Risky Biz News: STAR Labs wins Pwn2Own 2022
In other news: Oracle and Cisco release emergency security updates; ArguePatch malware attacks in Ukraine.
This newsletter is brought to you by Airlock Digital, Rumble Network Discovery, Proofpoint, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
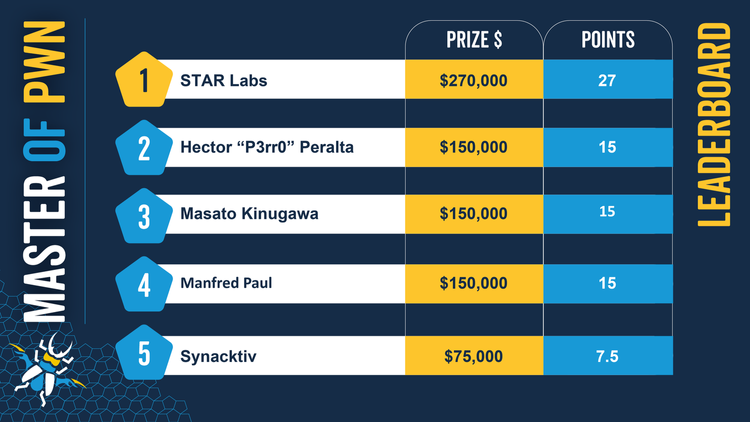
STAR Labs, a small cybersecurity company based in Singapore, has won the Pwn2Own 2022 hacking contest after demonstrating successful exploits against Microsoft Teams, Windows 11, Ubuntu Desktop, and Oracle VirtualBox.
The group won more than $270,000 in prize money and accumulated 27 points to win the contest.
- Microsoft Teams zero-click exploit of 2 bugs (injection and arbitrary file write) ($150,000; 15 points)
- Microsoft Windows 11 use-after-free elevation of privilege ($40,000; 4 points)
- Ubuntu Desktop use-after-free ($40,000; 4 points)
- Oracle VirtualBox OOB Read and OOB Write to reach escalation of privileges ($40,000; 4 points)
The researchers who made up STAR Labs' Pwn2Own line-up this year included Daniel Lim Wee Soong (@daniellimws), Poh Jia Hao (@Chocologicall), Li Jiantao (@CurseRed) Ngo Wei Lin (@Creastery), Billy Jheng Bing-Jhong (@st424204), Muhammad Alifa Ramdhan (@n0psledbyte), Nguyễn Hoàng Thạch (@hi_im_d4rkn3ss), Phan Thanh Duy (@PTDuy), and Lê Hữu Quang Linh (@linhlhq).
Our team members have put in a lot of hard work and efforts into this like other contestants. We have come so far by standing on the shoulders of giants
— starlabs (@starlabs_sg) 3:08 AM ∙ May 21, 2022
We won’t forget some of our previous team members whom we built the success on.
[2/n]
Although several Pwn2Own hacking contests usually take place throughout the year, the Pwn2Own CanSecWest edition, typically held in Vancouver, Canada, in the spring, is considered the world's premiere hacking competition today—where most top vulnerability researchers come to compete against each other. During CanSecWest, participants can select from a list of desktop and server products that they can hack during 15-minute sessions on stage.
Other Pwn2Own editions also take place throughout the year with a focus on smart devices and smartphones (Tokyo, in the fall), and in recent years even ICS/SCADA industrial equipment (Miami, in the winter).
Breaches and hacks
ICE contractor breach: Trust Stamp, a contractor for the US ICE, left the personal information of several dozen people on an unsecured database. The information included names, birthdays, home addresses, and driver's license data. The leaky server came to light after a security researcher notified BusinessInsider.
BfK breach: The Chicago Public Schools said that the data of 495,448 students and more than 56,000 staff was exposed last year after Battelle for Kids, an Ohio-based not-for-profit, suffered a ransomware attack last December. The incident is believed to have exposed the personal details of millions of children as the Ohio non-profit also caters to 250+ other schools, to which it provides data analytics services.
DeliveryClub: Russian food delivery platform DeliveryClub confirmed that it leaked more than 250 million data points containing information on past customer orders, including full names and delivery addresses, Interfax reported last week. And if that wasn’t bad enough, a Ukrainian security researcher found 10 million more additional records over the weekend with additional information such as chat messages sent by customers, and in some cases even email and geo-location data.
[NEW EXPOSURE] Apparently, RU-based Delivery Club @DeliveryClub recent data leak was not full enough, so they exposed a cluster with users support chats (via misconfigured Webim chat platform), incl. name/phone/IP/geo/emails (if added), order chats. 10+ records (might be dups).
— Bob Diachenko (@MayhemDayOne) 8:33 PM ∙ May 22, 2022
General tech and privacy
FairEmail shuts down: The developer of FairEmail, an open-source email client, shut down their applications after Google flagged its app as "spyware" without any explanation.
Government, politics, and policy
NATO meeting: Last week, the senior cyber coordinators from all NATO members and allies met in Brussels for the first time. They discussed topics of cyber defense and Russia's invasion of Ukraine and its implications for the cyber threat landscape.
EU concerns on cybercrime treaty: The European Data Protection Supervisor (EDPS) has raised concerns that a cybercrime treaty proposed by Russia to the UN and up for a vote later this year would weaken digital rights and limit international cooperation in cybercrime cases. The criticism comes as several human rights activists raised similar concerns last month, arguing that the treaty would classify online free speech as a form of cybercrime and provide oppressive regimes a way to go after critics and dissidents.
Ransomware victims do an eye-roll: Nikolai Patrushev, Secretary of the Russian Security Council, said last week that "the anonymity of the US-supported Internet contributes to the spread of computer viruses and the activities of cybercriminals" and that "hackers financially motivated by Western countries" are increasingly conducting cyber-attacks against the Russian Federation. (cough, Russian ransomware gangs operating with impunity, cough, cough, cough)
Signs of altered emails: DDoSecrets, an investigative journalism organization, claimed over the weekend that it found signs of altered and implanted evidence in a collection of emails that supposedly came from Hunter Biden's laptop. The organization said the supposedly altered email collection was being shared by members of the Republican Party and, more accurately, by "Trump allies and former staffers."
Cybercrime and threat intel
PyPI library: DevOps security company Sonatype has discovered a malicious Python package on the PyPI portal that would install Cobalt Strike beacons and backdoors on developers' systems. The package was named pymafka and tried to pass as PyKafka, a popular Python library for working with the Apache Kafka project.
Backdoored WP plugin: The Jetpack team said last week that versions before 9.9.7 of the WordPress plugin "The School Management Pro" from Weblizar contain a backdoor allowing an unauthenticated attacker to execute arbitrary PHP code on sites with the plugin installed
Deadbolt attacks: Last week, QNAP warned of new attacks carried out with the Deadbolt ransomware. In a blog post over the weekend, IoT search engine Censys said it had already detected more than 500 infected QNAP NAS devices part of these recent attacks. That number is around 3,500 in the ZoomEye search engine.
Midas rebrand: Security firm CloudSek said it discovered a new ransomware group calling itself Axxes and which appears to be a rebrand of the older Midas ransomware operation.
Malware technical reports
Metastealer: Security firm NCC Group has published a report on Metastealer, a new information stealer advertised on underground forums and designed to fill the void following Racoon Stealer suspending operations in March of this year.
Fbot: Chinese security firm Qihoo 360 has reported on a series of DDoS attacks against Chinese government websites using the Fbot IoT malware/botnet.
ArguePatch: ESET said the Sandworm APT had continued its attacks against Ukrainian targets with a new malware strain named ArguePatch. ESET said the malware was disguised in a version of its own antivirus, commonly deployed across Ukraine.
#BREAKING #Sandworm continues attacks in Ukraine 🇺🇦. #ESETresearch found an evolution of a malware loader used during the #Industroyer2 attacks. This updated piece of the puzzle is malware
— ESET research (@ESETresearch) 6:08 AM ∙ May 20, 2022
@_CERT_UA calls #ArguePatch. ArguePatch was used to launch #CaddyWiper. #WarInUkraine 1/6
APTs and cyber-espionage
Naming schemes: The Curated Intelligence group has published a blog post about how the APT naming schemes of various companies work and the thinking behind them.
Vulnerabilities and bug bounty
Oracle emergency security update: Oracle has released an emergency security update to patch CVE-2022-21500, a pre-auth RCE in the Oracle E-Business Suite. The company says that "if successfully exploited, this vulnerability may result in the exposure of personally identifiable information (PII)."
Cisco IOS XR zero-day: Cisco released router updates last week to fix a zero-day vulnerability (CVE-2022-20821) that was exploited in some of its devices earlier this month. The company said the vulnerability can "allow an unauthenticated, remote attacker to access the Redis instance that is running within the NOSi container."
Infosec industry
Ghostrings: Security firm NCC Group has open-sourced Ghostrings, a collection of Ghidra scripts for recovering string definitions in Go binaries.




