Risky Biz News: Sparks fly when lawyers meet a certificate revocation
In other news: Shareholders sue CrowdStrike over IT outage; Greece absolves itself from PredatorGate scandal; two cyber-criminals included in major US-Russian prisoner swap.

This newsletter is brought to you by no-code automation platform Tines. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

An emergency certificate revocation initiated by DigiCert earlier this week has met a brick wall after the company got sued by one of its customers and several critical infrastructure operators raised safety concerns.
DigiCert initiated the certificate revocation on Monday as part of the normal procedures and agreements between Certificate Authorities (CAs) and browser and OS makers like Microsoft, Apple, Google, and Mozilla.
According to rules established by the CA/B Forum, DigiCert is mandated to revoke any certificates it issued through invalid procedures.
In this case, the company found that almost 85,000 TLS certificates (~0.4% of all DigiCert certs) were issued while a bug was present on its platform.
The bug impacted DigiCert customers who bought a TLS certificate and decided to validate their identity by adding a CNAME entry in their domain DNS records.
DigiCert usually generates a random string and gives it to customers to add as a DNS CNAME subdomain entry. Typically, to avoid conflicts with existing subdomains, the string is prefixed by an underscore "_" character.
DigiCert said the problem was that for a period of time, its platform failed to include this prefix. Even if the customers successfully proved their identity, and it's very unlikely this was abused in any way, this broke CA/B Forum rules.
In the past several CAs ignored trivial safety incidents like this. Variations of trivial verification procedures like this have happened before, especially where the chances of something like this getting exploited are incredibly small.
However, the bug came just as Google lowered the ban hammer on two CAs over the past few weeks. In the span of a month, Google removed trust from two major certificate providers, GlobalTrust and Entrust.
In what was very likely a move designed not to enrage Google's security team, DigiCert decided to bite the bullet and revoke all the certificates it issued while the bug was active on its platform.
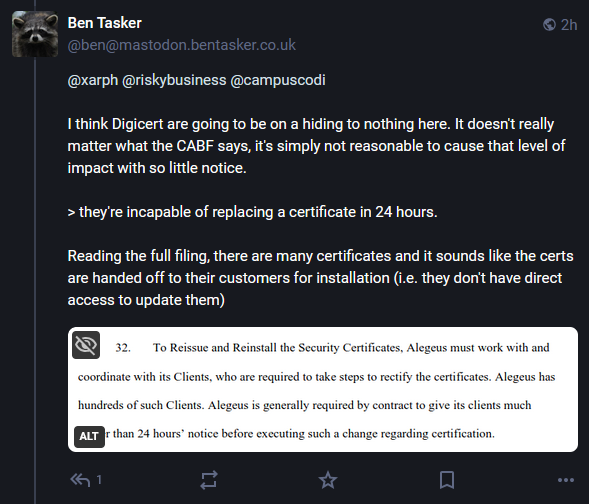
This process involved revoking trust in all the older certificates and issuing new ones to all affected customers. All of this needed to be done in 24 hours, which was by Wednesday, July 31, 2024, 19:30 UTC.
DigiCert says the process was going great for the most part until it began hearing from the operators of critical services, where certificates couldn't be replaced due to strict maintenance and uptime requirements.
Things escalated to a whole new level when one of DigiCert's customers—US healthcare payments processor Alegeus Technologies—sued the company and obtained a temporary restraining order preventing DigiCert from revoking its cert.
Following the lawsuit and the pushback, DigiCert says it contacted browser makers and, based on the feedback from critical service operators, has now decided to loosen the rules and allow some companies to still operate certificates until Saturday, August 3.
Except Alegeus, which will be allowed to use its certificate until a court hearing is set next week where lawyers will duke it out.
Regardless of how this plays out in court, there are some real lessons to be learned here by the CA/B Forum about emergency 24-hour certificate revocations—namely, that special rules and deadlines need to be made available for critical infrastructure operators. It's one thing to revoke a school's TLS certificate, it's another thing to revoke the certificate of a 911 call center's dashboard or an emergency reporting backend used by the water sector.
[h/t Xarph]
Breaches, hacks, and security incidents
Terra crypto-heist: The Terra blockchain lost $6.8 million worth of crypto-assets in a security breach this week. The platform says the attacker exploited a vulnerability in the mechanism that interconnects with other blockchains. Terra has suspended operations to patch the exploited issue. [Additional coverage in Coinpedia]
Fresnillo hack: The world's largest silver producer says it's been hit by a cyberattack. Mexico's Fresnillo says it detected unauthorized access to certain IT systems and its data. The company says it's investigating the incident and that there's no impact on its mines. Fresnillo is the world's largest silver producer, with an output of 1,600 tons per year.
Ransomware attack impacts US blood donation centers: A ransomware attack has crippled the operations of OneBlood, a blood donation non-profit serving the Southeastern US. OneBlood says it's operating at a reduced capacity after the attack crippled some of its IT systems. The non-profit says it asked the more than 250 US hospitals to activate critical blood shortage protocols as it works to restore its blood donation centers.
Ransomware attack impacts Indian banks: A ransomware attack on a small Indian software company is disrupting the activities of more than 300 Indian regional and cooperative banks. The incident has hit C-Edge Technologies, a company that makes financial software. The attack is preventing banks from making payments via four different payment methods (UPI, IMPS, NEFT, RTGS). The Indian National Payments Corporation of India has temporarily blocked C-Edge's software from interacting with the rest of the Indian retail payment system. The attack was allegedly the work of the RansomEXX group. [h/t Ravi Nayyar] [Additional coverage in Techlusive]
Azure suffers a major DDoS attack: Multiple Azure services went down this week following a DDoS attack. The incident lasted for eight hours and impacted some of Microsoft's largest services, including the Microsoft 365 platform. The company says the incident was actually made worse by its DDoS mitigation service. Microsoft says a Front Door error amplified the attacks instead of blocking the malicious traffic.
General tech and privacy
Entrust survives: After Google announced it was distrusting Entrust certificates inside Chrome later this year, the CA announced a partnership with SSL.com to continue issuing TLS certs for its customers.
Booking.com fined in Spain: Spain's data protection agency has fined Booking.com $413 million for abusing its dominant market position and imposing unfair conditions on Spanish hotels, restricting them from working with local travel agencies.
Shareholders sue CrowdStrike: Shareholders have filed a lawsuit against security firm CrowdStrike over a recent IT outage that impacted countries all over the world. The outage was caused by an update to the company's Windows EDR kernel driver that contained a bug and was not properly tested. In a class-action lawsuit filed in Texas this week, shareholders accused the company of concealing inadequate software testing practices. The lawsuit claims the company previously described its software as "validated, tested, and certified." [Additional coverage in Reuters]
Normal people hate AI: A recent study found that consumers are turned away by products that use AI features. I'm surprised none of these big-brain companies did this very basic market research before adding AI to literally everything these days.
curl supply-chain protections: The curl project has published a list of defenses it uses to protect its code from backdoors and supply-chain attacks.
Swift adds support for homomorphic encryption: The Swift programming language has added support for homomorphic encryption. Homomorphic encryption is a cryptographic technique that enables computation on encrypted data without decrypting or revealing the underlying data. Swift is a programming language developed at Apple and widely used for its iOS and macOS operating systems.
Mozilla distrusts Entrust: Mozilla has announced plans to distrust certificates issued by Entrust after November 30, this year. Google previously announced a similar decision for distrusting any new Entrust certificate issued after October 31.
Government, politics, and policy
KOSA passes Senate: The US Senate has passed the Kids Online Safety Act (KOSA) with an overwhelming 91–3 vote despite criticism from privacy advocates. [Additional coverage in ArsTechnica]
CISA & FBI DDoS warning: Both CISA [PDF] and the FBI have published public service announcements warning that foreign actors may try to use DDoS attacks to block access to election information but they will not be able to impact the voting process itself.
CyberCom AI Task Force: US CyberCom's new AI task force will be included in the agency's elite cyber unit, the Cyber National Mission Force (CNMF). [Additional coverage in DefenseScoop]
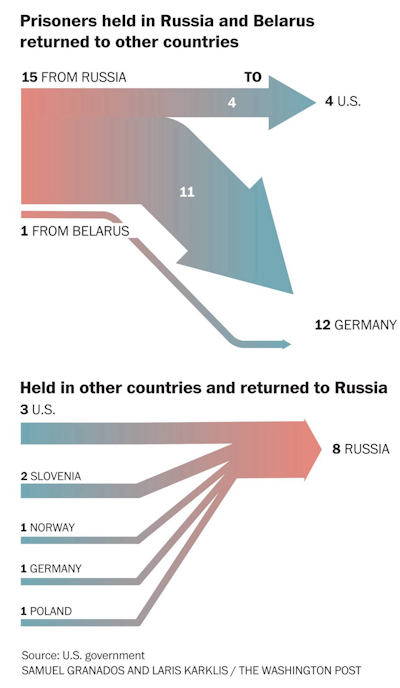
Cybercriminals exchanged in prisoner swap: Two Russian cybercriminals held in the US have been sent back home in a massive prisoner swap that freed Wall Street Journal reporter Evan Gershkovich and former US Marine Paul Whelan. A White House spokesperson confirmed that as part of the deal, the US released convicted Russian cybercriminals Roman Seleznev and Vladislav Klyushin. Seleznev was being held on a 27-year prison sentence for running the Carder.su carding forum. Klyushin was being held on a 9-year prison sentence for using hacked data for insider trading. The prisoner swap involved 24 individuals held in seven countries and also saw the release of several Russian opposition political figures. [Additional coverage in CyberScoop]
North Korea's cyber force: South Korea's intelligence agency estimates that around 8,400 hackers are currently part of North Korea's cyber force. The number is up from 1,700 recorded in 2015. Officials say these units are involved in both cyber warfare and cybercrime operations. [Additional coverage in Donga]
China prepares digital ID system: China's internet watchdog is working on a new regulation that will assign a digital identifier to each Chinese citizen using the internet. The new system would link a person's real identity to a unique ID to be used when registering for online platforms. Beijing officials say the new system is designed to prevent online fraud and the ability of private companies to track user behavior, since users will not have to share any of their personal data with online platforms going forward. Critics say the new system allows the government easier ways to track users online. [Additional coverage in FT]
Germany summons Chinese ambassador over hack: Germany has formally blamed the Chinese government for hacking its national office for cartography (BKG) in a 2021 cyberattack. The German government has summoned the Chinese ambassador for the first time since the Tiananmen Square massacre. In typical Beijing fashion, the Chinese embassy in Germany called the accusation as "targeted defamation." This marks the second time an ambassador is summoned because of a cyberattack. The British government also summoned the Russian ambassador last December after the FSB's cyber units hacked members of Parliament.
Romanian government meets with social media giants: Representatives from the Romanian government are holding meetings with Meta, TikTok, and Google after the country has seen several waves of deepfakes promoting various fraudulent schemes. The government says Romania is in the Top 3 EU countries targeted by online scams. [Additional coverage in HotNews]
Pakistan now has a "national firewall": Pakistan has joined the list of countries with a national firewall. We learned this because they misconfigured it and some traffic into a black hole for a few hours.
Greek government absolves itself: In a shocking decision this week, Greece's Supreme Court has ruled that there is no evidence that the country's government agencies were involved in the PredatorGate spying scandal. The decision comes in a two-year-old case where the ruling government was accused of spying on tens of opposition leaders and journalists. The case was also investigated by the EU's PEGA commission, which named Greece one of the worst spyware offenders in the EU. The Supreme Court's decision has dismissed charges against government officials but has left the door open for the prosecution of individuals tied to the spyware. The decision comes contrary to tens of reports from local journalists that exposed the hacks, exact targets, and even ties between the government and the spyware maker. Opposition leaders called the Supreme Court's decision a stain on the country's justice system. [Additional coverage in BalkanInsight]
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Thomas Kinsella, co-founder and Chief Customer Officer of Tines, about figuring out what AI is really good for and taking advantage of it in automating workflows.

Cybercrime and threat intel
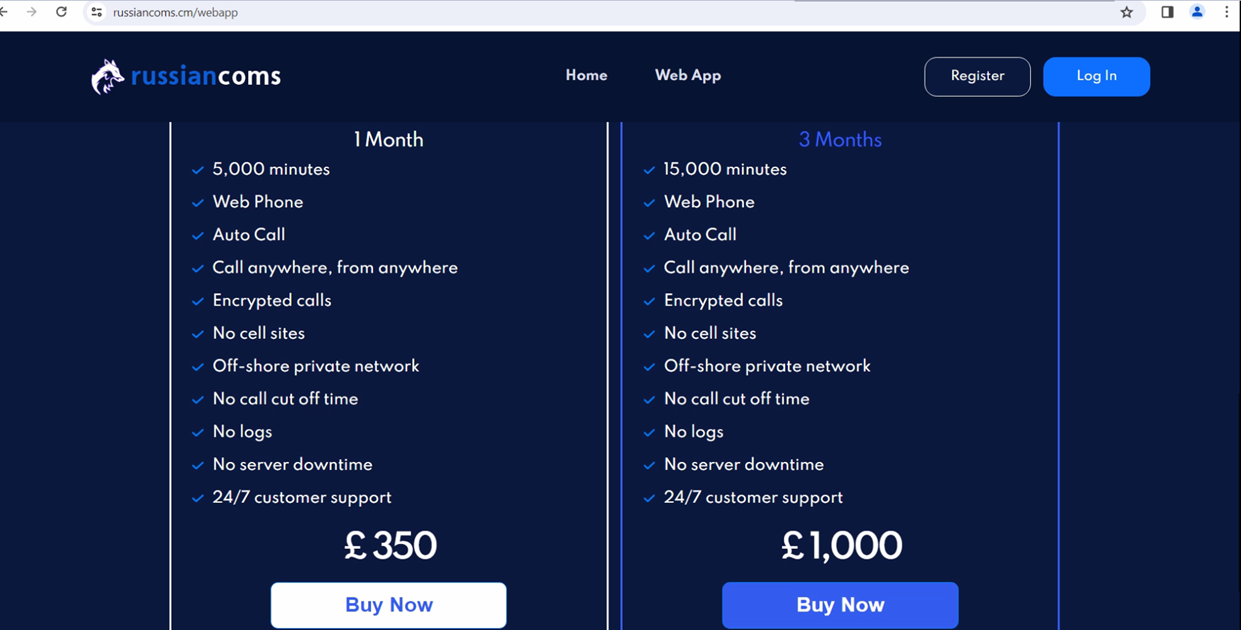
UK takes down Russian Coms platform: UK authorities have shut down an online platform that was used by hundreds of cybercriminals to defraud victims around the world. Named Russian Coms, the platform launched in 2021 and allowed threat actors to spoof phone numbers. Cybercrime groups used the service to pose as banks, tech companies, and law enforcement and request payments from their targets. UK police have detained three suspects, including two of the site's administrators.
Bloody Wolf: Russian security firm BI.ZONE has published a report on Bloody Wolf, a financially motivated cybercrime group it saw targeting commercial entities in Kazakhstan. The final payload was STRRAT, a commercial RAT also known as Strigoi Master.
Rilide tied to SYS01: Trustwave says it found evidence to tie the developer of the Rilide infostealer to the SYS01 infostealer, itself an offshoot of the older Ov3r_Stealer.
Malicious PyPI package: Fortinet researchers have found a malicious Python library uploaded on the PyPI portal. The package installs a basic infostealer for data collection.
StackExchange PyPI campaign: A threat actor is using StackExchange comments to redirect developers to malicious Python packages. The libraries are designed to infect the victim's device and steal funds from their cryptocurrency wallet. They will also steal browser passwords and data from encrypted instant messengers. According to Checkmarx, the packages targeted developers interested in the Raydium and Solana blockchains.
FBI scam warning: The FBI has sent out a new alert warning that scammers are impersonating cryptocurrency exchanges and their employees in schemes to steal a victim's funds.
ERIAKOS scam campaign: Recorded Future has discovered a network of 608 e-commerce stores impersonating major brands. The sites were part of a major Facebook malvertising campaign that redirected users to the sites in order to collect their payment details. Researchers named the group behind the network ERIAKOS after the name of the CDN service they used to host the sites.
Cloudflare Tunnel abuse: Proofpoint has published a report looking at how threat actors are abusing the TryCloudflare service to create one-time (demo) tunnels as part of their malware operations.
Spamhaus criticizes Cloudflare: Spamhaus says that 1,200 malicious sites are using Cloudflare to shield their services. The number represents 10% of Spamhaus' blocklist. In a blog post this week, Spamhaus has added its name to a long list of security experts who have criticized Cloudflare for closing its eyes to all the cybercrime sites being hosted on its service.
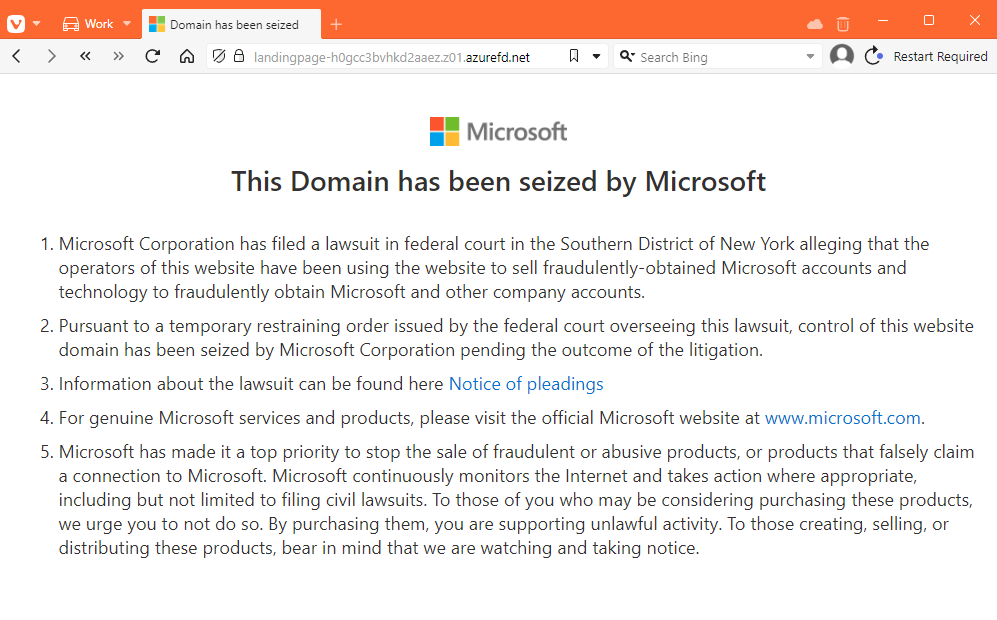
Microsoft seizes Storm-1152 domains: Microsoft has seized a new domain operated by a Vietnamese cybercrime group named Storm-1152. The domain hosted a service designed to bypass CAPTCHA services. The seizure is Microsoft's second legal action against the group. Redmond lawyers previously seized domains and servers from the group in December of last year. Microsoft says Storm-1152 created and sold access to more than 750 million Microsoft accounts. [Additional coverage in CyberScoop]
Malware technical reports
Black Basta: Infoblox has a novel look at the DNS traffic typically generated by a Black Basta attack.
BingoMod: Security firm Cleafy has discovered a new Android malware that is being used to infect devices and steal funds from victims' accounts. Named BingoMod, the malware also contains a feature to wipe an infected device. Cleafy says attackers are using the feature to wipe devices after stealing funds. This keeps victims focusing on fixing their devices instead of looking at their bank accounts. According to the comments identified within the malware code, Cleaby believes the malware was developed by Romanian speakers.
CraxsRAT: Group-IB analyzes CraxsRAT, an Android remote access trojan used in campaigns targeting Malaysian users.
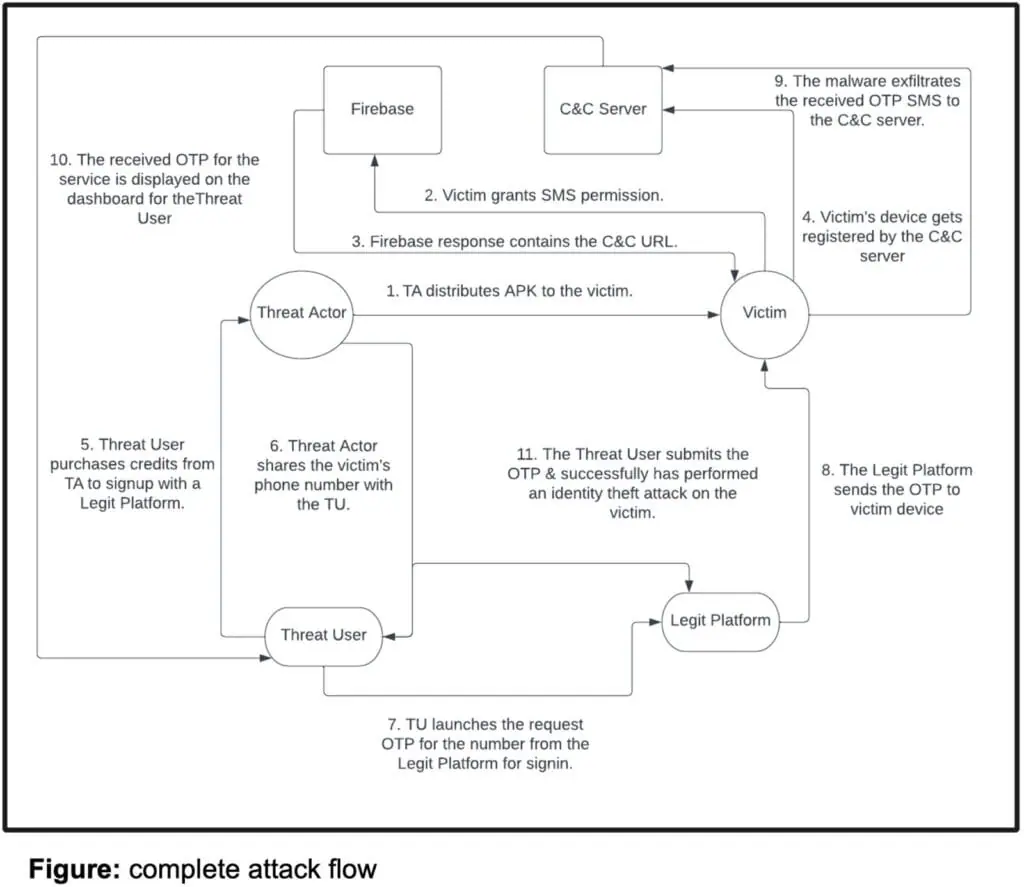
SMS stealer trojan: Security firm Zimperium has discovered a stealthy malware operation that has been infecting Android devices since February 2022. The malware was unsophisticated, and its primary feature was to intercept incoming SMS messages. Researchers believe the malware's main purpose was to infect devices and then abuse their phone numbers as a way to sign up for online services and bypass 2FA and OTP verifications. Zimperium says it found traces of the malware on devices located in 113 countries. Most of the infections were located in Russia and India.
Facebook malvertising epidemic: Trustwave has published part two of a report covering a massive malvertising campaign abusing Facebook ads to deliver the SYS01 infostealer. Part one is here.
DeerStealer: Malvertising is everywhere these days, and the latest campaign abusing Google Ads was spotted by ANY.RUN and Malwarebytes. Ironically, this one used a clone of Google's own Authenticator app to trick users into infecting themselves with the DeerStealer malware.
NetSupport RAT: Cisco Talos looks at several NetSupport RAT campaigns active in the wild.
BITSLOTH: Elastic's security team has published a technical analysis of BITSLOTH, a new Windows backdoor spotted in LATAM. The malware stands out from the rest because of its use of the Background Intelligent Transfer Service (BITS) as a command-and-control mechanism. The company attributed the backdoor to a group it tracks as REF8747. Based on code artifacts, the malware appears to have been written by Chinese-speaking individuals.
GhostHook: iVerify has published a report on GhostHook, a framework used by cybercrime groups for sending malicious push notifications to "enslaved" browsers and mobile devices.
Sponsor Section
In this demo, Tines CEO and co-founder Eoin Hinchy demonstrates the Tines no-code automation platform to RiskyBiz host Patrick Gray.
APTs, cyber-espionage, and info-ops
DEV#POPPER: Securonix has published more details on DEV#POPPER, a North Korean espionage operation targeting software developers with fake job interviews. The report is a continuation of a previous article from April.
APT41: Cisco Talos says that Chinese cyber-espionage group APT41 has compromised a Taiwanese government-affiliated research institute since at least July 2023. The attack exploited an outdated version of Microsoft Office to deploy the ShadowPad backdoor on the institution's network. The attack focused on information gathering and exfiltration.
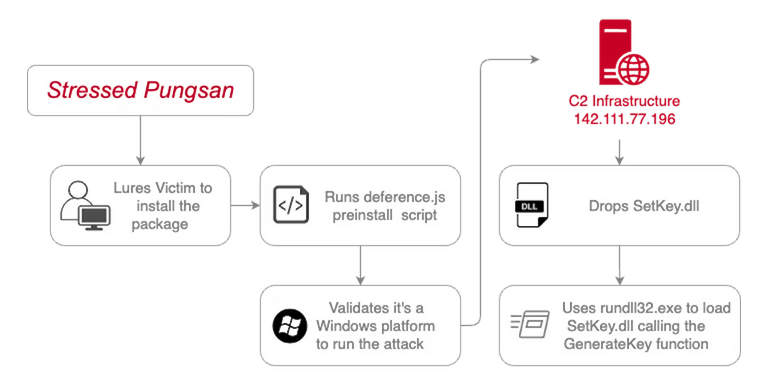
Stressed Pungsan: A North Korean hacking group has uploaded two malicious packages in early July on the official npm portal. According to the Datadog security team, the packages were designed to download additional Windows malware from a remote server. The company linked the attacks to a group it tracks as Stressed Pungsan. The group overlaps with what Microsoft tracks as Moonstone Sleet.
Vulnerabilities, security research, and bug bounty
OpenSSL bug: Back in June, the OpenSSL project fixed an 11-year-old bug, CVE-2024-5535, that could have been used to leak server memory.
Windows AppLocker EoP: Crowdfense has published an analysis of CVE-2024-21338, a Windows AppLocker Driver LPE vulnerability patched back in February.
FlowFixation vulnerability: SecureLayer7 has published a technical report on CVE-2024-39877, an Apache Airflow RCE, also known as FlowFixation.
Coinbase $500k payout: According to Coinbase's bug bounty page, the company appears to have handed out a $500,000 bounty to blockchain security firm CertiK. Details of the bug are still unknown.
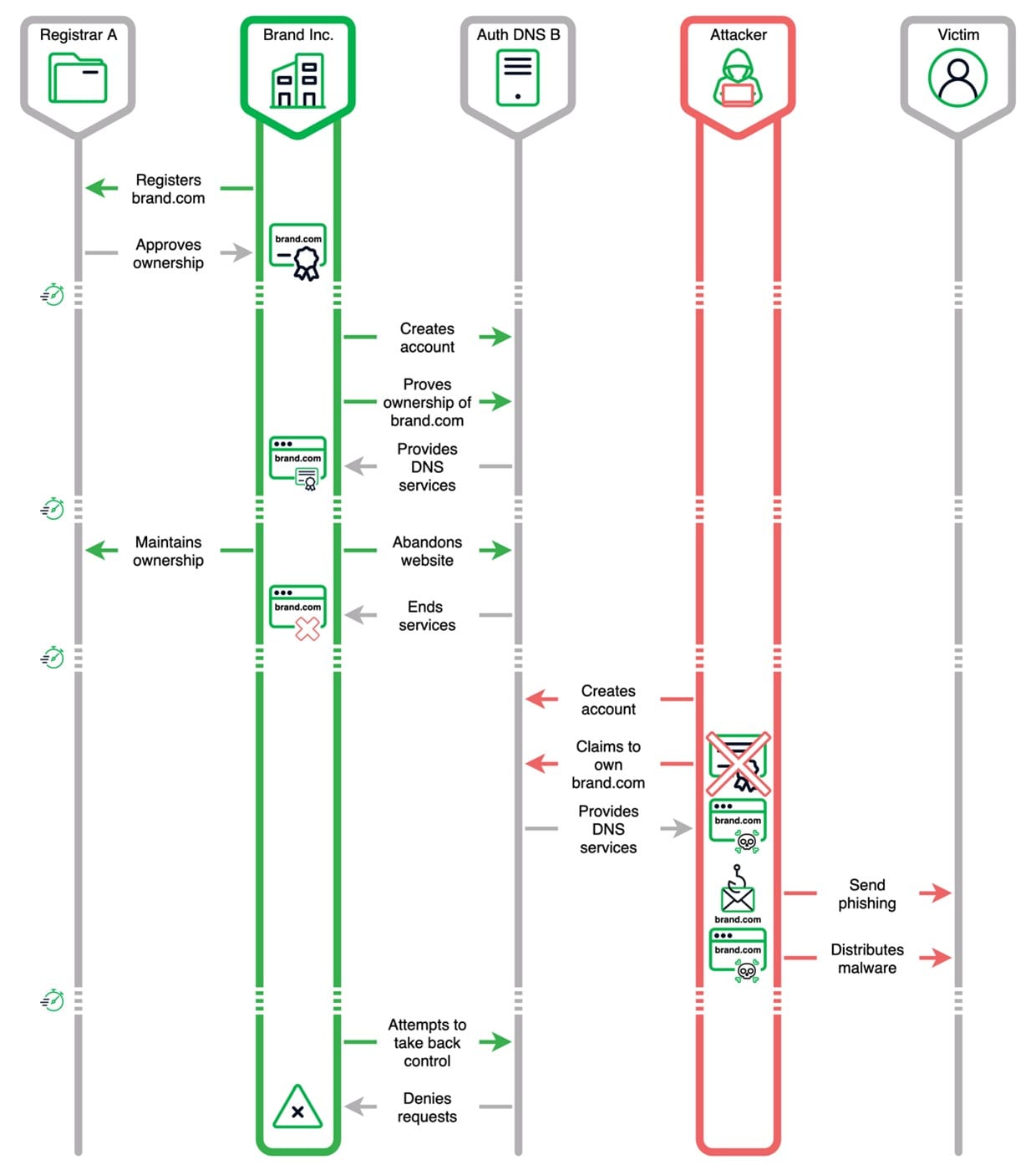
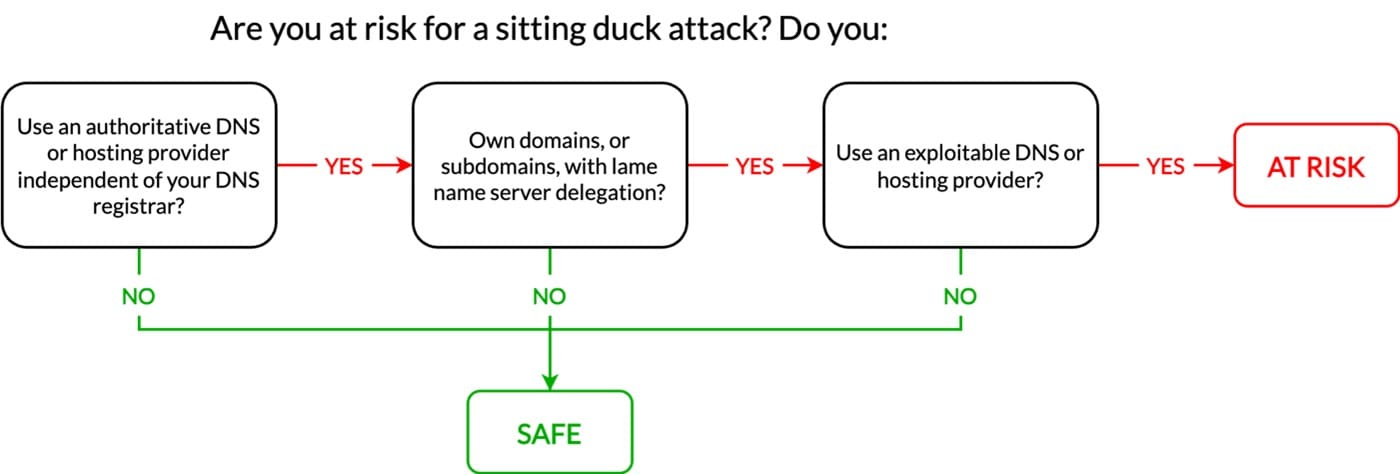
Sitting Ducks attack: Threat actors are exploiting a new DNS attack named Sitting Ducks to hijack domains and host malicious infrastructure. The attack affects misconfigured domains where the registrar and the authoritative DNS provider are different entities. Security firms Eclypsium and Infoblox estimate the number of vulnerable domains to one million. Threat actors have used the attack to hijack more than 30,000 domains since 2019. Most have been used to host malware or phishing sites. Infoblox says it discovered the attack while investigating 404TDS, a traffic distribution system operated by a Russian cybercrime group known as Vacant Viper.
WLAN calling vulnerabilities: A team of academics has discovered two major vulnerabilities in the Voice over Wi-Fi (VoWiFi) protocol, also known as WLAN calling. The protocol has been around since 2016, is now offered by almost all major mobile networks, and is pre-installed on all new smartphones. Researchers say that 13 of 275 mobile networks they analyzed used static encryption keys to establish WLAN calls, allowing for easy interception. In addition, 5G smartphones using MediaTek chips can be forced to use weaker forms of WLAN calling encryption, also opening the door for interception attacks. Researchers say that more than 140 million mobile users are at risk but that fixes are being rolled out.
LayeredSyscall research: White Knight Labs has published details on LayeredSyscall, a new technique that abuses Vectored Exception Handlers (VEH) to bypass EDR solutions.
Dating app tracking issues: An academic study [PDF] from researchers in Belgium found that six of 15 popular dating apps leak precise user location data, exposing their users to stalking and harassment. The six include the likes of Badoo, Bumble, Grindr, happn, Hinge, and Hily. The apps leaked location data through different versions of a triangulation attack. The research team said that apps like Tinder thwarted such attacks by using concepts such as "grid snapping." Besides location data, the 15 apps also leaked personal and sensitive information about users. (see tables below) [Additional coverage in TechCrunch]
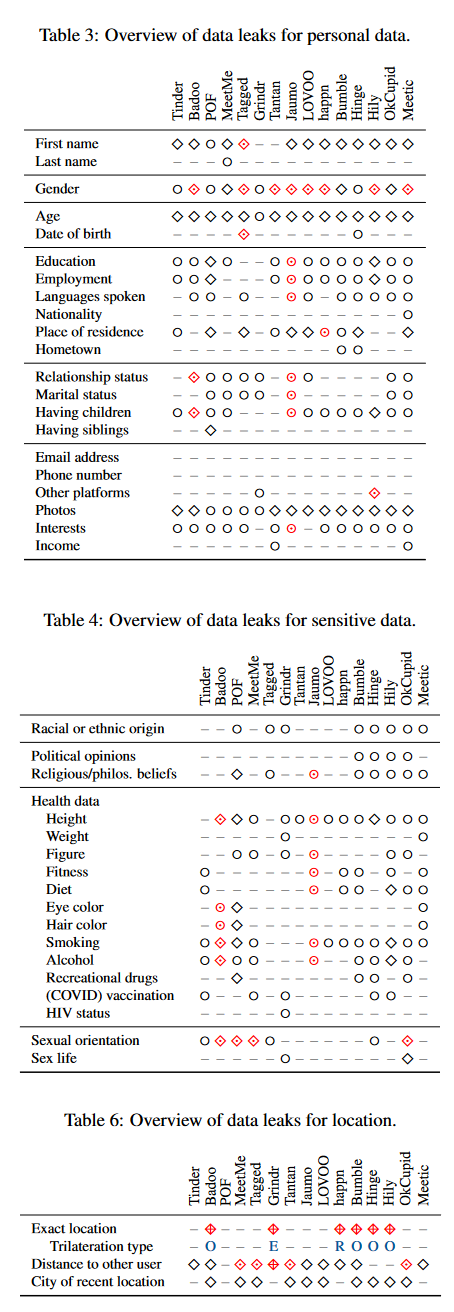
Infosec industry
New tool—EDR Telemetry Blocker: Tier Zero Security has open-sourced EDR Telemetry Blocker, an off-sec tool that blocks EDR telemetry (duh!) by performing a Person-in-the-Middle attack and filtering network traffic.
MSRC Researcher Resource Center: Microsoft has launched the MSRC Researcher Resource Center, a portal hosting educational content for security researchers.
Threat/trend reports: Akamai, FACCT, Keyfactor, Netskope, Semperis, and Trend Micro have recently published reports covering infosec industry threats and trends.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss what the widespread disruption caused by CrowdStrike's faulty update tells us about how useful cyber operations are for war.
In this podcast, Tom Uren and Patrick Gray discuss the Israeli government seizing documents from NSO Group so that they couldn't be shared with opposition counsel in a US lawsuit during discovery. It's a terrible look.
The Risky Business team has recently started publishing video versions of our podcasts. Below is the main weekly show, with Pat and Adam at the wheel!




