has a technical breakdown of Dark Cat, Anubis, and Keyhole—the VNC remote access backdoor module that the operators of the IcedID malware use to connect to infected systems. The modules are what security researchers call Dark VNC and what the IcedID gang calls the HDESK module.

Sponsor Section
Proofpoint is one of this newsletter's main sponsors. Below is a product demo Patrick Gray, the host of the main Risky Business podcast, recorded with them last year, where they show off Nexus People Risk Explorer, the company's product for mitigating insider threats:
APTs and cyber-espionage
Bitter APT: Intezer has published details on a Bitter APT campaign targeting the nuclear energy industry in China.
Donot Team: QiAnXin has a report on the recent operations of the Donot Team APT group. Victims of recent attacks include China, Pakistan, Sri Lanka, and other South Asian countries.
ICS APT attacks overview: Kaspersky published an overview of APT attacks on ICS networks that took place in the second half of 2022.
Vulnerabilities and bug bounty
Microsoft aCropalypse patches: Microsoft has released an out-of-band security update for the Snipping Tool on Windows 11 and the Snip & Sketch tool on Windows 10 to address a major security flaw. Publicly known as aCropalypse, the vulnerability allows threat actors to recover the original image from cropped or redacted screenshots. Initially, the vulnerability impacted only Android Pixel smartphones, but researchers discovered last week that Windows devices were also impacted. The Android version of aCropalypse is tracked as CVE-2023-21036, while the Windows variant is CVE-2023-28303.
WooCommerce Payments vulnerability: Automattic has released a security update for a WooCommerce module that handles store payments. Automattic says the vulnerability could permit unauthorized admin access to impacted stores. The plugin has more than 500,000 installs, but Automattic says it received the bug report via its HackerOne program, and it has seen no active exploitation in the wild so far.
Joomla under attack: Threat actors are exploiting a recently-patched vulnerability in the Joomla CMS. Tracked as CVE-2023-23752, the vulnerability allows unauthorized access to a site's endpoints, which can lead to the exposure of a site's Joomla database username and password.
CentOS failed to patch kernel bugs: Google's Project Zero team says the CentOS Linux distro has failed to backport kernel security fixes into older distros, leaving users and customers open to attacks. Google says that despite notifying RedHat Software of the issues and giving it 90 days to backport kernel security fixes to its older (and still supported) CentOS versions, the company failed to release security updates.
"It would be good if upstream Linux and distributions like you could figure out some kind of solution to keep your security fixes in sync, so that an attacker who wants to quickly find a nice memory corruption bug in CentOS/RHEL can't just find such bugs in the delta between upstream stable and your kernel. (I realize there's probably a lot of history here)."
CVE-2023-28760 (TP-Link): Security researcher Rocco Calvi has published details and a PoC on CVE-2023-28760, a remote code execution in TP-Link routers. The vulnerability is not exploitable via the internet and requires either physical or LAN access to the device. TP-Link has released patches.
Veeam PoC: Horizon3 researchers have published details and a PoC for CVE-2023-27532, a leak of database server credentials to unauth users. Similar reports are also available from Huntress Labs and Y4er.
DOD bug bounty program: Martin Matishak from The Record has a story on how the Pentagon slowly embraced its vulnerability bug bounty program across the years.
H26FORGE: A team of academics has designed H26FORGE, a platform for analyzing and identifying vulnerabilities in video encoding of H.264 files. The researchers say they identified several vulnerabilities, some of which have been patched (CVE-2022-42850, CVE-2022-42846, CVE-2022-32939, and CVE-2022-3266), while others not. Vendors like Apple, Mozilla, and VLC released updates, while companies like Google, MediaTek, and vendors that sell multimedia IP to SOC vendors did not. The paper [PDF] will be presented this summer at the USENIX security conference.
"First, domain-specific tools are useful and necessary for improving video decoder security. [...] Second, the video decoder ecosystem is more insecure than previously realized. Platform vendors should urgently consider designs that deprivilege software and hardware components that process untrusted video input."
Infosec industry
New tool—AntiCropalypse: Software developer Lexi Larkin has created a Discord bot that scans channels for aCropalypse-vulnerable images and deletes them before threat actors can recover or un-redact potentially sensitive images.
Acquisition?: One of the old domains of AdvIntel (advanced-intel.com) is not resolving, while the other one (advintel.io) is now redirecting to Red Sense. It appears an acquisition took place there.




