Risky Biz News: Spyware vendors behind 24 zero-days last year
In other news: Hacker steals and then returns $62 million; US charges KuCoin and its founders with money laundering; Brutus botnet targets VPN servers.

This newsletter is brought to you by Sublime Security, an email security platform that's not a black box. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

Commercial spyware/surveillance vendors were behind 24 of the 97 zero-days that were exploited in the wild in 2023, according to a Google report published this week.
Eleven of the 24 zero-days impacted Safari and iOS, while the rest impacted Android and other Google products.
The data shows a clear interest from spyware vendors for mobile platforms. Google says it did not link any non-Apple or non-Google zero-days to spyware vendors.
Attribution was only possible for 58 of the 97 zero-days discovered last year. Spyware vendors and APT espionage groups each accounted for 24 zero-days, while financially-motivated groups (ransomware gangs, initial access brokers, etc.) accounted for the other 10.
Of these 10, Google linked three zero-days to FIN11, while another four were the work of four separate ransomware groups.
"Affiliates of the Nokoyawa ransomware reportedly exploited two separate zero-day vulnerabilities (CVE-2023-28252 and CVE-2023-23376), while affiliates of both Akira and LockBit ransomware reportedly separately exploited the same vulnerability as a zero-day (CVE-2023-20269). We also discovered the exploitation of an unpatched security bypass in Microsoft’s SmartScreen security feature (CVE-2023-24880), which financially motivated actors used to deliver the Magniber ransomware without any security warnings."
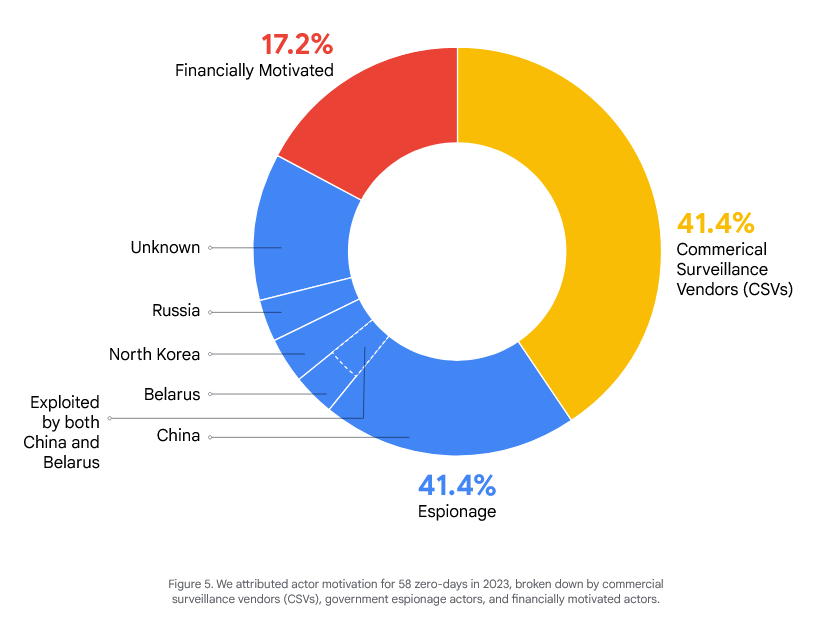
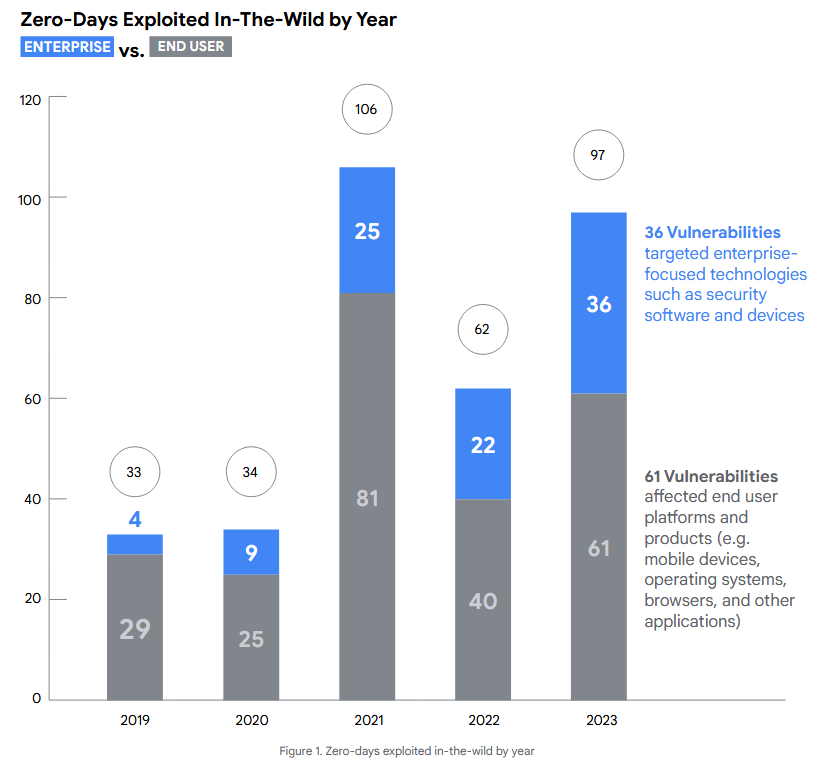
Google says that while the 97 zero-days spotted last year were a 50% jump from the year before, 2021 still holds the record with the most zero-days spotted abused in the wild with 106.
Even if attributed or not, the vast majority of zero-days last year impacted what Google described as end-user products—such as browsers, operating systems, mobile devices, and software apps. These accounted for 61, while the other 36 were zero-days in enterprise software and appliances.
The product targeted with the most zero-days last year was the Windows OS, with 17, followed by Safari at a distant 8. This was to be expected, as Windows has been on the top of zero-day charts for two decades now—a consequence of its immense popularity, both with end-users and enterprise environments.
Breaches, hacks, and security incidents
NHS Scotland ransomware attack: Scotland's national healthcare system has suffered a security breach after a ransomware gang encrypted some of the agency's IT systems. The incident has impacted the NHS board serving the Dumfries and Galloway region in South Scotland. The incident has not impacted patient care in the region. A ransomware group named INC Ransom has taken credit for the attack.
SolarWinds SEC backlash: The SEC is being criticized for "overreach" after reaching out to several telcos and tech companies about how they handled the SolarWinds 2020 hack. [Additional coverage in Bloomberg]
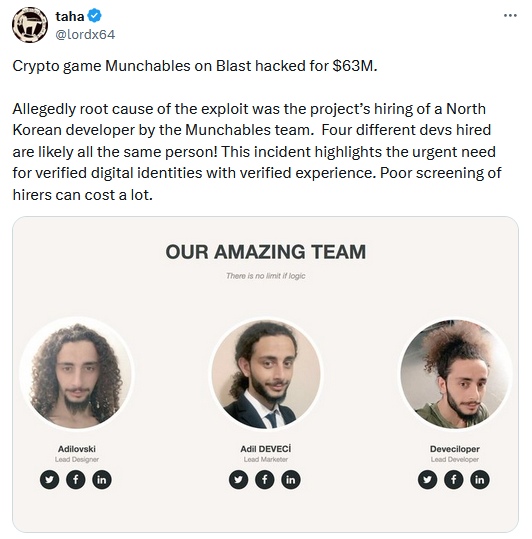
Munchables crypto-heist: A threat actor has stolen and then returned $62 million worth of tokens from crypto-gaming platform Munchables. Several blockchain security experts claimed the hack took place after Munchables had inadvertently hired a North Korean IT developer. The individual is believed to have stolen the platform's main private key and stolen the funds using a backdoor they planted in the code. It is currently unknown why the attacker returned the funds a day after the hack. [Additional coverage in CryptoSlate]
General tech and privacy
TeamCity change: JetBrains has rolled out a new TeamCity feature that will automatically download critical security updates.
"This approach helps to keep your system fortified against emerging risks and to swiftly tackle major vulnerabilities. Note that after an update is downloaded automatically, a system administrator still needs to approve its installation."
Redis clone: The Linux Foundation has announced a new open-source clone of the older Redis project—which has recently switched to a pay-to-play licensing scheme. The new project is named Valkey.
Government, politics, and policy
Russia's PSN clone: The Kremlin has given the green light to the creation of its own domestic gaming industry and gaming consoles. They also said they wanted a GitHub clone, and a report from a few days ago claims they never actually forwarded the money to build it. So, that Russian PSN/Xbox clone isn't coming any time soon. [Additional coverage in TASS]
Nepal NCSC: Nepal's government has moved to create a National Cyber Security Centre. [Additional coverage in The Annapurna Express]
France expects Olympics cyberattacks: The head of France's cybersecurity agency expects threat actors to target the Paris Olympics this year. ANSSI Director General Vincent Strubel says hackers might try to disrupt the opening ceremony and the city's public transport network. The official stopped short of accusing Russia. [Additional coverage in France24]
UK IPCO annual report: The UK's Investigatory Powers Commissioner Office has published its annual report for 2022. The report looks at how US law enforcement and intelligence have used their investigative powers. [Additional coverage in The Record]
"In 2022, there were 31 warrant applications to identify a journalistic source."
FCC seeking comment on telco security: The US Federal Communications Commission is asking for public comments on how telcos should approach securing the Signaling System 7 (SS7) and Diameter protocols. Both protocols have been abused over the past years to track users' locations through their mobile devices.
FTC yearly report: The FTC has published its yearly Privacy and Data Security Update report.
AI cybersecurity risks: The US Treasury Department has published a report on cybersecurity risks related to using AI in the fintech sector.
CIRCIA draft: CISA has published the first draft [PDF] of its upcoming Cyber Incident Reporting for Critical Infrastructure Act (CIRCIA). [Additional coverage in CyberScoop]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Josh Kamdjou, co-founder and CEO of Sublime Security. Josh describes how Sublime implemented the concept of attack surface reduction to email security last year, how it works, and what customers are saying about it.

Cybercrime and threat intel
US charges KuCoin: The US Justice Department has charged cryptocurrency exchange KuCoin and its two founders. US officials claim the company intentionally didn't run an anti-money laundering program. The DOJ says that since 2017, KuCoin received over $5 billion and transferred out over $4 billion of suspicious and criminal proceeds. Funds were allegedly linked to proceeds from darknet markets, malware, ransomware, and fraud schemes. The company's two founders are still at large.
"In fact, GAN, TANG, and KuCoin affirmatively attempted to conceal the existence of KuCoin's U.S. customers in order to make it appear as if KuCoin was exempt from U.S. AML and KYC requirements. Despite the fact that KuCoin gathered and tracked location information for its customers, KuCoin actively prevented its U.S. customers from identifying themselves as such when opening KuCoin accounts. And KuCoin lied to at least one investor, in 2022, about where its customers were located, falsely representing that it had no U.S. customers when, in truth, KuCoin had a substantial U.S. customer base. In fact, in a number of social media posts, KuCoin actively marketed itself to U.S. customers as an exchange where they could trade without having to undergo KYC. For example, KuCoin stated in an April 2022 message on Twitter that 'KYC is not supported to USA users, however, it is not mandatory on KuCoin to do KYC. Usual transactions can be done using an unverified account'."
SBF sentencing: FTX's Samuel Bankman-Fried was sentenced to 25 years in prison, three years of supervised release, and ordered to pay $11 billion in forfeiture for his orchestration of multiple fraudulent schemes.
BEC scammer gets 12 years: A US judge has sentenced a Cameroonian national to 12 years in prison for his role in BEC scams. Officials say Njuh Valentine Fombe stole more than $2 million through BEC scams between 2016 and 2018. Fombe fled to the UK in 2019 after he was indicted where he allegedly engaged in pandemic-related unemployment scams.
Jumbotron hacker sentenced: The US has sentenced a Florida man to 220 years in prison for CSAM-related crimes and for hacking the Jumbotron of the Jacksonville Jaguars NFL team.
"Before the expiration of Thompson’s contract in March 2018, Thompson installed remote access software on a spare server in the Jaguars’ server room. Thompson then remotely accessed computers that controlled the Jumbotron during three 2018 season NFL games, causing the video boards to repeatedly malfunction. After conducting an investigation, the Jaguars determined that the outages were being caused by a malicious actor sending commands via the spare server. On December 16, 2018, the Jaguars set up a “honeypot” by putting the server on its own network and removing its access to the other computers that controlled the Jumbotron. During the next NFL game, the spare server was again remotely accessed and attempted to be used to send commands to computers controlling the Jumbotron. The Jaguars were able to capture the Internet Protocol (IP) address of the intruder – which the Federal Bureau of Investigation traced to Thompson’s residence."
FCC bans BPO Innovate: The FCC banned BPO Innovate and ordered US telcos to stop accepting the company's mobile traffic after BPO failed to implement anti-robocall mitigations.
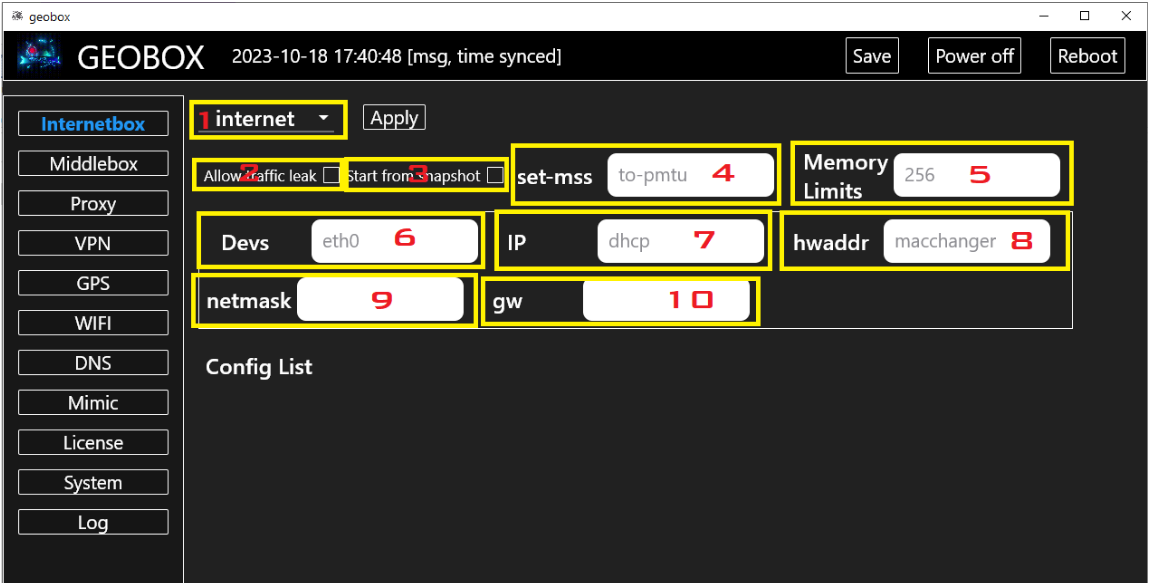
GEOBOX software: Threat actors are selling custom-made software that can transform Raspberry Pi devices into an anonymization tool for cybercrime operations. The tool is named GEOBOX and is being advertised on Telegram for $700. GEOBOX can turn Raspberry Pi devices into no-log proxies that can spoof any GPS location and WiFi network. Security firm Resecurity says it has encountered GEOBOX in an attack at a Fortune 100 financial institution.
"The malicious individuals utilized several GEOBOX devices, each connected to the Internet and strategically placed in various remote locations. These devices served as proxies, significantly enhancing their anonymity. This approach complicated the investigation and tracking process, especially since, by default, GEOBOX devices do not store any logs."
Darcula PhaaS: Netcraft security researchers have linked more than 20,000 phishing sites to a new Phishing-as-a-Service platform named Darcula. The platform launched this year and is advertised to Chinese-speaking hackers. Darcula is also one of the first phishing platforms to incorporate support for RCS messages instead of SMS, allowing phishing messages to bypass SMS firewalls.
RPT Company investigation: A joint Qurium and LeMonde investigation has linked a vast network of sites impersonating legitimate news sites that were driving traffic to cryptocurrency and other investment scams. Investigators say they linked the network to RPT Company, a Russian affiliate marketing organization run by Leonid Belov and Yakov Rutman.
DVE threats: Recorded Future has published a report on how US domestic violent extremists (DVEs) operate. The report covers how extremists are doxing senior leaders in government organizations and private companies in order to encourage violence and harassment.
MEV bot hacks: Scammy MEV bots have stolen $1.69 million worth of crypto assets from users in the first two months of the year, per ScamSniffer.
Brutus attacks: A new botnet named Brutus is behind a wave of brute-force attacks that have hit VPN appliances across the world. According to security researcher Aaron Martin, attacks began on March 15. The brute-force activity is indiscriminate and targets VPN servers from many vendors, such as Cisco, Fortinet, and Sonicwall. Martin says Brutus launches tens of millions of brute-force requests per day. Recent attacks are now also targeting web apps that use Active Directory for authentication.
PyPI malware upload campaign: The Python Software Foundation temporarily suspended new project creation and new user registration on the PyPI platform. PyPI admins said they suspended the platform to mitigate a malware upload campaign. Access to the platform was restored after ten hours.
Malicious Google ads: Google has blocked or removed more than 5.5 billion ads and 12.7 million advertiser accounts for violating its policies in 2023. The company says that 90% of the takedowns started from its machine learning and AI systems. Almost a fifth of the blocked ads promoted malware.
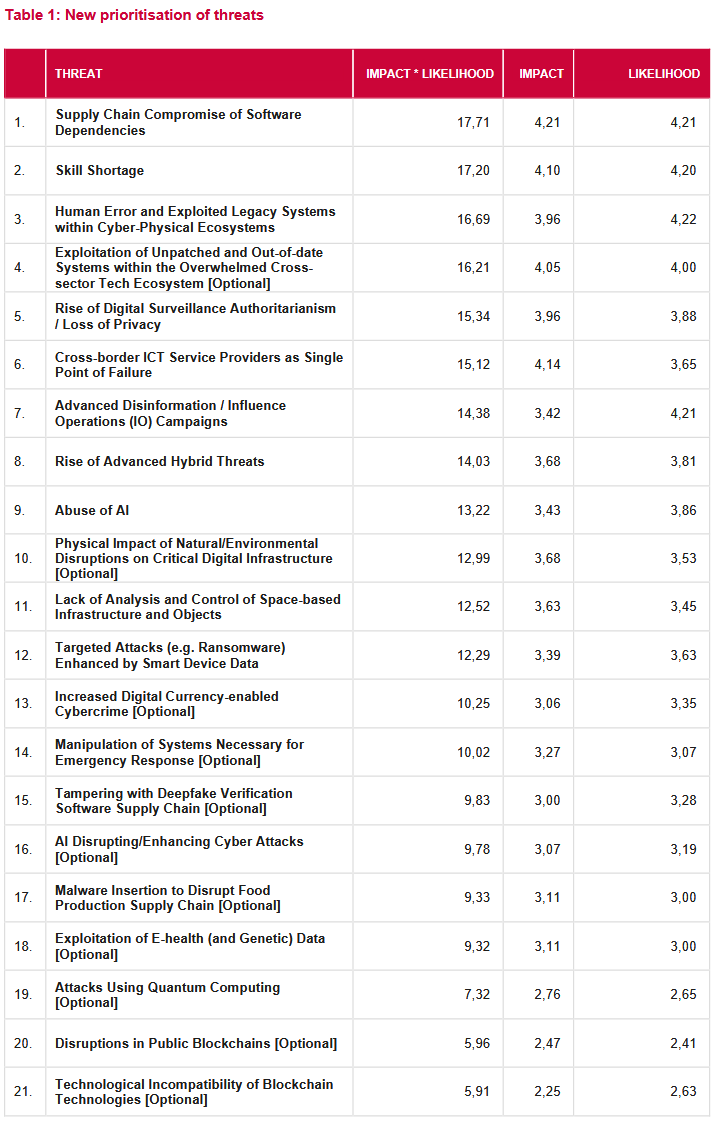
Threat/trend reports: ENISA, Flashpoint, and Positive Technologies have recently published reports covering infosec industry threats and trends. The most interesting of the reports is the one from ENISA, which ranked supply chain attacks as the top emerging cybersecurity threat for the next half-decade. The other area of concern is the cybersecurity workforce skill shortage, which moved from number ten to number two. New on the agency's Top 10 list is the exploitation of unpatched systems, which entered the top at number four directly.
Malware technical reports
BunnyLoader: ANY.RUN has published an analysis of the BunnyLoader v3. A report on the same malware is also available via PAN Unit42.
Sync-Scheduler: CyFirma looks at Sync-Scheduler, a new infostealer written in C++ that the company spotted in the wild.
New Go trojan: Sonicwall's Capture Labs have published an analysis of a new remote access trojan written in the Go programming language that they have spotted in the wild.
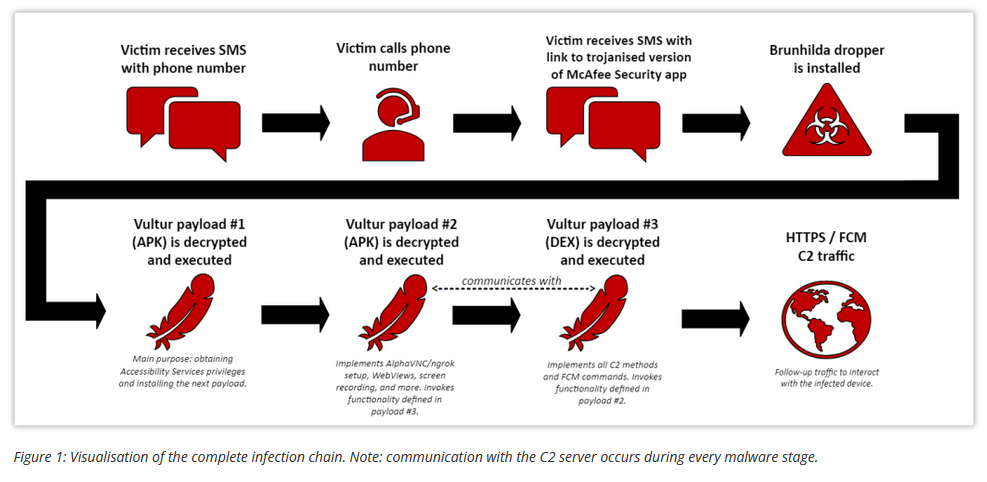
Vultur: Fox-IT looks at the recent changes in Vultur, an Android banking trojan that launched operations in March 2021.
Sponsor Section
The latest evolution of PikaBot is using phishing to gain initial access. Learn why it's been effective and how to protect your organization from novel email attacks. Read the full post.
APTs, cyber-espionage, and info-ops
ASEAN APT attacks: PAN Unit42 has published a report on two Chinese APT attacks on Southeast Asia. The report covers Stately Taurus and a yet-to-be-named group.
Operation FlightNight: EclecticIQ has identified a new threat actor targeting Indian government entities and organizations in its energy sector. The attacker is using a modified version of the open-source infostealer HackBrowserData to steal and send data to remote Slack channels. EclecticIQ has notified Indian authorities about multiple successful intrusions. Researchers named the campaign "Operation FlightNight" after one of the attacker's Slack channels.
DinodasRAT: Kaspersky looks at DinodasRAT, a backdoor also known as XDealer, used in Operation Jacana, a cyber-espionage campaign that targeted the Guyana government. ESET previously attributed the attacks to a Chinese threat actor.
APT37's RokRAT: South Korean security firm Genians has published a report covering the fileless version of the RokRAT, a backdoor used in attacks by North Korean group APT37 (Reaper).
Kosovo's cyber-bully army: BlakanInsight looks at how the Kosovo government uses internet trolls to cyber-bully its critics—a tactic also widely used by more and more (klepto-friendly) governments these days.
China lulz: Last month, SentinelOne published a report describing how China has been failing to attribute cyber-attacks to the US by constantly referencing old incidents. Chinese security firm Antiy has responded to SentinelOne's report by... drum roll... referencing Stuxnet and a bunch of old reports.
Russian propaganda network busted: Czech intelligence services have disrupted a Russian propaganda network operating in Prague. The network operated a news website named the Voice of Europe. Officials say the website was registered to a local company but was financed from Russia. It published opinions from EU politicians who were demanding that the EU stop financing Ukraine. According to local news outlet Denik N, some of the politicians were paid using funds from Russia. The Czech government sanctioned the Voice of Europe and two of its administrators. One of them is former Ukrainian politician Viktor Medvedchuk. Czech officials claim Medvedchuk ran the entire operation from Moscow. [Additional coverage in Denik N]
Prigozhin troll farms: This was initially covered by an NYT report a few weeks back, but Mandiant has also published a report on how Prigozhin's troll farms have survived the oligarch's assassination. It's like he never left, and the Patriot Group of fake news outlets is still going strong and pushing propaganda all over Africa, Europe, and the US.
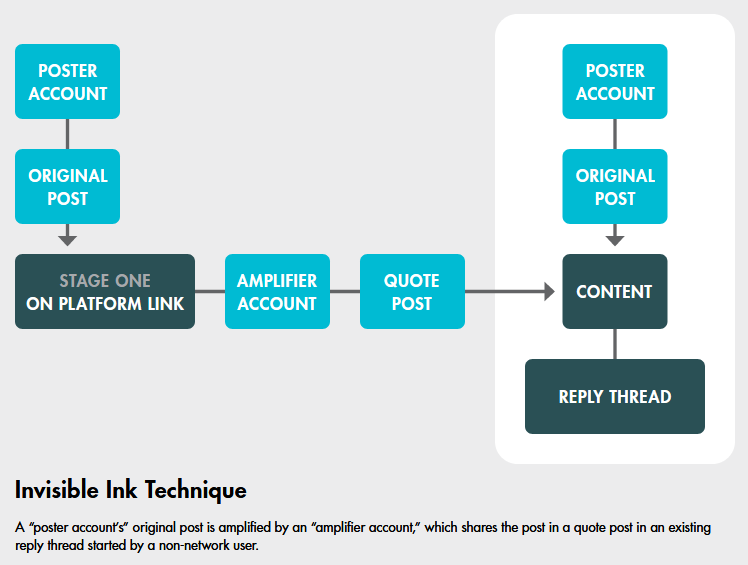
Invisible Ink: And speaking of Russian disinformation, Alethea looks at the recent tactics of the Doppelgänger group—Operation Invisible Ink. It's a bunch of fake news sites and Twitter accounts operated by GRU operatives and designed to interfere in foreign elections.
"The network demonstrates a shift in Russian objectives as it relates to the elections. To date in the United States, the Russian objective was to sow chaos. Now, the objective is to support candidates and amplify issues that reduce support for Ukraine. Russia is spreading multiple messages to amplify narratives in the United States that create false dichotomies on domestic issues like border security, inflation, unemployment, and general criticism of the Biden Administration."
Vulnerabilities, security research, and bug bounty
MS Edge vulnerability analysis: Guardio Labs has published a write-up on a vulnerability (CVE-2024–21388) it discovered in Microsoft's Edge web browser.
"This flaw could have allowed an attacker to exploit a private API, initially intended for marketing purposes, to covertly install additional browser extensions with broad permissions without the user's knowledge. Promptly after our discovery, we fully disclosed the issue to Microsoft, leading to a resolution in February 2024."
nf_tables vulnerability analysis: PwningTech has published a write-up on CVE-2024-1086, a use-after-free vulnerability in the Linux kernel's netfilter.
io_uring vulnerability analysis: Exodus Intelligence has published a write-up on CVE-2024-0582, a use-after-free vulnerability in the Linux kernel discovered by Google Project Zero researchers earlier this year.
Grafana vulnerability analysis: Palo Alto Networks has published a write-up covering CVE-2024-1313, a Broken Object Level Authorization (BOLA) vulnerability the company discovered in Grafana.
ColdFusion vulnerability analysis: Security researcher Ma4ter has published a write-up covering CVE-2024-20767, an arbitrary file system read vulnerability in Adobe ColdFusion. Ma4ter published the write-up and a PoC after Adobe patched the bug earlier this month.
SharePoint vulnerability analysis: Security researcher Jang has published a write-up on CVE-2023-38177, a SharePoint RCE that Microsoft patched last November.
KEV update: CISA has updated its KEV database with four (one+three) vulnerabilities that are currently exploited in the wild. These include bugs in SharePoint, Fortinet, Ivanti, and Nice Linear.
Telerik RCE: Progress Software has patched a critical vulnerability in Telerik Report Server, a centralized data reporting platform. The vulnerability (CVE-2024-1800) allows remote code execution attacks through an insecure deserialization vulnerability. According to Censys, more than 100 Telerik Report Servers have their login pages exposed on the internet.
WallEscape vulnerability: Security researcher Skyler Ferrante has discovered a vulnerability in Wall, a Linux utility to display a message on the terminals of all logged-in users. The vulnerability allows unprivileged users to put malicious text on other users' terminals. The vulnerability can be used to prompt and collect user passwords or alter clipboard data. Ferrante says all Wall versions released over the past 11 years are vulnerable. He named the vulnerability WallEscape (CVE-2024-28085). Proof of concept is available on GitHub.
Cisco security updates: Cisco has released or updated 17 security advisories for various products.
Privacy Sandbox security audit: The NCC Group has conducted a security audit of the Aggregation Service, a core component of Google's new Privacy Sandbox Chrome component.
"NCC Group did not identify any flaws in the design of Privacy Sandbox Aggregation Service. It appears to satisfy industry best practices and provide strong protections for the confidentiality and integrity of data collected from end users."
CVEs in EoL software: According to recent Chainguard research, EOL software accumulates—on average—218 CVEs every six months.
"98.4% of the vulnerabilities accumulate within image components, 1.4% in the application dependencies, and only 0.2% of vulnerability accumulation every six months are directly within the application."
Infosec industry
New tool—Jigsaw: Security firm RedSiege has open-sourced a new shellcode obfuscation tool named Jigsaw. It works by hiding shellcode by shuffling bytes into a random array and reconstructing it at runtime.
New tool—SharpConflux: Security firm Nettitude has open-sourced a tool named SharpConflux that can help red-team explore attacks against Atlassian Confluence servers.
New tool—HL7Magic: Security firm WithSecure has open-sourced a tool named HL7Magic, a tool for pen-testing devices using the Health Level Seven (HL7) medical protocol. The tool is a Burp extension for converting HL7 messages to JSON readable format, enabling MitM relays.
Tool update—drozer: After seven years, WithSecure has released a new version of the drozer security testing framework for Android.
RWC 2024 slides: Slides from the Real World Crypto 2024 security conference, which took place last week, are available on the conference's site.
New Mandiant home: As part of its Google acquisition, Mandiant's blog has a new home. Update your RSS feeds!
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at Russia's recent leak of an intercepted German military discussion. From an intelligence point of view, the content of the discussion is only moderately interesting, but Russia decided to leak it in an attempt to influence European attitudes towards providing military aid to Ukraine.




