Risky Biz News: Squarespace DNS hijack spree hits crypto sites, everyone else watch out!
In other news: AT&T discloses Snowflake hack; Russia plans to ban YouTube later this year; Lazarus Group hacks CoinStats.

This newsletter is brought to you by asset inventory and network visibility company runZero. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Spotify:
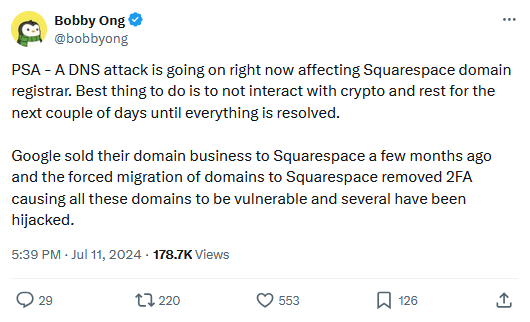
At least four cryptocurrency platforms hosting their domains on Squarespace have been hit by DNS hijacks over the past week.
The Celer Network, Compound Finance, Pendle Finance, and Unstoppable Domains reported losing control over their official websites on Thursday and Friday last week.
The hijackers pointed the domains to malicious servers hosting wallet-draining phishing kits.
According to a report [PDF] published by a team of security researchers from Paradigm and Metamask, the affected domains were previously hosted on Google's now-defunct domain business.
Squarespace acquired Google Domains earlier in June 2023 and moved all Google customers to its infrastructure in June this year.
The research team says domains migrated from Google Domains to Squarespace had their MFA disabled as a technical measure to prevent admins from being locked out of their accounts after the migration.
It's unclear if Squarespace notified domain admins of the change, but what's clear is that threat actors appear to have realized that MFA was disabled on some domains. The main theory is that hackers used leaked or stolen credentials to access admin accounts and change DNS records to hijack public websites and private email servers.
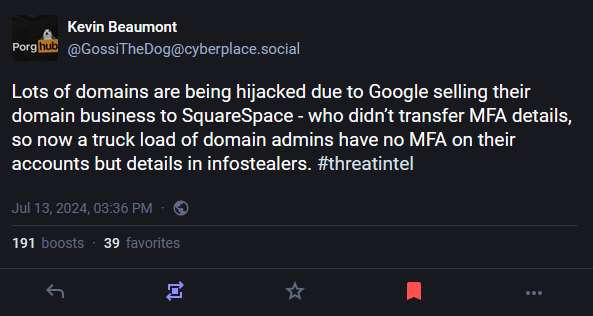
Since the first attack, cryptocurrency experts have compiled lists of crypto-related domains that are hosted on Squarespace. They are recommending that users don't access these sites until admins confirm they secured domains and enabled MFA on their Squarespace accounts.
Domain admins are advised to review accounts, change passwords, remove any new unauthorized users with access to DNS records, revert recent DNS changes, and make sure to enable MFA.
Researchers also warn that attackers may also try to use the hijacked domains to other systems inside an organization. This is done by hijacking MX records for the email servers and using Squarespace's role as a Google Workspace reseller.
"This gives Squarespace account administrators the ability to add new Google Workspace administrators, even if the same email address is not itself a Google Workspace administrator via the reseller service account. The threat actor leverages this to escalate access within the Google Workspace tenant. If no Google Workspace tenant is linked, then the threat actor may create a new Google Workspace tenant associated with the domain."
Security firm Blockaid, which was the one to spot the initial DNS hijacks, says the threat actor behind the attacks appears to have moved on and is now setting up phishing infrastructure for various brands, including the hacked ones.
While attacks have currently targeted crypto-themed websites, the same threat remains valid for every other former Google Domain website owner.
Companies that had public-facing or internal domains moved to Squarespace should review their Squarespace admin accounts and make sure MFA is enabled before ransomware gangs catch on to how useful this issue can be.
Post publication update: After this newsletter went live, the Paradigm and Metamask researchers have published their own post-mortem of the attacks after Squarespace mitigated the migration loophole.
Breaches, hacks, and security incidents
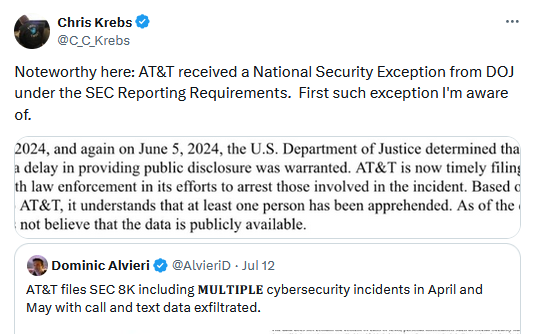
AT&T mega breach: US wireless carrier AT&T has disclosed a major security breach that impacts almost all of its cellular customers. The company says a hacker stole phone call and text message records from one of its cloud storage accounts. The breach took place in mid-April and AT&T confirmed to TechCrunch the incident is related to the larger Snowflake hacking spree. Wired reports that AT&T paid a $370,000 ransom to the hacker to delete the stolen data. A source has told 404 Media that an American man named John Binns is allegedly responsible for the hack. Binns previously also hacked T-Mobile in 2021. He was detained by Turkish authorities in late May and is currently facing extradition to the US.
mSpy data: More than 2.3 million records collected by the mSpy surveillance company was added to Have I Been Pwnd last week. [Additional coverage in TechCrunch]
Rapid Legal leak: Legal advice service Rapid Legal leaked 38 million records due to an exposed cloud storage database.
PyPI token leak: JFrog says it detected a leak of an access token from a developer with access to the GitHub repositories of the Python Foundation and the PyPI portal. The access token leaked through a public Docker container hosted on Docker Hub. JFrog says PyPI revoked the token 17 minutes after they reported the incident.
CDK pays ransom: Software company CDK Global appears to have paid a $25 million ransom to the BlackSuit ransomware gang. The payment took place last week, according to blockchain data. CNN reports the company has been slowly onboarding car dealers back onto its software platform. CDK Global fell victim to a ransomware attack in mid-June. Its services have been down for almost three weeks.
Indiana county files disaster declaration: The government of Clay County, Indiana, filed a disaster declaration last week following a ransomware attack. Officials say the attack has crippled its ability to provide critical services required for the daily operations. The incident has impacted the county's courthouse, health department, and probation and corrections system. [Additional coverage in The Record]
Indonesia ransomware attack: The Indonesian government says it has started recovering its systems after a ransomware attack took out its national data center. The attack took place last month and has impacted the activity of more than 160 government agencies. The government began recovering systems after the hackers apologized and released a free decryption key. The Brain Cipher ransomware gang took credit for the attack. [Additional coverage in Reuters]
Dough Finance crypto-heist: A threat actor has stolen $1.8 million worth of crypto-assets from decentralized finance (DeFi) protocol Dough Finance. The company says the attacker manipulated one of its smart contracts to steal some of its Aave tokens. Unlike other hacked crypto platforms, Dough Finance didn't offer the hacker a generous reward to return the stolen funds. Instead, it posted a message threatening the hacker with legal consequences.
CoinStats crypto-heist: The Lazarus North Korean hacking group has stolen $2.2 million worth of assets from cryptocurrency service CoinStats. The company says the hackers orchestrated a massive operation that breached multiple of its third-party service providers. Lazarus then gained access to its servers and stole the private keys of 1,590 customer wallets. The incident took place in mid-June, and CoinStats says it rebuilt its entire IT infrastructure after the attack.
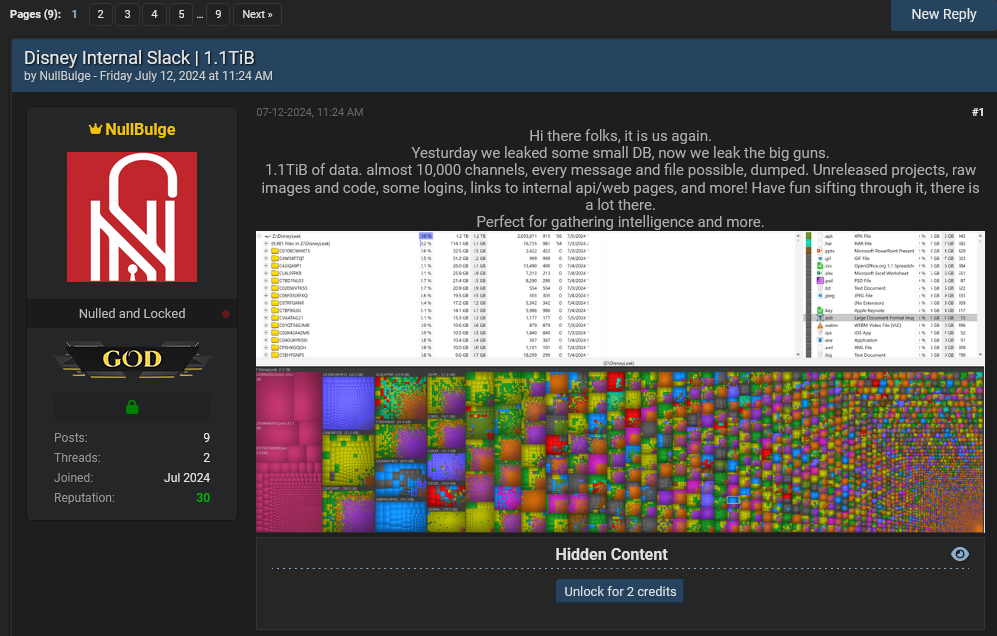
Disney hack: A hacktivist group named NullBulge has leaked more than 1.1 TB of data from Disney's internal Slack channel. The data was leaked on hacking forums and the group's official website. It allegedly contains unreleased projects, concept art, login details, and personal data. Some of the leaked data has been confirmed as authentic by both fans and gaming news sites. NullBulge says it leaked the data in response to Disney's unfair treatment and compensation of its writers and artists. According to a post on its website, the group claims it had help from a Disney employee. [Additional coverage in GameRant]
General tech and privacy
Thunderbird Nebula: Mozilla has released its new Thunderbird version with the new revamped Nebula UI.
Trump threatens Zuckerberg: Former US President Donald Trump threatened Facebook's CEO Mark Zuckerberg with a long prison sentence for... probably having his Meta account banned following the January 6 US Capitol attack. Trump got shot four days later. No, Zuckerberg didn't do it.
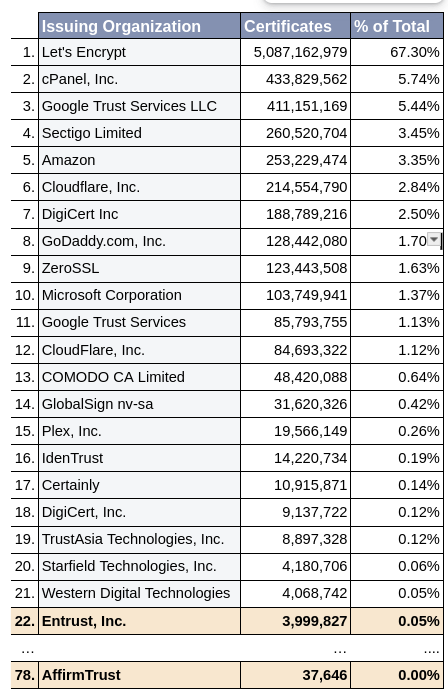
Entrust distrust stats: Google is scheduled to distrust Entrust-issued certificates inside Chrome at the end of October this year. According to Censys stats, Entrust is the 22nd-largest certificate authority on the internet.
Government, politics, and policy
Net neutrality on hold: The Sixth Circuit US Court of Appeals has put the FCC's net neutrality reinstatement on hold until August 5. [Additional coverage in Reuters]
AI consolidation: Three Democrat Senators have asked the FTC to investigate Amazon, Microsoft, and Google for their efforts to consolidate and create a dominant market position in the emerging AI market.
EU says Twitter broke DSA: The European Commission says Twitter does not comply with the block's Digital Services Act and plans to start an official investigation. Officials say the social network uses dark patterns to manipulate user behavior, does not share data with independent researchers, and is not transparent about its advertising policies. The Commission specifically called out Twitter for its use of the verified status that boosts post visibility but does not actually verify an account's identity. If the EU finds Twitter guilty, the company is on the hook for a fine of up to 6% of its revenue.
EU spyware sanctions: Mailyn Fidler, an Assistant Professor at the University of New Hampshire Franklin Pierce School of Law, argues that the EU could use its financial sanctions capabilities to go after spyware and surveillance enablers. More in her op-ed for Binding Hook.
Singapore bans OTPs: Singapore's Monetary Authority has ordered banks to phase out one-time passcodes (OTPs) within the next three months. The authority says the use of OTPs as a second authentication factor is currently insecure. Officials say threat actors have developed sophisticated social engineering tactics to reliably phish OTPs in real time.
Russia's Wikipedia: The Economist has published a profile on RuWiki, the Russian government's own version of Wikipedia where major political events are either rewritten or not included in order to advance Russian propaganda.
Russia throttles, plans to block YouTube: The Russian government is intentionally throttling download and upload speeds for YouTube traffic. The slowdowns were first reported last week by users all over Russia. In a TASS interview, government officials tried to blame the slow speeds on faulty Google equipment. IT experts later debunked the theory and confirmed the throttling was done on purpose with the help of two local ISPs. Several sources independently told Gazeta.ru that the Kremlin plans to fully block YouTube later this year in September. The slowdown and possible ban comes two weeks after a Russian government agency launched a YouTube clone named Платформа (Platforma) at the end of June. The Kremlin has constantly accused YouTube of hosting "terrorist" content since Russia invaded Ukraine. Russians regularly use YouTube to get unfiltered and non-propaganda news from outside the country.
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Rob King, Director of Security Research at runZero, about keeping up with the stream of vulnerabilities in the KEV list and OT devices and runZero's research into the SSH protocol.
Cybercrime and threat intel
Threat/trend reports: Gartner, Kaspersky, Sophos, and a two-part Trend Micro series have recently published reports covering infosec industry threats and trends.
New npm malware: Eighty-three malicious npm packages were discovered last week. Check out GitHub's security advisory portal for additional details.
Massive malvertising campaign: Malwarebytes has spotted a massive malvertising campaign abusing Google search ads to redirect users to websites hosting Windows apps infected with backdoor trojans such as WorkersDevBackdoor and MadMxShell. The same company also spotted a different malvertising campaign delivering the Atomic infostealer via Microsoft Teams for Mac.
Data destructive attacks: CERT-France has published a series of guides on how IT teams can deal with data-destructive attacks such as wipers and ransomware.
ClickFix campaign: McAfee has published a report on a new social engineering campaign that uses tech support scam sites to encourage users to run malicious PowerShell commands on their PCs. The commands are designed to download and install malware on targeted systems. The technique is named ClickFix because most of the tech support sites are advertising the PowerShell commands as a fix for various browser and PC issues.
Malware technical reports
Braodo Stealer: CyFirma researchers have spotted a new infostealer named Braodo Stealer. The malware launched in early 2024, is written in Python, and has been used in campaigns primarily targeting Vietnamese users.
DarkGate: Sonicwall has published a review of recent changes in the DarkGate malware loader.
TangleBot: Security researcher Cryptax has published an analysis of the TangleBot Android banking trojan, also known as BankBot and Medusa.
ShadowRoot ransomware: Forcepoint researchers have discovered a new ransomware strain named ShadowRoot that is currently used in attacks against Turkish businesses. An analysis seems to suggest this is an unsophisticated low-skill effort.
FishXProxy phishing kit: SlashNext has published a profile on FishXProxy, a new phishing kit advertised in the cybercrime underground.
Sponsor Section
Senior Sales Engineer Ali Cheikh demonstrates the runZero platform to Risky Business host Patrick Gray. runZero is a cyber asset management tool that combines active scanning, passive discovery, and API integrations to discover IT, OT, and IoT assets (both managed and unmanaged) across your network, including cloud, mobile, and remote environments.
APTs, cyber-espionage, and info-ops
Japan's APT attributions: Piyolog has compiled a list of all the seven times the Japanese government has publicly attributed hacks and APT activities.
Vulnerabilities, security research, and bug bounty
CosmicSting exploitation: Threat actors are hijacking online stores using a recently patched vulnerability known as CosmicSting. Security firm SanSec says attacks exploiting the bug began at the end of June and have now entered the phase of mass exploitation. The company says it's seeing between three and five stores getting hacked every hour, including major brands. The vulnerability was patched in early June and impacts roughly three-quarters of all Magento and Adobe Commerce stores. SanSec describes CosmicSting (CVE-2024-34102) as the worst bug to hit Magento and Adobe Commerce stores in the past two years.
Nette exploitation: SANS ISC reports active exploitation of a 2020 bug in the Nette PHP framework tracked as CVE-2020-15227. The attacker's payload was a Go-based malware strain.
Netgear patches: Netgear has released a firmware patch to fix an authentication bypass vulnerability in some of its cable modem routers.
Havoc C2 vulnerability: Security researcher Evan Ikeda has published details and a PoC for an unauth SSRF vulnerability in the Havoc C2 server, a toolkit commonly used by threat actors to host malware command and control servers.
Infosec industry
cDc 40th anniversary: The Cult of the Dead Cow (cDc), one of the earliest hacking groups, celebrated its 40th anniversary on July 11 last week.
Google-Wiz talks: The WSJ reports that Google, through its parent Alphabet company, is in talks to acquire cloud security firm Wiz for a whopping $23 billion.
OC3 2024 videos: Talks from the Open Confidential Computing 2024 security conference, which took place in March, are now available on YouTube.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about how bureaucracies should deal with outstandingly talented individuals.
In this podcast, Tom Uren and Patrick Gray talk about how South Korean internet regulations inadvertently encouraged a large ISP to hack their own customers to cut down on torrent traffic.
Abhishek Agrawal is the CEO and co-founder of Material Security, an email security company that locks down cloud email archives. Attackers have been raiding mailspools since hacking has existed, and with those mailspools now in the cloud with services like o365 and Google Workspace, guess where the attackers are going?




