Risky Biz News: State Dept puts $10 million bounty on IRGC-CEC hackers
In other news: Windows downgrade attack revealed at Black Hat; ICO fines contractor behind NHS ransomware attack; SEC drops MOVEit hack investigation.

This newsletter is brought to you by Material Security, the company that secures the cloud office with unified email security, user behavior analytics, and data loss prevention for Microsoft 365 and Google Workspace. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

The US State Department is offering a $10 million reward for any information on six Iranians behind Cyber Av3ngers, an Iranian hacktivist group that has repeatedly attacked critical infrastructure across the US and other countries.
The six were identified as members of an Iranian cyber unit known as the Iranian Islamic Revolutionary Guard Corps Cyber-Electronic Command (IRGC-CEC).
The six were sanctioned by the US Treasury in February this year, but this marks the first time the US has formally linked the six to the Cyber Av3ngers persona.
The group emerged at the end of last year when it used default passwords to access PLCs from Israeli company Unitronics and deface control panels with anti-Israel and pro-Gaza messages.

The group focused its attacks on countries allied with Israel, with the most prominent of these hitting the water authority in Aliquippa, Pennsylvania.
According to the Shadowserver Foundation, there were between 500 to 800 Unitronics PLCs exposed on the internet at the time of the hacks. Several sources have confirmed to Risky Business earlier this year successful intrusions and defacements in the US, Australia, Israel, Singapore, Romania, and Czechia—although most did not have any lasting impact.
A month after the intrusion, the US intelligence community said the attack was the work of Iranian state-sponsored hackers and not a grassroots hacktivist movement—which was no surprise since Iran has been doing a horrendous job of hiding its cyber operations as "hacktivism" for a few years now.
It named the six responsible individuals as IRGC-CEC head Hamid Reza Lashgarian and five of the unit's senior officials—Mahdi Lashgarian, Hamid Homayunfal, Milad Mansuri, Mohammad Bagher Shirinkar, and Reza Mohammad Amin Saberian.
Although it did not link the six to Cyber Av3ngers at the time, clues in the Treasury Department press release allowed anyone in infosec to link the two.
However, these initial sanctions appear to have kicked a hornet's nest, as the US kept looking at IRGC-CEC activity.
A few months later, in April, the US sanctioned two of the IRGC-CEC's front companies and four of its hackers. One of them was a member of the Tortoiseshell APT and was also charged by the DOJ.
No charges have been filed against the six IRGC-CEC Cyber Av3ngers, but with sanctions and a State Department on their heads, an indictment may not be far away.

Breaches, hacks, and security incidents
ICO fines contractor over NHS hack: The UK's privacy watchdog has fined a software provider £6 million over a ransomware attack that crippled Britain's National Health Service (NHS) in August 2022. The UK ICO says the Advanced Computer Software Group failed to secure its IT systems, which allowed a ransomware gang to breach its systems, steal patient data, and encrypt servers used by a crucial NHS system. The LockBit ransomware group claimed the NHS ransomware attack. Two years later, UK authorities played a central role in dismantling the gang's operation.
LoanDepot ransomware losses: American mortgage provider LoanDepot says it incurred losses of almost $27 million in connection to a ransomware attack from January. The cost covers expenses related to recovering from the attack and providing coverage for more than 16 million customers who had their data stolen in the breach. LoanDepot was the fourth major US mortgage and real estate insurance provider that was hit by a cyberattack towards the end of 2023 and the start of 2024. Mr. Cooper, Fidelity National Financial, and First American Financial also reported similar attacks.
SEC drops MOVEit investigation: The SEC has notified Progress Software that it has closed its investigation into the company's handling of the 2023 MOVEit hacks. The SEC told Progress it does not plan to fine or continue any enforcement action for the time being. The SEC started investigating Progress Software over the MOVEit hacks in October of last year. The MOVEit hack took place over the Memorial Day weekend in 2023 when the Clop cybercrime group exploited a vulnerability in the Progress MOVEit file-sharing software to steal data and extort companies.
ADT hack: Home alarm and physical security company ADT has confirmed a data breach in SEC filings after its data was published on an underground hacking forum.
Ransomware attack kills cow: A ransomware attack on a Swiss farmer has led to the death of a pregnant cow and its unborn calf. The death occurred after the farmer couldn't receive health alerts from the milking station about the cow's condition while the PC was encrypted. The unnamed ransomware gang requested $10,000 to decrypt the farmer's computer. [Additional coverage in Agrarheute]
McLaren Health Care attack: At least 13 hospitals and clinics operated by McLaren Health Care across Michigan have been impacted by a mysterious cyberattack. [Additional coverage in The Record]
Nexera crypto-heist: A threat actor has stolen $1.8 million worth of tokens from cryptocurrency platform Nexera. The hacker allegedly exploited a vulnerability in the platform's smart contract. The attacker is linked to several other hacks, including the OKX $11 million crypto-heist. [Additional coverage in CoinDesk]
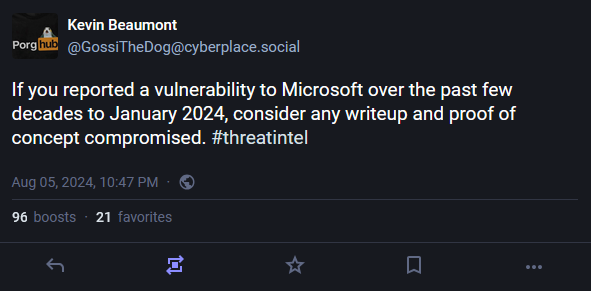
Midnight Blizzard hacks: The Russian hackers who breached Microsoft last year have stolen emails from email systems managed by the UK government. The breach impacted Home Office inboxes, according to a report from The Record. The UK government is the most well-known victim of the hack, besides Microsoft itself. Microsoft disclosed the hack earlier at the end of last year and said a Russian espionage group known as Midnight Blizzard breached its internal corporate network. The group stole emails from the inboxes of its management and security teams. Microsoft has tried to keep the hack and its aftermath and has been silently notifying affected customers—many of which remain unknown. Just days before The Record's report, security researcher Kevin Beaumont claimed the hack of Microsoft itself was much larger than previously disclosed. Beaumont said that Midnight Blizzard stole data on all security flaws reported to Microsoft's team for the past decades and that Microsoft failed to detect this bigger breach until January 2024, months after it disclosed the initial hack. Three days later, Beaumont's LinkedIn profile was mysteriously banned.
General tech and privacy
LibreOffice configuration guide: The German cybersecurity agency has published a guide for safely configuring LibreOffice.
macOS Gatekeeper update: Apple is making important security-related changes to the macOS Sequoia operating system that is scheduled to be released next month. The company is removing the option of pressing CTRL+Click to bypass the Gatekeeper security protections and open an unnotarized app. Users can still open the app by going through a more laborious procedure, but Apple has asked app developers to sign and notarize their apps with the company.
PSF suspends toxic core dev: The Python Software Foundation has temporarily suspended one of its core developers for three months after they spent weeks harassing other members on a variety of "weird" topics.
Google emails users: According to two reports, Google has allegedly sent an email to some customers to notify them that the company is legally bound to provide some of their confidential data to the US government in the case of investigations. I honestly thought everyone already knew this, but nice from Google to notify users of it.
Chrome to block 0.0.0.0: Chrome developers have announced they will soon block public websites from connecting to the local resources via the 0.0.0.0 IP address. Google previously banned public websites from accessing local resources through the more famous localhost and 127.0.0.1/8 URLs. The company says it simply forgot to ban the 0.0.0.0 URL at the time—mainly because it only impacted macOS and Linux users. Over the past decade, malvertising and IoT botnets have used malicious code that uses private URLs and IP addresses to exploit locally running apps. The 0.0.0.0 ban will take effect with the release of Chrome 133, expected around next January. [More about attacks on 0.0.0.0 via Oligo Security]
Chrome to support Web Monetization: Google will support the new Web Monetization API in a future version of the Chrome browser. The new API provides a way for websites to automatically receive and collect payments from users. The API allows users to tip website owners or provide small payments based on the time they spend browsing its content. Chrome is the first browser to publicly commit to support the new API, launched in February this year.
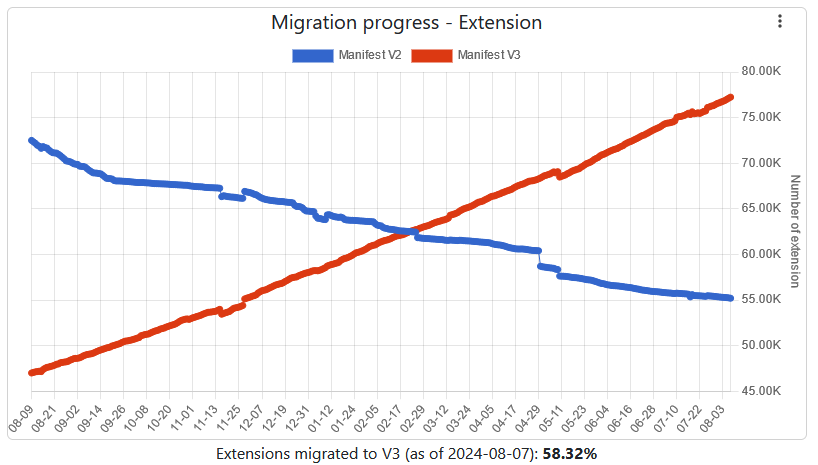
Chrome extension migration lagging behind: Chrome extension developers have migrated only 58% of Chrome extensions to the browser's new Manifest V3 extension framework. Google has recently started showing visible warnings to users still using extensions built on the older Manifest V2 framework. Based on recent stats, Google is set to purge more than 55,000 older Chrome extensions from its Web Store..
Government, politics, and policy
CISA's Secure by Demand: The US cybersecurity agency has asked companies that procure software to demand secure-by-design features in acquired products from their respective vendors. CISA says that such requests will help move the general state of software security faster if vendors understand that security is important for their clients. CISA is calling this new initiative Secure by Demand.
Full YouTube block in Russia: The Russian government is now fully blocking access to YouTube. It was previously just throttling its traffic. A full block was initially expected in September but was accelerated after Ukrainian forces took control of the Kursk region in Russia, and the site began hosting videos of Russian soldiers surrendering en masse and without fighting. As soon as the block entered into effect, threat actors started spreading "YouTube accelerators" to deploy malware.
Turkiye blocks popular VPNs: The Turkish government has blocked access to 27 VPN services across the country. The ban comes a week after the government also blocked access to Instagram. Privacy experts believe the government is trying to crack down on users still accessing the site through VPNs. Among the biggest VPN providers blocked this week are Proton, NordVPN, and Surfshark.

Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Rajan Kapoor, VP of Customer Experience at Material Security, on how threat actors view email inboxes as the targets of their attacks and not just an entry point into organizations.

Cybercrime and threat intel
WWH Club arrests: The US government has detained and charged the founders and administrators of an underground cybercrime forum on the dark web named the WWH Club. The two suspects were identified in court documents as Russian national Pavel Kublitskii and Alexandr Khodyrev of Kazakhstan. The US says the two founded the WWH Club in 2020, where they began trading in stolen data. The site had more than 170,000 registered users and allowed threat actors to buy stolen bank accounts, buy login credentials, hire hackers, and order DDoS attacks. Kublitskii was detained in Florida, while Khodyrev's status is not mentioned in court documents. Both fled their countries and sought asylum in the US in 2022, relocating to South Florida. [Additional coverage in CourtWatch]
Instagram hackers detained: Ukraine's cyber police detained three suspects on charges of hacking Instagram accounts using brute-force attacks.
Moldavian scammers detained: Moldavian authorities have arrested 12 suspects for their role in an online cryptocurrency investment scam. The group allegedly used online ads mimicking Romanian personalities and brands to trick Romanian-speaking users into investing in cryptocurrencies via a platform they controlled. Romanian officials say the group made over $3.2 million since 2022. At least 150 victims filed official complaints. [Additional coverage in Agerpres]
Cloud abuse: Broadcom's Symantec has published a report looking at how threat actors have been abusing cloud services in recent operations.
ScreenConnect abuse: Proofpoint has seen an increase in malware campaigns that are distributing ScreenConnect, a legitimate remote access and management program. The tool is being used by cybercriminals to access infected systems since it's not detected as malware (in most instances).
Google Drawings abuse: Menlo Security has published a report on a novel phishing campaign that abuses Google Drawings for its operations.
Post-compromise VPN abuse: On the same note, Akamai has published a report on how threat actors have abused VPNs post their compromise.
Large-scale DDoS: Akamai says it blocked a massive DDoS attack of 419 Tbps on July 15. The attack lasted for 24 hours and targeted a major financial service provider in Israel.
"The attacker deployed larger-than-usual resources, indicating a serious risk for future attacks."
DeathGrip RaaS: SentinelOne looks at DeathGrip, a RaaS platform that emerged in June and began advertising via Telegram.
New ransomware group: A new ransomware group named Mad Liberator has been spotted launching attacks and extorting companies.

Malware technical reports
CMoon: A new Windows worm named CMoon is currently spreading among Russian internet users. The malware is being spread via malicious documents hosted on Russian-specific sites. The first infections were spotted at the end of last month and have slowly grown in numbers. According to Russian security firm Kaspersky, the malware can copy itself to local drives, steal sensitive files, install other malware, and carry out DDoS attacks. It is unclear if CMoon is the work of a state-sponsored group.
BlackSuit ransomware: CISA says that the former Royal ransomware gang has now rebranded as BlackSuit and is engaged in a massive wave of attacks across the US. The US cybersecurity agency says that the Royal-BlackSuit group has now demanded ransoms going over $500 million from victims since September 2022, making the group one of the most dangerous gangs active today. Ransoms typically range from $1 million to $10 million, with BlackSuit's biggest demand reaching $60 million.
Play ransomware: Netskope researchers look at the Play ransomware's anti-analysis techniques.
Mimic ransomware: Sophos looks at a Mimic ransomware campaign targeting organizations in India. The campaign targets Internet-exposed Microsoft SQL servers for initial access. Similar Mimic campaigns targeting MSSQL databases were seen last year targeting South Korea.
Botnet 7777 (Quad7): Team Cymru has conducted a new analysis of the 7777 (Quad7) botnet, a year after it was first spotted, and has found an offshoot named 63256. Both botnets appear to command more than 12,700 infected systems, which are used primarily for brute-force attacks.
MichaMichaBot: CloudSEK has discovered a Telegram channel named MichaMichaBot that is currently being used by some cybercrime groups to launch phishing campaigns that abuse clickjacking on domains with missing "X-Frame-Options" HTTP headers.
PureVNC: Fortinet looks at a campaign spreading PureVNC to targeted systems, along with other "lovely" surprises.
macOS infostealer: Kandji looks at a new macOS infostealer that abuses the SwiftUI and OpenDirectory API to collect passwords from users.
New Android malware: Japan's CERT has published a report on a newly discovered Android malware strain that abuses a new injection technique targeting Smali widgets.
Sponsor Section
New attacks are harder to spot at greater volumes than your security team can handle. The legacy and so-called modern email security market has left you with two extreme options – write and maintain your own set of detection rules or trust a black box with no way to customize. Either route is a burden on security teams when testing and tuning rules or building and implementing response workflows. Watch a demo to see the Material difference for inbound email detection. Leverage the combined power of AI, behavioral analysis, custom detections, and collective intelligence to thwart new flavors of email attacks with precision and speed.
APTs, cyber-espionage, and info-ops
New APT malware: The same Symantec report linked above detailing new cloud malware trends also includes mentions of three new malware strains linked to APT activity—GoGra (Harvester APT), Grager (UNC5330), MoonTag (Sabre Panda).
i-SOON leak: APT-doxing group Intrusion Truth takes another look at the leak from Chinese cyber contractor i-SOON.
MuddyWater IDF campaign: Iranian APT group MuddyWater has sent a massive wave of emails to Israeli citizens posing as the country's military—the Israel Defense Force. The emails contained warning about an impending Iranian military attack and tried to lure users to click on a malicious link.
Kimsuky: Cybersecurity firm Resilience has published a report on Kimsuky's recent espionage operations targeting universities. The report also looks at one of the group's recent infrastructure OPSEC mistakes.
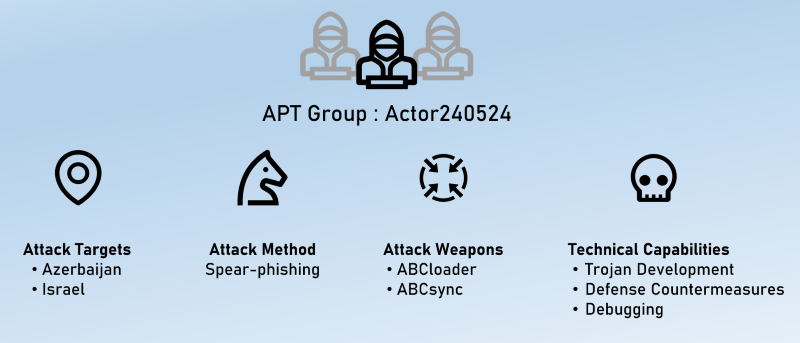
Actor240524: NSFocus researchers have spotted a new APT group they are calling Actor240524, which they've linked to espionage operations targeting Azerbaijan and Israel.
Vulnerabilities, security research, and bug bounty
Windows downgrade attack: Security firm SafeBreach Labs has discovered two vulnerabilities in the Windows operating system that can allow threat actors to downgrade OS components to vulnerable versions. The vulnerabilities reside in the Windows kernel (CVE-2024-21302) and update (CVE-2024-38202) functions. The issues were presented at the Black Hat security conference this week. Microsoft has acknowledged both issues and is scheduled to release patches next week.
GhostWrite attack: A team of academics has discovered three architectural vulnerabilities in CPUs from Chinese chipmaker T-Head. Named GhostWrite, the vulnerabilities impact the company's XuanTie CPUs, usually used in data centers. The vulnerabilities allow threat actors to bypass isolation and security features and gain full read-and-write access to impacted CPUs— C906, C908, and C910.
Solarman and Deye vulnerabilities: Bitdefender researchers have identified multiple vulnerabilities in Solarman and Deye solar power plant management platforms. If exploited, the vulnerabilities could allow threat actors to control power inverter settings and overload power grids. Solarman and Deye are currently used to manage around 195 GW of solar power, or around a fifth of all the global solar production. All issues have now been fixed.
Unitronics PLCs bugs: Claroty researchers have found two issues in PLCs from Israeli company Unitronics, the same one that had its devices exploited by Iranian group Cyber Av3ngers last year. Both issues have been patched.
Jenkins security updates: The Jenkins project has published two security updates for the project's core files.
Cisco security updates: Two security updates are also out for Cisco products, including an RCE in Cisco SPA300 and SPA500 IP phones.
Progress RCE exploitation: Threat actors are exploiting a recently patched vulnerability in the Progress WhatsUp Gold network monitoring solution. The attacks started at the start of August, according to experts from the Shadowserver Foundation. They are exploiting a pre-authentication remote code execution bug (CVE-2024-4885) that was patched in early June. Details and a PoC have been available since the start of July.
1Password vulnerability: 1Password has fixed a bug (CVE-2024-42219) in its macOS app that could have allowed third-party apps to impersonate the 1Password app and steal password data from its vault.
Linux eBPF vulnerability: Google's red team has published a write-up on CVE-2023-2163, a bug in the Linux kernel eBPF driver that can be exploited for LPE and container escape attacks.
FCST bypass: Researchers at Certitude Consulting have discovered a simple way to hide the First Contact Safety Tip, an Outlook security feature that warns users when they receive emails from a new address for the first time. The technique is dead simple and involves using CSS code to hide the First Contact Safety Tip warning box inside the email's body. This type of CSS hiding trick has been used many times in the past.
Infosec industry
Threat/trend reports: AWS and Positive Technologies have recently published reports covering infosec industry threats and trends.
Acquisition news: Swedish VC firm EQT will acquire a majority stake in data security firm Acronis.
ClownStrike drama: CrowdStrike has tried to take down a parody site making fun of its IT outage named ClownStrike. While its initial DMCA complained failed, the site also had complaints filed against it with Cloudflare and is now designated as a malicious phishing site on Fortinet products. Most of our readers (and me) didn't know or even care if this website existed... until CrowdStrike got all sensitive about it. Good job, CrowdStrike PR and legal!
New tool—Ice Axe: The Dune Group has open-sourced Ice Axe, a Snowflake Native Application designed to provide insights into Snowflake account activities that may be potential threats. It enables users to efficiently audit and monitor login history, user activities, and system usage.
New tool—Outflank C2: Pen-testing company Outflank has released Outflank C2, a commercial command-and-control framework. Blue teams might want to find a way to detect this.
New tool—SSHamble: Security firm runZero has released SSHamble (GitHub), a tool that can help security teams validate SSH implementations by testing for uncommon but dangerous misconfigurations and software bugs.
New tool—T3C: The Global Cyber Alliance has launched the Threat Taming Tools Collection (T3C), an extensive compilation of 300 resources tailored for cybersecurity professionals, researchers, and organizations.
New tool—Zero Trust Guide: NIST and 24 tech companies have published a new guide [PDF] on implementing Zero Trust architectures.
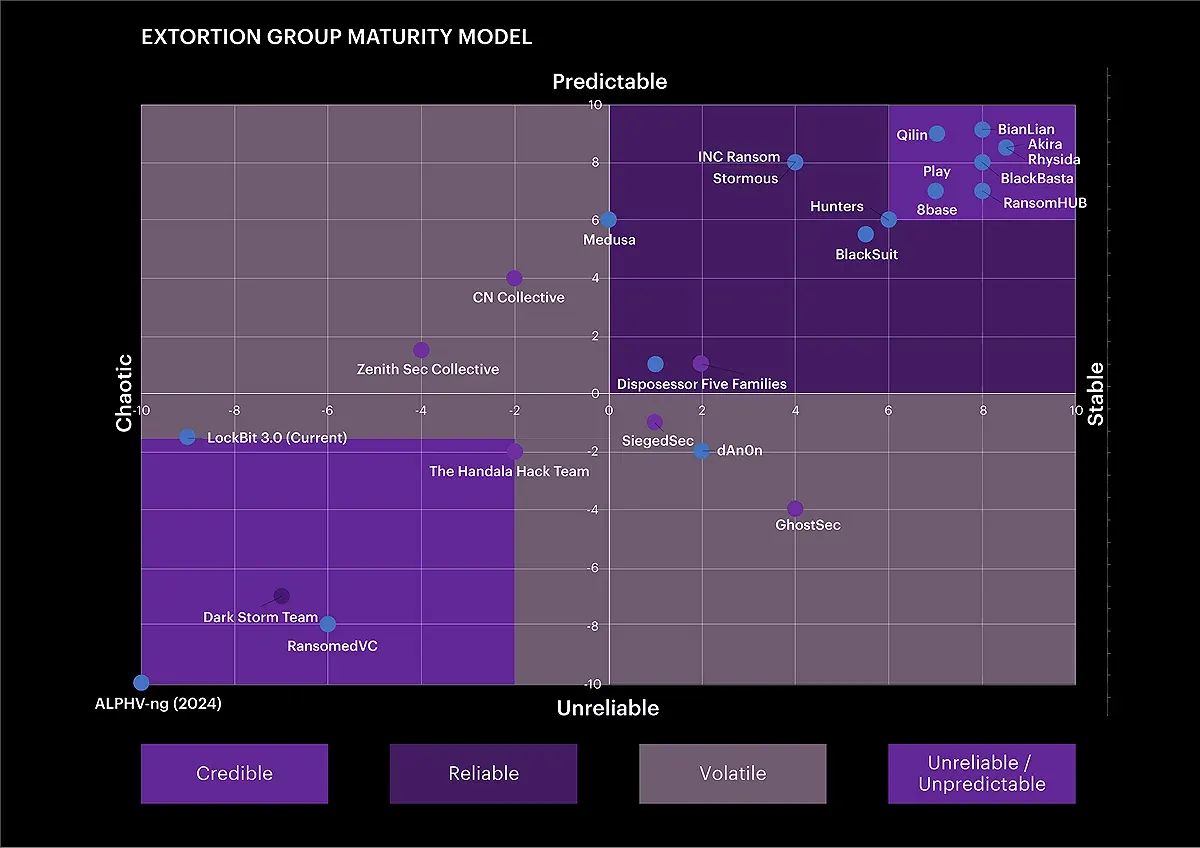
New tool—EGMM: Accenture has developed a new Extortion Group Maturity Model (EGMM) that assesses the credibility and stability of ransomware and data extortion groups.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss recent changes in a Chinese APT's tactics and how cyber security agencies have responded.
In this podcast, Tom Uren and Patrick Gray discuss the US’s National Counterintelligence strategy, and that it highlights the risk that foreign intelligence entities will use personal information to target and blackmail individuals.
The Risky Business team has recently started publishing video versions of our podcasts. Below is the main weekly show, with Pat and Adam at the wheel!




